TryHackMe - c4ptur3th3fl4g
Description
Hello hackers, I hope you are doing well. We are doing c4ptur3th3fl4g from TryHackMe.
Translation & Shifting
Translate, shift and decode the following.
#1 : c4n y0u c4p7u23 7h3 f149?
This one looks like leetspeak, we need to replace the numbers with their corresponding letters.
| 0 = O | 1 = I | 2 = Z | 3 = E | 4 = A | 5 = S | 6 = G | 7 = T | 8 = B | 9 = g |
ans : can you capture the flag?
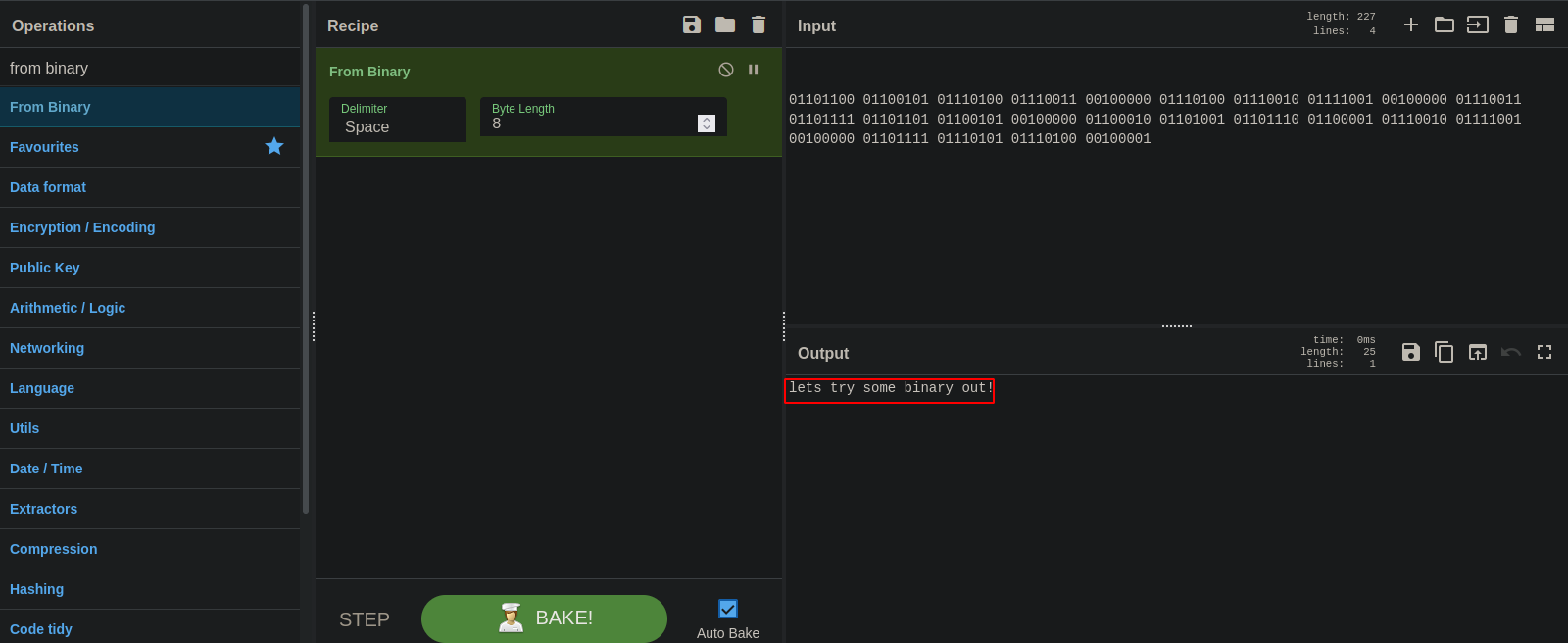
#2
This one is binary, we can go to CyberChef and convert it.
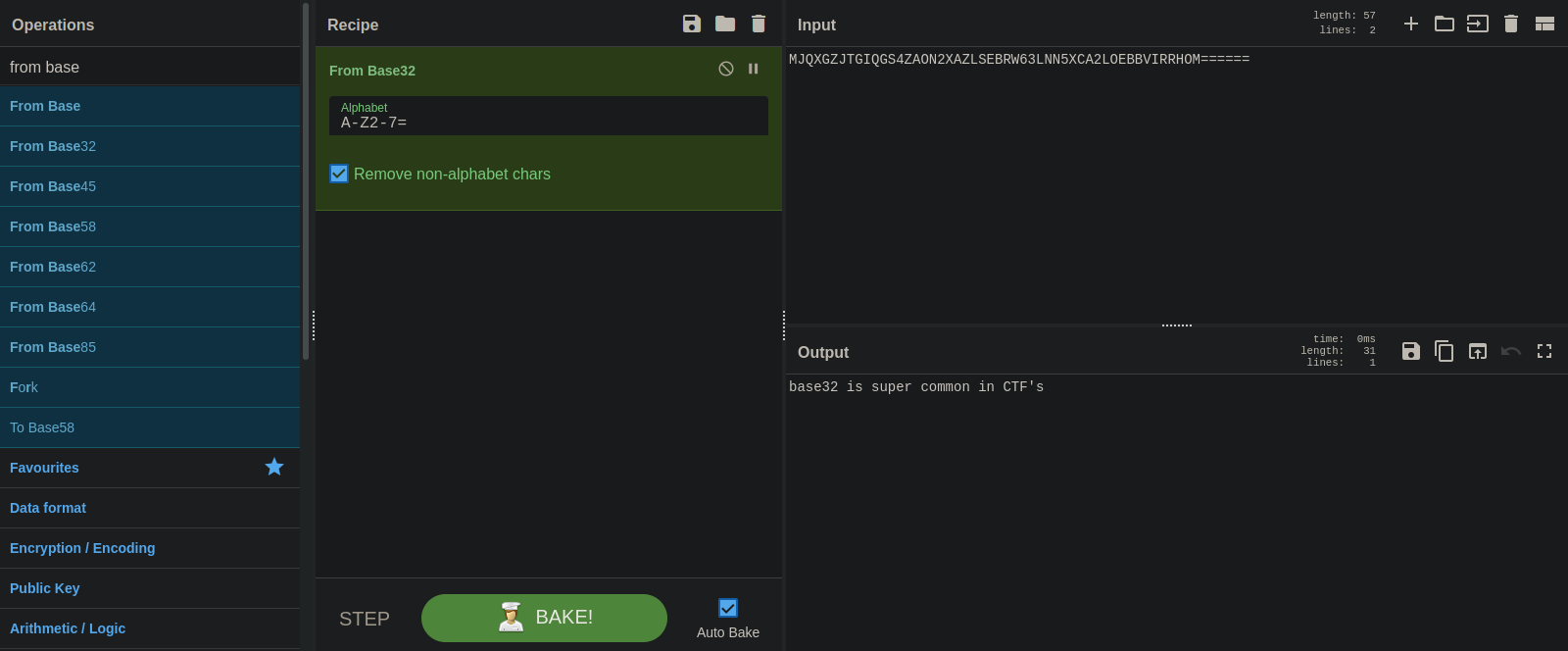
#3
This one looks a base. Let’s use CyberChef.
