OverTheWire - Bandit - Level 25 -> Level 33
Description
Hello l33ts, I hope you are doing well. In today’s episode, we will be doing Level 25 -> Level 33 of Bandit from OverTheWire. Let’s connect to bandit25 and start.
Level 25 -> Level 26
Goal
Logging in to bandit26 from bandit25 should be fairly easy… The shell for user bandit26 is not /bin/bash, but something else. Find out what it is, how it works and how to break out of it.
Solution
On bandit25’s home directory, we see bandit26.sshkey which is bandit26’s ssh private key. When we try to login using that key, we get logged out after
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
bandit25@bandit:~$ ssh -i bandit26.sshkey bandit26@localhost
Could not create directory '/home/bandit25/.ssh'.
The authenticity of host 'localhost (127.0.0.1)' can't be established.
ECDSA key fingerprint is SHA256:98UL0ZWr85496EtCRkKlo20X3OPnyPSB5tB5RPbhczc.
Are you sure you want to continue connecting (yes/no)? yes
Failed to add the host to the list of known hosts (/home/bandit25/.ssh/known_hosts).
This is a OverTheWire game server. More information on http://www.overthewire.org/wargames
Linux bandit.otw.local 5.4.8 x86_64 GNU/Linux
,----.. ,----, .---.
/ / \ ,/ .`| /. ./|
/ . : ,` .' : .--'. ' ;
. / ;. \ ; ; / /__./ \ : |
. ; / ` ; .'___,/ ,' .--'. ' \' .
; | ; \ ; | | : | /___/ \ | ' '
| : | ; | ' ; |.'; ; ; \ \; :
. | ' ' ' : `----' | | \ ; ` |
' ; \; / | ' : ; . \ .\ ;
\ \ ', / | | ' \ \ ' \ |
; : / ' : | : ' |--"
\ \ .' ; |.' \ \ ;
www. `---` ver '---' he '---" ire.org
Welcome to OverTheWire!
If you find any problems, please report them to Steven or morla on
irc.overthewire.org.
For more information regarding individual wargames, visit
http://www.overthewire.org/wargames/
For support, questions or comments, contact us through IRC on
irc.overthewire.org #wargames.
Enjoy your stay!
_ _ _ _ ___ __
| | | (_) | |__ \ / /
| |__ __ _ _ __ __| |_| |_ ) / /_
| '_ \ / _` | '_ \ / _` | | __| / / '_ \
| |_) | (_| | | | | (_| | | |_ / /| (_) |
|_.__/ \__,_|_| |_|\__,_|_|\__|____\___/
Connection to localhost closed.
bandit25@bandit:~$
We know that the shell for bandit26 is not /bin/bash, so let’s check what shell this user has by executing the following.
1
2
bandit25@bandit:~$ cat /etc/passwd | grep -i bandit26
bandit26:x:11026:11026:bandit level 26:/home/bandit26:/usr/bin/showtext
The shell in /usr/bin/showtext, let’s see what this binary does.
1
2
3
4
5
6
7
bandit25@bandit:~$ cat /usr/bin/showtext
#!/bin/sh
export TERM=linux
more ~/text.txt
exit 0
This binary set the value of the environmental variable TERM to linux, and then executes the command more with text.txt which is in bandit26’s home directory.
According to the man page of more, the latter is a filter for paging through text one screenful at a time. Reading through the man page in the commands section, we can type v and get vim editor, and that will allow us to execute commands on the system.
For that, we need to be in the command view of more first, to do that, let’s make our terminal small so that the program doesn’t just exit.
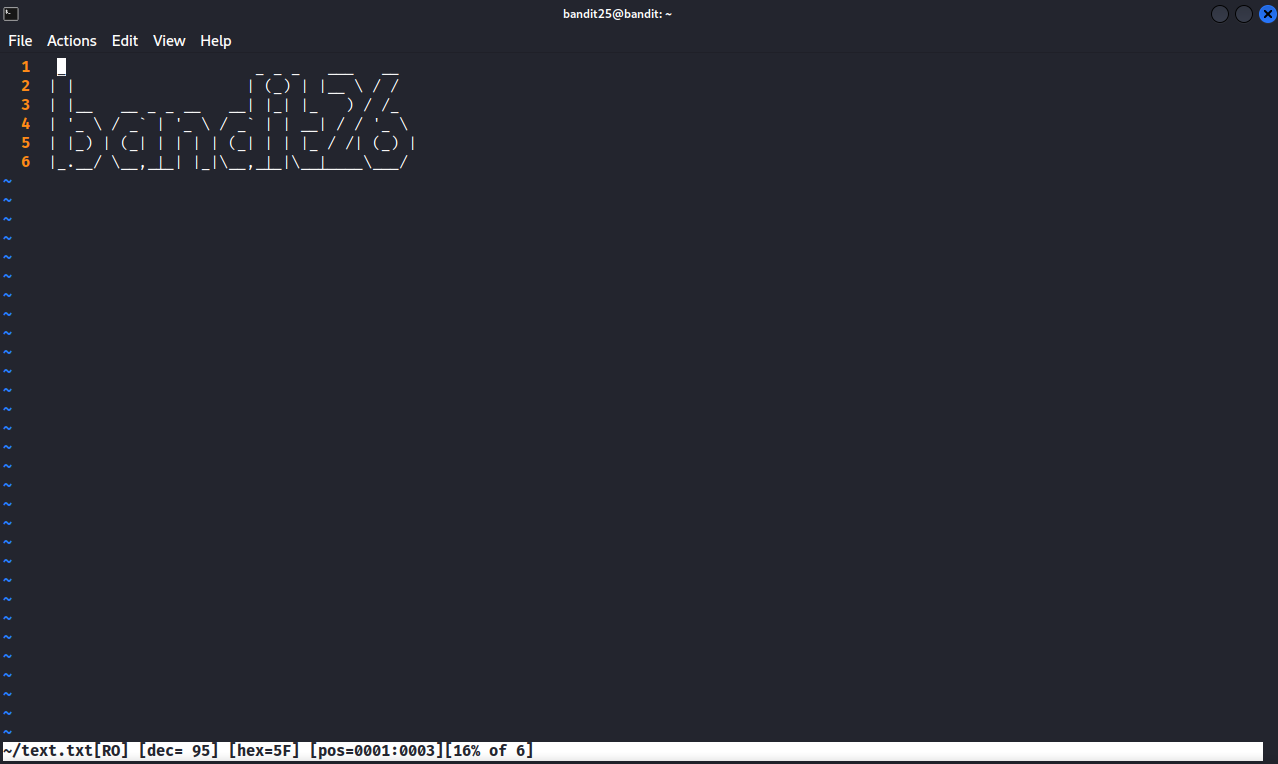
Now we press the button “v” and we get vim editor, we can now put our terminal window to it’s normal size.
