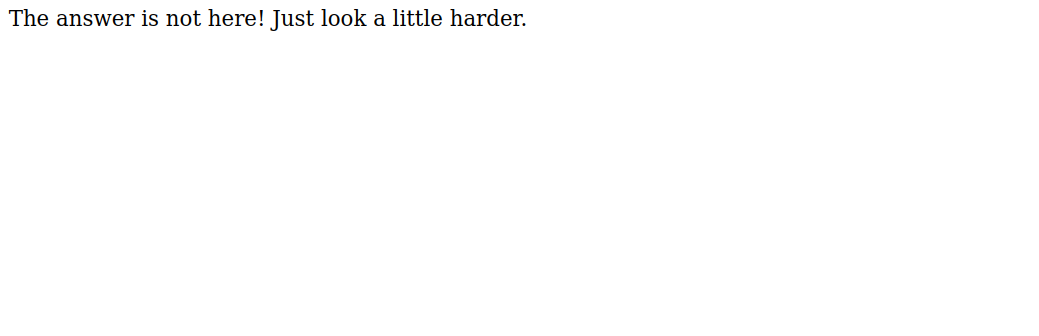HackThisSite - Basic mission 11
Description
Hello l33ts, I hope you are doing well. We will be doing Basic mission 11 from HackThisSite. It is the last challenge of this series.
Solution
According to the description, we have a music site, and it has something to do with Apache. Let’s navigate to the challenge page.
We got a message, and every time we refresh the webpage we get similar messages.
I love my music! “Candle in the Wind” is the best!
I love my music! “Sick City” is the best!
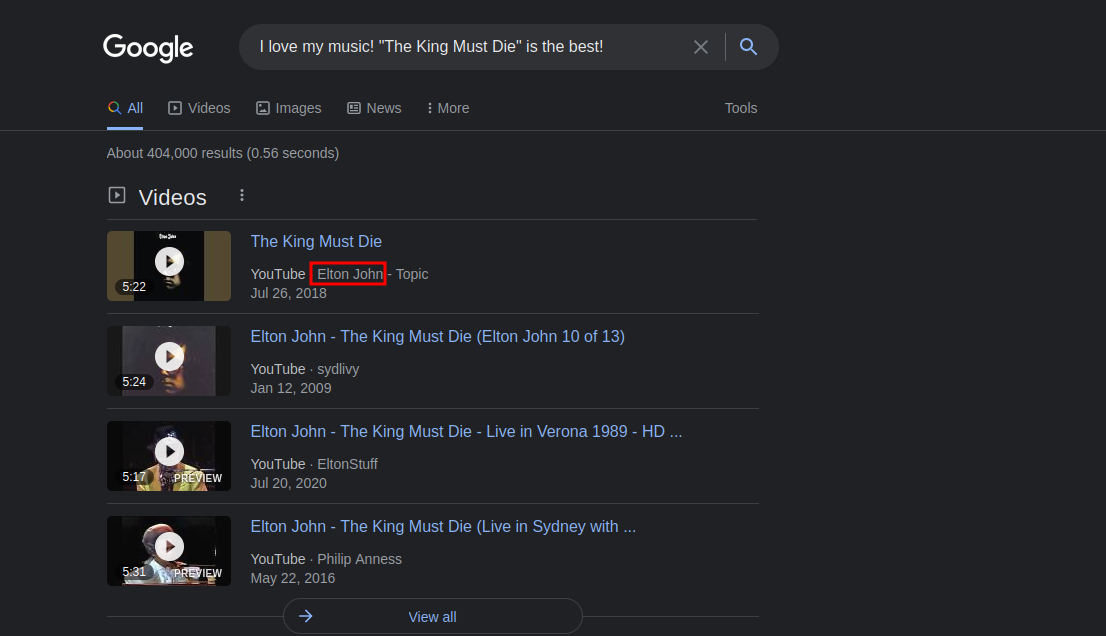
I love my music! “The King Must Die” is the best!