It’s a bse32.
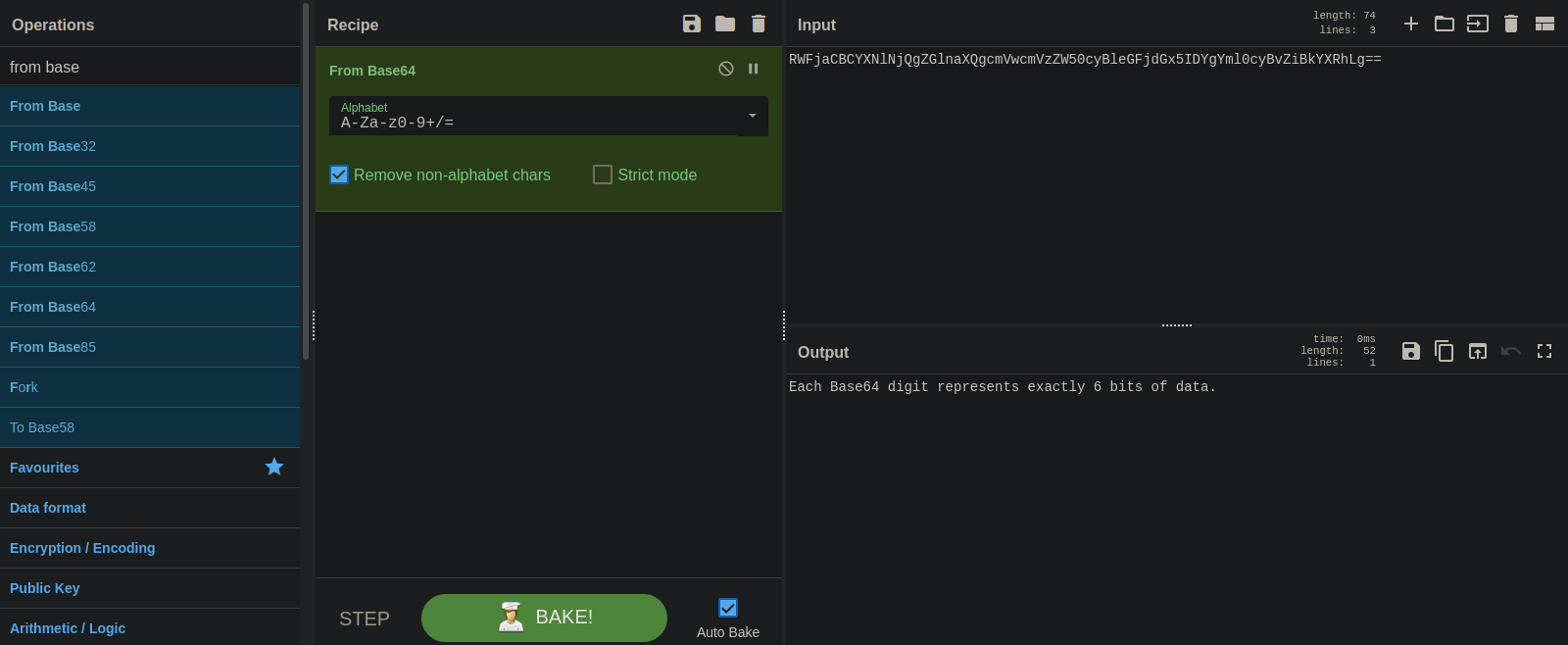
#4
This is base64.
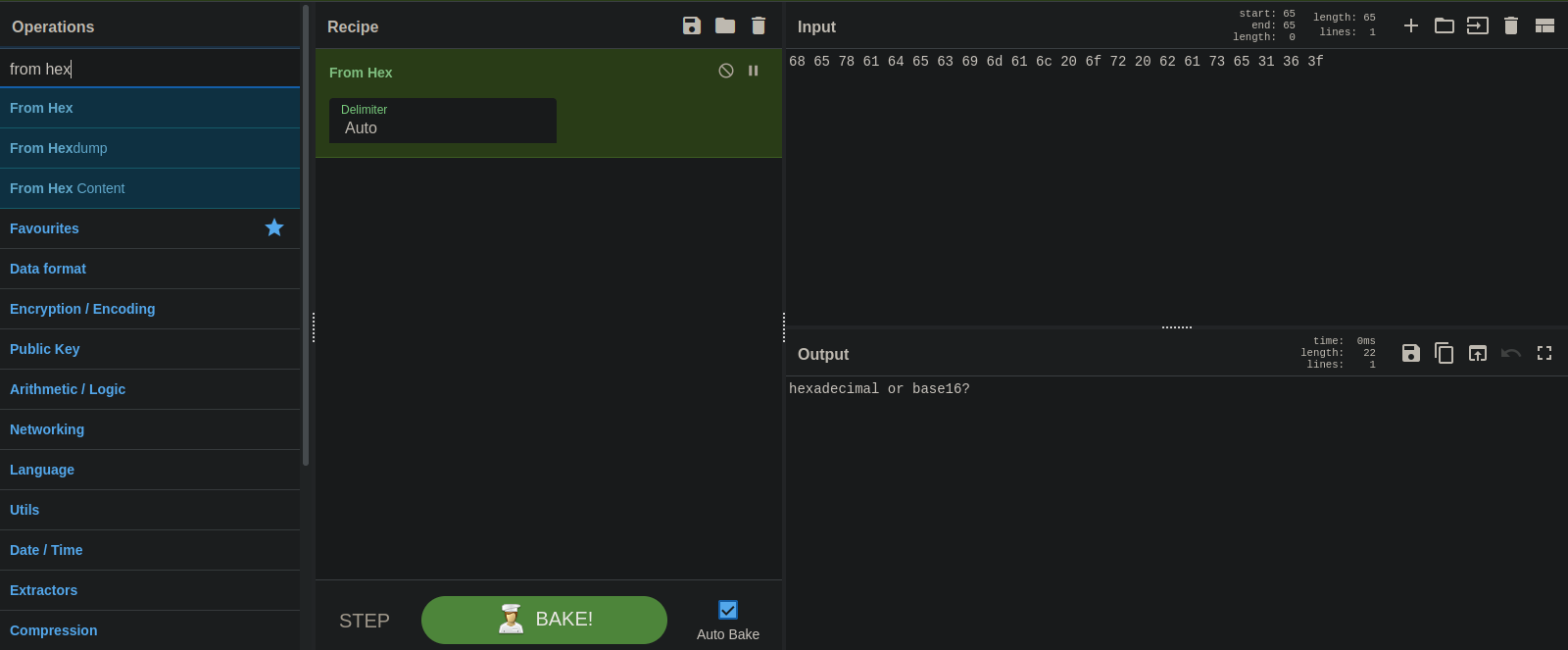
#5
This one is hex.