The command we need to execute on vim is shell, this suppose to give us a shell, but when we run it, we get back into more, let’s check the value of shell by typing :set shell ? and hit enter
When get back shell=/usr/bin/showtext
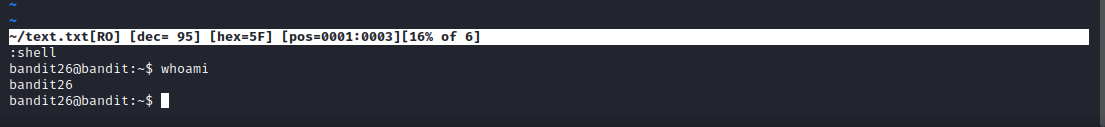
Now we now why we got back to more after running shell. We need to set the value of shell to /bin/bash by running :set shell=/bin/bash and run :shell after that in order to get our shell.
Level 26 -> Level 27
Goal
Good job getting a shell! Now hurry and grab the password for bandit27!
Solution
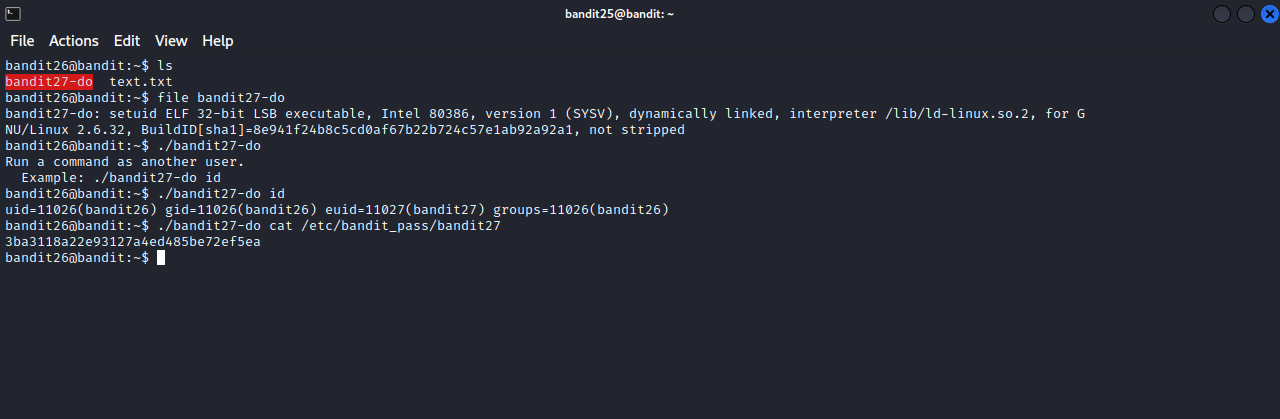
After the hard times trying to get a shell for bandit26, we now have one. Listing the content of bandit26’s home directory we see bandit27-do binary with suid permission, running it we get the syntax on how to use it, and just like level 19, running the binary with id we see that we ran it as bandit27. Let’s get the password for the next level.
Level 27 -> Level 28
Goal
There is a git repository at ssh://bandit27-git@localhost/home/bandit27-git/repo. The password for the user bandit27-git is the same as for the user bandit27.
Clone the repository and find the password for the next level.