I googled these sentences and got this.
They are songs from someone called Elton John.
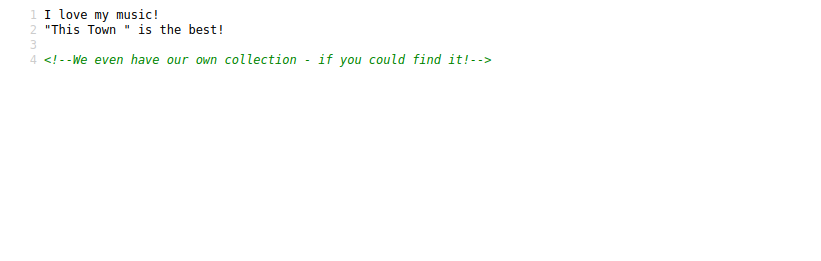
Let’s view the source code of the page.
There is a comment saying there are more stuff if we can find it. Let’s try running a directory/file scan. gobuster dir -w /usr/share/wordlists/dirb/small.txt -u https://www.hackthissite.org/missions/basic/11/ -x php
$ gobuster dir -w /usr/share/wordlists/dirb/small.txt -u https://www.hackthissite.org/missions/basic/11/ -x php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://www.hackthissite.org/missions/basic/11/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2022/04/28 07:54:30 Starting gobuster in directory enumeration mode
===============================================================
/e (Status: 301) [Size: 256] [--> http://www.hackthissite.org/missions/basic/11/e/]
/index (Status: 200) [Size: 116]
/index.php (Status: 200) [Size: 146]
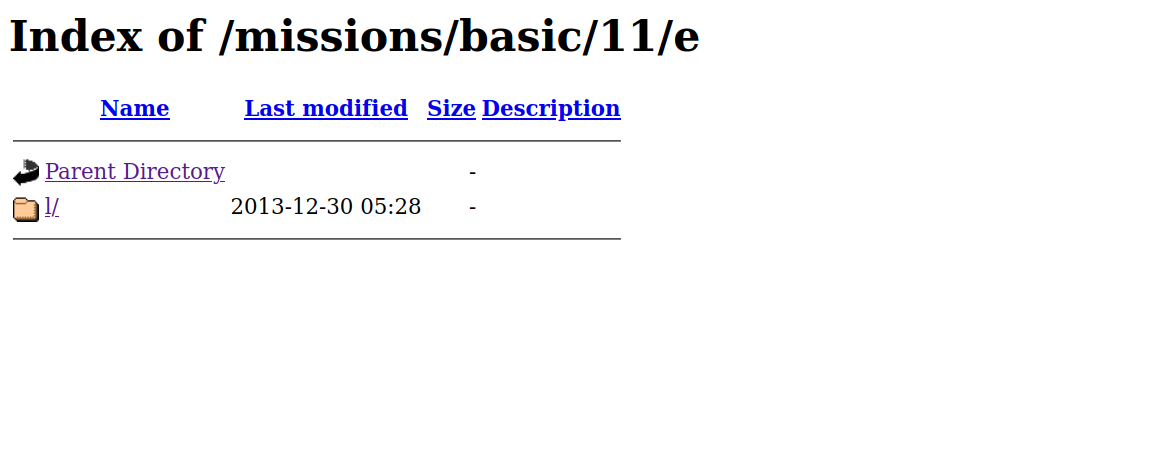
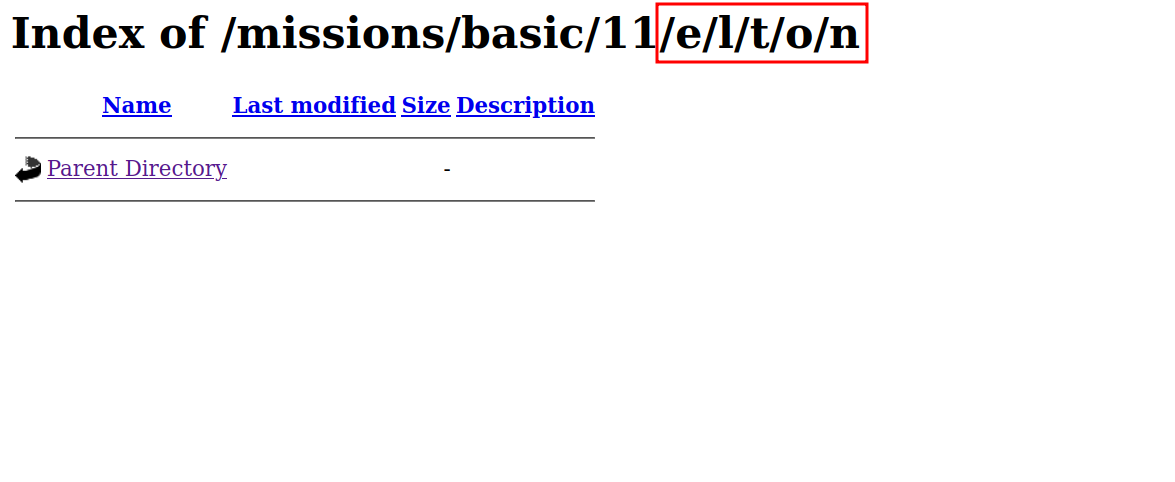
We found /e directory, let’s see what’s there.
we found another directory, and even more directories. Following them we get this.
Elton, the singer we found earlier, but this directory is empty.
One of the hints we got is that Sam doesn’t understand Apache. Some of the import files in Apache are .htaccess files, they are configuration files for the Apache web server that can be used to override certain server configuration options on a per-directory basis using a human readable file.