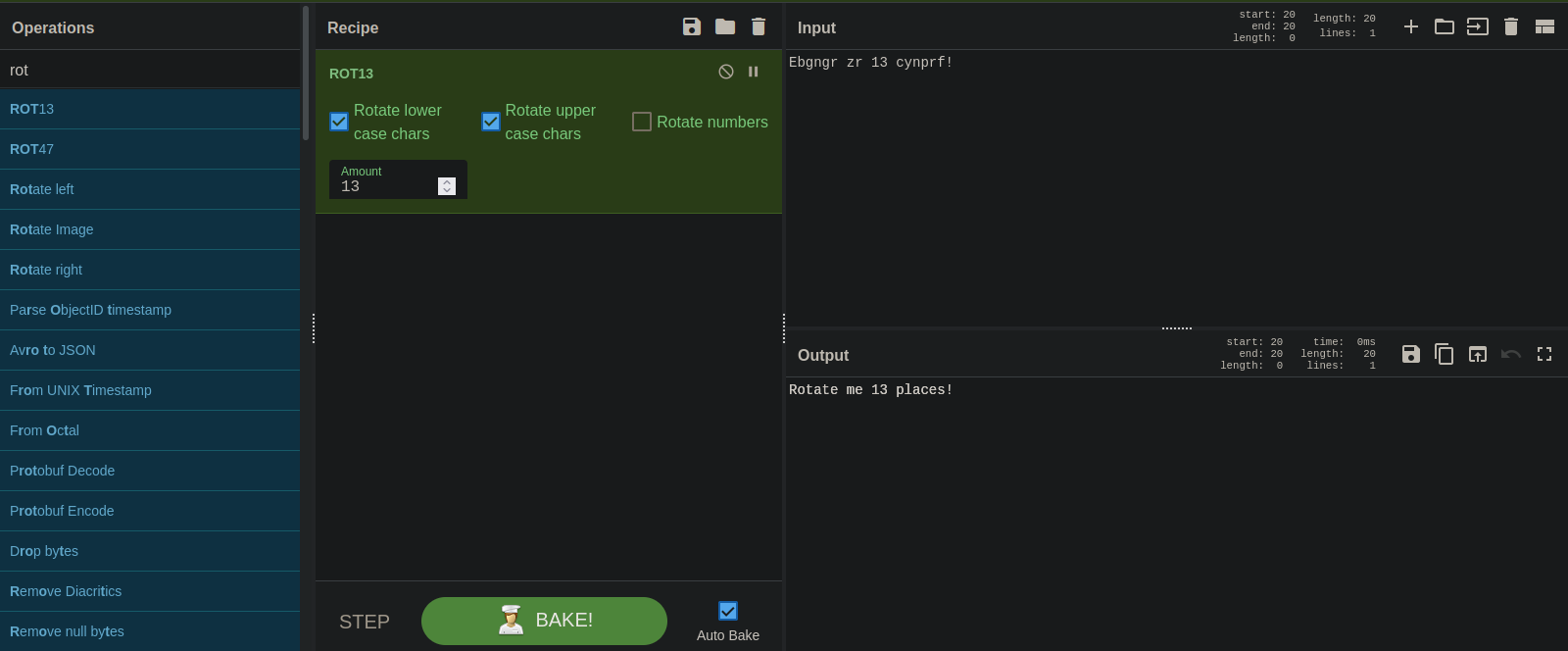
#6 : Ebgngr zr 13 cynprf
I see the number 13, so i’m guessing it’s rot13.
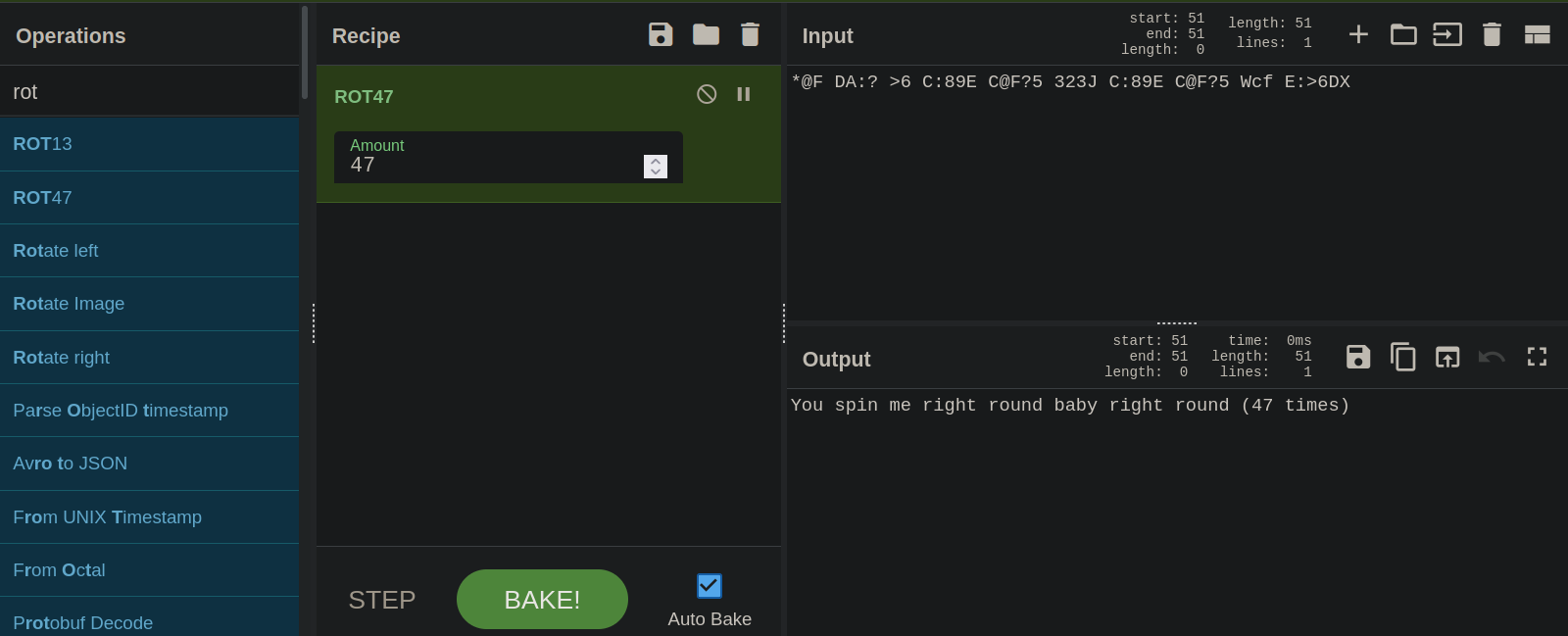
#7
This is rot47.