Solution
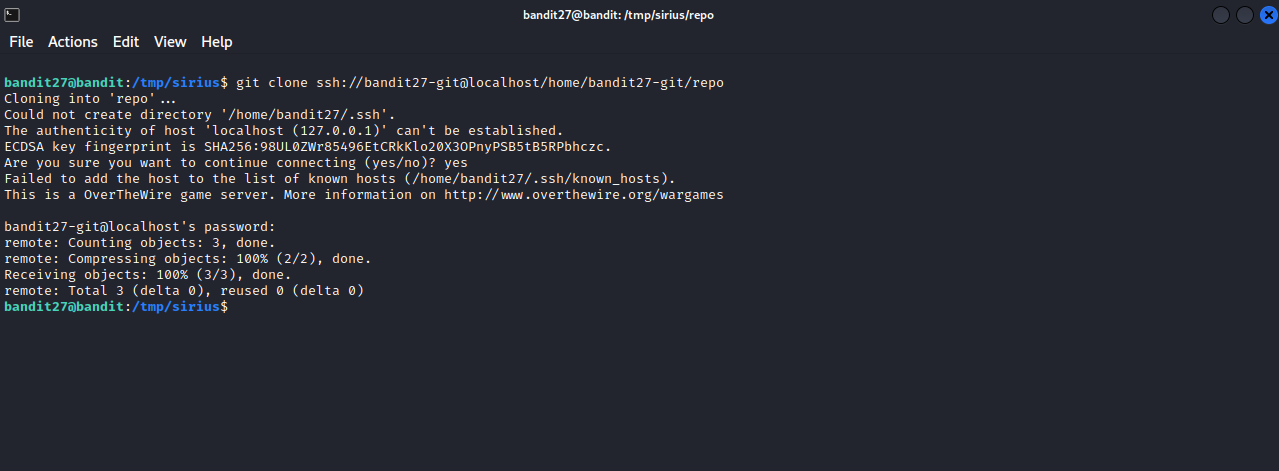
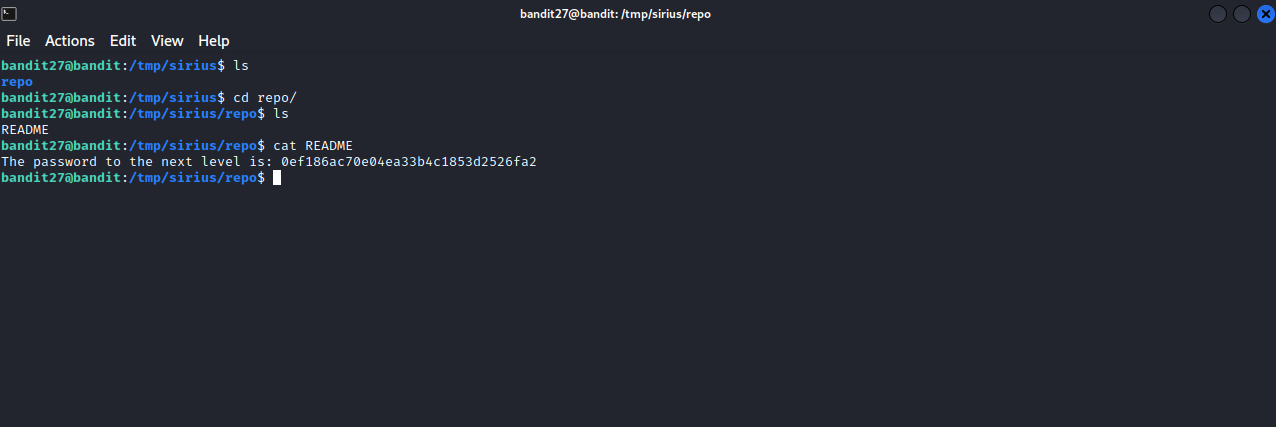
Let’s create a directory in /tmp, move to it and clone the repository using git clone ssh://bandit27-git@localhost/home/bandit27-git/repo
Navigating to repo we find a file named README, and it contains the password for the next level.
password for the next level : 0ef186ac70e04ea33b4c1853d2526fa2
Level28 -> Level 29
Goal
There is a git repository at ssh://bandit28-git@localhost/home/bandit28-git/repo. The password for the user bandit28-git is the same as for the user bandit28.
Clone the repository and find the password for the next level.
Solution
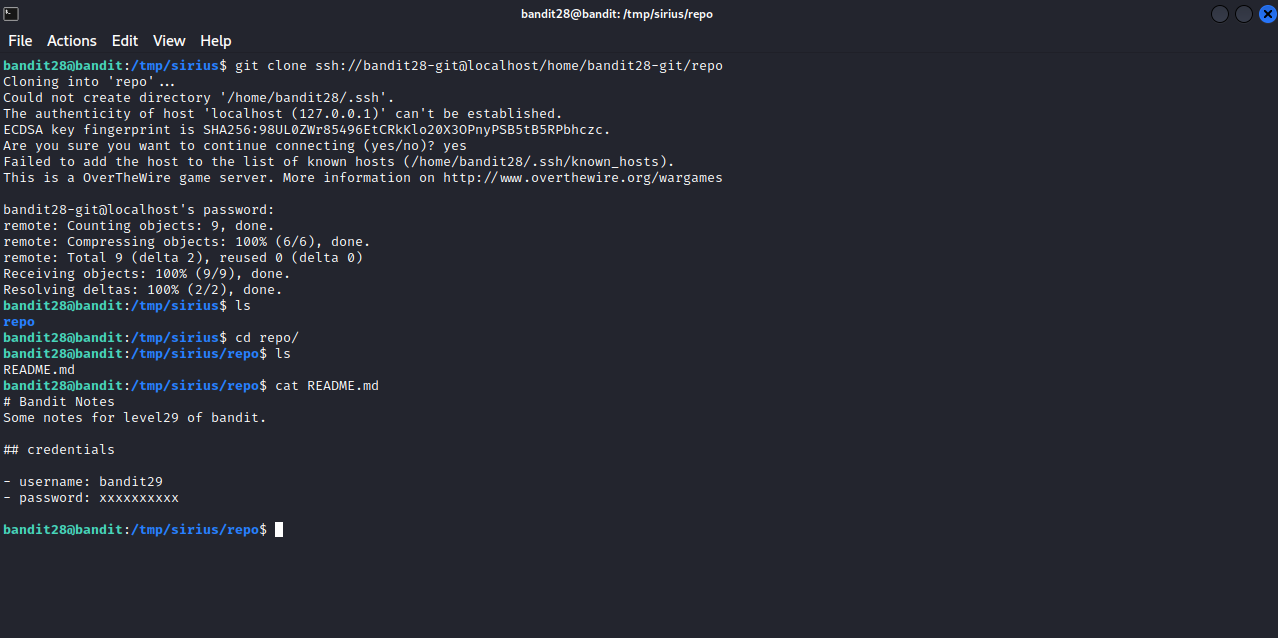
The same steps of the previous level apply here.
