HackThisSite - Basic mission 8
Description
Hello l33ts, I hope you are doing well. We will be doing Basic mission 8 from HackThisSite.
Solution
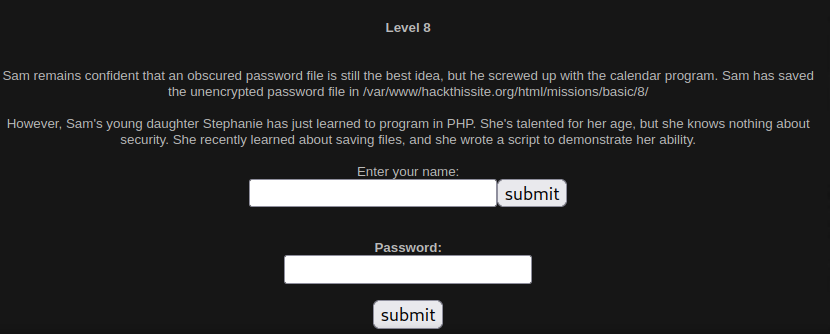
Let’s navigate to the challenge page.
An unencrypted password file is still there, now we have a program that saves user input into a file, let’s submit a name to see what the program does.
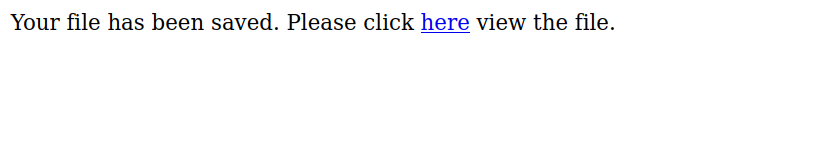
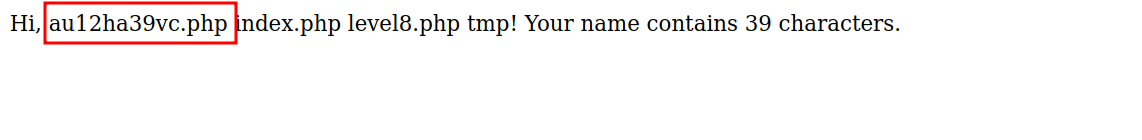
We get redirected to this page that tells us to click a link to view the file. Let’s click the link.
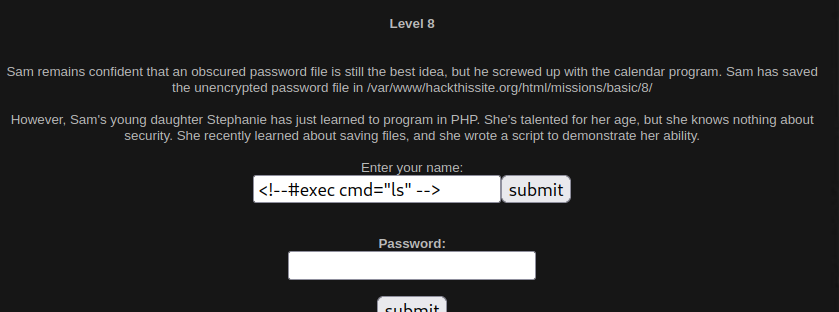
It says Hi, prints the name we submitted and tells us how many characters the name has. One other thing to notice is the URL : https://www.hackthissite.org/missions/basic/8/tmp/ubjvgnow.shtml. The file has a random string and a .shtml as an extension. I googled shtml exploit and found that it is famously vulnerable to SSI Injection. I found this article that explains how the vulnerability works. In the article i found a payload that would let us list the content of the directory: <!--#exec cmd="ls" -->, let’s submit that as a name and see.
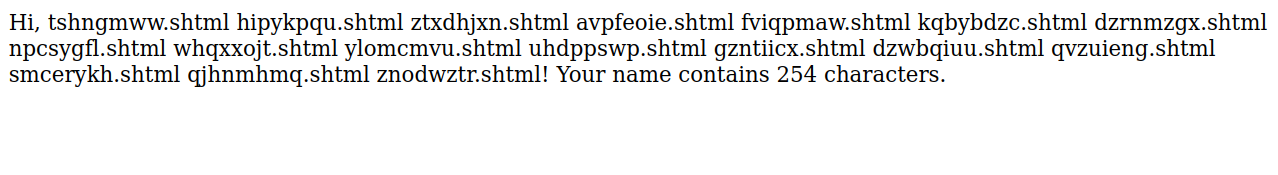
We managed to list the content of /tmp directory, we know that the password is up a directory, so let’s run ls .. to see the content of /8 directory, the final payload will look like this <!--#exec cmd="ls .." -->
Great! We listed the content of the challenge directory and we found the password file, navigate to that file to get the password.
Thank you for taking the time to read my writeup, I hope you have learned something with this, if you have any questions or comments, please feel free to reach out to me. See you in the next hack :) .
References
https://owasp.org/www-community/attacks/Server-Side_Includes_(SSI)_Injection