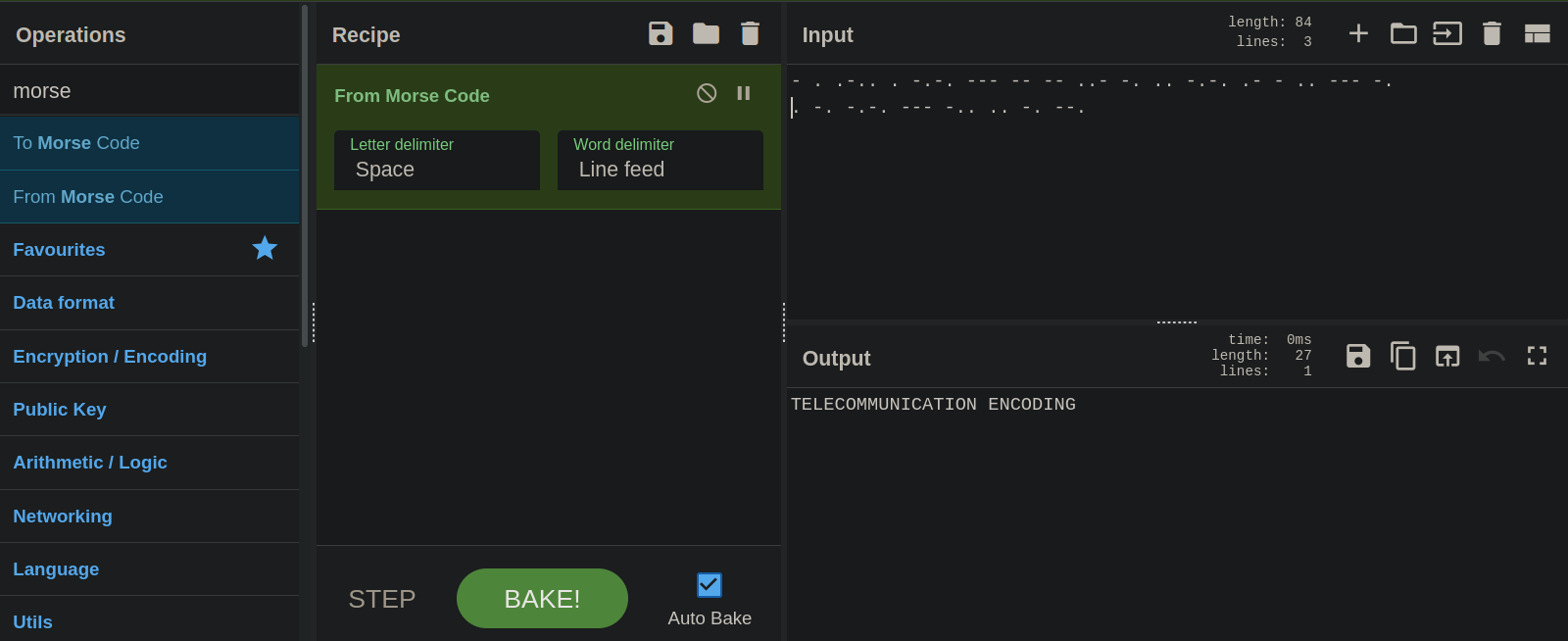
#8
This looks like morse code.
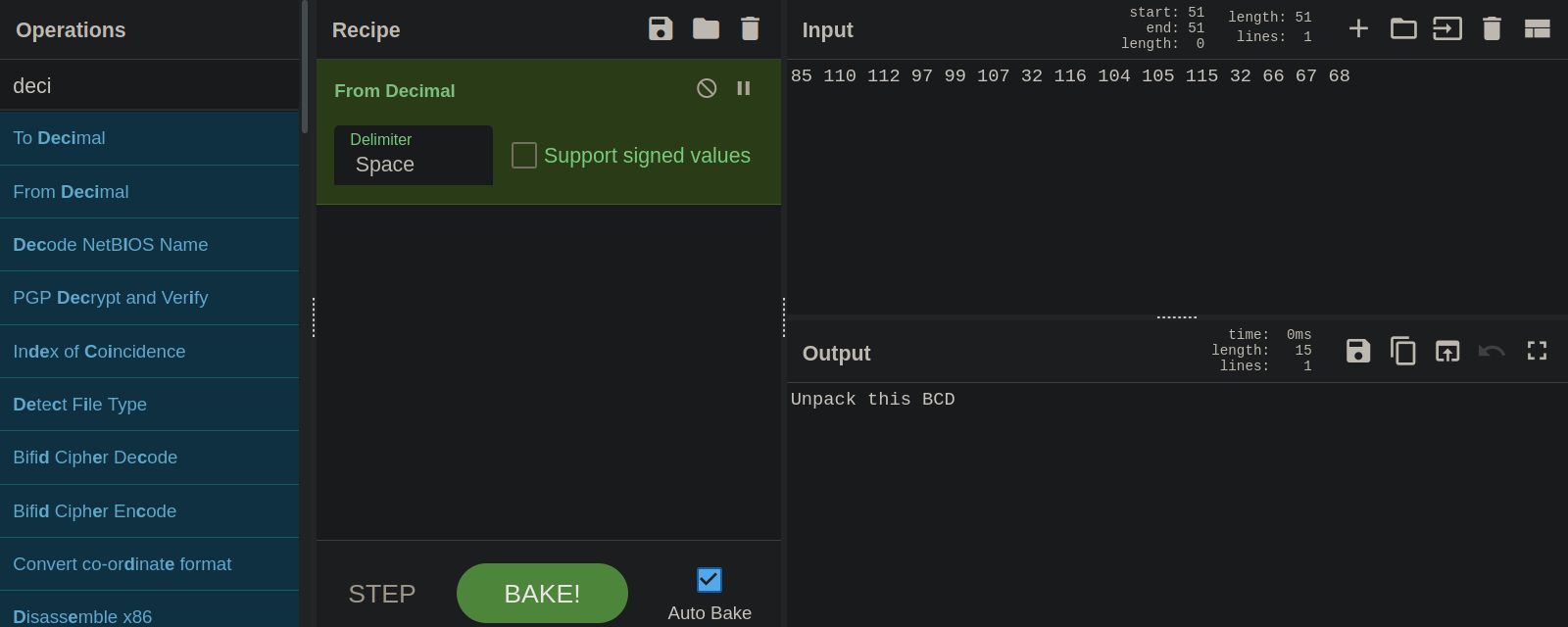
#9
This is decimal.