If their contents are exposed, attackers can gain valuable insight into te server configuration and may read sensitive datal.
If we run another directory/file scan, we can see that the file is readable.
$ gobuster dir -w /usr/share/wordlists/dirb/common.txt -u https://www.hackthissite.org/missions/basic/11/e/l/t/o/n/ 1 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://www.hackthissite.org/missions/basic/11/e/l/t/o/n/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/04/28 08:04:39 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 14925]
/.htaccess (Status: 200) [Size: 80]
/.htpasswd (Status: 403) [Size: 15033]
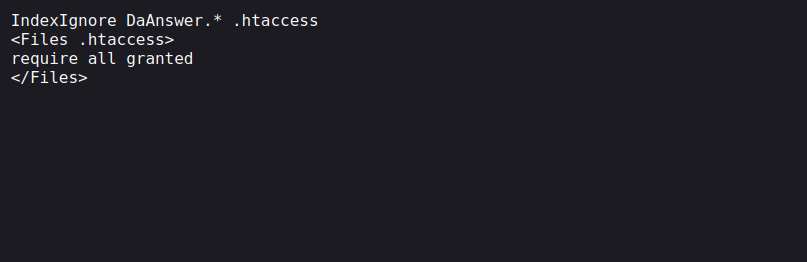
Let’s see what it holds.
Beside .htaccess, there is another file on the directory, DaAnswer
We got the message : The answer is not here! Just look a little harder. This is really confusing, but if we think a little, the answer is not here.
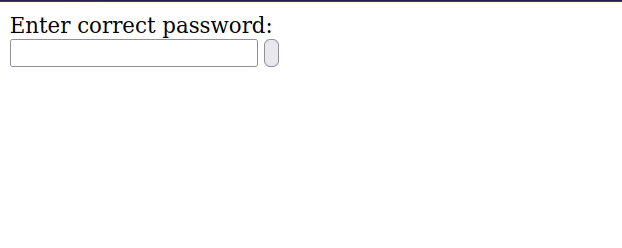
Now we need a place to submit the password. From our first directory scan, we found index.php page, and this is where we submit the password.
Now enter the password ‘not here’ and submit it.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).
References
https://www.invicti.com/web-vulnerability-scanner/vulnerabilities/htaccess-file-detected/