Let’s navigate to repo and see what can we find.
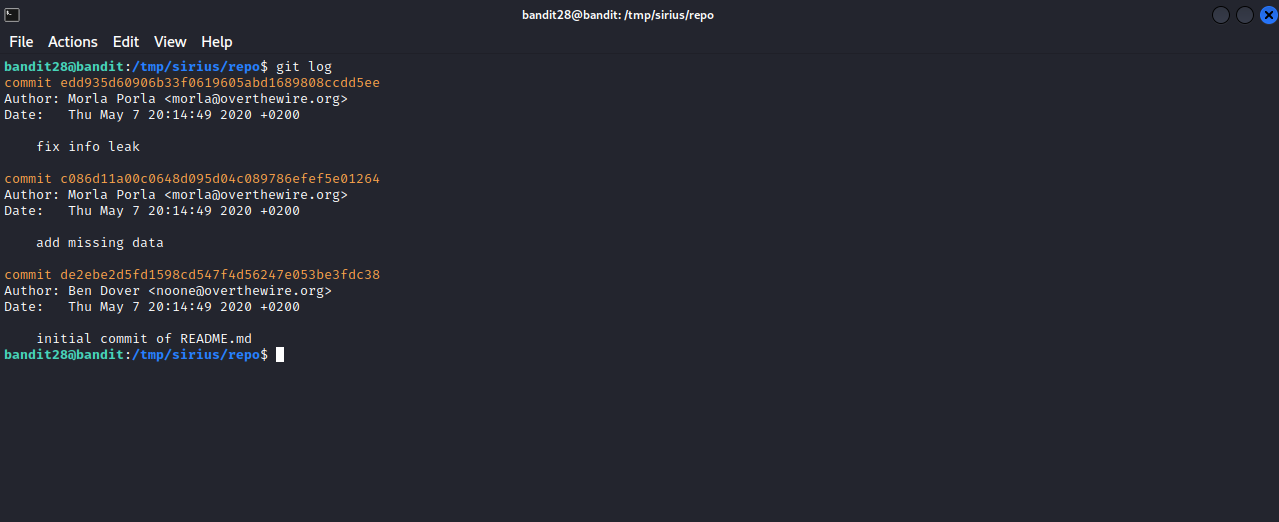
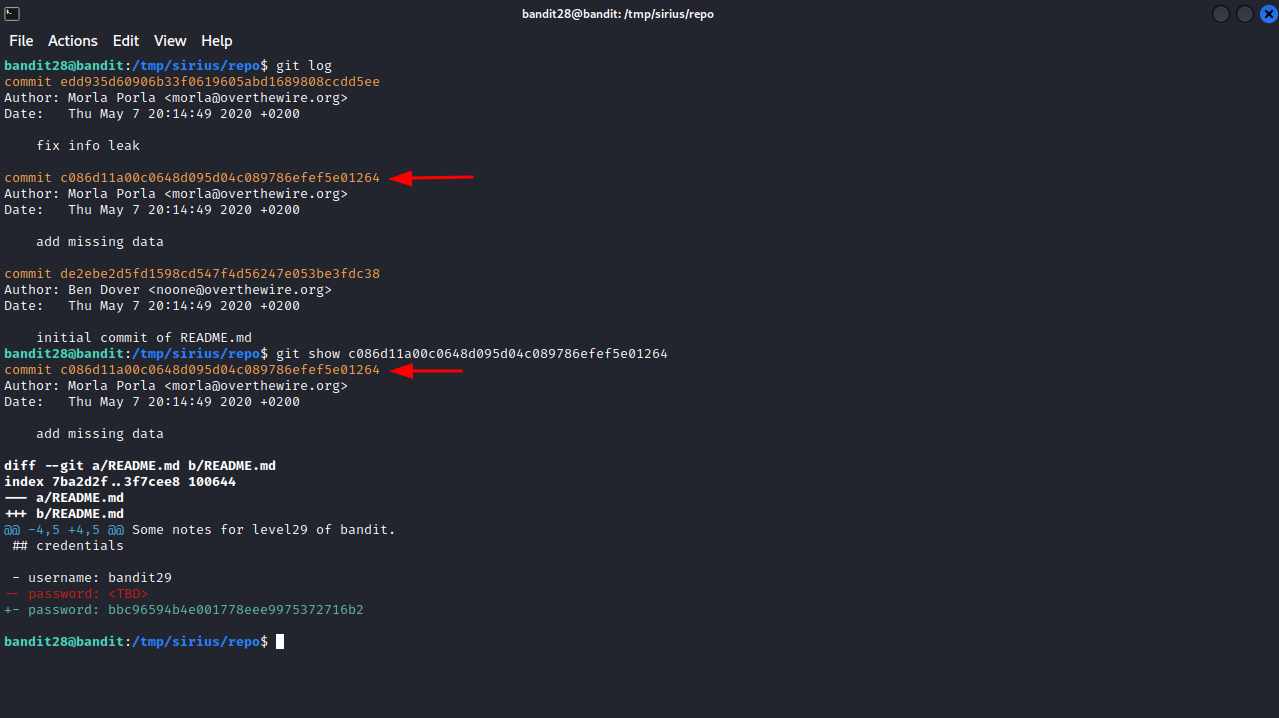
We found a README.md file but it doesn’t have the password. Since this is a git repository, let’s check the history of changes done to it, run the command git log inside the repo directory.
The last commit has the description of “fix info leak”, That’s why we didn’t find the password, let’s now check the second commit which will likely be the one where readme file contained the password. We can do that by executing git show {hash}.
