HackTheBox - Meow
Description
Hello l33ts, I hope you are doing well. Today we are going to look at Meow from HackTheBox. A very easy machine from Starting Point machines.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
Nmap scan report for 10.129.1.17 (10.129.1.17)
Host is up (0.15s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
23/tcp open telnet Linux telnetd
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Port 23 is open running telnet.
The telnet service is an old service used for remote management of other hosts on the network. Telnet is inherently insecure. Credential information (usernames and passwords) submitted through telnet is not encrypted and is therefore vulnerable to identity theft. Because of that, it has been replaced with SSH (Secure Shell) that encrypts traffic in both directions.
Foothold
Connecting to telnet requires a combination of a username and password as we can see when we try to connect to it.
Every time presented with a login form, the first things to try if we have no credentials is to try some default or top used credentials, some examples are :
- admin:admin
- admin:password
- root:root
Let’s see if we can login wit those credentials.
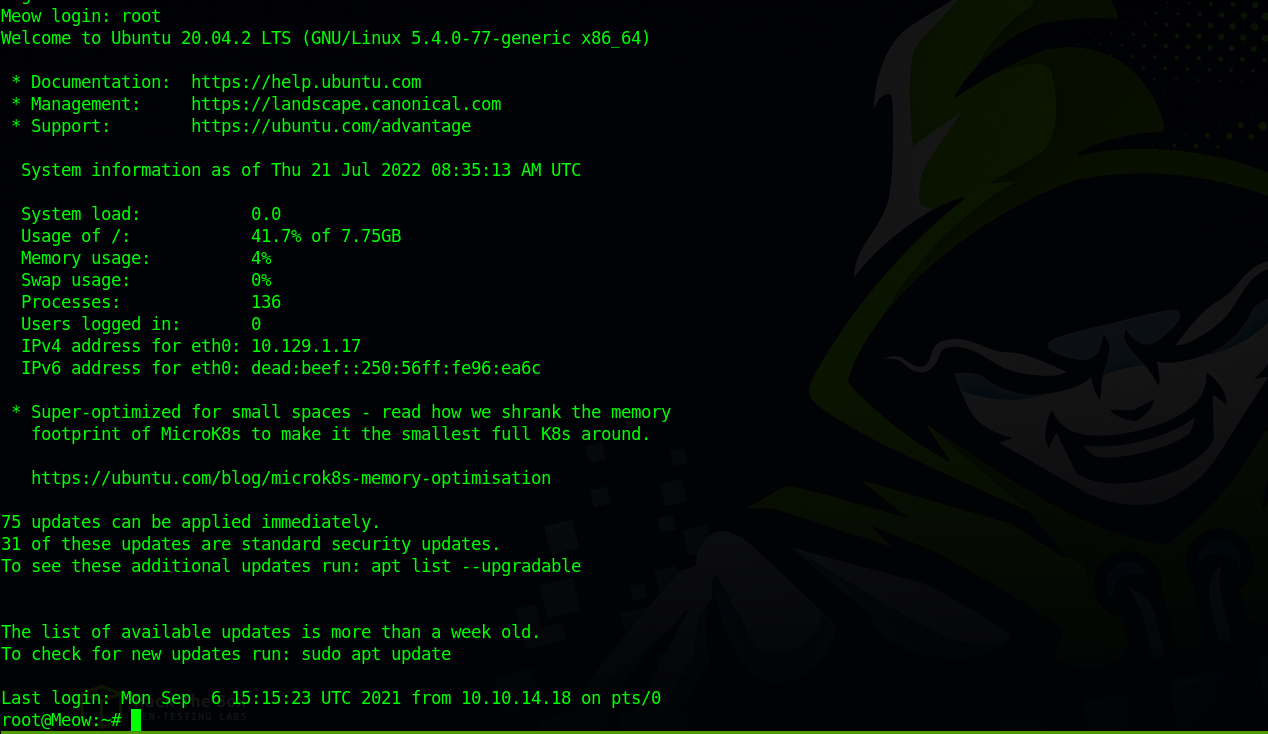
The first two creds didn’t work. Let’s try the last one.
Great! We have logged into the target system successfully.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).