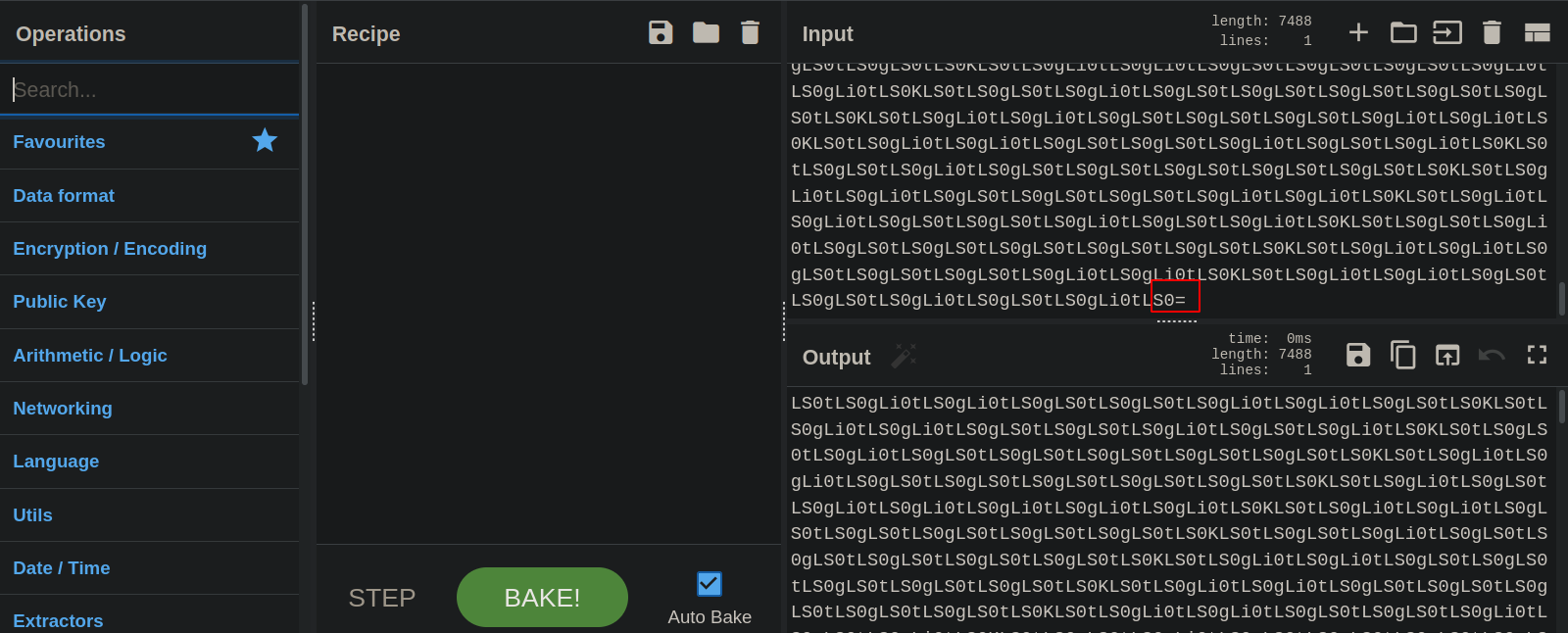
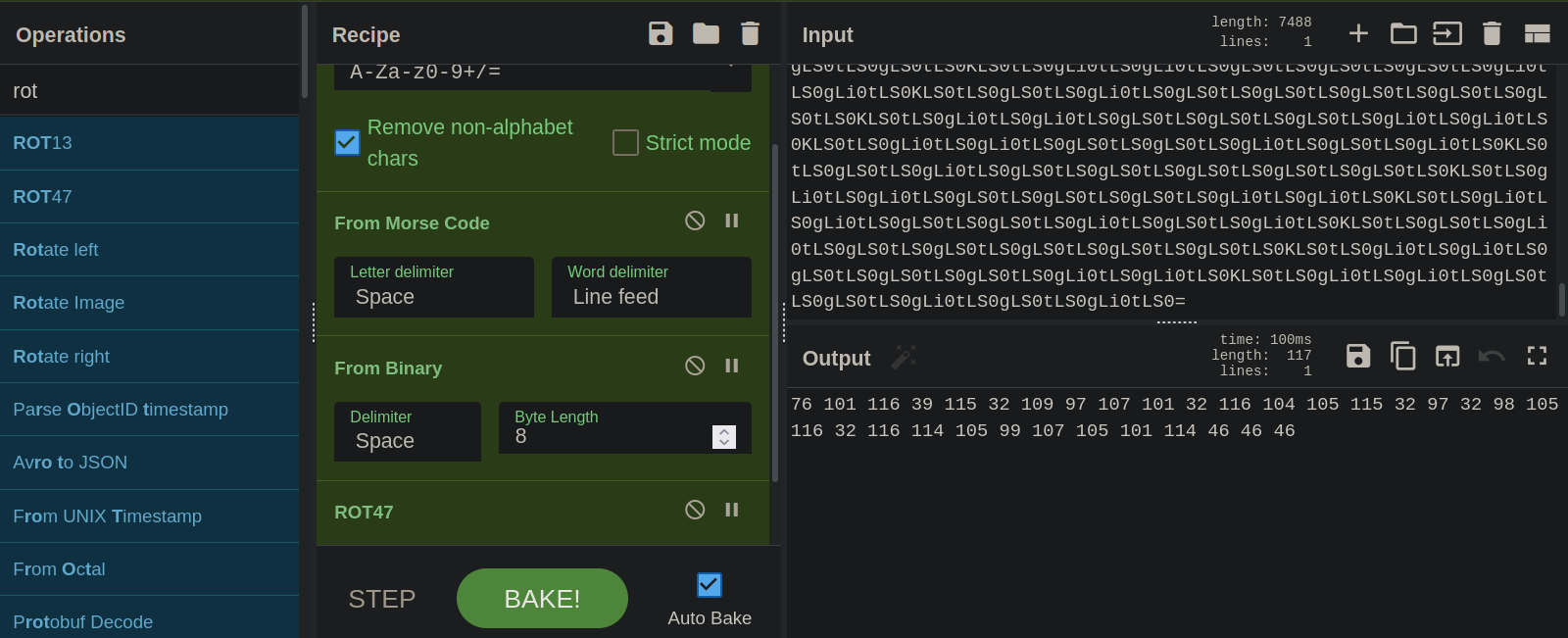
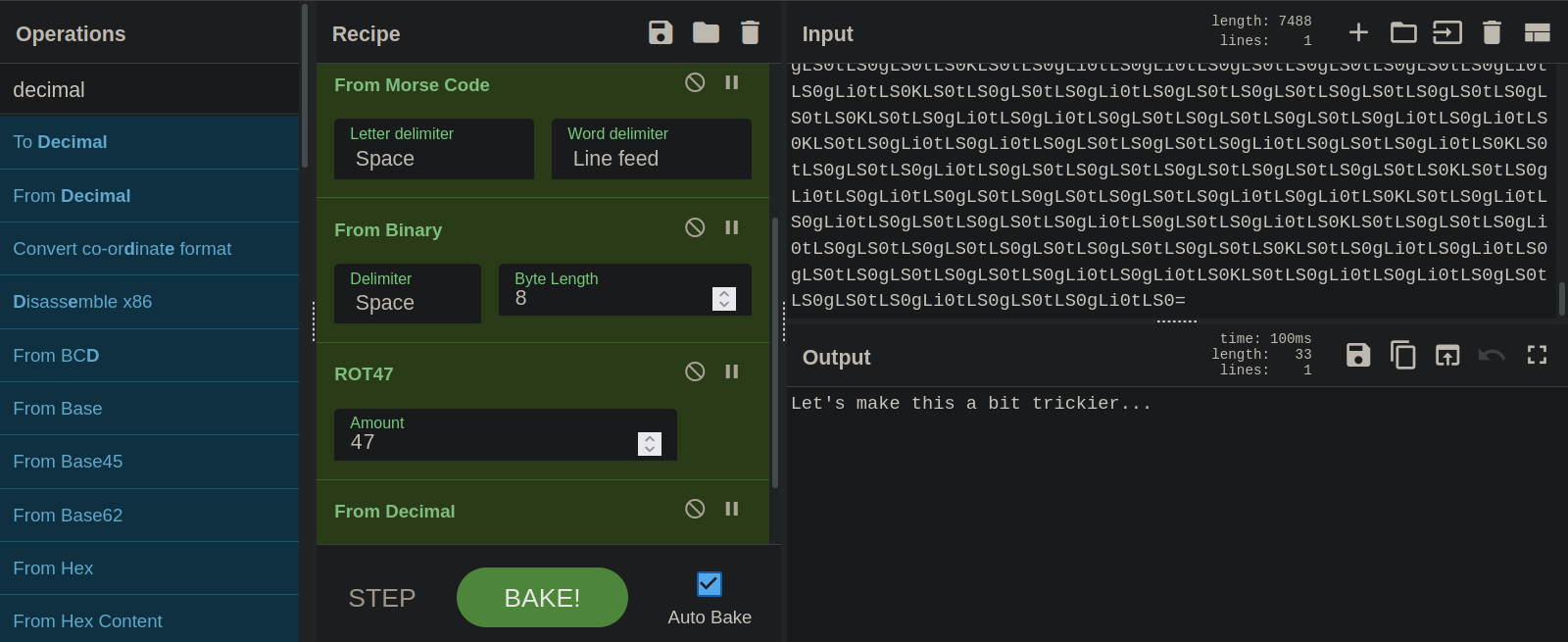
#10
We got a very long string here, let’s inspect it.