The password for the next level : bbc96594b4e001778eee9975372716b2
Level 29 -> Level 30
Goal
There is a git repository at ssh://bandit29-git@localhost/home/bandit29-git/repo. The password for the user bandit29-git is the same as for the user bandit29.
Clone the repository and find the password for the next level.
Solution
Let’s clone the repository and investigate it. README file doesn’t have the password as expected, let’s see the logs.
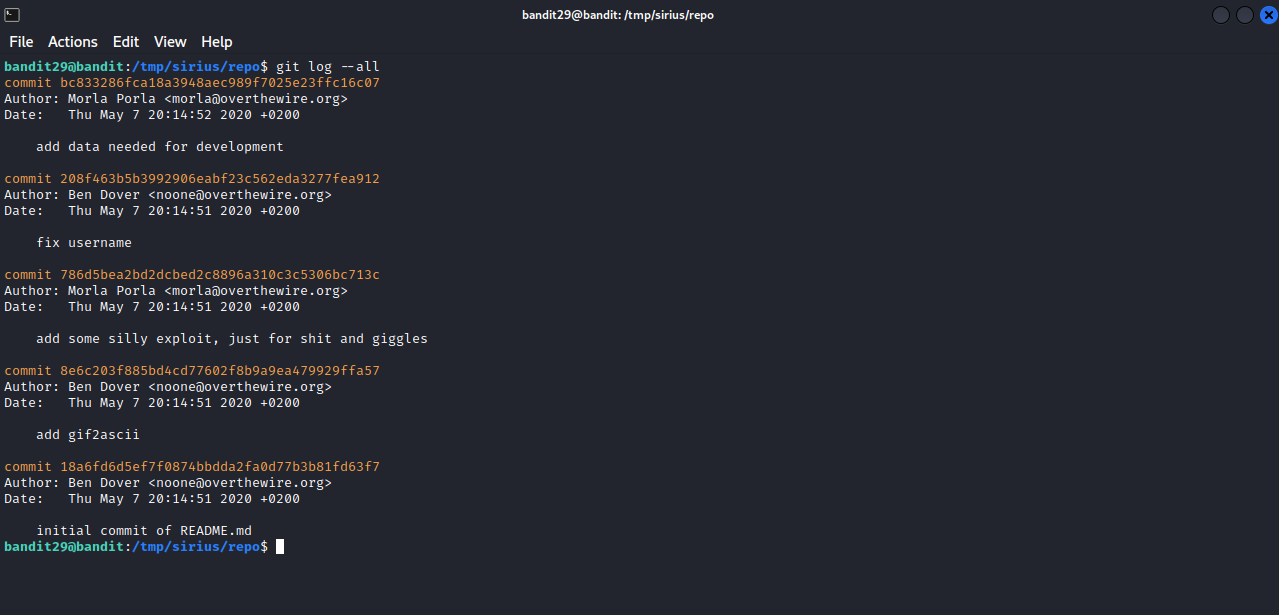
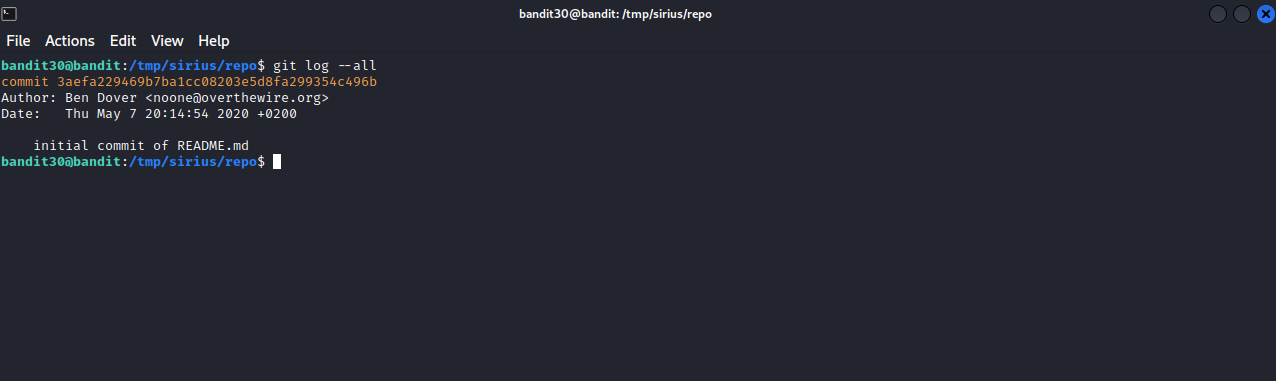
Checking the first commit, we don’t see any password. Let’s run git logs --all to see if there is any other commit we couldn’t see before.
Indeed there are other commits. Let’s check the changes of each commit.
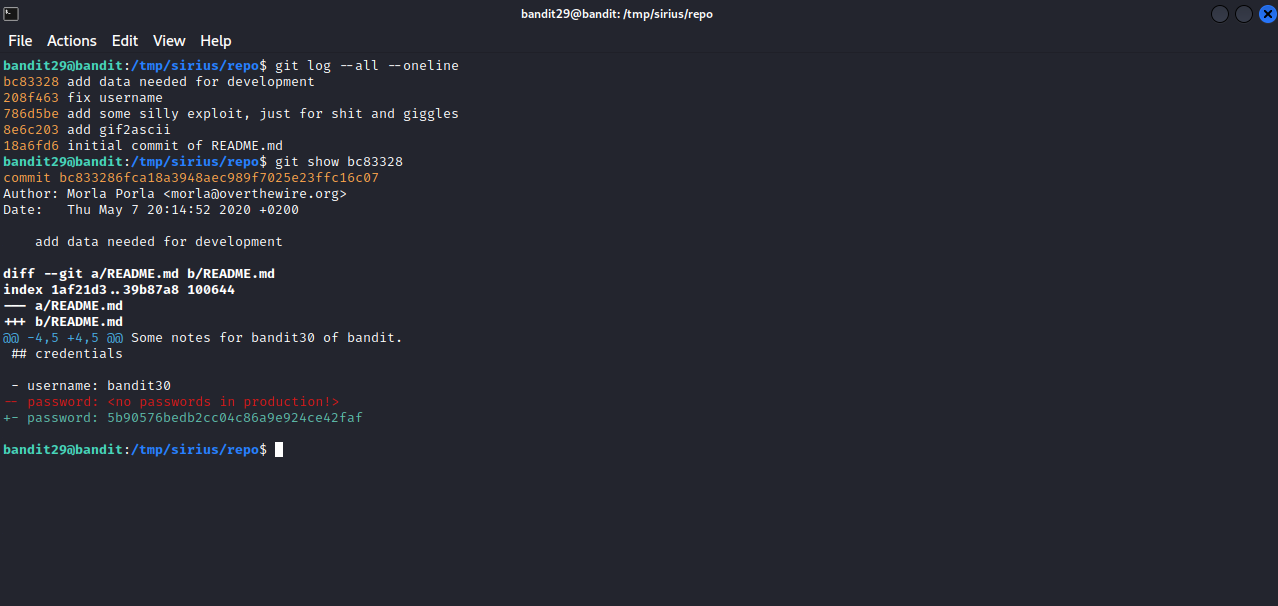
The –oneline option used in the image above shows only a small part of the hash and the description for better view, and we can use the short version of the hash with git show to see the changes.
The password for the next level : 5b90576bedb2cc04c86a9e924ce42faf
Level 30 -> Level 31
Goal
There is a git repository at ssh://bandit30-git@localhost/home/bandit30-git/repo. The password for the user bandit30-git is the same as for the user bandit30.
Clone the repository and find the password for the next level.
Solution
Let’s clone the repository and check the logs.
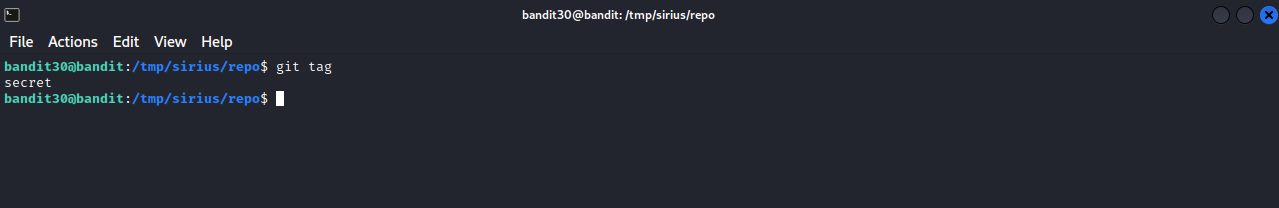
We only see one commit. Let’s check if there is any tags using git tag.
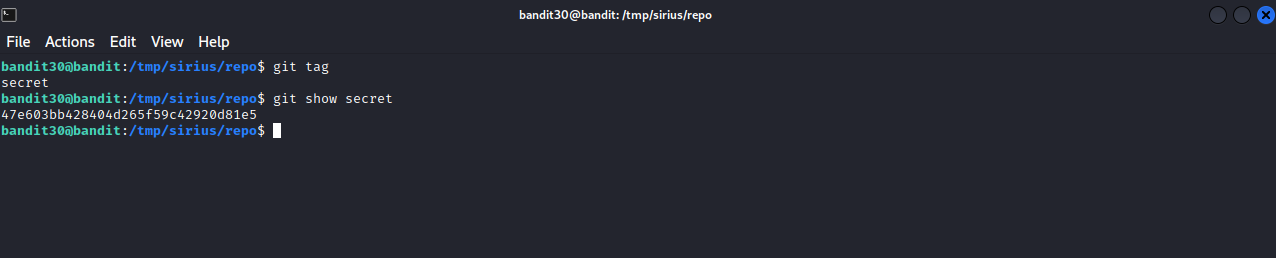
Tags are ref’s that point to specific points in Git history, and it is usually used to capture a point in history that is used for marked version release. In our case, we found secret tag, let’s show it using git show secret
The password for the next level : 47e603bb428404d265f59c42920d81e5
Level 31 -> Level 32
Goal
There is a git repository at ssh://bandit31-git@localhost/home/bandit31-git/repo. The password for the user bandit31-git is the same as for the user bandit31.
Clone the repository and find the password for the next level.
Solution
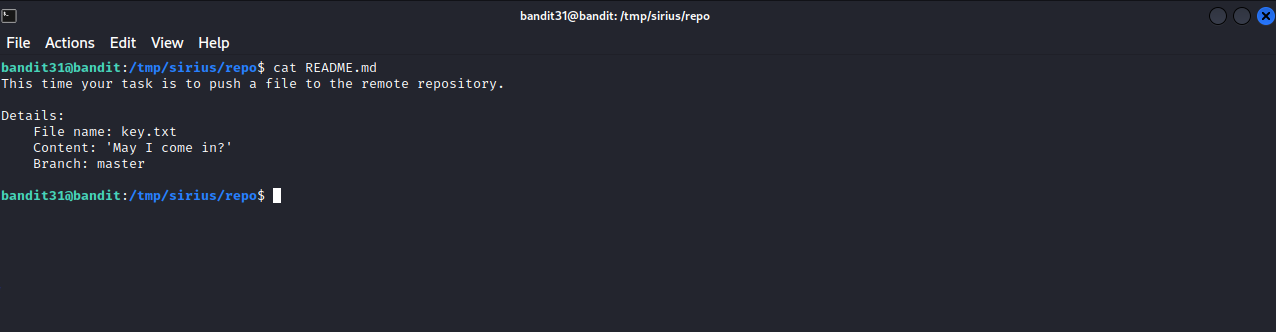
As always, let’s clone the repository and see what’s there.