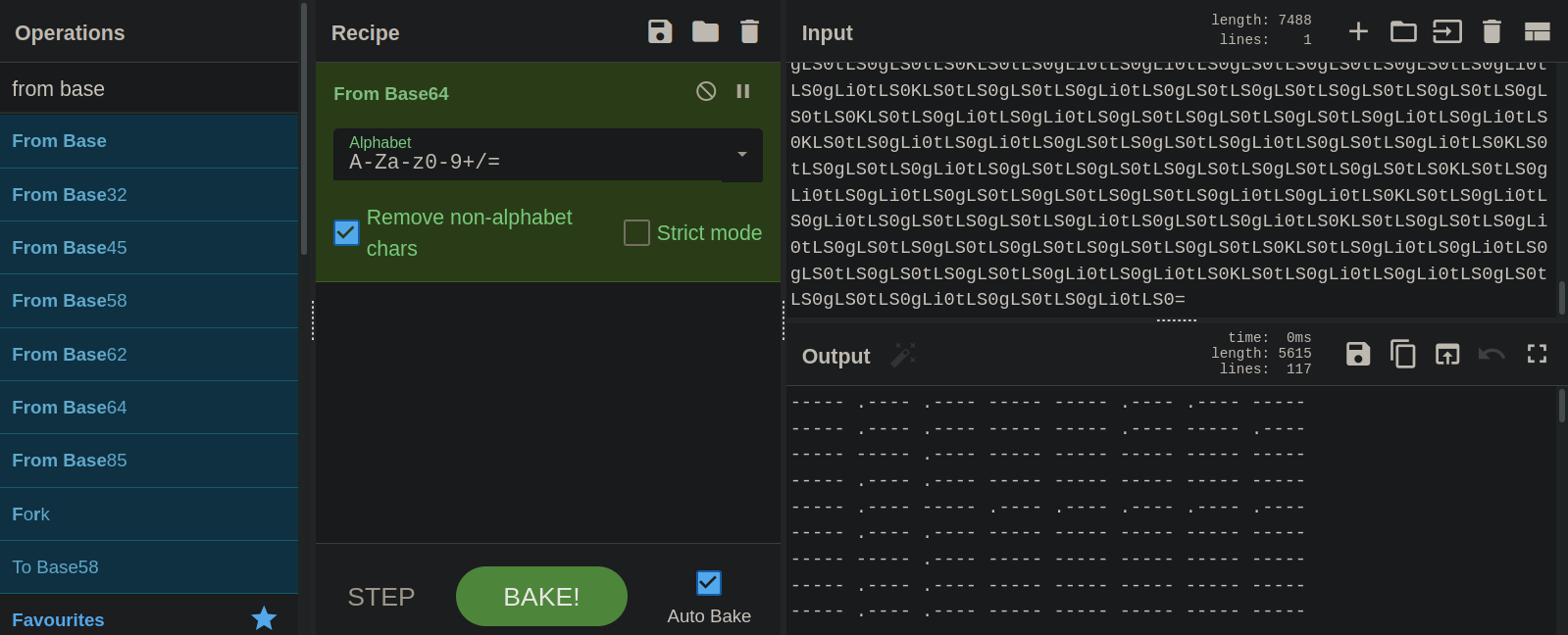
We see that the string ends with an equal sign, which can be a base64.
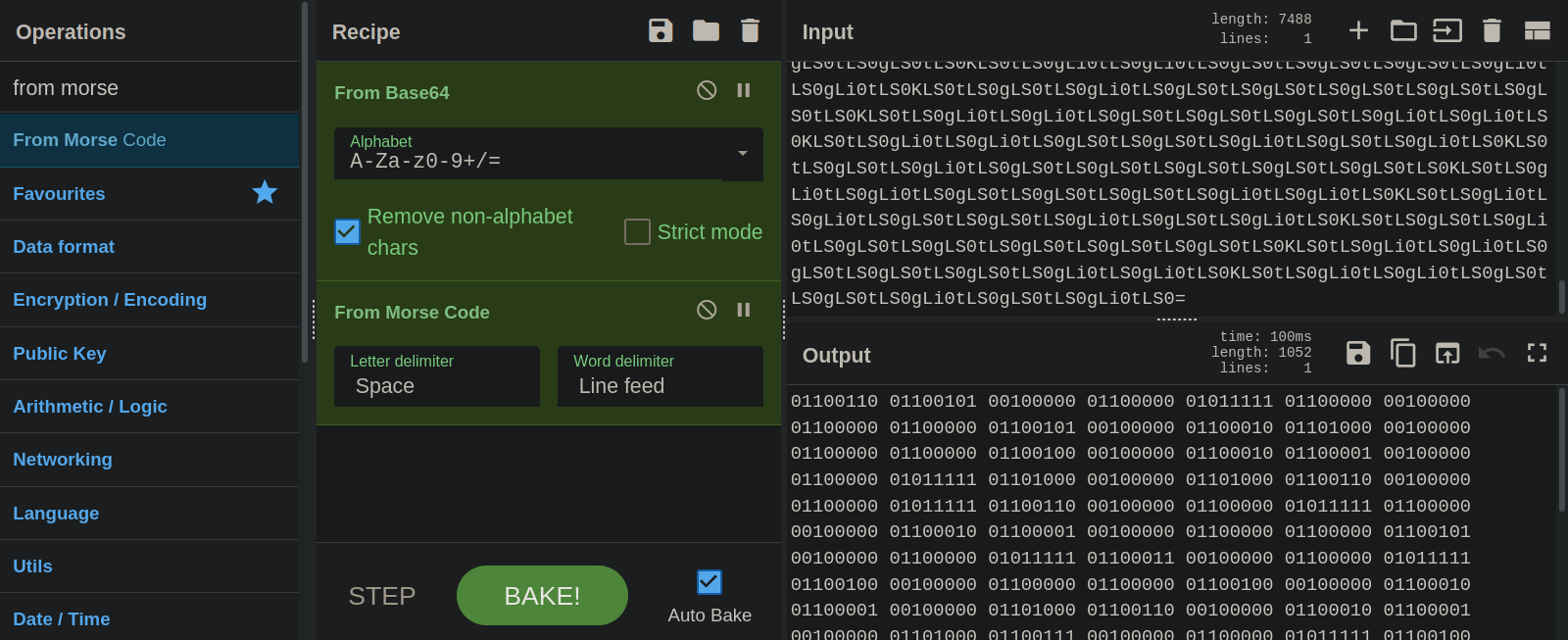
After we decoded it, it gave us a morse code.