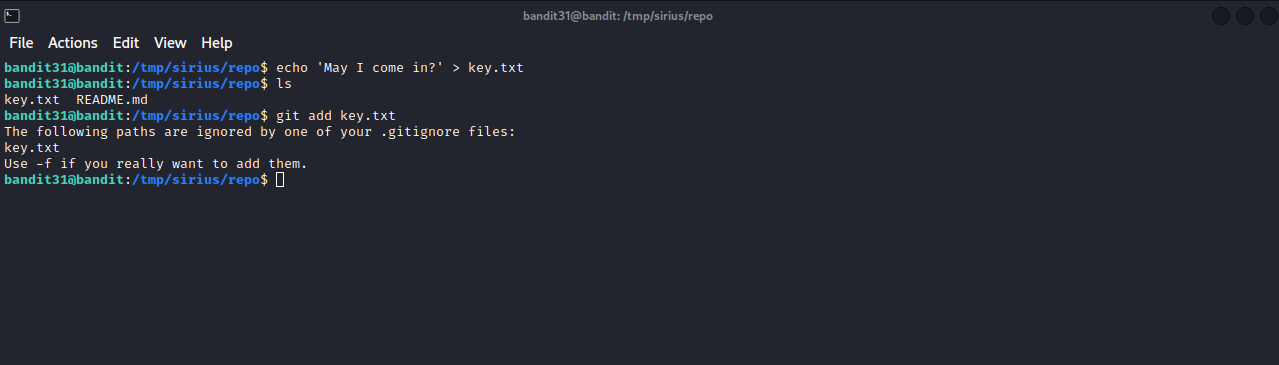
It seems that we need to create a file called key.txt that contains ‘May I come in?’ in it and push that file to the remote repository, so let’s create the file and push it.
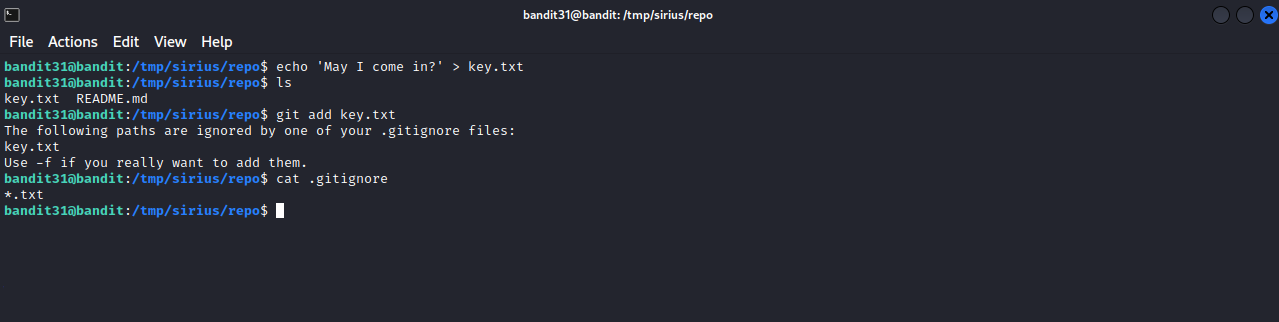
We couldn’t upload the file because there is a .gitignore file, which is a file that specifies intentionally untracked files that Git should ignore. Inside of the file there is .txt, which means it will ignore every .txt file.
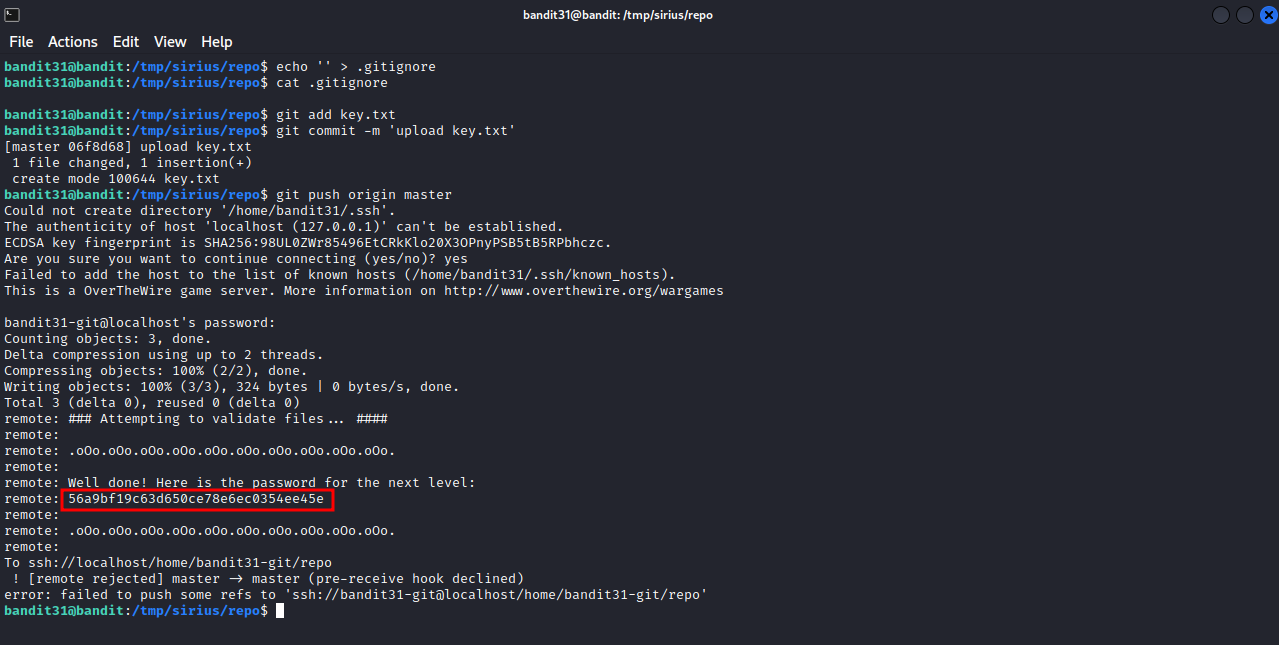
Let’s modify the file by removing *.txt, push it after that.