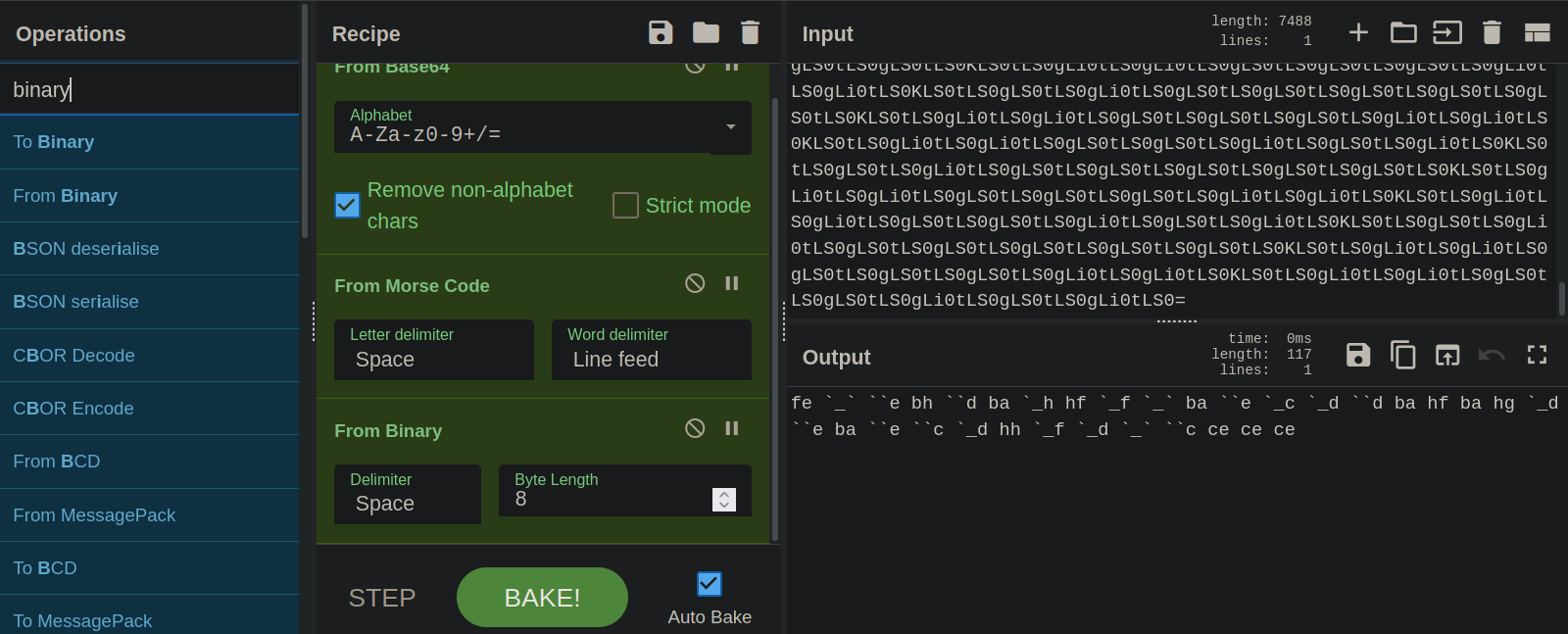
Morse code gave a hex code.
The hex gives a rot47.
We decode that and get decimal.
And this was the final one.
Spectrograms
A spectrogram is a visual representation of the spectrum of frequencies of a signal as it varies with time. When applied to an audio signal, spectrograms are sometimes called sonographs, voiceprints, or voicegrams. When the data is represented in a 3D plot they may be called waterfalls.
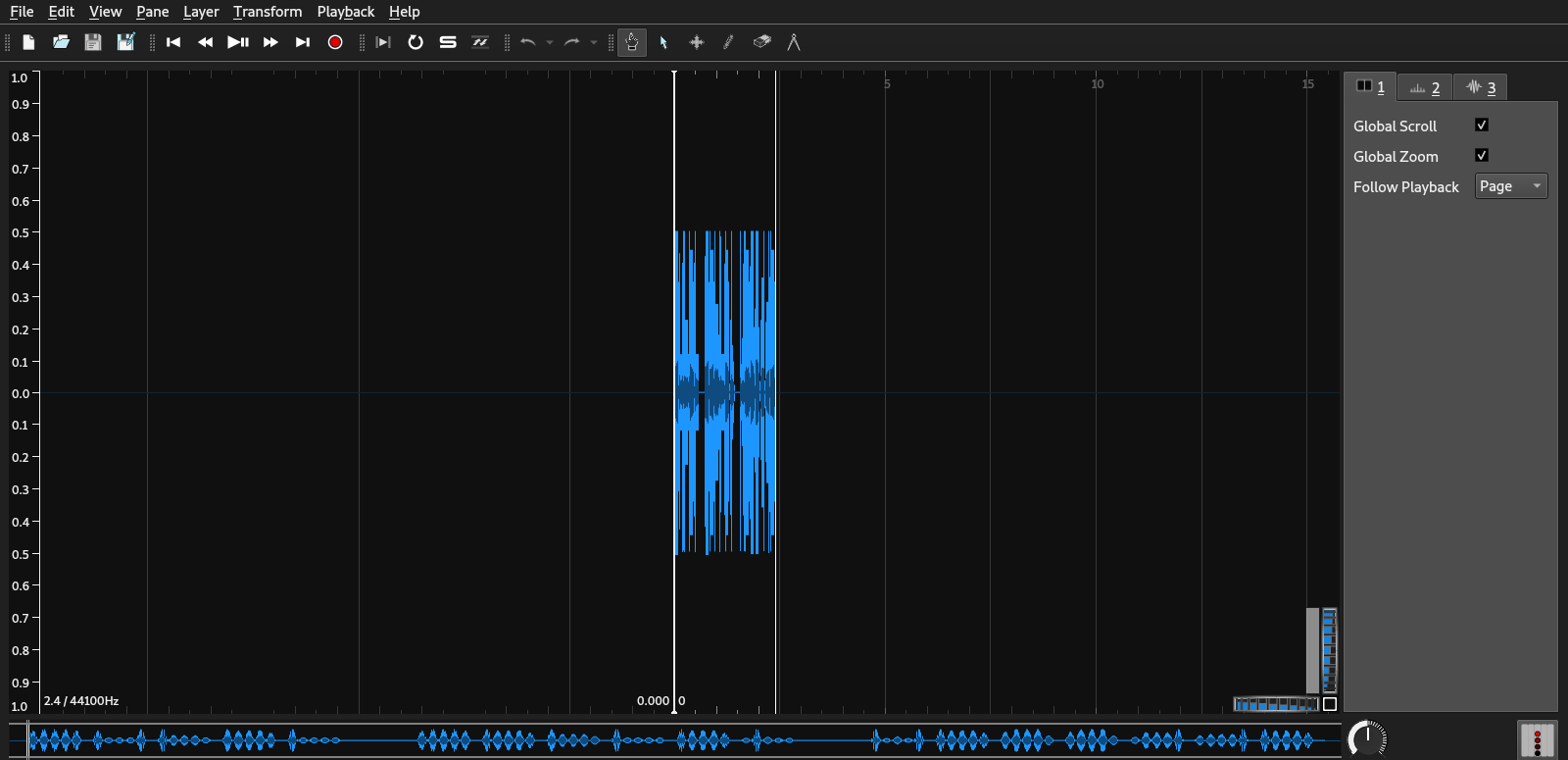
Let’s download the task file and open it with sonic-visualizer.
1
sonic-visualiser secretaudio.wav
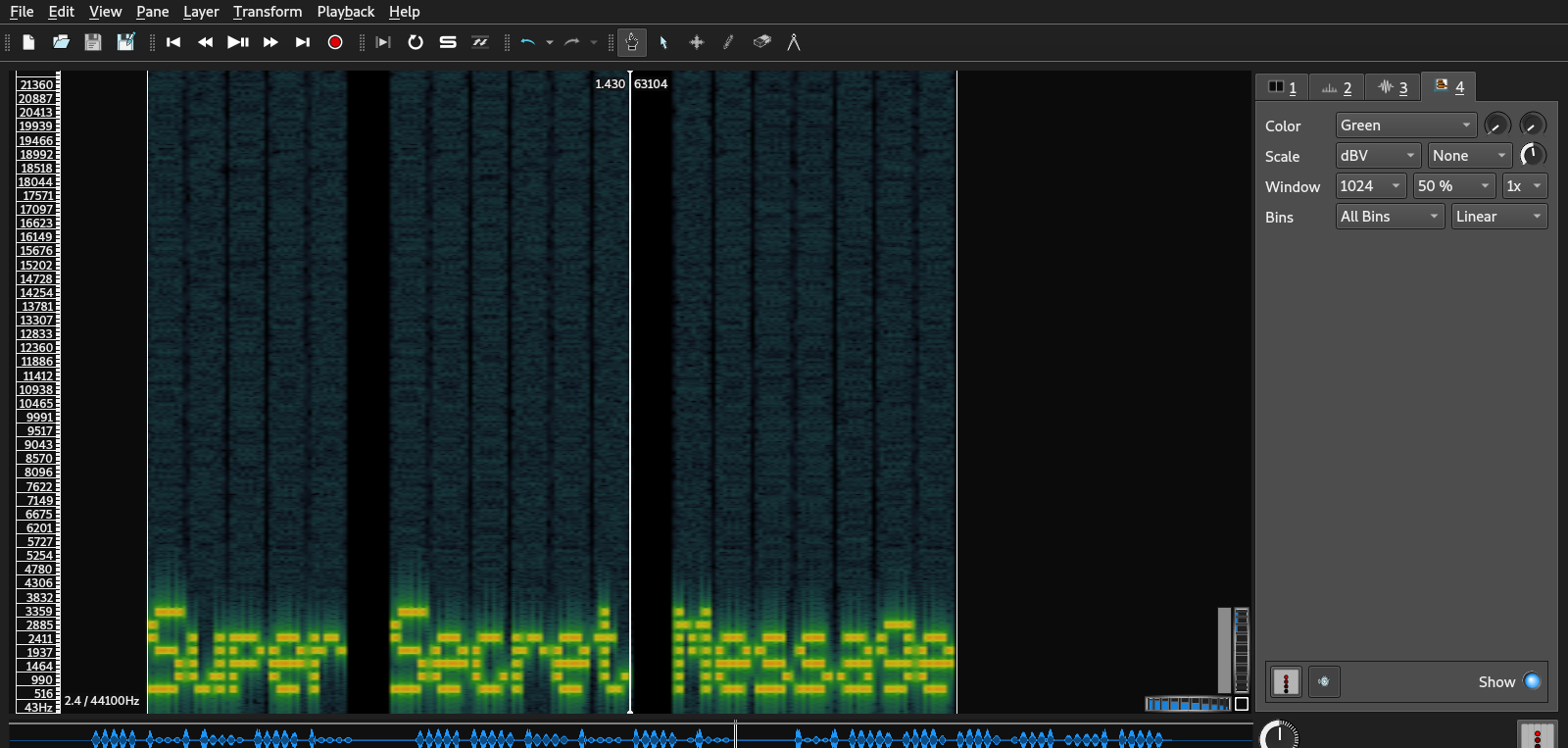
Now we need to add a spectrogram layer by going to Layer -> Add Spectrogram or pressing shift + G.
Steganography
Steganography is the practice of concealing a file, message, image, or video within another file, message, image, or video.
Let’s download the task file.
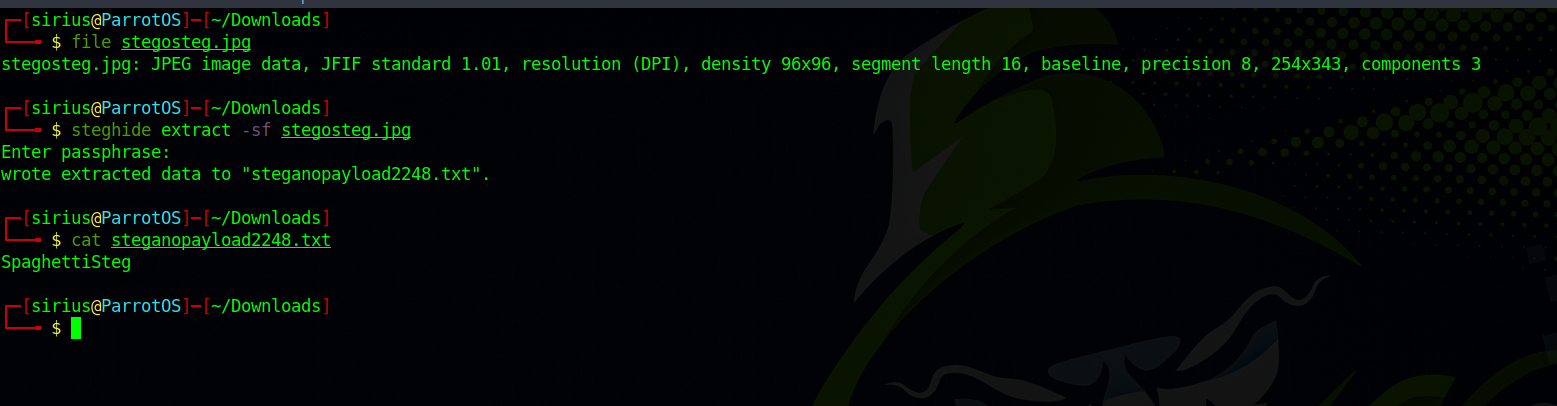
In order to extract files from images, we can use a tool called steghide.
1
Steghide extract -sh stegosteg.jpg`
After that we submit an empty password.
Security through obscurity
Security through obscurity is the reliance in security engineering on the secrecy of the design or implementation as the main method of providing security for a system or component of a system.
After downloading the task file, we run the command strings on the file.
1
Strings meme.jpg
At the very end we can see the answer to the last questions.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).