We have successfully pushed the file and got the password.
The password for the next level : 56a9bf19c63d650ce78e6ec0354ee45e
Level 32 -> Level 33
Goal
After all this git stuff its time for another escape. Good luck!
Solution
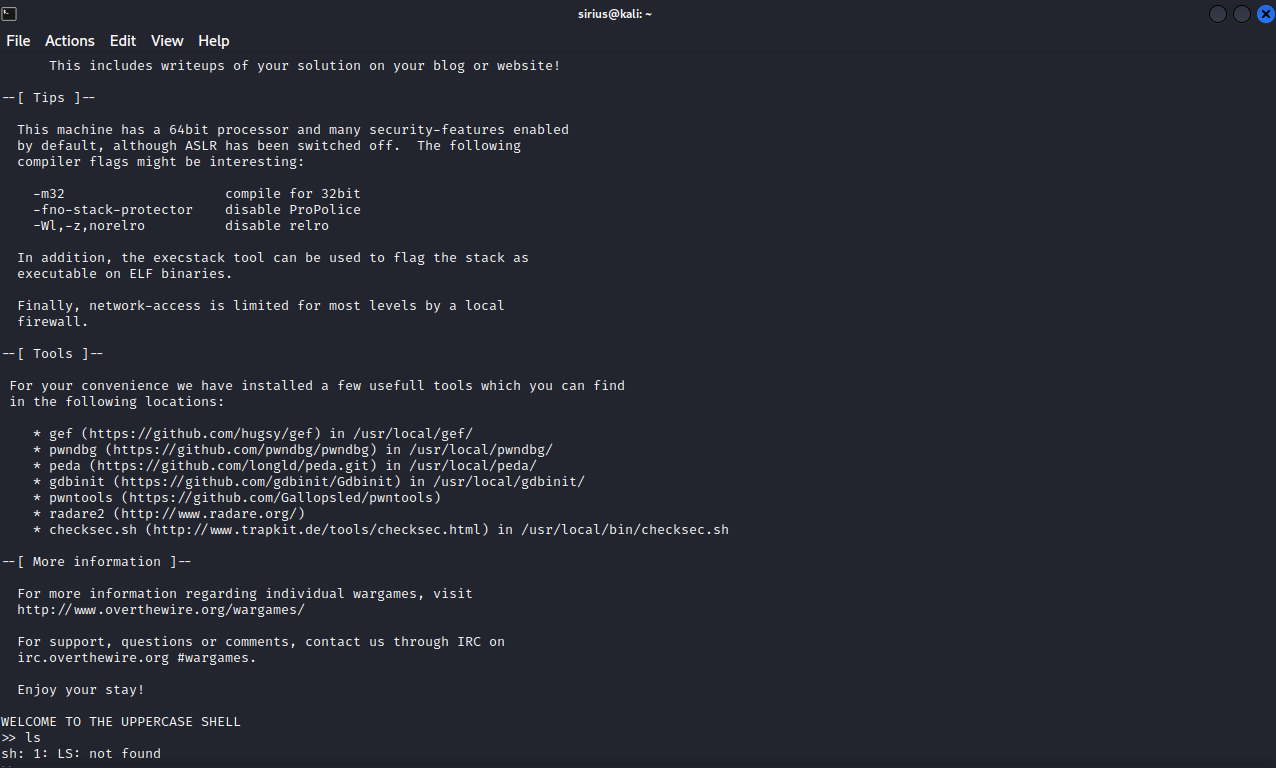
When we login, we get a unusual prompt, and we can’t execute linux commands
The shell seems to convert every command we enter into uppercase. Let’s go back the bandit 31 and check what shell bandit32 use.
1
2
bandit31@bandit:~$ cat /etc/passwd | grep bandit32
bandit32:x:11032:11032:bandit level 32:/home/bandit32:/home/bandit32/uppershell
It uses a shell called uppershell.
Let’s try tho understand how this shell works.
When we run a command, let’s say for example whoami, we get the following:
1
2
>> whoami
sh: 1: WHOAMI: not found
We can see sh, which is what the program uses to execute commands, and after it we see a 1 and WHOAMI. We conclude from that error message that the program uses positional parameter to do it’s job. Read more about positional parameter in this article
What we need to do to get a shell is to invoke the first positional parameter - that happens to be sh- by typing the parameter for sh which is going to be $0
By executing $0 we get an sh shell, we can get an appropriate shell by exporting the value of $SHELL to /bin/bash and calling it after that.
We have finally finished the all the 33 levels of Bandit, so kudos for making it here, thank you for taking the time to read my writeup, hopefully you have learnt some new tricks along the way. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :) .